Holiday Hack 2025: It's All About Defang
Introduction
It's All About Defang
Difficulty:❅❅❅❅❅I’ll find Ed inside his office on the second floor of City Hall:
Ed Skoudis
I’m the Founder of Counter Hack Innovations, the team that brings you the SANS Holiday Hack Challenge for the last 22 years.
I’m also the President of the SANS Technology Institute College, which has over 2,300 students studying for their Bachelor’s Degrees, Master’s Degrees, and various certificates.
I was the original author of the SANS SEC504 (Incident Handling and Hacker Attacks) and SANS SEC560 (Enterprise Penetration Testing) courses.
I love Capture the Flag games and puzzles.
I’ve got a steampunk office filled with secret rooms, and I collect antique crypto systems and communication technologies.
I’ve got an original Enigma machine (A726, from the early war years), a leaf of the Gutenberg Bible (1 John 2:3 to 4:16) from 1455, and a Kryha Liliput from the 1920s.
Oh gosh, I could talk for hours about this stuff but I really need your help!
The team has been working on this new SOC tool that helps triage phishing emails…and there are some…issues.
We have had some pretty sketchy emails coming through and we need to make sure we block ALL of the indicators of compromise. Can you help me? No pressure…
Chat with Ed Skoudis
Congratulations! You spoke with Ed Skoudis!
The terminal opens up an interactive dashboard to handle a phishing email incident:
Solution
Headers
The email viewer has an email with full headers. Taking a look, it’s from a domain icicleinnovations.mail:
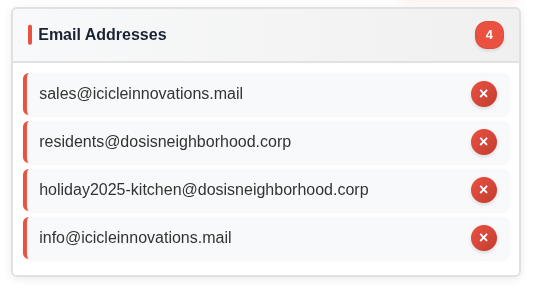
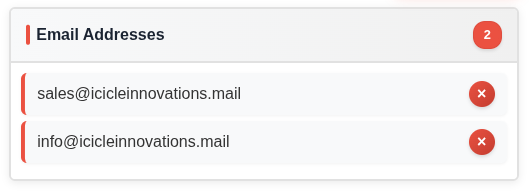
From: "Icicle Innovations" <sales@icicleinnovations.mail>
To: "Neighborhood Watch" <residents@dosisneighborhood.corp>
Subject: 🎄 URGENT: Holiday Kitchen Makeover - Smart Home Integration! 🎄
Date: Wed, 25 Dec 2025 09:15:33 -0500
Message-ID: <holiday2025-kitchen@dosisneighborhood.corp>
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
X-Mailer: KitchenAlert v2.025
Received: from mail.icicleinnovations.mail (172.16.254.1) by dosisneighborhood.corp (10.0.0.5) with SMTP;
Wed, 25 Dec 2025 09:15:28 -0500
Received: from core.icicleinnovations.mail (192.168.1.1) by mail.icicleinnovations.mail (172.16.254.1);
Wed, 25 Dec 2025 09:15:22 -0500
It’s sent to holiday2025-kitchen@dosisneighborhood.corp. I’m going to assume that that domain, as well as the 10.0.0.5 IP for the SMTP server are friendly infrastructure.
Body
The email body is offering kitchen renovations:
Dear Valued Dosis Neighborhood Residents,
🚨 IMMEDIATE ACTION REQUIRED 🚨
Our elite team of Sunny’s kitchen renovation specialists have detected some SERIOUSLY outdated kitchen setups in your neighborhood! It appears that certain homes are still using legacy appliances without proper smart home integration - like non-IoT fridges that can’t automatically order milk, or microwaves that don’t sync with your meal planning apps!
