Holiday Hack 2025: Intro to Nmap
Introduction
Intro to Nmap
Difficulty:❅❅❅❅❅Eric Pursley is in the hotel parking lot with a motorcycle:

Eric Pursley
Hey, I’m Eric. As you can see, I’m an avid motorcyclist. And I love traveling the world with my wife.
I enjoy being creative and making things. For example, a cybersecurity tool called Zero-E that I’m quite proud of, and the Baldur’s Gate 3 mod called Manaflare. I’m even in the BG3 credits!
I also make tools, ranges, and HHC worlds for Counter Hack. Yup, including the one you’re in right now.
But most of the time, I’m helping organizations in the real world be more secure. I do a bunch of different kinds of pentesting, but speciailize in network and physical.
Some advice: stay laser-focused on your goals and don’t let the distractions life throws at you lead you astray. That’s how I ended up at Counter Hack!
Speaking of tools, let me introduce you to one of the most essential weapons in any pentester’s arsenal: Nmap.
It’s like having X-ray vision for networks, and I’ve set up a perfect environment for you to learn the fundamentals.
Help me find and connect to the wardriving rig’s service on my motorcycle!
Chat with Eric Pursley
Congratulations! You spoke with Eric Pursley!
The terminal opens up a terminal with two panes. The top pane has instructions, and the bottom a place to interact:
Solution
Overview
On entering “y”, the bottom has a Linux terminal:
This challenge will present a series of tasks in the top pane that will advance as I complete them.
#1
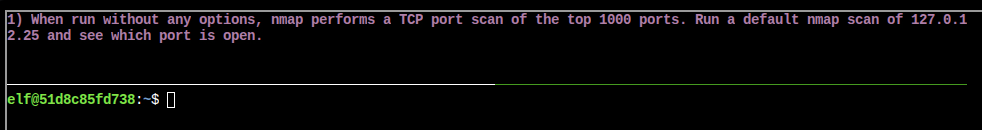
1) When run without any options, nmap performs a TCP port scan of the top 1000 ports. Run a default nmap scan of 127.0.12.25 and see which port is open.
To complete this, I just need to run nmap <target>, where the target is the given IP:
elf@6dc372329d71:~$ nmap 127.0.12.25
Starting Nmap 7.80 ( https://nmap.org ) at 2025-11-07 15:24 UTC
Nmap scan report for 127.0.12.25
Host is up (0.000065s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 0.04 seconds
#2
2) Sometimes the top 1000 ports are not enough. Run an nmap scan of all TCP ports on 127.0.12.25 and see which port is open.
To scan all ports, I’ll use -p -. -p is the option to set the ports. I can give a single port, multiple separated by ,, and include ranges like 25-30. By giving it just -, that means do all:
elf@6dc372329d71:~$ nmap -p - 127.0.12.25
Starting Nmap 7.80 ( https://nmap.org ) at 2025-11-07 15:26 UTC
Nmap scan report for 127.0.12.25
Host is up (0.000047s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE
24601/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 1.74 seconds
#3
3) Nmap can also scan a range of IP addresses. Scan the range 127.0.12.20 - 127.0.12.28 and see which has a port open.
Just like with ports, I can give a range of IPs using -:
elf@6dc372329d71:~$ nmap 127.0.12.20-28
Starting Nmap 7.80 ( https://nmap.org ) at 2025-11-07 15:26 UTC
Nmap scan report for 127.0.12.20
Host is up (0.00017s latency).
All 1000 scanned ports on 127.0.12.20 are closed
Nmap scan report for 127.0.12.21
Host is up (0.00019s latency).
All 1000 scanned ports on 127.0.12.21 are closed
Nmap scan report for 127.0.12.22
Host is up (0.00018s latency).
All 1000 scanned ports on 127.0.12.22 are closed
Nmap scan report for 127.0.12.23
Host is up (0.00017s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
8080/tcp open http-proxy
Nmap scan report for 127.0.12.24
Host is up (0.00017s latency).
All 1000 scanned ports on 127.0.12.24 are closed
Nmap scan report for 127.0.12.25
Host is up (0.00018s latency).
All 1000 scanned ports on 127.0.12.25 are closed
Nmap scan report for 127.0.12.26
Host is up (0.00017s latency).
All 1000 scanned ports on 127.0.12.26 are closed
Nmap scan report for 127.0.12.27
Host is up (0.00016s latency).
All 1000 scanned ports on 127.0.12.27 are closed
Nmap scan report for 127.0.12.28
Host is up (0.00018s latency).
All 1000 scanned ports on 127.0.12.28 are closed
Nmap done: 9 IP addresses (9 hosts up) scanned in 1.59 seconds
For all but one of the IPs, it returns that all 1000 ports scanned are closed. For 127.0.12.23, it shows port 8080 open.
#4
4) Nmap has a version detection engine, to help determine what services are running on a given port. What service is running on 127.0.12.25 TCP port 8080?
To scan for service banners, I’ll use -sV:
elf@6dc372329d71:~$ nmap -sV -p 8080 127.0.12.25
Starting Nmap 7.80 ( https://nmap.org ) at 2025-11-07 15:28 UTC
Nmap scan report for 127.0.12.25
Host is up (0.000070s latency).
PORT STATE SERVICE VERSION
8080/tcp open http SimpleHTTPServer 0.6 (Python 3.10.12)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.70 seconds
It’s running a Python webserver! This could be from python -m http.server 8080, or a script that uses that module.
#5
5) Sometimes you just want to interact with a port, which is a perfect job for Ncat! Use the ncat tool to connect to TCP port 24601 on 127.0.12.25 and view the banner returned.
I’ll make that connection as instructed:
elf@6dc372329d71:~$ ncat 127.0.12.25 24601
Welcome to the WarDriver 9000!
Terminated
Outro
Intro to Nmap
Congratulations! You have completed the Intro to Nmap challenge!
On completing question 5, the banner says:
Congratulations, you finished the Intro to Nmap and found the wardriving rig’s service! Type “exit” to close…
Eric offers his congrats:
Eric Pursley
Excellent work! You’ve got the Nmap fundamentals down - that X-ray vision is going to serve you well in future challenges.
Now you’re ready to scan networks like a seasoned pentester!