Hackvent 2024 - Medium

There were seven plus one hidden medium challenges in 2024 Hackvent. I had a lot of fun with the Windows memory dump, escaping from a Wine shell, programming a BFS to solve a maze, looking at corrupt disk sectors, with some steg and crypto mixed in.
HV24.04
Challenge
| HV24.04 Missing QR | |
|---|---|
| Categories: |
|
| Level: | medium |
| Author: | Dr. Nick |
Oh my Santa, the same elf who once messed up the color table did it again. But this time he seems to have been interrupted while painting the Christmas ball. Maybe you can help Santa finish his job?
Analyze the image and get the flag.
I’m given this image:

Solution
Identify Palette Data
Much like in Day 1, I’ll check out the color palette. In Gimp, it shows 231 out of the possible 255 colors occupied:

However, if I look at the palette bytes, there’s data past 231:
oxdf@hacky$ python
Python 3.12.3 (main, Nov 6 2024, 18:32:19) [GCC 13.2.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> from PIL import Image
>>> orig = Image.open('ba6004dd-2610-4443-a5c8-b12a9b655554.gif')
>>> orig.getpalette()
[0, 1, 0, 46, 4, 7, 83, 6, 12, 47, 21, 22, 109, 10, 20, 83, 18, 23, 57, 28, 35, 59, 34, 28, 60, 35, 37, 80, 29, 37, 132, 14, 22, 116, 19, 28, 132, 18, 28, 76, 38, 27, 121, 26, 35, 82, 40, 47, 144, 25, 37, 130, 29, 39, 133, 30, 36, 96, 43, 49, 121, 36, 45, 98, 46, 57, 101, 47, 57, 173, 26, 42, 90, 53, 55, 143, 37, 47, 136, 44, 53, 113, 50, 56, 90, 59, 69, 196, 28, 44, 99, 58, 68, 172, 36, 50, 107, 56, 62, 99, 61, 70, 116, 57, 68, 114, 59, 66, 142, 50, 59, 93, 67, 72, 121, 65, 60, 207, 38, 54, 170, 51, 60, 142, 58, 66, 139, 60, 70, 109, 70, 80, 110, 71, 78, 119, 71, 50, 106, 74, 50, 112, 70, 79, 113, 71, 82, 198, 49, 63, 173, 57, 69, 226, 40, 61, 216, 47, 64, 145, 70, 79, 140, 75, 52, 233, 46, 65, 208, 54, 70, 120, 82, 90, 114, 84, 92, 121, 85, 92, 116, 87, 84, 174, 70, 81, 243, 53, 71, 142, 84, 54, 116, 90, 100, 146, 84, 88, 207, 70, 83, 123, 96, 87, 147, 91, 98, 174, 82, 90, 161, 92, 59, 120, 102, 109, 171, 90, 99, 138, 103, 82, 156, 97, 94, 203, 83, 93, 174, 90, 98, 143, 102, 110, 145, 103, 109, 146, 105, 111, 152, 104, 106, 149, 104, 112, 206, 89, 99, 159, 105, 103, 171, 104, 60, 169, 105, 72, 172, 100, 108, 160, 107, 107, 171, 105, 111, 177, 103, 110, 150, 114, 89, 149, 117, 112, 193, 107, 114, 185, 115, 60, 145, 122, 132, 173, 118, 84, 173, 119, 115, 164, 122, 118, 158, 124, 130, 169, 123, 111, 197, 114, 122, 166, 124, 129, 126, 134, 145, 146, 132, 118, 194, 122, 76, 171, 125, 130, 177, 125, 131, 176, 125, 133, 177, 130, 92, 145, 137, 144, 177, 133, 106, 201, 122, 130, 172, 134, 118, 177, 135, 113, 170, 135, 136, 172, 136, 118, 178, 136, 110, 177, 136, 118, 173, 136, 135, 178, 136, 115, 204, 132, 79, 172, 137, 136, 178, 134, 140, 170, 139, 141, 174, 139, 141, 145, 148, 154, 179, 145, 116, 194, 138, 145, 193, 143, 107, 188, 145, 116, 150, 155, 163, 187, 146, 123, 192, 144, 115, 174, 149, 151, 189, 148, 106, 179, 149, 144, 179, 148, 151, 181, 148, 146, 194, 149, 116, 180, 150, 149, 169, 154, 164, 183, 153, 149, 199, 152, 111, 181, 154, 161, 195, 150, 153, 194, 153, 156, 173, 162, 164, 153, 169, 174, 197, 156, 161, 170, 166, 156, 208, 159, 118, 168, 169, 175, 179, 167, 168, 172, 168, 168, 186, 164, 166, 172, 168, 175, 211, 164, 119, 198, 164, 170, 201, 164, 166, 157, 176, 184, 200, 166, 171, 200, 169, 170, 205, 167, 171, 214, 167, 158, 208, 169, 153, 200, 171, 172, 213, 169, 144, 167, 181, 187, 215, 171, 137, 224, 172, 125, 219, 174, 147, 221, 176, 124, 198, 178, 182, 171, 186, 195, 226, 176, 126, 209, 178, 181, 178, 186, 195, 217, 181, 139, 213, 179, 198, 210, 180, 182, 186, 188, 189, 185, 188, 192, 188, 189, 197, 209, 183, 185, 195, 188, 196, 212, 184, 201, 189, 193, 187, 233, 185, 132, 209, 189, 193, 185, 197, 201, 213, 188, 192, 178, 200, 208, 222, 192, 158, 186, 200, 208, 188, 203, 208, 189, 202, 204, 220, 196, 172, 215, 197, 200, 196, 203, 208, 238, 192, 165, 206, 202, 203, 246, 198, 141, 188, 210, 219, 196, 212, 219, 196, 212, 220, 191, 215, 225, 194, 213, 220, 251, 200, 162, 241, 202, 204, 203, 215, 221, 199, 218, 227, 211, 216, 216, 208, 219, 224, 243, 214, 162, 252, 213, 150, 214, 218, 225, 218, 218, 221, 247, 214, 166, 220, 218, 224, 240, 217, 216, 222, 223, 227, 209, 231, 239, 221, 228, 233, 253, 230, 173, 224, 235, 243, 242, 231, 232, 221, 243, 251, 246, 236, 241, 250, 236, 240, 255, 245, 184, 254, 255, 208, 255, 253, 252, 0, 0, 1, 1, 0, 1, 1, 0, 0, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 0, 1, 1, 0, 0, 1, 0, 1, 0, 0, 0, 0, 1, 1, 0, 0, 1, 0, 0, 1, 0, 0, 1, 1, 0, 0, 0, 1, 1, 0, 1, 0, 0, 1, 1, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
>>> orig.getpalette()[(230-255)*3:]
[255, 253, 252, 0, 0, 1, 1, 0, 1, 1, 0, 0, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 0, 1, 1, 0, 0, 1, 0, 1, 0, 0, 0, 0, 1, 1, 0, 0, 1, 0, 0, 1, 0, 0, 1, 1, 0, 0, 0, 1, 1, 0, 1, 0, 0, 1, 1, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Each entry is three bytes long, so looking at from (230-255)*3 to the end gives the last entry and what comes after. Interestingly, all the real entries have an assortment of numbers, but after the end of the table, there’s just 0s and 1.
Least Significate Bit
A common steganography technique is to hide data in the least significant bit. I’ll take a look at that here:
>>> bits = [b&1 for b in orig.getpalette()]
>>> byte_str = bytes(int("".join(map(str, bits[i:i+8])), 2) for i in range(0, len(bits), 8))
>>> byte_str
b"Fill in:||\xc6 \x99#\xb4BE\x81\xcf\x95U\x00dx\x02\xdc)\xa9q;\x11\xf9\x83\xf8\xed\xa4\xe0xH\x1b\xb9\xb4\x1d\x01)(71\xe9\xd2\xe6\xb1\x19\xed\xaaj\x13\xc0\x1a$+\xa6\xb7\xe6\xc1E?\x03\x1f\x87\xef\xe0\x01A\x91$\x91\xd4\x9e\xc5\x110'\xedk\x91\x966)L\xa1\x92cN\x08\x00"
I’m definitely onto something here, as the first eight bytes make the string “Fill in:”. But then the rest is non-ASCII.
Fill In
I’ll take a look at the QR code in the image. Each black or white is five pixels wide, and the entire section is 145 x 145. That makes it a 29 x 29 grid, with three corners already filled in, each 7 x 7.
- Total bits: 29 x 29 = 841
- Single corner bits: 7 x 7 = 49
- Three corner bits: 49 x 3 = 147
- Missing bits: 841 - 147 = 694
The remaining 1s and 0s after taking off the first 64 bytes to make eight bytes “Fill in:” leaves 704, which is a bit over what’s needed to fill 694!
>>> len(bits) - 64
704
With some help from ChatGPT, I’ll write a Python script that generates a new QRcode from the remaining bits, filling in around the existing corners, and pastes it back into the original image:
from PIL import Image
orig = Image.open('ba6004dd-2610-4443-a5c8-b12a9b655554.gif')
bits = [b&1 for b in orig.getpalette()]
byte_str = bytes(int("".join(map(str, bits[i:i+8])), 2) for i in range(0, 64, 8))
remaining_bits = bits[64:]
# print(byte_str.decode())
# print(remaining_bits)
image_size = 29
corner_pattern = [
[1, 1, 1, 1, 1, 1, 1],
[1, 0, 0, 0, 0, 0, 1],
[1, 0, 1, 1, 1, 0, 1],
[1, 0, 1, 1, 1, 0, 1],
[1, 0, 1, 1, 1, 0, 1],
[1, 0, 0, 0, 0, 0, 1],
[1, 1, 1, 1, 1, 1, 1],
]
qr_code = [[0] * image_size for _ in range(image_size)]
img = Image.new("1", (image_size, image_size)) # 1-bit image
pixels = img.load()
for i in range(7):
for j in range(7):
pixels[i, j] = 1 - corner_pattern[i][j]
pixels[i, image_size - 7 + j] = 1 - corner_pattern[i][j]
pixels[image_size - 7 + i, j] = 1 - corner_pattern[i][j]
bit_index = 0
for row in range(image_size):
for col in range(image_size):
if (
(row < 7 and col < 7) or
(row < 7 and col >= image_size - 7) or
(row >= image_size - 7 and col < 7)
):
continue
if bit_index < len(remaining_bits):
pixels[row, col] = 1 - int(remaining_bits[bit_index])
bit_index += 1
img = img.resize((image_size*5, image_size*5), Image.NEAREST)
orig = orig.convert("RGBA")
orig.paste(img, (144, 193))
orig.save("result.png")
orig.show()
On running that, I get:

It’s worth noting in the code that PIL sets 1 to white and 0 to black, so on my initial run, I generated:

I can tell from the corners that it’s inverted. To fix it I added this line to invert black and white:
img = ImageOps.invert(img.convert("L")).convert("1")
Either image scans with my phone camera to the flag, but zbarimg only recognizes the inverted correct one:
oxdf@hacky$ zbarimg result.png
QR-Code:HV24{QR_$tuff_h1dd3n_in_th3_c0lor_t@b1e}
scanned 1 barcode symbols from 1 images in 0 seconds
Flag: HV24{QR_$tuff_h1dd3n_in_th3_c0lor_t@b1e}
HV24.05
Challenge
| HV24.05 Last Password | |
|---|---|
| Categories: |
|
| Level: | medium |
| Author: | xtea418 |
Last Password, I gave you away and the very next day, all my accounts where astray. This year to save me from tears, I’ll give it to no one.
Analyze the file and get the flag.