While this sounds like a delightfully festive renovation opportunity (and totally not a security assessment), we need you to:
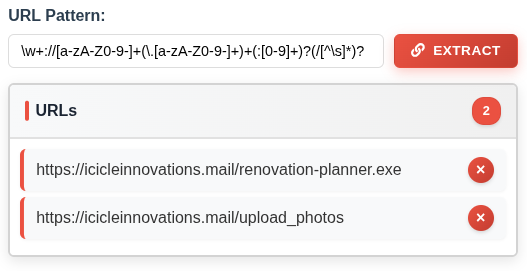
1) Download our FREE Kitchen Renovation Planner™ with built-in security features (totally legit, we promise!): https://icicleinnovations.mail/renovation-planner.exe
2) Upload high-resolution photos of your current kitchen to our secure design portal (we need to see ALL angles for proper renovation planning): https://icicleinnovations.mail/upload_photos
For instant help with any kitchen renovation questions, contact our 24/7 design hotline at 523.555.0100 or our renovation specialists at 523.555.0101.
Remember: If your old appliances start acting up during the assessment, it’s probably just excitement about their upcoming upgrades! But please document any issues with photos.
Stay merry (and consider smart upgrades),
Icicle Innovations
Chief Kitchen Design Specialist
📞 523.555.RENO
info@icicleinnovations.mail
P.S. - Has anyone else noticed their kitchen cabinets mysteriously rearranging themselves overnight? We can fix that with proper smart storage solutions!
This has several signs of a phishing email:
- Urgency, creating pressure to act now before the target has a chance to think.
- Link to
.exefile. It’s never wise to run a executable from an untrusted source. - Use of the
.maildomain. While these “newer” top level domains are becoming more common, they are still less trustworthy than.com.
Step 1
Overview
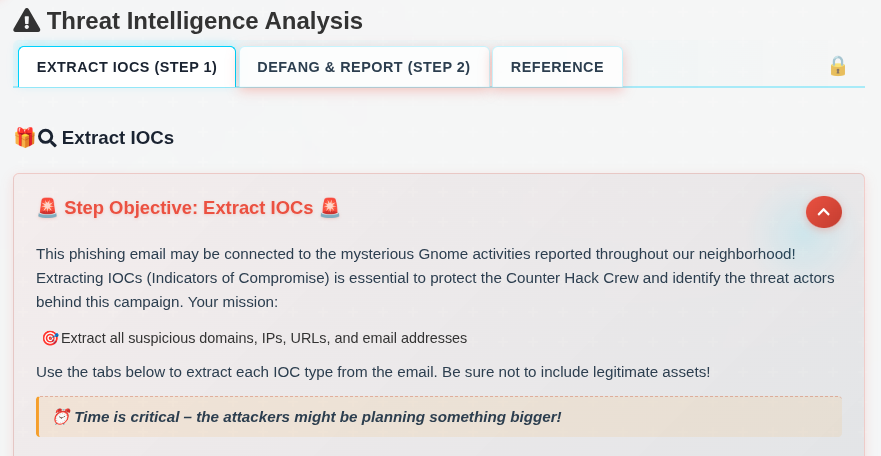
The Threat Intelligence Analysis panel has three tabs. The “Extract IOCS (Step 1)” tab has instructions:
Below that are four tabs for different indicators of compromise (IOCs):
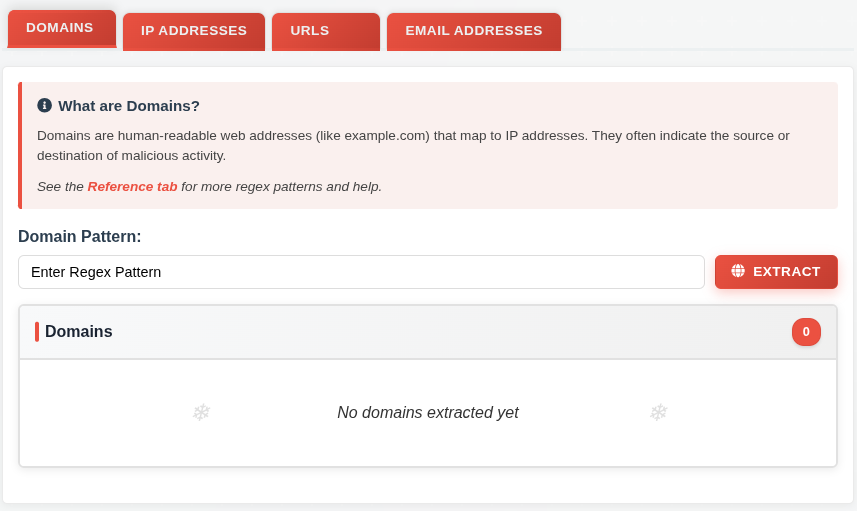
