Holiday Hack 2025: Going in Reverse
Introduction
Going in Reverse
Difficulty:❅❅❅❅❅Kevin McFarland is hanging out in the Retro Emporium:

Kevin McFarland
Hello, I’m Kevin (though past friends have referred to me as ‘Heavy K’). If you ever hear any one say that philosophy is a useless college degree, don’t believe them; it’s not. I’ve arrived where I am at because of it. It just made the path more interesting.
I have more hobbies than I can keep up with, including Amateur Astronomy, Shortwave Radio, and retro-gaming. Things like backyard observances of distant galaxies, non-internet involved, around the world communications, and those who program for the Atari 2600 still invoke degrees of awe for me.
One of the most influential books I’ve read is “Godel, Escher, and Bach” by Douglas Hofstadter. I’m also a bit of a Tolkien fanatic.
My wife and my daughter are everything; without them, I surely would still be kicking rusty tin cans down the lonely highways of my past.
You know, there’s something beautifully nostalgic about stumbling across old computing artifacts. Just last week, I was sorting through some boxes in my garage and came across a collection of 5.25” floppies from my college days - mostly containing terrible attempts at programming assignments and a few games I’d copied from friends.
Finding an old Commodore 64 disk with a mysterious BASIC program on it? That’s like discovering a digital time capsule. The C64 was an incredible machine for its time - 64KB of RAM seemed like an ocean of possibility back then. I spent countless hours as a kid typing in program listings from Compute! magazine, usually making at least a dozen typos along the way.
The thing about BASIC programs from that era is they were often written by clever programmers who knew how to hide things in plain sight. Sometimes the most interesting discoveries come from reading the code itself rather than watching it execute. It’s like being a digital archaeologist - you’re not just looking at what the program does, you’re understanding how the programmer thought.
Take your time with this one. Those old-school programmers had to be creative within such tight constraints. You’ll know the flag by the Christmas phrase that pays.
Chat with Kevin McFarland
Congratulations! You spoke with Kevin McFarland!
Kevin gives me a program that shows up in my badge:

Just a BASIC Program
You’ve stumbled upon an old Commodore 64 floppy disk containing a mysterious BASIC program.
Solution
Program
The program is very short:
10 REM *** COMMODORE 64 SECURITY SYSTEM ***
20 ENC_PASS$ = "D13URKBT"
30 ENC_FLAG$ = "DSA|auhts*wkfi=dhjwubtthut+dhhkfis+hnkz" ' old "DSA|qnisf`bX_huXariz"
40 INPUT "ENTER PASSWORD: "; PASS$
50 IF LEN(PASS$) <> LEN(ENC_PASS$) THEN GOTO 90
60 FOR I = 1 TO LEN(PASS$)
70 IF CHR$(ASC(MID$(PASS$,I,1)) XOR 7) <> MID$(ENC_PASS$,I,1) THEN GOTO 90
80 NEXT I
85 FLAG$ = "" : FOR I = 1 TO LEN(ENC_FLAG$) : FLAG$ = FLAG$ + CHR$(ASC(MID$(ENC_FLAG$,I,1)) XOR 7) : NEXT I : PRINT FLAG$
90 PRINT "ACCESS DENIED"
100 END
Each line in BASIC starts with a line number, and typically programmers would number in 10s so that if they needed to add something later, they could put it in without having to renumber everything that follows.
The first line is a comment, marked by REM.
Next, it sets the ENC_PASS$ variable to “D13URKBT”, and then the ENC_FLAG$ variable as well. The ' is another way to signify a comment for everything that follows it.
INPUT prompts the user with the given string, and stores the result in PASS$.
Line 50 checks if the length of the input password matches the length of the ENC_PASS$ variable, and it if doesn’t, jumps to LINE 90 where it prints “ACCESS DENIED” and then ends.
If the lengths are the same, it’ll reach lines 60-80, which are a loop from 1 to the length of PASS. For each character in PASS$, it converts it to an integer and XORs it with 7. Then it converts back to a character, and compares to the corresponding character in ENC_PASS$. If any don’t match, it jumps to the end.
If it makes it through that loop, there’s another loop setting FLAG$ by doing basically the same thing, taking each character in ENC_FLAG$ and XORing it by 7.
Recover Flag
The straight forward way to get the flag is to take the ENC_FLAG$ value, “DSA|auhts*wkfi=dhjwubtthut+dhhkfis+hnkz”, and XOR each character with 7. CyberChef will do this nicely:
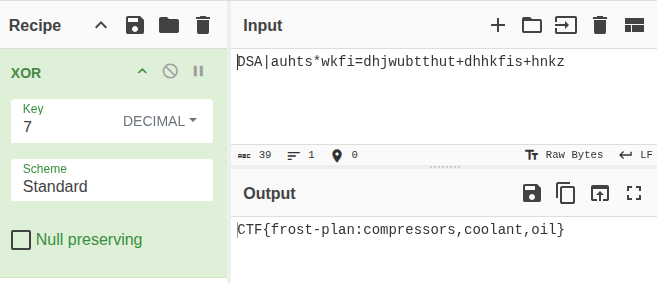
I could also do this in Python:
$ python
Python 3.12.3 (main, Aug 14 2025, 17:47:21) [GCC 13.3.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> enc_flag = 'DSA|auhts*wkfi=dhjwubtthut+dhhkfis+hnkz'
>>> ''.join(chr(ord(c) ^ 7) for c in enc_flag)
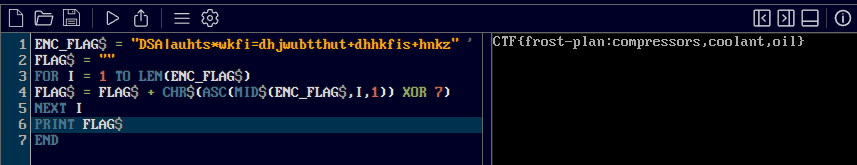
'CTF{frost-plan:compressors,coolant,oil}'
And of course the password decrypts the same way:
>>> enc_pass = "D13URKBT"
>>> ''.join(chr(ord(c) ^ 7) for c in enc_pass)
'C64RULES'
Emulation
There are a lot of different BASIC emulators online, and some that are specifically C64 emulators, but I had a very hard time finding one that would support both line numbers and all the characters used in this program. Even inside strings, “|” and “_” caused errors.
That said, I don’t need to run the entire program. Shoutout to elakamarcus who found qbjs.org that will run the code I need it to run:
Outro
Going in Reverse
Congratulations! You have completed the Going in Reverse challenge!
Kevin is impressed:
Kevin McFarland
Excellent work! You’ve just demonstrated one of the most valuable skills in cybersecurity - the ability to think like the original programmer and unravel their logic without needing to execute a single line of code.
He has more to say, but it’s the introduction to his Act III challenge, Schrödinger’s Scope.