I’m given a dump.raw file that file reports as “data”:
oxdf@hacky$ file dump.raw
dump.raw: data
Solution
I’ll start by trying Volatility3 against the dump, and it works:
oxdf@hacky$ vol -f dump.raw windows.info.Info
Volatility 3 Framework 2.8.0
Progress: 100.00 PDB scanning finished
Variable Value
Kernel Base 0xf80479c14000
DTB 0x1aa000
Symbols file:///home/oxdf/.local/share/pipx/venvs/volatility3/lib/python3.12/site-packages/volatility3/symbols/windows/ntkrnlmp.pdb/BFF14F607A9930D2FDA0481A29685111-1.json.xz
Is64Bit True
IsPAE False
layer_name 0 WindowsIntel32e
memory_layer 1 FileLayer
KdVersionBlock 0xf8047a823418
Major/Minor 15.19041
MachineType 34404
KeNumberProcessors 23
SystemTime 2024-11-24 15:04:30+00:00
NtSystemRoot C:\Windows
NtProductType NtProductWinNt
NtMajorVersion 10
NtMinorVersion 0
PE MajorOperatingSystemVersion 10
PE MinorOperatingSystemVersion 0
PE Machine 34404
PE TimeDateStamp Mon Jun 10 14:11:02 2069
This is a Windows memory dump. Given that, I’ll check for running processes with the pstree module:
oxdf@hacky$ vol -f dump.raw windows.pstree
Volatility 3 Framework 2.8.0
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime Audit Cmd Path
4 0 System 0xc0832a883080 334 - N/A False 2024-11-24 15:00:59.000000 UTC N/A - - -
* 648 4 smss.exe 0xc0833851c0c0 2 - N/A False 2024-11-24 15:00:59.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\smss.exe \SystemRoot\System32\smss.exe \SystemRoot\System32\smss.exe
* 1956 4 MemCompression 0xc0833b5b1040 26 - N/A False 2024-11-24 15:01:15.000000 UTC N/A MemCompression - -
* 260 4 Registry 0xc0832aa63040 4 - N/A False 2024-11-24 15:00:56.000000 UTC N/A Registry - -
748 740 csrss.exe 0xc08336f0c140 13 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\csrss.exe %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 C:\Windows\system32\csrss.exe
824 740 wininit.exe 0xc0832cd08080 1 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\wininit.exe wininit.exe C:\Windows\system32\wininit.exe
* 972 824 lsass.exe 0xc08338cd7080 12 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\lsass.exe C:\Windows\system32\lsass.exe C:\Windows\system32\lsass.exe
* 964 824 services.exe 0xc0832cd1f080 9 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\services.exe C:\Windows\system32\services.exe C:\Windows\system32\services.exe
** 1400 964 svchost.exe 0xc0833d104280 24 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted -p C:\Windows\System32\svchost.exe
*** 4160 1400 ctfmon.exe 0xc0833d896280 13 - 1 False 2024-11-24 15:01:37.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\ctfmon.exe "ctfmon.exe" C:\Windows\system32\ctfmon.exe
** 3724 964 SearchIndexer. 0xc083381182c0 14 - 0 False 2024-11-24 15:01:16.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\SearchIndexer.exe C:\Windows\system32\SearchIndexer.exe /Embedding C:\Windows\system32\SearchIndexer.exe
*** 4032 3724 SearchProtocol 0xc08338142080 6 - 0 False 2024-11-24 15:01:16.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\SearchProtocolHost.exe "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe1_ Global\UsGthrCtrlFltPipeMssGthrPipe1 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" C:\Windows\system32\SearchProtocolHost.exe
*** 11228 3724 SearchProtocol 0xc0833db87080 4 - 1 False 2024-11-24 15:02:14.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\SearchProtocolHost.exe "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe_S-1-5-21-3909435439-1930665703-3246598564-10012_ Global\UsGthrCtrlFltPipeMssGthrPipe_S-1-5-21-3909435439-1930665703-3246598564-10012 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" "1" C:\Windows\system32\SearchProtocolHost.exe
*** 4060 3724 SearchFilterHo 0xc083375bb080 5 - 0 False 2024-11-24 15:01:16.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\SearchFilterHost.exe--
** 2832 964 MpDefenderCore 0xc083393c40c0 9 - 0 False 2024-11-24 15:01:16.000000 UTC N/A \Device\HarddiskVolume2\ProgramData\Microsoft\Windows Defender\Platform\4.18.24090.11-0\MpDefenderCoreService.exe "C:\ProgramData\Microsoft\Windows Defender\platform\4.18.24090.11-0\MpDefenderCoreService.exe" C:\ProgramData\Microsoft\Windows Defender\platform\4.18.24090.11-0\MpDefenderCoreService.exe
** 1556 964 svchost.exe 0xc0833dd632c0 6 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceAndNoImpersonation C:\Windows\system32\svchost.exe
** 2844 964 MsMpEng.exe 0xc083372db340 86 - 0 False 2024-11-24 15:01:16.000000 UTC N/A \Device\HarddiskVolume2\ProgramData\Microsoft\Windows Defender\Platform\4.18.24090.11-0\MsMpEng.exe "C:\ProgramData\Microsoft\Windows Defender\platform\4.18.24090.11-0\MsMpEng.exe" C:\ProgramData\Microsoft\Windows Defender\platform\4.18.24090.11-0\MsMpEng.exe
** 4256 964 svchost.exe 0xc0833980b300 6 - 1 False 2024-11-24 15:01:37.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k ClipboardSvcGroup -p C:\Windows\system32\svchost.exe
** 6572 964 svchost.exe 0xc08336def080 10 - 0 False 2024-11-24 15:02:52.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceAndNoImpersonation -p C:\Windows\system32\svchost.exe
** 9388 964 svchost.exe 0xc08339583080 12 - 0 False 2024-11-24 15:03:17.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted -p C:\Windows\System32\svchost.exe
** 1200 964 WUDFHost.exe 0xc0833dd11080 5 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\WUDFHost.exe "C:\Windows\System32\WUDFHost.exe" -HostGUID:{193a1820-d9ac-4997-8c55-be817523f6aa} -IoEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-51a51248-3003-49b7-bd5c-9e8fb646ad69 -SystemEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-c25e7f0f-7f86-4b0b-a3d7-198e49c7018c -IoCancelEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-50384fbf-acf7-4015-9925-d85689ee8d57 -NonStateChangingEventPortName:\UMDFCommunicationPorts\WUDF\HostProcess-d1e57201-2740-4c74-8157-d454689faa5b -LifetimeId:83732c2d-77ac-4b5f-9da7-d6207b0b3f64 -DeviceGroupId:WudfDefaultDevicePool -HostArg:0C:\Windows\System32\WUDFHost.exe
** 2480 964 spoolsv.exe 0xc0832cdd3080 8 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\spoolsv.exe C:\Windows\System32\spoolsv.exe C:\Windows\System32\spoolsv.exe
** 8880 964 svchost.exe 0xc0833a1e4080 2 - 1 False 2024-11-24 15:01:57.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k PrintWorkflow C:\Windows\system32\svchost.exe
** 2100 964 svchost.exe 0xc0833b508080 11 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted -p C:\Windows\System32\svchost.exe
*** 9268 2100 audiodg.exe 0xc0833ae722c0 6 - 0 False 2024-11-24 15:01:58.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\audiodg.exe C:\Windows\system32\AUDIODG.EXE 0x558 C:\Windows\system32\AUDIODG.EXE
** 11188 964 SgrmBroker.exe 0xc0833671d080 7 - 0 False 2024-11-24 15:03:16.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\SgrmBroker.exe C:\Windows\system32\SgrmBroker.exe C:\Windows\system32\SgrmBroker.exe
** 4152 964 NisSrv.exe 0xc0833565c080 3 - 0 False 2024-11-24 15:01:21.000000 UTC N/A \Device\HarddiskVolume2\ProgramData\Microsoft\Windows Defender\Platform\4.18.24090.11-0\NisSrv.exe "C:\ProgramData\Microsoft\Windows Defender\platform\4.18.24090.11-0\NisSrv.exe" C:\ProgramData\Microsoft\Windows Defender\platform\4.18.24090.11-0\NisSrv.exe
** 1852 964 SecurityHealth 0xc08336ee0280 15 - 0 False 2024-11-24 15:01:50.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\SecurityHealthService.exe C:\Windows\system32\SecurityHealthService.exe C:\Windows\system32\SecurityHealthService.exe
** 4288 964 svchost.exe 0xc0833565a080 23 - 1 False 2024-11-24 15:01:37.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k UnistackSvcGroup C:\Windows\system32\svchost.exe
** 836 964 svchost.exe 0xc08337715240 26 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k DcomLaunch -p C:\Windows\system32\svchost.exe
*** 5984 836 RuntimeBroker. 0xc0833d326300 7 - 1 False 2024-11-24 15:01:38.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\RuntimeBroker.exe C:\Windows\System32\RuntimeBroker.exe -Embedding C:\Windows\System32\RuntimeBroker.exe
*** 5792 836 SearchApp.exe 0xc08338ea4080 31 - 1 False 2024-11-24 15:01:38.000000 UTC N/A \Device\HarddiskVolume2\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe "C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe
*** 6948 836 RuntimeBroker. 0xc0833d8d6080 4 - 1 False 2024-11-24 15:03:18.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\RuntimeBroker.exe C:\Windows\System32\RuntimeBroker.exe -Embedding C:\Windows\System32\RuntimeBroker.exe
*** 3432 836 dllhost.exe 0xc083398e92c0 5 - 0 False 2024-11-24 15:01:17.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\dllhost.exe C:\Windows\system32\DllHost.exe /Processid:{3EB3C877-1F16-487C-9050-104DBCD66683} C:\Windows\system32\DllHost.exe
*** 6600 836 RuntimeBroker. 0xc08338553080 12 - 1 False 2024-11-24 15:02:51.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\RuntimeBroker.exe C:\Windows\System32\RuntimeBroker.exe -Embedding C:\Windows\System32\RuntimeBroker.exe
*** 6712 836 smartscreen.ex 0xc0832cf1e300 8 - 1 False 2024-11-24 15:01:50.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\smartscreen.exe C:\Windows\System32\smartscreen.exe -Embedding C:\Windows\System32\smartscreen.exe
*** 5612 836 RuntimeBroker. 0xc08336e66300 3 - 1 False 2024-11-24 15:01:38.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\RuntimeBroker.exe C:\Windows\System32\RuntimeBroker.exe -Embedding C:\Windows\System32\RuntimeBroker.exe
*** 6140 836 dllhost.exe 0xc0833b5c7080 8 - 1 True 2024-11-24 15:04:31.000000 UTC N/A \Device\HarddiskVolume2\Windows\SysWOW64\dllhost.exe - -
*** 7160 836 TextInputHost. 0xc08335c22340 10 - 1 False 2024-11-24 15:01:48.000000 UTC N/A \Device\HarddiskVolume2\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe "C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXk0k6mrh4r2q0ct33a9wgbez0x7v9cz5y.mca C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe
*** 5372 836 StartMenuExper 0xc0833df5a080 7 - 1 False 2024-11-24 15:01:38.000000 UTC N/A \Device\HarddiskVolume2\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe "C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe
** 1476 964 svchost.exe 0xc0833d2e2240 17 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs C:\Windows\system32\svchost.exe
** 2756 964 svchost.exe 0xc0833dfa4240 11 - 0 False 2024-11-24 15:01:16.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k utcsvc -p C:\Windows\System32\svchost.exe
*** 772 2756 AggregatorHost 0xc083398a90c0 1 - 0 False 2024-11-24 15:01:16.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\AggregatorHost.exe AggregatorHost.exe C:\Windows\System32\AggregatorHost.exe
** 1356 964 svchost.exe 0xc083342bf2c0 34 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalService -p C:\Windows\system32\svchost.exe
** 1108 964 svchost.exe 0xc083384e32c0 11 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k RPCSS -p C:\Windows\system32\svchost.exe
** 2260 964 svchost.exe 0xc0832cdad0c0 9 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k appmodel -p C:\Windows\system32\svchost.exe
** 2520 964 svchost.exe 0xc0833b509300 13 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNoNetworkFirewall -p C:\Windows\system32\svchost.exe
** 6748 964 svchost.exe 0xc08336716080 6 - 0 False 2024-11-24 15:03:17.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalService C:\Windows\system32\svchost.exe
** 1248 964 svchost.exe 0xc083324c8240 69 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k netsvcs -p C:\Windows\system32\svchost.exe
*** 3664 1248 taskhostw.exe 0xc0833c1872c0 0 - 1 False 2024-11-24 15:01:37.000000 UTC 2024-11-24 15:01:37.000000 UTC \Device\HarddiskVolume2\Windows\System32\taskhostw.exe - -
*** 4532 1248 taskhostw.exe 0xc0833c19e0c0 9 - 1 False 2024-11-24 15:01:37.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\taskhostw.exe taskhostw.exe {222A245B-E637-4AE9-A93F-A59CA119A75E} C:\Windows\system32\taskhostw.exe
*** 4492 1248 sihost.exe 0xc083381130c0 19 - 1 False 2024-11-24 15:01:37.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\sihost.exe sihost.exe C:\Windows\system32\sihost.exe
** 1376 964 svchost.exe 0xc0833d2442c0 6 - 0 False 2024-11-24 15:01:16.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted C:\Windows\System32\svchost.exe
** 3812 964 svchost.exe 0xc083361a2240 27 - 0 False 2024-11-24 15:01:16.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k wsappx -p C:\Windows\system32\svchost.exe
** 1124 964 svchost.exe 0xc0833328a080 11 - 0 False 2024-11-24 15:03:16.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k NetworkService -p C:\Windows\System32\svchost.exe
** 2024 964 svchost.exe 0xc0833b55a2c0 17 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNoNetwork -p C:\Windows\system32\svchost.exe
** 1260 964 svchost.exe 0xc083324cd2c0 15 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted -p C:\Windows\System32\svchost.exe
** 2288 964 svchost.exe 0xc0832cdbc2c0 4 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNetworkRestricted -p C:\Windows\system32\svchost.exe
** 1524 964 svchost.exe 0xc0833d2f62c0 18 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k NetworkService -p C:\Windows\System32\svchost.exe
** 2296 964 svchost.exe 0xc0832cdbe2c0 4 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted -p C:\Windows\System32\svchost.exe
** 1916 964 svchost.exe 0xc0833b5ab2c0 3 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\svchost.exe C:\Windows\system32\svchost.exe -k LocalService -p C:\Windows\system32\svchost.exe
* 1004 824 fontdrvhost.ex 0xc0833771b140 5 - 0 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\fontdrvhost.exe "fontdrvhost.exe" C:\Windows\system32\fontdrvhost.exe