For each, I have to give a regex pattern to pull out those indicators from the email. The “Reference” tab has some example regex to pull out these indicators, but most of these have errors or are incomplete:
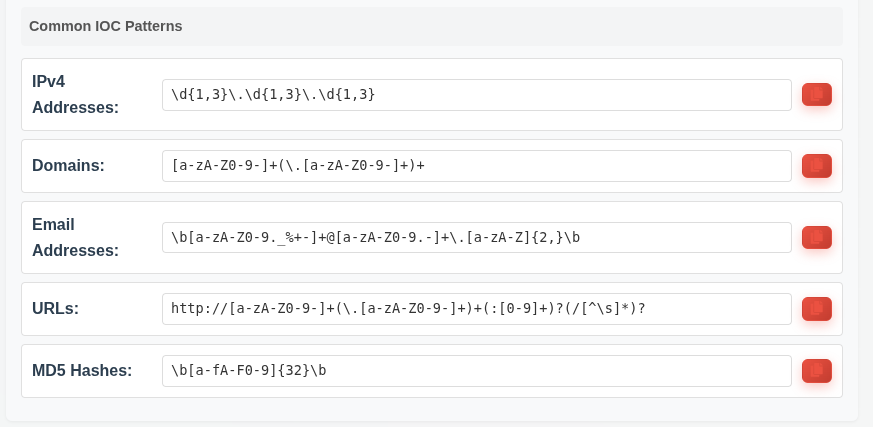
Domains
Domains are strings connected by “.”. The last item is the top level domain (TLD), like “.com” or “.net”. Originally there were only a handful of these, but starting in 2008 many more have been added. The given regex isn’t actually incorrect, as it defines a character set of lower, upper, and digits ([a-zA-Z0-9-]) and say there will be one or more of those (+), followed by a group that appears one or more times. That group is an escaped “.” (because without the escape it would mean any character) followed by one or more of that that same class of characters. This is going to capture all valid domains, but it also captures other things:
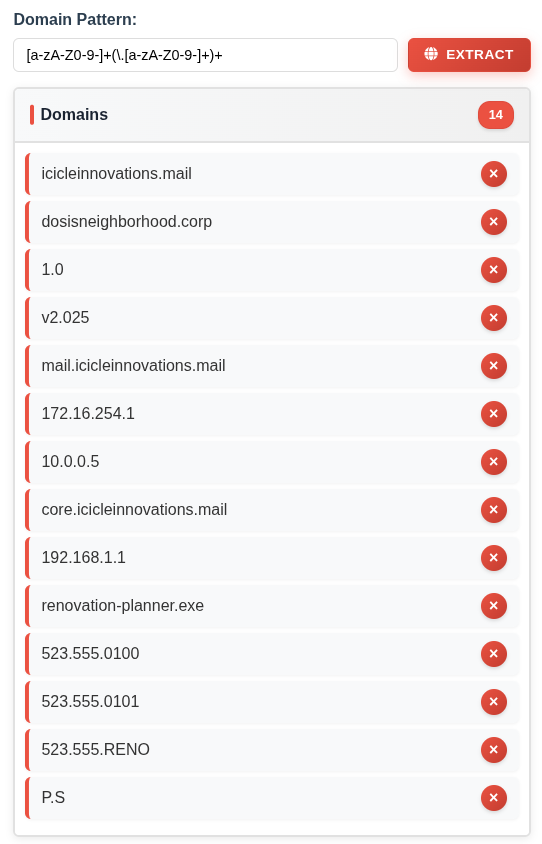
Version numbers, filenames, and IP addresses also match this pattern. For something like this, I like to target specific TLDs at the end. For this example, I’ll look for “com”, “net”, “mail”, and “corp”. Were I doing this in a real environment, I’d come up with a much longer list. I’ll replace the + on the last group with a * to mean 0 or more rather than 1 or more, and add the TLD to the end:
[a-zA-Z0-9-]+(\.[a-zA-Z0-9-]+)*\.(com|net|mail|corp)
This works:
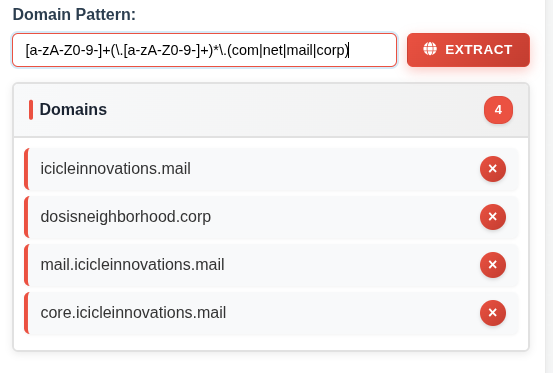
I’ll remove dosisneighborhood.corp using the “X” button since it’s not associated with the malicious actor to get the final answer:
IPv4
IPv4 addresses are made up of four octets, each represented as an integer from 0 - 255. The above regex uses \d to represent a digit, and then {1,3} to match between one and three digits. Then there’s a . character, escaped by \ because otherwise . represents any character. Then one to three digits, dot, and then one to three digits.