832 816 csrss.exe 0xc0832cd0b140 13 - 1 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\csrss.exe %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 C:\Windows\system32\csrss.exe
924 816 winlogon.exe 0xc083342e3080 5 - 1 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\winlogon.exe winlogon.exe C:\Windows\system32\winlogon.exe
* 3948 924 userinit.exe 0xc0833d8c6080 0 - 1 False 2024-11-24 15:01:37.000000 UTC 2024-11-24 15:02:00.000000 UTC \Device\HarddiskVolume2\Windows\System32\userinit.exe - -
** 3852 3948 explorer.exe 0xc0833d8d8080 92 - 1 False 2024-11-24 15:01:37.000000 UTC N/A \Device\HarddiskVolume2\Windows\explorer.exe C:\Windows\Explorer.EXE C:\Windows\Explorer.EXE
*** 11040 3852 WinRAR.exe 0xc0833b164300 5 - 1 False 2024-11-24 15:02:54.000000 UTC N/A \Device\HarddiskVolume2\Program Files\WinRAR\WinRAR.exe "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\xtea418\Documents\Personal\secret.7z" C:\Program Files\WinRAR\WinRAR.exe
*** 8064 3852 soffice.exe 0xc0833a110080 2 - 1 False 2024-11-24 15:01:54.000000 UTC N/A \Device\HarddiskVolume2\Program Files\LibreOffice\program\soffice.exe "C:\Program Files\LibreOffice\program\soffice.exe" -o "C:\Users\xtea418\Documents\nice-naugthy-list.ods" C:\Program Files\LibreOffice\program\soffice.exe
**** 8124 8064 soffice.bin 0xc0833277d080 13 - 1 False 2024-11-24 15:01:54.000000 UTC N/A \Device\HarddiskVolume2\Program Files\LibreOffice\program\soffice.bin "C:\Program Files\LibreOffice\program\soffice.exe" "-o" "C:\Users\xtea418\Documents\nice-naugthy-list.ods" "-env:OOO_CWD=2C:\\Windows\\system32" C:\Program Files\LibreOffice\program\soffice.bin
*** 11076 3852 DumpIt.exe 0xc0833b5e1080 4 - 1 True 2024-11-24 15:04:29.000000 UTC N/A \Device\HarddiskVolume2\Users\xtea418\Downloads\DumpIt.exe "C:\Users\xtea418\Downloads\DumpIt.exe" C:\Users\xtea418\Downloads\DumpIt.exe
**** 9288 11076 conhost.exe 0xc0833d2f1080 7 - 1 False 2024-11-24 15:04:29.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\conhost.exe \??\C:\Windows\system32\conhost.exe 0x4 C:\Windows\system32\conhost.exe
*** 2680 3852 WinRAR.exe 0xc0833216f080 9 - 1 False 2024-11-24 15:04:11.000000 UTC N/A \Device\HarddiskVolume2\Program Files\WinRAR\WinRAR.exe "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ver -imon1 -- "C:\Users\xtea418\Documents\Personal\secret.7z" C:\Users\xtea418\Documents\Personal\ C:\Program Files\WinRAR\WinRAR.exe
*** 2128 3852 SecurityHealth 0xc0832cf1f080 7 - 1 False 2024-11-24 15:01:50.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\SecurityHealthSystray.exe "C:\Windows\System32\SecurityHealthSystray.exe" C:\Windows\System32\SecurityHealthSystray.exe
*** 5236 3852 msedge.exe 0xc0833df74080 52 - 1 False 2024-11-24 15:01:51.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Microsoft\Edge\Application\msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
**** 9184 5236 msedge.exe 0xc0832cce1340 8 - 1 False 2024-11-24 15:01:57.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Microsoft\Edge\Application\msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --string-annotations=is-enterprise-managed=no --field-trial-handle=6164,i,10330629398175313172,2014274514233217906,262144 --variations-seed-version --mojo-platform-channel-handle=6216 /prefetch:8 C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
**** 4708 5236 msedge.exe 0xc0833c1ae080 8 - 1 False 2024-11-24 15:01:51.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Microsoft\Edge\Application\msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\xtea418\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\xtea418\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=131.0.6778.86 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=131.0.2903.63 --initial-client-data=0x260,0x264,0x268,0x25c,0x270,0x7fffcbe66070,0x7fffcbe6607c,0x7fffcbe66088 C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
**** 6148 5236 msedge.exe 0xc083385dc080 12 - 1 False 2024-11-24 15:02:51.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Microsoft\Edge\Application\msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --string-annotations=is-enterprise-managed=no --field-trial-handle=5696,i,10330629398175313172,2014274514233217906,262144 --variations-seed-version --mojo-platform-channel-handle=6948 /prefetch:8 C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
**** 9868 5236 msedge.exe 0xc0833ae64080 8 - 1 False 2024-11-24 15:02:01.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Microsoft\Edge\Application\msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=video_capture.mojom.VideoCaptureService --lang=en-US --service-sandbox-type=none --string-annotations=is-enterprise-managed=no --field-trial-handle=6836,i,10330629398175313172,2014274514233217906,262144 --variations-seed-version --mojo-platform-channel-handle=6524 /prefetch:8 C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
**** 7184 5236 msedge.exe 0xc0833778b0c0 37 - 1 False 2024-11-24 15:01:54.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Microsoft\Edge\Application\msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations=is-enterprise-managed=no --pdf-upsell-enabled --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=4 --enable-main-frame-before-activation --renderer-client-id=8 --field-trial-handle=5032,i,10330629398175313172,2014274514233217906,262144 --variations-seed-version --mojo-platform-channel-handle=5116 /prefetch:1 C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
**** 3828 5236 msedge.exe 0xc0833e6b9080 18 - 1 False 2024-11-24 15:01:51.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Microsoft\Edge\Application\msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --string-annotations=is-enterprise-managed=no --field-trial-handle=2384,i,10330629398175313172,2014274514233217906,262144 --variations-seed-version --mojo-platform-channel-handle=2724 /prefetch:3 C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
**** 3412 5236 msedge.exe 0xc0833824c080 9 - 1 False 2024-11-24 15:01:51.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Microsoft\Edge\Application\msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --string-annotations=is-enterprise-managed=no --field-trial-handle=2772,i,10330629398175313172,2014274514233217906,262144 --variations-seed-version --mojo-platform-channel-handle=2372 /prefetch:8 C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
**** 7284 5236 msedge.exe 0xc0833670c080 10 - 1 False 2024-11-24 15:01:58.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Microsoft\Edge\Application\msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --string-annotations=is-enterprise-managed=no --field-trial-handle=6356,i,10330629398175313172,2014274514233217906,262144 --variations-seed-version --mojo-platform-channel-handle=6240 /prefetch:8 C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
**** 7864 5236 msedge.exe 0xc0833295b0c0 14 - 1 False 2024-11-24 15:01:55.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Microsoft\Edge\Application\msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations=is-enterprise-managed=no --pdf-upsell-enabled --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=4 --enable-main-frame-before-activation --renderer-client-id=11 --field-trial-handle=6008,i,10330629398175313172,2014274514233217906,262144 --variations-seed-version --mojo-platform-channel-handle=6056 /prefetch:1 C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
**** 1884 5236 msedge.exe 0xc0833e6b60c0 29 - 1 False 2024-11-24 15:01:51.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Microsoft\Edge\Application\msedge.exe "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations=is-enterprise-managed=no --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=2252,i,10330629398175313172,2014274514233217906,262144 --variations-seed-version --mojo-platform-channel-handle=2004 /prefetch:2 C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
*** 7508 3852 OneDrive.exe 0xc0833dd8b080 24 - 1 False 2024-11-24 15:01:52.000000 UTC N/A \Device\HarddiskVolume2\Users\xtea418\AppData\Local\Microsoft\OneDrive\OneDrive.exe "C:\Users\xtea418\AppData\Local\Microsoft\OneDrive\OneDrive.exe" /background C:\Users\xtea418\AppData\Local\Microsoft\OneDrive\OneDrive.exe
*** 856 3852 WinRAR.exe 0xc0833ae76080 5 - 1 False 2024-11-24 15:03:00.000000 UTC N/A \Device\HarddiskVolume2\Program Files\WinRAR\WinRAR.exe "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\xtea418\Documents\Personal\secret.7z" C:\Program Files\WinRAR\WinRAR.exe
*** 7900 3852 notepad.exe 0xc083324cc340 4 - 1 False 2024-11-24 15:03:25.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\notepad.exe "C:\Windows\system32\notepad.exe" C:\Windows\system32\notepad.exe
* 1692 924 dwm.exe 0xc08333d4b080 42 - 1 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\dwm.exe "dwm.exe" C:\Windows\system32\dwm.exe
* 996 924 fontdrvhost.ex 0xc0833771d140 5 - 1 False 2024-11-24 15:01:15.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\fontdrvhost.exe "fontdrvhost.exe" C:\Windows\system32\fontdrvhost.exe
7956 7780 chrome.exe 0xc0832cebb0c0 42 - 1 False 2024-11-24 15:01:54.000000 UTC N/A \Device\HarddiskVolume2\Program Files\Google\Chrome\Application\chrome.exe "C:\Program Files\Google\Chrome\Application\chrome.exe" https://www.youtube.com/watch?v=dQw4w9WgXcQ C:\Program Files\Google\Chrome\Application\chrome.exe
* 7808 7956 chrome.exe 0xc0833c1b8080 30 - 1 False 2024-11-24 15:01:55.000000 UTC N/A \Device\HarddiskVolume2\Program Files\Google\Chrome\Application\chrome.exe - -
* 8960 7956 chrome.exe 0xc0833567c080 22 - 1 False 2024-11-24 15:01:57.000000 UTC N/A \Device\HarddiskVolume2\Program Files\Google\Chrome\Application\chrome.exe "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations=is-enterprise-managed=no --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=4 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=4684,i,13128673760615730583,15092746657484269437,262144 --variations-seed-version=20241121-182614.093000 --mojo-platform-channel-handle=4044 /prefetch:1 C:\Program Files\Google\Chrome\Application\chrome.exe
* 9280 7956 chrome.exe 0xc0833ae71080 18 - 1 False 2024-11-24 15:01:58.000000 UTC N/A \Device\HarddiskVolume2\Program Files\Google\Chrome\Application\chrome.exe "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations=is-enterprise-managed=no --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=4 --enable-main-frame-before-activation --renderer-client-id=8 --field-trial-handle=2984,i,13128673760615730583,15092746657484269437,262144 --variations-seed-version=20241121-182614.093000 --mojo-platform-channel-handle=4408 /prefetch:1 C:\Program Files\Google\Chrome\Application\chrome.exe
* 5592 7956 chrome.exe 0xc0833aeca080 17 - 1 False 2024-11-24 15:01:55.000000 UTC N/A \Device\HarddiskVolume2\Program Files\Google\Chrome\Application\chrome.exe "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --string-annotations=is-enterprise-managed=no --field-trial-handle=2292,i,13128673760615730583,15092746657484269437,262144 --variations-seed-version=20241121-182614.093000 --mojo-platform-channel-handle=2308 /prefetch:3 C:\Program Files\Google\Chrome\Application\chrome.exe
* 8560 7956 chrome.exe 0xc0833a1e6080 37 - 1 False 2024-11-24 15:01:56.000000 UTC N/A \Device\HarddiskVolume2\Program Files\Google\Chrome\Application\chrome.exe - -
* 9648 7956 chrome.exe 0xc08337549240 13 - 1 False 2024-11-24 15:02:00.000000 UTC N/A \Device\HarddiskVolume2\Program Files\Google\Chrome\Application\chrome.exe "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations=is-enterprise-managed=no --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=4 --enable-main-frame-before-activation --renderer-client-id=10 --field-trial-handle=3496,i,13128673760615730583,15092746657484269437,262144 --variations-seed-version=20241121-182614.093000 --mojo-platform-channel-handle=4856 /prefetch:1 C:\Program Files\Google\Chrome\Application\chrome.exe
* 9556 7956 chrome.exe 0xc0833aa80080 9 - 1 False 2024-11-24 15:01:59.000000 UTC N/A \Device\HarddiskVolume2\Program Files\Google\Chrome\Application\chrome.exe "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --string-annotations=is-enterprise-managed=no --field-trial-handle=4916,i,13128673760615730583,15092746657484269437,262144 --variations-seed-version=20241121-182614.093000 --mojo-platform-channel-handle=4904 /prefetch:8 C:\Program Files\Google\Chrome\Application\chrome.exe