This only matches three octets. If I throw it in to the tool and submit, this is clear:
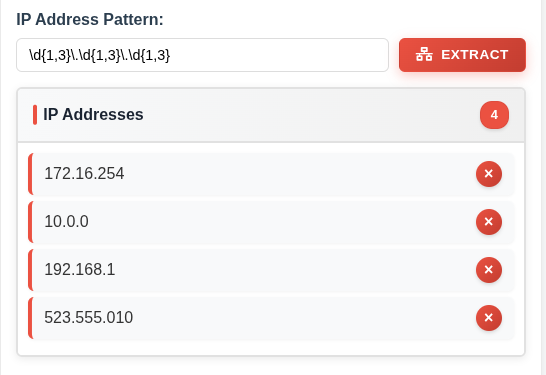
A simple fix is to just add \.\d{1,3}:
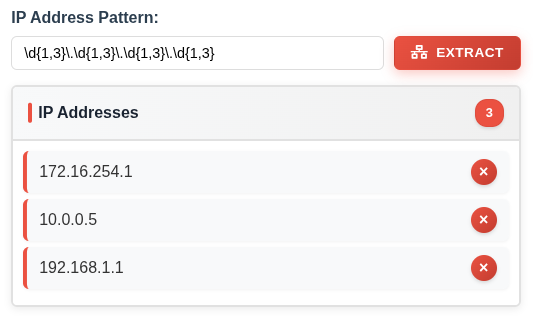
Most of the time, this is a good enough regex to get IPs. Still, there are issues with it. For one, 300.10.10.10 is not a valid IPv4, but it would match here.
I can ask Claude for a regex for IPv4, and it gives basically the one above (adding \b to match on word boundaries), as well as a stricter one that validates the true integer range:
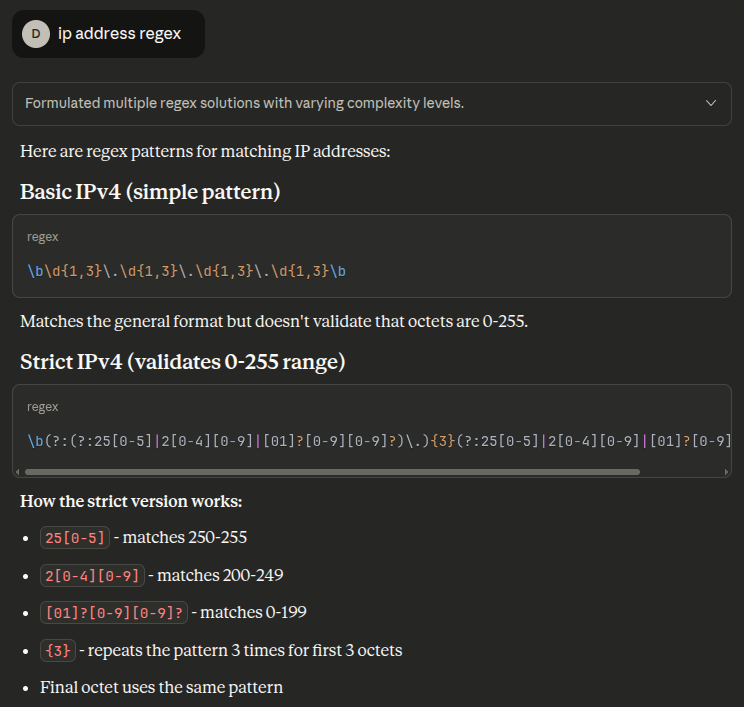
This one matches the same stuff.