* 8980 7956 chrome.exe 0xc0833c1ba2c0 8 - 1 False 2024-11-24 15:02:04.000000 UTC N/A \Device\HarddiskVolume2\Program Files\Google\Chrome\Application\chrome.exe "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=video_capture.mojom.VideoCaptureService --lang=en-US --service-sandbox-type=none --string-annotations=is-enterprise-managed=no --field-trial-handle=5668,i,13128673760615730583,15092746657484269437,262144 --variations-seed-version=20241121-182614.093000 --mojo-platform-channel-handle=5656 /prefetch:8 C:\Program Files\Google\Chrome\Application\chrome.exe
* 8056 7956 chrome.exe 0xc0833277c080 8 - 1 False 2024-11-24 15:01:54.000000 UTC N/A \Device\HarddiskVolume2\Program Files\Google\Chrome\Application\chrome.exe "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\xtea418\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\xtea418\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\xtea418\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=131.0.6778.86 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7fffb13afd08,0x7fffb13afd14,0x7fffb13afd20 C:\Program Files\Google\Chrome\Application\chrome.exe
* 7644 7956 chrome.exe 0xc0833295f240 9 - 1 False 2024-11-24 15:01:55.000000 UTC N/A \Device\HarddiskVolume2\Program Files\Google\Chrome\Application\chrome.exe "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --string-annotations=is-enterprise-managed=no --field-trial-handle=2408,i,13128673760615730583,15092746657484269437,262144 --variations-seed-version=20241121-182614.093000 --mojo-platform-channel-handle=2424 /prefetch:8 C:\Program Files\Google\Chrome\Application\chrome.exe
8048 7916 firefox.exe 0xc0833d365080 81 - 1 True 2024-11-24 15:01:54.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" https://www.youtube.com/watch?v=dQw4w9WgXcQ C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 8288 8048 firefox.exe 0xc08338bda080 5 - 1 True 2024-11-24 15:02:05.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc --channel=4692 -parentBuildID 20241110231641 -sandboxingKind 1 -prefsHandle 4864 -prefMapHandle 4696 -prefsLen 38428 -prefMapSize 264507 -win32kLockedDown -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - {0ede9abc-4f99-49eb-a6cc-f1263bd56144} 8048 "\\.\pipe\gecko-crash-server-pipe.8048" 6 utility C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 10180 8048 firefox.exe 0xc083362d2080 5 - 1 True 2024-11-24 15:02:05.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc --channel=5324 -parentBuildID 20241110231641 -sandboxingKind 2 -prefsHandle 5256 -prefMapHandle 4860 -prefsLen 38428 -prefMapSize 264507 -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - {fa1340a4-44d5-494f-8887-3c00664dbd84} 8048 "\\.\pipe\gecko-crash-server-pipe.8048" 8 utility C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 10044 8048 firefox.exe 0xc0833826a080 29 - 1 True 2024-11-24 15:02:05.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc --channel=5616 -isForBrowser -prefsHandle 5608 -prefMapHandle 5604 -prefsLen 34840 -prefMapSize 264507 -jsInitHandle 1480 -jsInitLen 234660 -parentBuildID 20241110231641 -win32kLockedDown -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - {82060315-d777-4f35-b0ac-c5e3bd96304d} 8048 "\\.\pipe\gecko-crash-server-pipe.8048" 9 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 2792 8048 firefox.exe 0xc08332118080 23 - 1 True 2024-11-24 15:03:16.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc --channel=6168 -isForBrowser -prefsHandle 7844 -prefMapHandle 6856 -prefsLen 35082 -prefMapSize 264507 -jsInitHandle 1480 -jsInitLen 234660 -parentBuildID 20241110231641 -win32kLockedDown -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - {9fa3c67f-5244-4f26-8cdf-0bb60ab31b6b} 8048 "\\.\pipe\gecko-crash-server-pipe.8048" 13 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 2536 8048 firefox.exe 0xc08336718080 23 - 1 True 2024-11-24 15:03:16.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc --channel=6724 -isForBrowser -prefsHandle 6880 -prefMapHandle 6268 -prefsLen 35082 -prefMapSize 264507 -jsInitHandle
1480 -jsInitLen 234660 -parentBuildID 20241110231641 -win32kLockedDown -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - {fb9d42e9-cda4-4d3c-8ede-de1e00398649} 8048 "\\.\pipe\gecko-crash-server-pipe.8048" 15 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 10204 8048 firefox.exe 0xc083362b6080 5 - 1 True 2024-11-24 15:02:05.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc --channel=5312 -parentBuildID 20241110231641 -sandboxingKind 0 -prefsHandle 5072 -prefMapHandle 5068 -prefsLen 38428 -prefMapSize 264507 -win32kLockedDown -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - {4e91db02-535c-40b0-9134-9157309d7e79} 8048 "\\.\pipe\gecko-crash-server-pipe.8048" 7 utility C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 10348 8048 firefox.exe 0xc0833af6c080 29 - 1 True 2024-11-24 15:02:06.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc --channel=5880 -isForBrowser -prefsHandle 5872 -prefMapHandle 5864 -prefsLen 34889 -prefMapSize 264507 -jsInitHandle 1480 -jsInitLen 234660 -parentBuildID 20241110231641 -win32kLockedDown -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - {9002c5f1-2b5e-4f37-98c6-955ec9eb650c} 8048 "\\.\pipe\gecko-crash-server-pipe.8048" 10 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 8252 8048 firefox.exe 0xc08338c790c0 5 - 1 True 2024-11-24 15:02:05.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc --channel=2620 -parentBuildID 20241110231641 -prefsHandle 4860 -prefMapHandle 4504 -prefsLen 38428 -prefMapSize 264507 -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - {73205a14-b8b7-4284-8bec-ef193c5aca4e} 8048 "\\.\pipe\gecko-crash-server-pipe.8048" 5 rdd C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 9392 8048 firefox.exe 0xc08337566080 33 - 1 True 2024-11-24 15:01:59.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe - -
* 10864 8048 firefox.exe 0xc08336735080 23 - 1 True 2024-11-24 15:03:16.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc --channel=7856 -isForBrowser -prefsHandle 7832 -prefMapHandle 7836 -prefsLen 35082 -prefMapSize 264507 -jsInitHandle 1480 -jsInitLen 234660 -parentBuildID 20241110231641 -win32kLockedDown -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - {6dec9cba-024f-4cd1-a181-5b1404f18b2e} 8048 "\\.\pipe\gecko-crash-server-pipe.8048" 14 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 9204 8048 firefox.exe 0xc08333678080 8 - 1 True 2024-11-24 15:01:58.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc --channel=2376 -parentBuildID 20241110231641 -prefsHandle 2372 -prefMapHandle 2368 -prefsLen 31744 -prefMapSize 264507 -win32kLockedDown -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - {abdadc28-fc56-4ed3-89ef-81904ec69c20} 8048 "\\.\pipe\gecko-crash-server-pipe.8048" 2 socket C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 10868 8048 firefox.exe 0xc08339005080 29 - 1 True 2024-11-24 15:02:09.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc --channel=7020 -isForBrowser -prefsHandle 7000 -prefMapHandle 6128 -prefsLen 38670 -prefMapSize 264507 -jsInitHandle 1480 -jsInitLen 234660 -parentBuildID 20241110231641 -win32kLockedDown -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - {c6ccdb59-1e51-4643-9812-8614761afa10} 8048 "\\.\pipe\gecko-crash-server-pipe.8048" 12 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 9944 8048 firefox.exe 0xc08332aa3240 28 - 1 True 2024-11-24 15:02:02.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc --channel=4516 -isForBrowser -prefsHandle 4524 -prefMapHandle 4520 -prefsLen 38428 -prefMapSize 264507 -jsInitHandle 1480 -jsInitLen 234660 -parentBuildID 20241110231641 -win32kLockedDown -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - {d32fca1b-a59e-4f31-8441-c3e37ad6db73} 8048 "\\.\pipe\gecko-crash-server-pipe.8048" 4 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 9148 8048 firefox.exe 0xc08332774240 26 - 1 True 2024-11-24 15:01:57.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc --channel=1992 -parentBuildID 20241110231641 -prefsHandle 1908 -prefMapHandle 1900 -prefsLen 31744 -prefMapSize 264507 -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - {b8081fe9-9b76-41a6-8ab6-23ccbfa34a7f} 8048 "\\.\pipe\gecko-crash-server-pipe.8048" 1 gpu C:\Program Files (x86)\Mozilla Firefox\firefox.exe
There’s a couple nice Easter eggs, like both Chrome and Firefox watching the Rick Roll video. There’s also a few WinRAR.exe processes interacting with a secret.7z. For example:
*** 856 3852 WinRAR.exe 0xc0833ae76080 5 - 1 False 2024-11-24 15:03:00.000000 UTC N/A \Device\HarddiskVolume2\Program Files\WinRAR\WinRAR.exe "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\xtea418\Documents\Personal\secret.7z" C:\Program Files\WinRAR\WinRAR.exe
I’ll see if I can pull the archive from memory, starting with filescan.FileScan:
oxdf@hacky$ vol -f dump.raw windows.filescan.FileScan > filescan.FileScan
oxdf@hacky$ cat filescan.FileScan | grep -i secret
0xc08339350e20 \Users\xtea418\Documents\Personal\secret.7z
0xc0833cb64b40 \Users\xtea418\Documents\Personal\secret.7z
0xc0833cb65e00 \Users\xtea418\Documents\Personal\secret.7z
I’ll pull one of these (it doesn’t matter which one, all work and provide the same) from memory with dumpfiles.DumpFiles:
oxdf@hacky$ vol -f dump.raw windows.dumpfiles.DumpFiles --virtaddr 0xc0833cb65e00
Volatility 3 Framework 2.8.0
Progress: 100.00 PDB scanning finished
Cache FileObject FileName Result
DataSectionObject 0xc0833cb65e00 secret.7z Error dumping file
SharedCacheMap 0xc0833cb65e00 secret.7z file.0xc0833cb65e00.0xc08338120a20.SharedCacheMap.secret.7z.vacb
Despite the error message, this makes two files:
oxdf@hacky$ file file.0xc0833cb65e00.0xc0833*
file.0xc0833cb65e00.0xc08338120a20.SharedCacheMap.secret.7z.vacb: 7-zip archive data, version 0.4
file.0xc0833cb65e00.0xc0833c619ed0.DataSectionObject.secret.7z.dat: 7-zip archive data, version 0.4
Trying to extract either asks for a password.
I’ll use 7z2john.pl to make a hash (either one works):
oxdf@hacky$ 7z2john.pl file.0xc0833cb65e00.0xc08338120a20.SharedCacheMap.secret.7z.vacb | tee file.extracted.7z.hash
ATTENTION: the hashes might contain sensitive encrypted data. Be careful when sharing or posting these hashes
file.0xc0833cb65e00.0xc08338120a20.SharedCacheMap.secret.7z.vacb:$7z$1$19$0$$16$bbdbbf3fa3bf8efcdc05153543d31569$433149696$144$140$b0786fd9d9562032270c06f5ce5a2b0f22c76b4bd6ed13b94da50d7c4756fa4c2cdb5c08b4d8a5ec26a7872bc076c2b2ad88c31a5e153dd99658ba5825c22fba90ef6f2b30cfbdb8fb538980c15493a094c82576a8259822b232c0c787f9481ea556ae50c51af6ea3016891025b44bc2c4c262a1d4a29afcddd080f65d747b47f78a4b41aa35263a908d551789595f36$166$5d00100000
Now hashcat with rockyou.txt cracks it:
$ hashcat ./file.extracted.7z.hash /opt/SecLists/Passwords/Leaked-Databases/rockyou.txt --user
hashcat (v6.2.6) starting in autodetect mode
...[snip]...
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
11600 | 7-Zip | Archive
...[snip]...
$7z$1$19$0$$16$bbdbbf3fa3bf8efcdc05153543d31569$433149696$144$140$b0786fd9d9562032270c06f5ce5a2b0f22c76b4bd6ed13b94da50d7c4756fa4c2cdb5c08b4d8a5ec26a7872bc076c2b2ad88c31a5e153dd99658ba5825c22fba90ef6f2b30cfbdb8fb538980c15493a094c82576a8259822b232c0c787f9481ea556ae50c51af6ea3016891025b44bc2c4c262a1d4a29afcddd080f65d747b47f78a4b41aa35263a908d551789595f36$166$5d00100000:santa1
...[snip]...
With that password “santa1”, I can list and extract the archive:
oxdf@hacky$ 7z l file.0xc08339350e20.0xc08338120a20.SharedCacheMap.secret.7z.vacb
7-Zip 23.01 (x64) : Copyright (c) 1999-2023 Igor Pavlov : 2023-06-20
64-bit locale=en_US.UTF-8 Threads:12 OPEN_MAX:1024
Scanning the drive for archives:
1 file, 262144 bytes (256 KiB)
Listing archive: file.0xc08339350e20.0xc08338120a20.SharedCacheMap.secret.7z.vacb
Enter password (will not be echoed): ...[snip]...
Date Time Attr Size Compressed Name
------------------- ----- ------------ ------------ ------------------------
2024-11-24 14:42:51 D.... 0 0 secret
2024-11-24 14:42:51 ....A 67260 65024 secret/image.jpg
------------------- ----- ------------ ------------ ------------------------
2024-11-24 14:42:51 67260 65024 1 files, 1 folders
Warnings: 1
The image just is another meme:

But there is a flag in the Exif data:
oxdf@hacky$ exiftool secret/image.jpg
ExifTool Version Number : 12.76
File Name : image.jpg
Directory : secret
File Size : 67 kB
File Modification Date/Time : 0000:00:00 00:00:00
File Access Date/Time : 0000:00:00 00:00:00
File Inode Change Date/Time : 2024:12:05 01:26:10+00:00
File Permissions : -rwxrwx---
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
XMP Toolkit : Image::ExifTool 13.03
Description : HV24{t0t4lly_s3cur3_p4ssw0rd_l1k3_4ctu4lly_s0_v3ry_much_s3cur3}
Image Width : 500
Image Height : 500
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 500x500
Megapixels : 0.250
Flag: HV24{t0t4lly_s3cur3_p4ssw0rd_l1k3_4ctu4lly_s0_v3ry_much_s3cur3}
HV24.HM
Challenge
| HV24.HM Mrs. Claus's Secret | |
|---|---|
| Categories: |
|
| Level: | medium |
| Author: | xtea418 |
Mrs. Claus said that she hid another flag in one of the medium. Do not tell Santa Claus!!
Solution
Recover Password
While the secret.7z file jumped out immediately from the running processes in the memory dump, there’s also another interesting process running:
*** 7900 3852 notepad.exe 0xc083324cc340 4 - 1 False 2024-11-24 15:03:25.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\notepad.exe "C:\Windows\system32\notepad.exe" C:\Windows\system32\notepad.exe
This post explains a custom Volatility plugin for notepad.exe (as well as a couple others) to read the data. The plugin is on GitHub. I’ll download that Python script and save it in my Volatility plugins directory. To find that, I’ll run vol -v, and it’s on the first line:
oxdf@hacky$ vol -v
Volatility 3 Framework 2.8.0
INFO volatility3.cli: Volatility plugins path: ['/home/oxdf/.local/share/pipx/venvs/volatility3/lib/python3.12/site-packages/volatility3/plugins', '/home/oxdf/.local/share/pipx/venvs/volatility3/lib/python3.12/site-packages/volatility3/framework/plugins']
...[snip]...
Since I installed vol using pipx, it’s in that directory. I’ll save notepad.py in one of those directories, and then when I run vol --help to list plugins, it’s there:
oxdf@hacky$ vol --help | grep windows.notepad
{banners.Banners,configwriter.ConfigWriter,frameworkinfo.FrameworkInfo,isfinfo.IsfInfo,layerwriter.LayerWriter,linux.bash.Bash,linux.capabilities.Capabilities,linux.check_afinfo.Check_afinfo,linux.check_creds.Check_creds,linux.check_idt.Check_idt,linux.check_modules.Check_modules,linux.check_syscall.Check_syscall,linux.elfs.Elfs,linux.envars.Envars,linux.iomem.IOMem,linux.keyboard_notifiers.Keyboard_notifiers,linux.kmsg.Kmsg,linux.library_list.LibraryList,linux.lsmod.Lsmod,linux.lsof.Lsof,linux.malfind.Malfind,linux.mountinfo.MountInfo,linux.netfilter.Netfilter,linux.proc.Maps,linux.psaux.PsAux,linux.pslist.PsList,linux.psscan.PsScan,linux.pstree.PsTree,linux.sockstat.Sockstat,linux.tty_check.tty_check,mac.bash.Bash,mac.check_syscall.Check_syscall,mac.check_sysctl.Check_sysctl,mac.check_trap_table.Check_trap_table,mac.dmesg.Dmesg,mac.ifconfig.Ifconfig,mac.kauth_listeners.Kauth_listeners,mac.kauth_scopes.Kauth_scopes,mac.kevents.Kevents,mac.list_files.List_Files,mac.lsmod.Lsmod,mac.lsof.Lsof,mac.malfind.Malfind,mac.mount.Mount,mac.netstat.Netstat,mac.proc_maps.Maps,mac.psaux.Psaux,mac.pslist.PsList,mac.pstree.PsTree,mac.socket_filters.Socket_filters,mac.timers.Timers,mac.trustedbsd.Trustedbsd,mac.vfsevents.VFSevents,timeliner.Timeliner,vmscan.Vmscan,windows.bigpools.BigPools,windows.callbacks.Callbacks,windows.cmdline.CmdLine,windows.crashinfo.Crashinfo,windows.devicetree.DeviceTree,windows.dlllist.DllList,windows.driverirp.DriverIrp,windows.drivermodule.DriverModule,windows.driverscan.DriverScan,windows.dumpfiles.DumpFiles,windows.envars.Envars,windows.filescan.FileScan,windows.getservicesids.GetServiceSIDs,windows.getsids.GetSIDs,windows.handles.Handles,windows.hollowprocesses.HollowProcesses,windows.iat.IAT,windows.info.Info,windows.joblinks.JobLinks,windows.kpcrs.KPCRs,windows.ldrmodules.LdrModules,windows.malfind.Malfind,windows.mbrscan.MBRScan,windows.memmap.Memmap,windows.modscan.ModScan,windows.modules.Modules,windows.mutantscan.MutantScan,windows.netscan.NetScan,windows.netstat.NetStat,windows.notepad.Notepad,windows.pedump.PEDump,windows.poolscanner.PoolScanner,windows.privileges.Privs,windows.processghosting.ProcessGhosting,windows.pslist.PsList,windows.psscan.PsScan,windows.pstree.PsTree,windows.psxview.PsXView,windows.registry.certificates.Certificates,windows.registry.getcellroutine.GetCellRoutine,windows.registry.hivelist.HiveList,windows.registry.hivescan.HiveScan,windows.registry.printkey.PrintKey,windows.registry.userassist.UserAssist,windows.sessions.Sessions,windows.shimcachemem.ShimcacheMem,windows.skeleton_key_check.Skeleton_Key_Check,windows.ssdt.SSDT,windows.statistics.Statistics,windows.strings.Strings,windows.suspicious_threads.SupsiciousThreads,windows.symlinkscan.SymlinkScan,windows.thrdscan.ThrdScan,windows.threads.Threads,windows.timers.Timers,windows.truecrypt.Passphrase,windows.unloadedmodules.UnloadedModules,windows.vadinfo.VadInfo,windows.vadwalk.VadWalk,windows.verinfo.VerInfo,windows.virtmap.VirtMap}
{banners.Banners,configwriter.ConfigWriter,frameworkinfo.FrameworkInfo,isfinfo.IsfInfo,layerwriter.LayerWriter,linux.bash.Bash,linux.capabilities.Capabilities,linux.check_afinfo.Check_afinfo,linux.check_creds.Check_creds,linux.check_idt.Check_idt,linux.check_modules.Check_modules,linux.check_syscall.Check_syscall,linux.elfs.Elfs,linux.envars.Envars,linux.iomem.IOMem,linux.keyboard_notifiers.Keyboard_notifiers,linux.kmsg.Kmsg,linux.library_list.LibraryList,linux.lsmod.Lsmod,linux.lsof.Lsof,linux.malfind.Malfind,linux.mountinfo.MountInfo,linux.netfilter.Netfilter,linux.proc.Maps,linux.psaux.PsAux,linux.pslist.PsList,linux.psscan.PsScan,linux.pstree.PsTree,linux.sockstat.Sockstat,linux.tty_check.tty_check,mac.bash.Bash,mac.check_syscall.Check_syscall,mac.check_sysctl.Check_sysctl,mac.check_trap_table.Check_trap_table,mac.dmesg.Dmesg,mac.ifconfig.Ifconfig,mac.kauth_listeners.Kauth_listeners,mac.kauth_scopes.Kauth_scopes,mac.kevents.Kevents,mac.list_files.List_Files,mac.lsmod.Lsmod,mac.lsof.Lsof,mac.malfind.Malfind,mac.mount.Mount,mac.netstat.Netstat,mac.proc_maps.Maps,mac.psaux.Psaux,mac.pslist.PsList,mac.pstree.PsTree,mac.socket_filters.Socket_filters,mac.timers.Timers,mac.trustedbsd.Trustedbsd,mac.vfsevents.VFSevents,timeliner.Timeliner,vmscan.Vmscan,windows.bigpools.BigPools,windows.callbacks.Callbacks,windows.cmdline.CmdLine,windows.crashinfo.Crashinfo,windows.devicetree.DeviceTree,windows.dlllist.DllList,windows.driverirp.DriverIrp,windows.drivermodule.DriverModule,windows.driverscan.DriverScan,windows.dumpfiles.DumpFiles,windows.envars.Envars,windows.filescan.FileScan,windows.getservicesids.GetServiceSIDs,windows.getsids.GetSIDs,windows.handles.Handles,windows.hollowprocesses.HollowProcesses,windows.iat.IAT,windows.info.Info,windows.joblinks.JobLinks,windows.kpcrs.KPCRs,windows.ldrmodules.LdrModules,windows.malfind.Malfind,windows.mbrscan.MBRScan,windows.memmap.Memmap,windows.modscan.ModScan,windows.modules.Modules,windows.mutantscan.MutantScan,windows.netscan.NetScan,windows.netstat.NetStat,windows.notepad.Notepad,windows.pedump.PEDump,windows.poolscanner.PoolScanner,windows.privileges.Privs,windows.processghosting.ProcessGhosting,windows.pslist.PsList,windows.psscan.PsScan,windows.pstree.PsTree,windows.psxview.PsXView,windows.registry.certificates.Certificates,windows.registry.getcellroutine.GetCellRoutine,windows.registry.hivelist.HiveList,windows.registry.hivescan.HiveScan,windows.registry.printkey.PrintKey,windows.registry.userassist.UserAssist,windows.sessions.Sessions,windows.shimcachemem.ShimcacheMem,windows.skeleton_key_check.Skeleton_Key_Check,windows.ssdt.SSDT,windows.statistics.Statistics,windows.strings.Strings,windows.suspicious_threads.SupsiciousThreads,windows.symlinkscan.SymlinkScan,windows.thrdscan.ThrdScan,windows.threads.Threads,windows.timers.Timers,windows.truecrypt.Passphrase,windows.unloadedmodules.UnloadedModules,windows.vadinfo.VadInfo,windows.vadwalk.VadWalk,windows.verinfo.VerInfo,windows.virtmap.VirtMap}
windows.notepad.Notepad
This plugin will output a bunch of data about the running notepad.exe instance:
oxdf@hacky$ vol -f dump.raw windows.notepad.Notepad
Volatility 3 Framework 2.8.0
Progress: 100.00 PDB scanning finished
PID Image Probable Strings
7900 notepad.exe 0 5 ` ` l 3 ( $ $ * , 0 =::=::\ ALLUSERSPROFILE=C:\ProgramData APPDATA=C:\Users\xtea418\AppData\Roaming CommonProgramFiles=C:\Program Files\Common Files CommonProgramFiles(x86)=C:\Program Files (x86)\Common Files CommonProgramW6432=C:\Program Files\Common Files COMPUTERNAME=DESKTOP-MB2MGE7 ComSpec=C:\Windows\system32\cmd.exe DriverData=C:\Windows\System32\Drivers\DriverData FPS_BROWSER_APP_PROFILE_STRING=Internet Explorer FPS_BROWSER_USER_PROFILE_STRING=Default HOMEDRIVE=C: HOMEPATH=\Users\xtea418 LOCALAPPDATA=C:\Users\xtea418\AppData\Local LOGONSERVER=\\DESKTOP-MB2MGE7 NUMBER_OF_PROCESSORS=23 OneDrive=C:\Users\xtea418\OneDrive OS=Windows_NT Path=C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Users\xtea418\AppData\Local\Microsoft\WindowsApps; PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC PROCESSOR_ARCHITECTURE=AMD64 PROCESSOR_IDENTIFIER=AMD64 Family 25 Model 97 Stepping 2, AuthenticAMD PROCESSOR_LEVEL=25 PROCESSOR_REVISION=6102 ProgramData=C:\ProgramData ProgramFiles=C:\Program Files ProgramFiles(x86)=C:\Program Files (x86) ProgramW6432=C:\Program Files PSModulePath=C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules PUBLIC=C:\Users\Public SESSIONNAME=Console SystemDrive=C: SystemRoot=C:\Windows TEMP=C:\Users\xtea418\AppData\Local\Temp TMP=C:\Users\xtea418\AppData\Local\Temp USERDOMAIN=DESKTOP-MB2MGE7 USERDOMAIN_ROAMINGPROFILE=DESKTOP-MB2MGE7 USERNAME=xtea418 USERPROFILE=C:\Users\xtea418 windir=C:\Windows " @ >@ DF C:\Users\xtea418\ C:\Windows\system32\notepad.exe "C:\Windows\system32\notepad.exe" C:\Users\xtea418\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar\Notepad.lnk Winsta0\Default C:\Windows\SYSTEM32\ntdll.dll C:\Windows\System32 C:\Windows\SYSTEM32;C:\Windows\system;C:\Windows; :< >@ @ rs" te C:\Users\xtea418\ PROCESSOR_IDENTIFIER=AMD64 Family 25 Model 97 Stepping 2, AuthenticAMD GDI32.dll @B C:\Windows\System32\KERNEL32.DLL ` PSModulePath=C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules / DF C:\Windows\System32\KERNELBASE.dll 0 \Sessions\1\Windows\ApiPortection ! D H T X ` ` 6 \ \ ` ` ` l A h d t p x :< C:\Windows\System32\GDI32.dll <> C:\Windows\System32\win32u.dll 2 C:\Windows\SYSTEM32\gdi32full.dll BD 0 T C:\Windows\System32\gdi32full.dll PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC msvcp_win.dll BD C:\Windows\System32\msvcp_win.dll CommonProgramW6432=C:\Program Files\Common Files DriverData=C:\Windows\System32\Drivers\DriverData C:\Windows\SYSTEM32\ucrtbase.dll @B C:\Windows\System32\ucrtbase.dll CommonProgramFiles(x86)=C:\Program Files (x86)\Common Files FPS_BROWSER_APP_PROFILE_STRING=Internet Explorer ER ll <> C:\Windows\System32\USER32.dll a !@ ! @@a A `` ` ! ! ! ! ! c ! ! a B ! ! ! ! ! ! @ ! ! ! ! ! ! @ C ` ` : a 8 5 >@ C:\Windows\System32\combase.dll ` ` : 7 s s e t ) ) = 2 > ) h <> PROCESSOR_ARCHITECTURE=AMD64 ProgramFiles=C:\Program Files ProgramW6432=C:\Program Files COMPUTERNAME=DESKTOP-MB2MGE7 ComSpec=C:\Windows\system32\cmd.exe C:\Windows\System32\shcore.dll 0 C:\Windows\System32\msvcrt.dll s C:\Windows\System32\IMM32.DLL F P ALLUSERSPROFILE=C:\ProgramData C:\Windows\System32\RPCRT4.dll 0 C F P C:\Windows\system32\resources.pri 0 LOGONSERVER=\\DESKTOP-MB2MGE7 OneDrive=C:\Users\xtea418\OneDrive 0 C:\Windows\S TEM32\kernel.appcore.dll <> d - Notepad ll <> CommonProgramFiles=C:\Program Files\Common Files C:\Windows\WinSxS\amd64_microsoft.windows.common-controls_6595b64144ccf1df_6.0.19041.4355_none_60b8b9eb71f62e16\ PR (* ) TMP=C:\Users\xtea418\AppData\Local\Temp onlyallowmicrosoftsignedbinaries USERDOMAIN_ROAMINGPROFILE=DESKTOP-MB2MGE7 restrictindirectbranchprediction APPDATA=C:\Users\xtea418\AppData\Roaming LOCALAPPDATA=C:\Users\xtea418\AppData\Local FPS_BROWSER_USER_PROFILE_STRING=Default ProgramFiles(x86)=C:\Program Files (x86) C:\Windows\System32\bcryptPrimitives.dll C:\Windows\system32\notepad.exe enforcesigninglevelfordependentmodules TEMP=C:\Users\xtea418\AppData\Local\Temp allowthreadsoptoutofarbitrarycodeguard C:\Windows\WinSxS\amd64_microsoft.windows.common-controls_6595b64144ccf1df_6.0.19041.4355_none_60b8b9eb71f62e16\COMCTL32.dll Path=C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Users\xtea418\AppData\Local\Microsoft\WindowsApps; C C C C SystemDrive=C: Data mandatoryaslr p OS=Windows_NT HOMEDRIVE=C: returnflowguard PROCESSOR_LEVEL=25 ow 32\W highentropyaslr ropsimexec win32kfiltering \Win / OM;. VBE; / MSC / RE=A IFIE / del / ntic / / 02 P bottomupaslr (x86 / x86) USERNAME=xtea418 SESSIONNAME=Console ndow PowerS prefersystem32 strictcfg / rive s TEMP=C 7 ? C :< ((((( H ; ((((( H ;L _MONETAR C ME 0 C ((((( H 4 codeintegrityguard dep 3 ProgramData=C:\ProgramData advancedprotections sehop browser nx 3 = Size UTF-8 d Plan 100% Plan OANO @ 52C64B7E P ) > blocklowlabelimageloads exportaddressfilter " ropstackpivotdetection disableextensionpoints importaddressfilter stricthandlechecks ( / arbitrarycodeguard ropcallerdetection % controlflowguard exportaddressfilterplus devicecapabilitycamera blockremoteimageloads ' & ' ' # cfg + / $ & ' ! ropgadgetdetection acg ) C:\Windows\system32\windows.storage.dll 2 7 C:\Windows\SYSTEM32\kernel.appcore.dll C:\Windows\System32\twinapi.appcore.dll ms-cortana://Insights