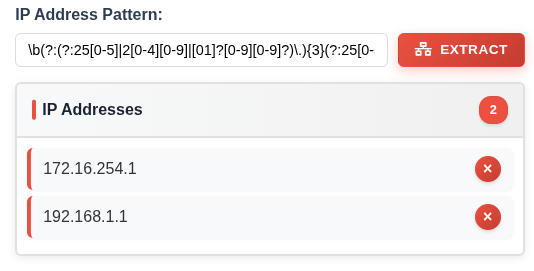
I’ll remove the 10.0.0.5 friendly SMTP server IP from the list using the “X” button for a final result:
URL
A uniform resource locator, or URL, is a web address, referring to a location on a network for retrieving some resource. It has a fancy diagram to describe the parts:

The only required parts are the scheme and path, though typically the //host is included as well at a minimum.
The reference URL regex breaks down as follows:
http://[a-zA-Z0-9-]+(\.[a-zA-Z0-9-]+)+(:[0-9]+)?(/[^\s]*)?
http://- the scheme hardcoded as “http” and then the separator “://”.[a-zA-Z0-9-]+(\.[a-zA-Z0-9-]+)+- The same domain regex as above.(:[0-9]+)?- The:and then one or more digits specifying the port. The?means that everything in the( )shows up zero or one time.(/[^\s]*)?- a “/” followed by zero or more characters that are not whitespace. If the first character in[ ]is^, that means everything not in the characters that follow.\sis shorthand for whitespace characters.
This doesn’t extract anything:
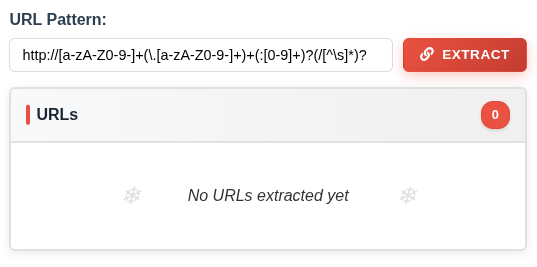
That’s because it’s hardcoded the scheme to be “http”. There’s a lot I could do to make this apply to all different kinds of URLs, but for most simple cases, just having that scheme be more flexible will do the trick. I’ll replace http with https? to capture both HTTP and HTTPS (because ? makes the “s” zero or one), or better is just \w+ to make it be any one or more word characters:
Emails
Email addresses can actually have a lot of complex information in them, but they are typically letters and numbers, and “@” symbol, and then a domain.
\b[a-zA-Z0-9._%+-]+@[a-zA-Z0-9.-]+\.[a-zA-Z]{2,}\b
This is actually a good simple regex for a quick scan, and works nicely here:
I’ll remove residents@dosisneighborhood.corp and holiday2025-kitchen@dosisneighborhood.corp, as they are the targets of the phish, not related to the actors:
Step 2
Overview
The “Defang & Report (Step 2)” tab has instructions for “defanging” the IOCs:
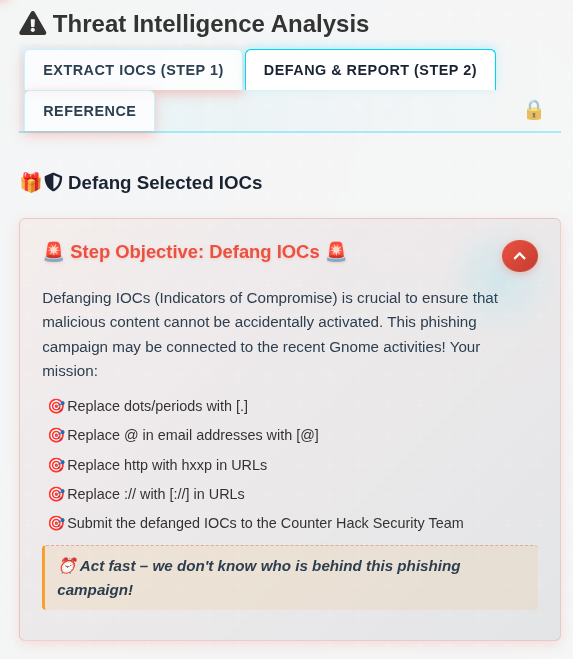
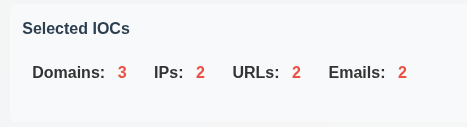
Below that, the stats for the IOCs I have from Step 1 are displayed:
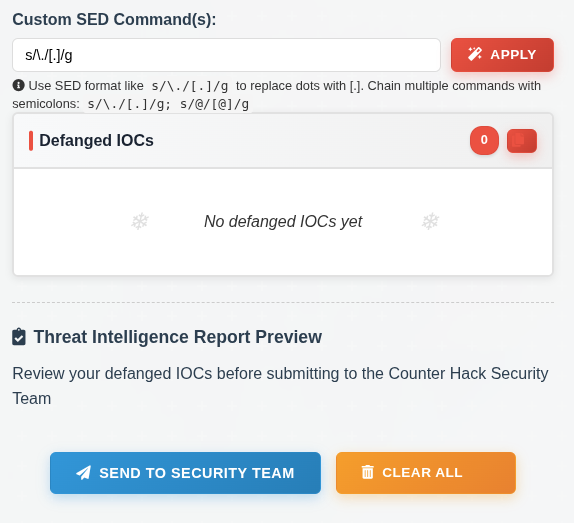
Then there’s a place to apply sed commands:
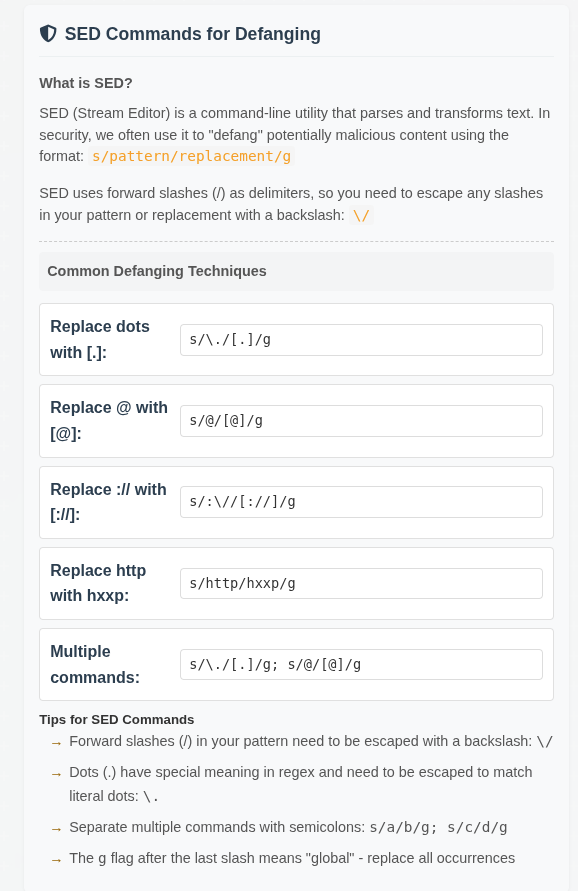
The reference page has a section on using sed:
Defang
The reference commands here are all good, they just need to be chained together (using “;” per the instructions):
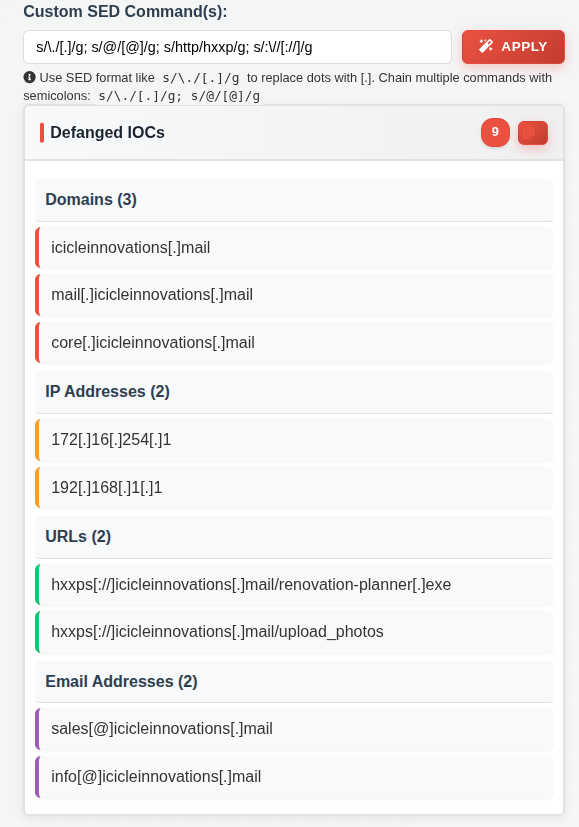
Submit
On clicking the button to submit this to the security team, there’s a pop-up showing the final report and that it’s complete!