C:\Windows\SYSTEM32\windows.storage.dll mp F 735E5ED6-4ABD-41d1-A315-4788CC6357FB C:\Windows\system32\windows.storage.dll C:\Windows\System32\twinapi.appcore.dll 3 7 4-1001 y\User\S-1-5-21-3909435439-193066570 Cl) Y - / T Local AppData m32 AppData\Local T C:\W tem32 T T Y24k8UPs $ ) 5 > 2 # 2 ) 1 = nage n Windows.ApplicationModel.Resources.Core.ResourceManager @ @ E 7 Windows.ApplicationModel.Resources.Core.ResourceManager " > TextQuery C:\Windows\System32\MPR.dll Kerberos NT AUTHORITY\LOCAL SERVICE NT Authority\NetworkService 8 WindowsRetailDemo WebUrl al p] 4 up] DESKTOP-MB2MGE7 t MSAA AccPropServices ImageBytes Negotiate MSCTFIME::Function Provider NegoExtender oso MSAA AccPropServices kup] ( RequestId Insights Schannel en-US MSCTFIME UI 6 ( 2 C:\Windows\system32\resources.pri C:\Windows\System32\MSCTF.dll 0 \xtea418\AppData\Local C:\Users\xtea418\AppData\Local anel to verify that the printer is configured properly. Cannot print the %% file. Be sure that your printer is connected properly and use Control Panel to verify that the printer is configured properly. Not a valid file name. Cannot create the %% file. Make sure that the path and file name are correct. Cannot carry out the Word Wrap command because there is too much text in the file. %% notepad.hlp Text Documents (*.txt) All Files Open Save As You cannot shut down or log off Windows because the Save As dialog box in Notepad is open. Switch to Notepad, close this dialog box, and then try shutting down or logging off Windows again. Cannot access your printer. Be sure that your printer is connected properly and use Control Panel to verify that the printer is configured properly. %% You do not have permission to open this file. See the owner of the file or an administrator to obtain permission. %% This file contains characters in Unicode format which will be lost if you save this file as an ANSI encoded text file. To keep the Unicode information, click Cancel below and then select one of the Unicode options from the Encoding drop down list. Continue? Common Dialog error (0x%04x) Page too small to print one line. Try printing using smaller font. Notepad - Goto Line The line number is beyond the total number of lines Auto-Detect ANSI UTF-16 LE UTF-16 BE UTF-8 UTF-8 with BOM Page %d &f Page &p Ln %d, Col %d Compressed, Encrypted, Hidden, Offline, ReadOnly, System, File fFpPtTdDcCrRlL &Encoding: Notepad was running in a transaction which has completed. Would you like to save the %% file non-transactionally? Text Editor Status Bar We can t open this file Either your organization doesn t allow it, or there s a problem with the file s encryption. Windows (CRLF) Unix (LF) Macintosh (CR) Found next from the bottom Found next from the top %d%% %s r G F " k" Cortana-AppToApp-ObjectInsights 6 6 6 @ 6 ; Z x < [ y ` DESKTOP-MB2MGE7\xtea418 1 ` P Local\1ImmersiveFocusTrackingActiveEvent ! C 1 n Wind 4 @ ; A 9 7 ? d c J 6 D < = C 6 7 a 6 6 6 ! " # $ ' ( + , 1 2 6 1 2 6 6 !"#$%&'()*+,-./012345 p !"#$%&'()*+,-./012345 p ! " # $ % & ' ( ) * + , - . / 0 1 2 3 4 5 0 6 6 6 6 0 $ $ % % & & ' ' ( ) ) * * + , - - . . / / 0 1 2 2 3 3 4 4 5 5 6 6 7 7 8 8 9 9 : : ; ; < < = = > @ ^ ` b b c c d d e f g g h h Segoe UI 0 0g @ Windows.Security.EnterpriseData.ProtectionPolicyManagerPrivatePT 8 @ Windows.Security.EnterpriseData.ProtectionPolicyManagerPrivatePT dll s Unicod ( .TTC,MS X LI SU 8 .T h TC .T ( He x os ( GUN. $ O:BAG:BAD:(A;;CCDCLC;;;PS)(A;;CCDC;;;SY)(A;;CCDCLC;;;BA)(A;;0x3;;;AC)(A;;0x3;;;S-1-15-3-1024-2405443489-874036122-4286035555-1823921565-1746547431-2453885448-3625952902-991631256) FH <> >@ :< 5 PR (* @B 68 <> NP &( @ Security-SPP-GenuineLocalStatus " * TV ,. JL "$ <> 1 " * 0 e " $ % & ' ( ) * + , - . / 0 1 2 3 4 5 6 7 8 9 : ; < = B D E F G H I J K L M N O P Q R S T U V W X Y Z [ \ ] b c d e f g h i j k l m n o p q r s t u v w x y z { } V 6 3 9: 3 !"37 3 36 3 ' ()*,45: 3 36 6 ! !2 ! !5 ! !2 ! !5 !2 ! !2 3 " "%& " #$ " " " " ! " 3 " 3 ! 3 " 3 ! " 3 36 " ! 3 36 ! !5 ! " ! " ! " ! " ! " ! " ! " 3 ! " !5 ! " ! " ! " ! " ! " ! "6 ! " ! " ! " !6 "6 ! " ! " ! " ! " ! " ! " ! " ! " ! "6 ! " ! " ! " ! " 3 !5 " 6 ! " ! " ! " ! " ! " ! " ! " ! " !6 "6 ! " ! " !5 " !5 " !5 " !5 " ! " !6 "6 ! " !6 "6 ! " ! " ! " !6 "6 ! " ! " ! " ! " ! " ! " ! " ! " ! " ! " ! " ! " ! " ! " ! " 36 3 6 5 5 5 5 !6 "6 c 5 6 5 5 c 5 5 3 e e e UX_d 3 ! 3 XYbd STXYd XYd XYbd XYd Xd Xabd Xd Xcd Xabd MNXZd XZd XZ\d XZd Xd XZd RXZd XZ`d XZd XZ^d Xd XZd Xd WXZd XZd OXd XZd Xd XZd XZ[d XZd Xd X^d Xd X[d Xd XYd Xabd Xd Xabd Xd PXd Xd Xabd Xd QXabd Xabd Xd Xabd Xd Y] Xd 0145 ./45 +-459 & 5 ; = < > ? @ A B C D E F G H I J K L 8 Xd I $ % & ' ( ) * + , - . / 0 1 2 3 4 5 6 7 8 9 : ; < = > @ ^ ` b c d e f g h -/ - -/7 -/ - -/ - ! - )*+,.01 " 8 )*+,.01 - ).01 "#$% "(56 ).01 "(56 " ).234 ).01 "(56 " "(56 "56 "&'56 "(56 )01 ).01 "(56 "#$%56 ).01 "(56 ).234 "# "(56 "(56 9:;<=>? @ABCDEFGHI Windows.Security.EnterpriseData.ProtectionPolicyManagerPrivatePT E Z Windows.ApplicationModel.Core.CoreApplicationon ; com.microsoft.services.cortana.cortanaactionableinsights_v1 x 7 Windows.Security.EnterpriseData.ProtectionPolicyManager 0 0 Ete 2\ e. nna give you my last p < & , 0 4 7 8 ` ` E ` Wi App - Windows.ApplicationModel.Core.CoreApplication indows\S T Windows.Foundation.Collections.PropertySetet H a T R W L ^ ` K df_6.0.19041.4355_none_60b8b9eb71f62e16\ M A _ N V b T Feature com.microsoft.services.cortana.cortanaactionableinsights_v1 is not available 2 : C:\Windows\System32\oleacc.dll H Ac tableClass H C:\Windows\System32\WinTypes.dll H H C:\Windows\System32\WinTypes.dll ,.0 H H C:\Windows\System32\oleacc.dll C:\Windows\System32\oleacc.dll H H C:\Windows\System32\WinTypes.dll H OLE5B0E6D3862702E37419E94E23FA8 C:\Windows\system32\OLEACCRC.DLL 2 C:\Windows\System32\WinTypes.dll C:\Windows\System32\oleacc.dll H H 0 C C C C C : % " 5 5 6 6 c 5 3 3 3 3 e ) \RPC p T Ptype_PSFactory NTLM DESKTOP-MB2MGE7 WinSta0\Default TSSSP lsapolicylookup Ptype_PSFactory T NT AUTHORITY\SYSTEM pku2u DESKTOP-MB2MGE7 d ` & $ $ & & E & * Windows.Foundation.Collections.PropertySet = c epma c epmapper epmapper ncal ncal epmapper ncal NPCTXT epmapper epmapper epmapper ncalrpc & A TSA: & & ( @ @ 3 10.0.2.15 Q Negotiate NegoExtender Kerberos NTLM TSSSP pku2u Schannel \ l H \ l H 8 8 8 @ t -+ncalrpc:[OLE5B0E6D3862702E37419E94E23FA8] * ( @ Machine\SOFTWA \Policies\Microsoft\Windows\Ap DESKTOP-MB2MGE7\xtea418 @ 3 DESKTOP-MB2MGE7 10.0.2.15 p p P DESKTOP- 8 8 \ l H D !" \ l H 8 8 8 8 8 8 @ \ DESKTOP-MB2MGE7 xtea418 y\Machine\Software\Classes\AppID\notepad.exe 564-1001_Classes\AppID\notepad.exe T ' System\RemoteTextInputProcessorDefault1 Syst \R eTex np oces rD lt1 ' ' System\RemoteTextInputProcessorDefault1 3 DESKTOP-MB2MGE7 10.0.2.15 d 3 DESKTOP-MB2MGE7 10.0.2.15 E ; ; 3 DESKTOP-MB2MGE7 10.0.2.15 *Untitled - Notepad eNamedObjects\CoreMessagingRegistrar " " {0}\[CoreUI]-PID({1})-TID({2}) {3} ;;BA) X C 54 ` d32 8 8 8 \REGISTRY\USER\S-1-5-21-3909435439-1930665703-3246598564-1001_Classes q 9 ` ` $ $ ) ) # = 2 ) 2 > 5 ; ) ! ) ) 8 ! ` @ ) P L ExternalObjectOwner 0 L MSAA_*FCFFFFFF00000000 MSAA_*FCFFFFFF00000000 C:\Windows\System32\CoreMessaging.dll C:\Windows\System32\CoreUIComponents.dll P C:\Windows\SYSTEM32\textinputframework.dll 8 C ` @ C C C C 8 C ` @ 8 C ` @ 8 ( @ Hp C C C C p 0665703- CLSID\{11659A23-5884-4D1B-9CF6-67D6F4F90B36} cf6 eat P O O O O ) O ` ` ` ` 0665703- CLSID\{B5F8350B-0548-48B1-A6EE-88BD00B4A5E7} 6ee eat 0665703- CLSID\{B5F8350B-0548-48B1-A6EE-88BD00B4A5E7} 6ee eat ) Windows (CRLF) C @ Local\ Bar V @ y @ H @ Ln 1, Col 1 T Status Bar . @ Text Editor Local\1 ` !"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrstuvwxyz{ } ` ` 6 = Edit WinS 6 Defa las ` X notepad.exe % 2 H H H H H H H C:\Windows\SYSTEM32\ntmarta.dll H 9 0 H { C:\Windows\System32\WS2_32.dll CoreMessaging Consolas nsole ( 8 H h X x d ( O O O O O O ` ` 6 l 8 j h C:\Windows\system32\notepad.exe :< 7 7 C:\Windows\system32\ole32.dll k e D f g i ` ` l 8 ) 6 H % / ; G Y k $ , 4 ? L [m # Input\Service.AlpcPort\Server C:\Windows\system32\notepad.exe < [ y 0 ( P \??\C:\Windows\SystemResources\USER32.dll.mun ext-ms-win-rtcore-ntuser-window-ext-l1-1-0.dll $ ; Z x Input\Service.AlpcPort\Server 1 8 j @ 2 CoreUIComponents TextInputServer ExternalComOwner C:\Windows\System32\ole32.dll TextInputServer Q t1s1s4t0t4llys3cur3p4ssw0rdn0rocky0 ParkedProxyOwner 0 TextInputServer > 6 O D 6 ; las l t1 t neve b t1s m pas H % / ; G Y k $ , 4 ? L [m ) Ln 2, Col 15 t1s1s4t0t4llys3c Ln 2, Col 42 Ln 2, Col 43 Notepad Ln 2, Col 51 Ln 2, Col 37 ( Ln 2, Col 50 Ln 2, Col 55 3 Ln 2, Col 26 Ln 2, Col 47 Ln 2, Col 49 Ln 2, Col 48 Ln 2, Col 33 Ln 2, Col 35 Ln 2, Col 54 Ln 2, Col 53 Ln 2, Col 39 3cur ( @ ( ) ext-ms-win-core-win32k-fulluser-l1-1-0 t ext-ms-win-core-win32k-fulluser-l1-1-0 ext-ms-win-core-win32k-minuser-l1-1-0 ext-ms-win-core-win32k-fulluser-l1-1-0 ext-ms-win-core-win32k-fulluser-l1-1-0 ext-ms-win-core-win32k-fulluser-l1-1-0 ext-ms-win-core-win32k-minuser-l1-1-0 ext-ms-win-core-win32k-fulluser-l1-1-0 ext-ms-win-core-win32k-minuser-l1-1-0 ext-ms-win-core-win32k-fulluser-l1-1-0 ext-ms-win-core-win32k-minuser-l1-1-0 \BaseNamedObjects X ext-ms-win-core-win32k-minuser-l1-1-0 ext-ms-win-core-win32k-minuser-l1-1-0 ext-ms-win-core-win32k-minuser-l1-1-0 X ext-ms-win-core-win32k-fulluser-l1-1-0 ext-ms-win-core-win32k-fulluser-l1-1-0 ext-ms-win-core-win32k-fulluser-l1-1-0 S S \BaseNamedObjects\[CoreUI]-PID(4160)-TID(4132) 1e6e6bc4-dd60-46b4-9e84-70f923d5629a 7 \BaseNamedObjects\[CoreUI]-PID(7900)-TID(7816) fc205108-f731-44a3-a019-8c2b4cb39c88 8 8 8 8 Consolas nsole ER\S 435439-1930665703-3246598564-1001 ` ` @ Security-SPP-GenuineLocalStatus ` ` D never gonna give you my last password: t1s1s4t0t4llys3cur3p4ssw0rdn0rocky0utxt Consolas ( V i
Right at the end:
never gonna give you my last password: t1s1s4t0t4llys3cur3p4ssw0rdn0rocky0utxt
Steghide
A common steg technique in CTF events like Hackvent is steghide (sudo apt install steghide). I’ll try it, giving it the password from above, and it works:
oxdf@hacky$ steghide extract -sf secret/image.jpg
Enter passphrase:
wrote extracted data to "secret-flag.png".
The image is a QRcode:

It has the flag:
oxdf@hacky$ zbarimg secret-flag.png
QR-Code:HV24{p4ssw0rd_h1dd3n_1n_z3_n0tep4d.exe}
scanned 1 barcode symbols from 1 images in 0.01 seconds
Flag: HV24{p4ssw0rd_h1dd3n_1n_z3_n0tep4d.exe}
HV24.06
Challenge
| HV24.06 Chimney Windows | |
|---|---|
| Categories: |
|
| Level: | medium |
| Author: | coderion |
Santa has seen it. He is done with Linux - it’s just too hard. So he installed Windows. Sadly, he also lost his flag while doing so. Help him find it.
Hint:
Ctrl+Zandstty raw -echo; fghelps fix the VM console.
Enumeration
I’ll connect to the instance and get a Windows cmd prompt:
oxdf@hacky$ nc 152.96.15.183 5000
=======================
🎅 HV24 VM instancer 🎅
=======================
Please wait while we create your VM...
🎉 Your VM is ready! 🎉
Press enter, if you don't see any prompt.
Microsoft Windows 10.0.19043
C:\users\santa>
I’ll do the back half of the standard shell upgrade trick:
C:\users\santa>^Z
[1]+ Stopped nc 152.96.15.183 5000
oxdf@hacky$ stty raw -echo; fg
nc 152.96.15.183 5000
C:\users\santa>
This looks like a Windows system, but looking at the tasklist shows that it’s actually Wine:
C:\users\santa>tasklist
Image Name PID Session Name Session# Mem Usage
========================= ======== ================ =========== ============
services.exe 56 Console 1 18,052 K
explorer.exe 68 Console 1 19,620 K
winedevice.exe 76 Console 1 17,744 K
winedevice.exe 116 Console 1 24,128 K
plugplay.exe 164 Console 1 15,576 K
svchost.exe 196 Console 1 10,592 K
rpcss.exe 228 Console 1 14,716 K
start.exe 288 Console 1 14,376 K
conhost.exe 296 Console 1 15,192 K
cmd.exe 304 Console 1 14,488 K
tasklist.exe 332 Console 1 12,600 K
There’s a notes.txt on santa’s desktop, but it’s just a RickRoll:
C:\users\santa\Desktop>type notes.txt
Never gonna give you up, never gonna let you down, never gonna run around and de
sert you
This Ubuntu forums post talks about how Z: is mounted as the the Linux system in Wine. It works here as well:
C:\users\santa>Z:
Z:\>dir
Volume in drive Z has no label.
Volume Serial Number is 5a00-0000
Directory of Z:\
12/05/2024 09:40 PM <DIR> bin
04/15/2020 11:09 AM <DIR> boot
12/05/2024 09:15 PM 523 entrypoint.sh
12/06/2024 05:57 PM <DIR> etc
12/05/2024 09:20 PM 303,357 flag.tar.gz
12/05/2024 09:40 PM <DIR> home
12/01/2024 03:40 AM <DIR> lib
10/11/2024 02:03 AM <DIR> lib32
10/11/2024 02:09 AM <DIR> lib64
10/11/2024 02:03 AM <DIR> libx32
10/11/2024 02:03 AM <DIR> media
10/11/2024 02:03 AM <DIR> mnt
12/01/2024 03:40 AM <DIR> opt
12/01/2024 03:41 AM <DIR> root
12/01/2024 03:39 AM <DIR> run
12/01/2024 03:40 AM <DIR> sbin
10/11/2024 02:03 AM <DIR> srv
12/06/2024 05:58 PM <DIR> tmp
12/01/2024 03:16 AM <DIR> usr
10/11/2024 02:09 AM <DIR> var
2 files 303,880 bytes
18 directories 289,423,200,256 bytes free
There’s a flag.tar.gz… but I don’t have any good tools to read it.
Exfil Tar Archive
Failed Solutions
I tried several things before getting success. For one, everything is being sent over an unencrypted connection, so I’ll open Wireshark and record. The challenge is that there are a ton of ANSI control characters being sent:
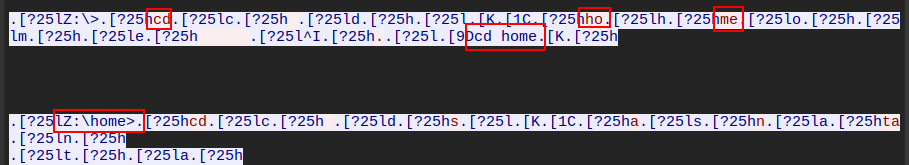
In this shot, I’m literally just running cd home, and the rest of the junk is added in. I can type the file, but I wasn’t able to remove all the control characters to recover the archive.
I also tried to use certutil to base64 encode the file. It is a valid binary on the host:
Z:\>certutil
Z:\>certutilaa
Can't recognize 'certutilaa' as an internal or external command, or batch script
.
This command runs:
Z:\>certutil -encodehex flag.tar.gz C:\users\santa\flag.tar.gx.hex 0x400
But no file is ever created.
cscript
I did figure out that cscript is in the environment and can run VB scripts:
C:\users\santa>echo WScript.Echo("Hello!") > a.vbs
C:\users\santa>cscript a.vbs
Hello!
Getting this working was a ton of trial and error, as there are not errors printed when things fail, and a lot of standard stuff doesn’t work. But I did eventually get something that would print the file as hex:
Set fso = CreateObject("Scripting.FileSystemObject")
filePath = "Z:\flag.tar.gz"
Set file = fso.OpenTextFile(filePath, 1)
hexstring = ""
Do Until file.AtEndOfStream
char = file.Read(1)
hexval = Hex(Asc(char))
if Len(hexval) = 1 Then hexval = "0" ^& hexval
hexstring = hexstring ^& hexval
Loop
file.Close
WScript.Echo hexstring
To create this, I’ll have to echo it line by line into a file and then run it:
echo Set fso = CreateObject("Scripting.FileSystemObject") > t.vbs
echo filePath = "Z:\flag.tar.gz" >> t.vbs
echo Set file = fso.OpenTextFile(filePath, 1) >> t.vbs
echo hexstring = "" >> t.vbs
echo Do Until file.AtEndOfStream >> t.vbs
echo char = file.Read(1) >> t.vbs
echo hexval = Hex(Asc(char)) >> t.vbs
echo if Len(hexval) = 1 Then hexval = "0" ^& hexval >> t.vbs
echo hexstring = hexstring ^& hexval >> t.vbs
echo Loop >> t.vbs
echo file.Close >> t.vbs
echo WScript.Echo hexstring >> t.vbs
cscript t.vbs
Characters such as “&” have to be escaped by “^” to be echoed properly.
This runs for a few minutes, but produces a hex string:
C:\users\santa>echo Set fso = CreateObject("Scripting.FileSystemObject") > t.vbs
C:\users\santa>echo filePath = "Z:\flag.tar.gz" >> t.vbs
C:\users\santa>echo Set file = fso.OpenTextFile(filePath, 1) >> t.vbs
C:\users\santa>echo hexstring = "" >> t.vbs
C:\users\santa>echo Do Until file.AtEndOfStream >> t.vbs
C:\users\santa>echo char = file.Read(1) >> t.vbs
C:\users\santa>echo hexval = Hex(Asc(char)) >> t.vbs
C:\users\santa>echo if Len(hexval) = 1 Then hexval = "0" ^& hexval >> t.vbs
C:\users\santa>echo hexstring = hexstring ^& hexval >> t.vbs
C:\users\santa>echo Loop >> t.vbs
C:\users\santa>echo file.Close >> t.vbs
C:\users\santa>echo WScript.Echo hexstring >> t.vbs
C:\users\santa>
C:\users\santa>cscript t.vbs
1F8B0800000000000003D4BA63702E5FD...[snip]...
On my host, I can save that hex to a file and decode it:
oxdf@hacky$ vim flag.tar.gz.hex
oxdf@hacky$ xxd -r -p flag.tar.gz.hex > flag.tar.gz
oxdf@hacky$ file flag.tar.gz
flag.tar.gz: gzip compressed data, from Unix, original size modulo 2^32 860335160 gzip compressed data, unknown method, ASCII, has CRC, has comment, encrypted, from FAT filesystem (MS-DOS, OS/2, NT), original size modulo 2^32 860335160
flag.png is just a RickRoll:

But the flag is in the metadata:
oxdf@hacky$ exiftool flag.png | grep HV24
Comment : HV24{w41t_1t5_4ll_l1nux???}
Escape Wine
The /exec flag in start allows for running Unix commands within the Wine environment:
z:\>start /exec /bin/bash -c 'ls'
bin entrypoint.sh home lib64 mnt root srv usr
boot etc lib libx32 opt run sys var
dev flag.tar.gz lib32 media proc sbin tmp
It’s not perfect, but I can do things like look at the files inside the archive:
z:\>start /exec /bin/bash -c "tar -tzvf flag.tar.gz"
-r--r--r-- alois/alois 303286 2024-12-05 21:06 flag.png
I’ll extract the file to /tmp:
z:\>start /exec /bin/bash -c "tar -xzvf flag.tar.gz -C /tmp"
flag.png
z:\>dir tmp
Volume in drive z has no label.
Volume Serial Number is 5a00-0000
Directory of z:\tmp
12/06/2024 06:37 PM <DIR> .
12/06/2024 05:57 PM <DIR> ..
12/05/2024 09:06 PM 303,286 flag.png
1 file 303,286 bytes
2 directories 287,709,204,480 bytes free
I can get the flag from grepping for it in the image:
z:\>start /exec /bin/bash -c "cat /tmp/flag.png | grep -a -oP 'HV24{.*}'"
HV24{w41t_1t5_4ll_l1nux???}
Flag: HV24{w41t_1t5_4ll_l1nux???}
HV24.07
Challenge
| HV24.07 Merry Mazemas | |
|---|---|
| Categories: |
|
| Level: | medium |
| Author: | keep3r |
A clumsy elf lost all the gifts in a magical maze right before Christmas Eve. Now, with time of the essence, Santa must navigate this maze, collecting every gift in the most optimal way - the shortest path possible - to save Christmas. Can you guide him to gather all the gifts and reach the exit before it’s too late?
Navigate the maze and get the flag.
There’s no downloadable, only a spawned docker container with a TCP port.
When I connect to the socket, I’m given a maze:
oxdf@hacky$ nc 152.96.15.12 8000
Ho Ho Ho! It's Merry Mazemas!
Guide Santa through the maze to collect all the gifts in the most efficient way possible before exiting.
s = Santa
x = Gift
e = Exit
###########
#s# # x#
# ### # # #
# # # # #
### # # # #
# # #x#
# ####### #
# # #
##### # # #
#e # #
###########
Move (w/a/s/d):
w, a, s, and d move up, left, down, and right respectively.
Move (w/a/s/d):
s
###########
# # # x#
#s### # # #
# # # # #
### # # # #
# # #x#
# ####### #
# # #
##### # # #
#e # #
###########
Move (w/a/s/d):
After some amount of time, it prints:
Ho ho ho, looks like you've been taking the scenic route through the maze!
Don't worry, Santa has all night, but let's see if we can find that exit a bit quicker, shall we?
I’ll need to code this.
Solution
I’ll use pwntools which has a nice API for interacting with remove sockets. I’ll connect to the IP / port and receive the intro data:
conn = remote(ip, port)
conn.recvuntil(b"Exit\n")
This ends up being three mazes to solve, so my script now drops into a while True loop that will read to the prompt after the maze, pass that string to a function that solves the maze, send the results, and the loop again:
while True:
resp = conn.recvuntil((move_prompt, b"HV24{")).decode()
if resp.endswith("HV24{"):
break
map_str = '\n'.join([l for l in resp.splitlines() if l.startswith("#")])
moves = solve_maze(map_str)
for move in moves:
conn.sendline(move.encode())
conn.recvuntil(b"Congratulations")
print("HV24{" + conn.readline().decode())
Originally I had the code sending each move and then reading up to the next prompt, but that was very slow. Instead, I found that sending all the moves and then looking for the word “Congratulations” allowed me to read all the responses at once, and then I could use the same recvuntil at the top of the loop to get the next map or the flag.
For the solve_maze function, it has two parts. First, it takes the string and parses the values into some sets:
def solve_maze(map_str: str) -> list[str]:
start_time = time()
walls = set()
presents = set()
for r, line in enumerate(map_str.splitlines()):
for c, chr in enumerate(line):
if chr == "s":
start = r, c
elif chr == "e":
end = r, c
elif chr == "x":
presents.add((r,c))
elif chr == "#":
walls.add((r, c))
I’m storing the starting point, the end point, as well as the locations of all the walls and presents.
I’ll initialize my queue and seen for a breadth first search (BFS). BFS works really well here as it will check all possible 1 moves, then all possible 2 moves, and so on, and can break when it finds a valid solution which will be guaranteed to be the shortest.
move_map = {(1, 0): 's', (0, 1): 'd', (-1, 0): 'w', (0, -1): 'a'}
# state = location, moves, collected presents
queue = deque([(start, [], set())])
seen = set()
For state, I’ll store the current position (start), the moves to get to that point (none), and the collected presents (empty set). move_map is just a way to track between the input letters and the directions moved on the coordinates (dr, dc).
Now I loop while queue isn’t empty:
while queue:
(r, c), moves, collected = queue.popleft()
if (r, c) == end and collected == presents:
print(f"Solved map in {time() - start_time: 0.02} seconds, {len(moves)} moves")
return moves
if (r, c) in presents:
collected.add((r,c))
seen.add((r, c, frozenset(collected)))
for dr, dc in move_map:
nr, nc = r + dr, c + dc
if (nr, nc) not in walls and (nr, nc, frozenset(collected)) not in seen:
queue.append(((nr, nc), moves + [move_map[(dr, dc)]], collected.copy()))
I get the next state out of the queue. If this is the end point and the collected presents matches the initial list of presents, then I’m done. I’ll print a message and returns moves.
Otherwise, I’ll check to see if the current location is a present, and if so, add it to the collected set. Then I’ll store the current state in seen. I only need the location and the set of presents. The presents matter because I might have to go over a location to get a present and then come back over that same location now having visited that present location. I’m converting the set to a frozenset so that it can be in a set.
Next I check all possible next moves from the current position. If the next spot is not a wall, and it’s not in seen, then I add that next spot to the queue.
This all runs very quickly and returns the flag:
$ time python solve.py 152.96.15.2 8000
[+] Opening connection to 152.96.15.2 on port 8000: Done
Solved map in 0.00014 seconds, 36 moves
Solved map in 0.0025 seconds, 380 moves
Solved map in 0.07 seconds, 874 moves
HV24{santa-is-a-travelling-salesman}
[*] Closed connection to 152.96.15.2 port 8000
real 0m2.465s
user 0m0.304s
sys 0m0.045s
Flag: HV24{santa-is-a-travelling-salesman}
HV24.18
Challenge
| HV24.18 Santa's Stego | |
|---|---|
| Categories: |
|
| Level: | medium |
| Author: | coderion |
Santa has written his own super secret stego algorithm back in the old days, after learning about base 2. It could even do RGB stuff to make the images not look off. Sadly he forgot how it worked, can you help him out?
Analyze the image and get the flag.
I’m given this image:

Solution via Python
Viewing the image at aperisolve.com showed something interesting for three of the planes:
There’s way more black in the 1 bit for red, 2 bit for green, and 4 bit for blue.
After playing around with ways to combine these for some time, I’ll find that literally enabling them if any bit is one (white in the image above) makes a QRCode:
from PIL import Image
image = Image.open('d7a90abe-b265-42ae-afe9-b57a7d28c5a8.png')
width, height = image.size
qrcode = Image.new("1", image.size)
for y in range(height):
for x in range(width):
r, g, b = image.getpixel((x, y))
pixel = -1 * (((r&1) | ((g & 2) // 2) | ((b & 4) // 4)) - 1)
qrcode.putpixel((x, y), pixel)
qrcode = qrcode.resize((450, 450), Image.NEAREST)
qrcode.save('flag.png')
The resulting image is:

And it scans to the flag:
oxdf@hacky$ zbarimg flag.png
QR-Code:HV24{v3ry_fun_l0l_s0rry_f0r_th3_p41n_n3v3r_g0nna_g1v3_y0u_up}
scanned 1 barcode symbols from 1 images in 0 seconds
Solution via Gimp
Another neat way to get the flag is to grab the three images from Aperi’s Solve and paste them as layers in Gimp. Typically, I’ll just see the top layer (blue pixel 4 in this case):
For the top two layers, I’ll switch the “Mode” from “Normal” to “Addition”:
Now it shows the QRcode:

My phone will read this, but zbarimg won’t because it’s inverted. I’ll go to Image –> Flatten Image to get the image as one layer, and then Colors –> Invert to switch black and white. I’ll also Image –> Scale Image to make it bigger (like 450 by 450), and export it as a PNG:

Now it returns the flag:
oxdf@hacky$ zbarimg gimp-qr.png
QR-Code:HV24{v3ry_fun_l0l_s0rry_f0r_th3_p41n_n3v3r_g0nna_g1v3_y0u_up}
scanned 1 barcode symbols from 1 images in 0.01 seconds
Flag: HV24{v3ry_fun_l0l_s0rry_f0r_th3_p41n_n3v3r_g0nna_g1v3_y0u_up}
HV24.19
Challenge
| HV24.19 Santa's Workshop: A Technical Emergency | |
|---|---|
| Categories: |
|
| Level: | medium |
| Author: | darkstar |
Santa’s magical workshop is more modern than ever this year! In addition to the classic toys and presents, Santa has launched a major project: Old computers are to be repaired, cleaned and recycled for children all over the world. His aim is not only to spread the magic of Christmas, but also to protect the environment.
But just before the big celebration, there is a problem: One of the elves discovers that some of the computers have not been properly prepared. Confidential data from previous owners may have been left on them, and some devices are displaying strange error messages that could indicate hardware problems.
As the elves in the workshop have their hands full, Santa turns to you, his specialist in digital magic. You are given access to a magical virtual machine that simulates one of the affected computers. Your job is to make sure that the computer gets under the Christmas tree safely and on time.