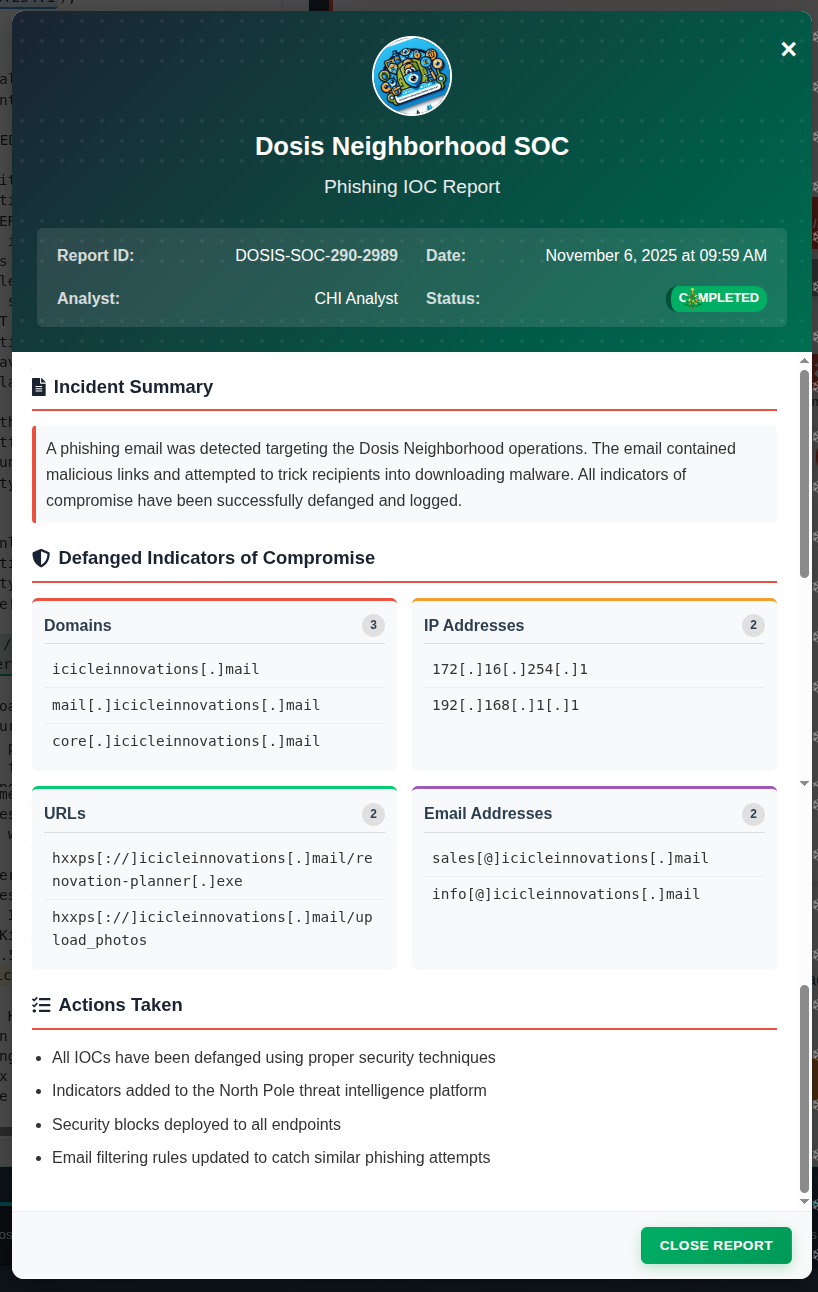
Outro
Its All About Defang
Congratulations! You have completed the Its All About Defang challenge!
Ed is pleased:
Ed Skoudis
Well you just made that look like a piece of cake! Though I prefer cookies…I know where to find the best in town!
Thanks again! See ya ‘round!