After you start the PC, you can connect to it via SSH with the credentials
root:santaon port2222.Start the service and get the flag.
Enumeration
Spawn VM
The spawned instance provides a web interface:
This page is not part of the challenge, but rather a control panel to spin up a VM that I can SSH into. I’ll click “Start PC”, and the buttons are replaced with a single button that says “Stop PC”.
VM Enumeration
I’ll connect over SSH:
oxdf@hacky$ sshpass -p santa ssh -p 2222 root@152.96.15.13
-----------[ Caution ]-----------
This PC has not yet been checked.
Not yet authorized to give away.
---------------------------------
#
The host is running Buildroot:
# cat /etc/os-release
NAME=Buildroot
VERSION=2024.02.8
ID=buildroot
VERSION_ID=2024.02.8
PRETTY_NAME="Buildroot 2024.02.8"
There are two users with shells set, root and Santa:
# cat /etc/passwd | grep "sh$"
root:x:0:0:root:/root:/bin/sh
Santa:x:1000:1000:Linux User,,,:/home/Santa:/bin/sh
/root is basically empty:
# find /root/
/root/
/root/.ash_history
/root/.ssh
/root/.ssh/known_hosts
The .ash_history file just has the command I’ve run. /home/Santa has only a .ash_history file:
# find /home/Santa/
/home/Santa/
/home/Santa/.ash_history
# cat /home/Santa/.ash_history
exit
ls -la
ddrescue
Santa has run ddrescue, though that is no longer on the box, running find / -name '*ddrescue*' will show.
There is a message file in /tmp, but there’s nothing interesting in it. It’s in /tmp because /var/log is symlinked to /tmp:
# ls -l /var
total 2
lrwxrwxrwx 1 root root 6 Nov 14 16:25 cache -> ../tmp
drwxr-xr-x 3 root root 1024 Nov 16 21:39 lib
lrwxrwxrwx 1 root root 11 Nov 14 16:25 lock -> ../run/lock
lrwxrwxrwx 1 root root 6 Nov 14 16:25 log -> ../tmp
lrwxrwxrwx 1 root root 6 Nov 14 16:25 run -> ../run
lrwxrwxrwx 1 root root 6 Nov 14 16:25 spool -> ../tmp
lrwxrwxrwx 1 root root 6 Nov 14 16:25 tmp -> ../tmp
drwxr-xr-x 2 www-data www-data 1024 Nov 16 21:37 www
ddrescue
Install
ddrescue is a GNU data recovery tool. I’ll grab a copy of the the source from one of the GNU mirrors, and then extract and build it, creating the binary:
oxdf@hacky$ tar xf ddrescue-1.28.tar.lz
oxdf@hacky$ cd ddrescue-1.28/
oxdf@hacky$ ./configure
creating config.status
creating Makefile
VPATH = .
prefix = /usr/local
exec_prefix = $(prefix)
bindir = $(exec_prefix)/bin
datarootdir = $(prefix)/share
infodir = $(datarootdir)/info
mandir = $(datarootdir)/man
CXX = g++
CPPFLAGS =
CXXFLAGS = -Wall -W -O2
LDFLAGS =
MAKEINFO = makeinfo
OK. Now you can run make.
oxdf@hacky$ make
g++ -Wall -W -O2 -c -o arg_parser.o arg_parser.cc
g++ -Wall -W -O2 -c -o rational.o rational.cc
g++ -Wall -W -O2 -c -o non_posix.o non_posix.cc
g++ -Wall -W -O2 -c -o loggers.o loggers.cc
g++ -Wall -W -O2 -c -o block.o block.cc
g++ -Wall -W -O2 -c -o mapfile.o mapfile.cc
g++ -Wall -W -O2 -c -o mapbook.o mapbook.cc
g++ -Wall -W -O2 -c -o fillbook.o fillbook.cc
g++ -Wall -W -O2 -c -o genbook.o genbook.cc
g++ -Wall -W -O2 -c -o io.o io.cc
g++ -Wall -W -O2 -c -o rescuebook.o rescuebook.cc
g++ -Wall -W -O2 -c -o command_mode.o command_mode.cc
g++ -Wall -W -O2 -DPROGVERSION=\"1.28\" -c -o main.o main.cc
g++ -Wall -W -O2 -o ddrescue arg_parser.o rational.o non_posix.o loggers.o block.o mapfile.o mapbook.o fillbook.o genbook.o io.o rescuebook.o command_mode.o main.o
g++ -Wall -W -O2 -DPROGVERSION=\"1.28\" -c -o ddrescuelog.o ddrescuelog.cc
g++ -Wall -W -O2 -o ddrescuelog arg_parser.o block.o mapfile.o ddrescuelog.o
oxdf@hacky$ file ddrescue
ddrescue: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=8171123523e4b7e007dd0ea411dab4fc3f15dde2, for GNU/Linux 3.2.0, not stripped
The VM is very stripped, doesn’t support scp and wget doesn’t work. I was able to get a copy onto the VM using ssh and pipes:
oxdf@hacky$ cat ddrescue-1.28/ddrescue | sshpass -p santa ssh -p 2222 root@152.96.15.13 'cat > /bin/ddrescue; chmod +x /bin/ddrescue'
-----------[ Caution ]-----------
This PC has not yet been checked.
Not yet authorized to give away.
---------------------------------
Running it now fails with a library issue:
# ddrescue
ddrescue: error while loading shared libraries: libstdc++.so.6: cannot open shared object file: No such file or directory
I’ll find that library on my host:
oxdf@hacky$ ldd ddrescue
linux-vdso.so.1 (0x00007fffed98d000)
libstdc++.so.6 => /lib/x86_64-linux-gnu/libstdc++.so.6 (0x0000721b59200000)
libgcc_s.so.1 => /lib/x86_64-linux-gnu/libgcc_s.so.1 (0x0000721b594a0000)
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x0000721b58e00000)
libm.so.6 => /lib/x86_64-linux-gnu/libm.so.6 (0x0000721b59117000)
/lib64/ld-linux-x86-64.so.2 (0x0000721b5950f000)
And copy it up as well:
oxdf@hacky$ cat /lib/x86_64-linux-gnu/libstdc++.so.6 | sshpass -p santa ssh -p 2222 root@152.96.15.13 'cat > /lib/libstdc++.so.6'
-----------[ Caution ]-----------
This PC has not yet been checked.
Not yet authorized to give away.
---------------------------------
Now it works:
# ddrescue
ddrescue: Both input and output files must be specified.
Try 'ddrescue --help' for more information.
Run
ddrescue can copy data and try to produce good copies from bad sectors. It also creates a mapfile, which contains a log of good and bad sectors on the disk.
To take a look a the sectors, I’ll run with the output file of /dev/null (and using -f or else it won’t “overwrite” an existing file). I’ll also use -d to get raw disk read.
# ddrescue -d -f /dev/sda /dev/null ddrescue.mapfile
GNU ddrescue 1.28
Press Ctrl-C to interrupt
ipos: 104792 kB, non-trimmed: 262144 B, current rate: 102 MB/s
opos: 104792 kB, non-scraped: 0 B, average rate: 102 MB/s
non-tried: 983040 B, bad-sector: 0 B, error rate: 196 kB/s
rescued: 103612 kB, bad areas: 0, run time: 1s
pct rescued: 98.81%, read errors: 4, remaining time: 1s
time since last successful read: 0s
Copying non-tried blocks... Pass 1 (forwards)
ipos: 102498 kB, non-trimmed: 458752 B, current rate: 102 MB/s
opos: 102498 kB, non-scraped: 0 B, average rate: 102 MB/s
non-tried: 262144 B, bad-sector: 0 B, error rate: 196 kB/s
rescued: 104136 kB, bad areas: 0, run time: 1s
pct rescued: 99.31%, read errors: 7, remaining time: 1s
time since last successful read: 0s
Copying non-tried blocks... Pass 2 (backwards)
ipos: 102957 kB, non-trimmed: 720896 B, current rate: 1703 kB/s
opos: 102957 kB, non-scraped: 0 B, average rate: 52068 kB/s
non-tried: 0 B, bad-sector: 0 B, error rate: 524 kB/s
rescued: 104136 kB, bad areas: 0, run time: 2s
pct rescued: 99.31%, read errors: 11, remaining time: 1s
time since last successful read: 0s
Copying non-tried blocks... Pass 5 (forwards)
ipos: 103117 kB, non-trimmed: 0 B, current rate: 1703 kB/s
opos: 103117 kB, non-scraped: 650752 B, average rate: 52068 kB/s
non-tried: 0 B, bad-sector: 1024 B, error rate: 524 kB/s
rescued: 104205 kB, bad areas: 2, run time: 2s
pct rescued: 99.37%, read errors: 13, remaining time: 1s
time since last successful read: 0s
Trimming failed blocks... (forwards)
ipos: 103117 kB, non-trimmed: 0 B, current rate: 109 kB/s
opos: 103117 kB, non-scraped: 0 B, average rate: 4985 kB/s
non-tried: 0 B, bad-sector: 157184 B, error rate: 6144 B/s
rescued: 104700 kB, bad areas: 187, run time: 20s
pct rescued: 99.85%, read errors: 318, remaining time: 0s
time since last successful read: n/a
Scraping failed blocks... (forwards)
Finished
The resulting log file is 10056 bytes.
Visualize
I’ll exfil the mapfile using SSH as well:
oxdf@hacky$ sshpass -p santa ssh -p 2222 root@152.96.15.13 "cat ddrescue.mapfile" > ddrescue.mapfilme
-----------[ Caution ]-----------
This PC has not yet been checked.
Not yet authorized to give away.
---------------------------------
ddrescueview (apt install ddrescueview) will help visualize the mapfile. I’ll open it and the mapfile. On the left side, there’s a bar representing the full disk, with some bad sectors at the bottom:
I’ll use the mouse wheel to zoom in as close as possible on those sectors, and by adjusting the width of my view, the bad sectors spell out the flag:
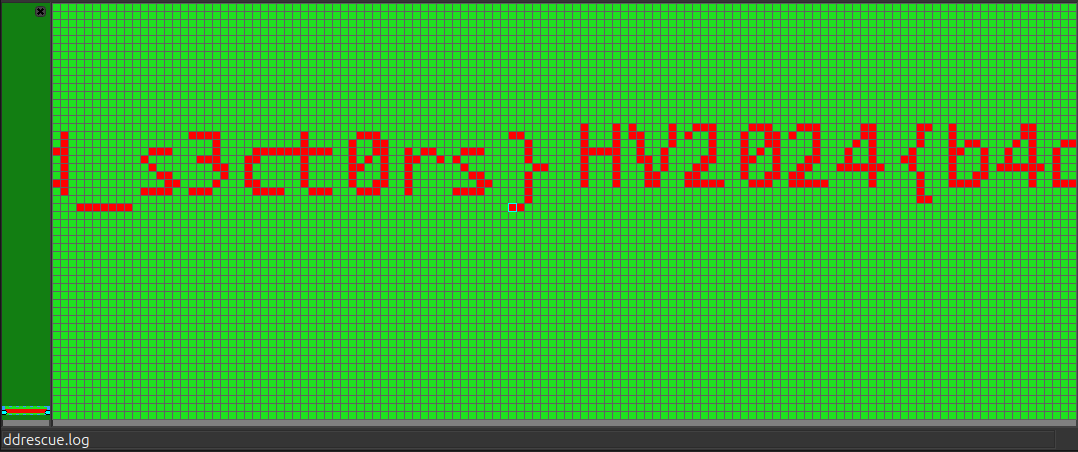
The actual flag is with HV24 instead of HV2024.
Flag: HV24{b4d_s3ct0rs}
HV24.20
Challenge
| HV24.20 Santa's Modular Calculator | |
|---|---|
| Categories: |
|
| Level: | medium |
| Author: | kuyaya |
As every year, Santa is wrapping gifts for the nice children. At some point, he was wrapping this calculator but it started to display dome weird numbers. Maybe they have a special meaning?
Start the service and get the flag.
Service
Source
The download has the Python source for this application. It generates a random s and converts the flag to bytes:
import random
s = random.randint(2<<1337, 2<<1338) * 2
flag = int.from_bytes(b"HV24{NOT_THE_REAL_FLAG}", "big")
It prints a giant ASCII art, and then drops into a loop reading n and returning pow(n, s, flag):
while True:
try:
n = int(input("Enter your n: "))
res = pow(n, s, flag)
print(f"Your result: {res}")
except:
print("Please submit an integer (base 10)")
Interactive
The service does just that:
oxdf@hacky$ nc 152.96.15.2 1337
...[snip]...
Welcome to Santa's modular calculator. Enter a number n and I'll print back n^s mod flag!
Enter your n: 4
Your result: 3285907370512263226118579084064605356456284313625932261442487479332653480477863144870485525345375615726057029487080
Enter your n: 1000
Your result: 9084587818548834780993406250160085549653574096713691465382918802066145189089904210051942792205403905809439011209033
Solve
Background
The math to understand this solution is as follows. I’m going to pick two numbers, m and m’, where m’ is m2. I’ll submit m and m’ to get c and c’ from the service. Because m’ = m2, c’ = c2 mod flag. That measn that (c’ - c2) = 0 mod flag, which is another way to say that c’ - c2 = k * flag for some k.
I don’t know k, but if I do this a couple times and look for the largest common divisor, eventually that will be flag. This is also described in this StackExchange answer.
Exploit
I’ll write a simple Python script to read numbers and exploit this:
import math
import sys
from pwn import *
from Crypto.Util.number import long_to_bytes
def get_value(n: int) -> int:
r.recvuntil(b"Enter your n: ")
r.sendline(f"{n}".encode())
r.recvuntil(b"Your result: ")
return int(r.recvline())
r = remote(sys.argv[1], 1337)
m = 2
flag = ""
diffs = []
while True:
c = get_value(m)
cp = get_value(pow(m, 2))
diffs.append(pow(c, 2) - cp)
flag = long_to_bytes(math.gcd(*diffs))
m += 1
if flag.startswith(b"HV24{"):
break
print(f"Found the flag with {m - 1} pairs of numbers:")
print(flag.decode())
It starts with m of 2, and just keeps going until it finds the flag:
oxdf@hacky$ python solve.py 152.96.15.2
[+] Opening connection to 152.96.15.2 on port 1337: Done
Found the flag with 3 pairs of numbers:
HV24{3ucl1d_c0uld've-s0lv3d_th4t_2300_y34rs_4g0}
[*] Closed connection to 152.96.15.2 port 1337
Flag: HV24{3ucl1d_c0uld've-s0lv3d_th4t_2300_y34rs_4g0}