Flare-On 2024: Meme Maker 3000

Meme Maker 3000 is an HTML / JavaScript challenge that is made so much easier using webcrack. Most of the solution here is running webcrack and then it’s fairly easy to see a few commands to run in the browser dev console to get the flag. I’ll include a video comparing my solution without webcrack with what webcrack can do.
Challenge
The challenge prompt reads:
You’ve made it very far, I’m proud of you even if no one else is. You’ve earned yourself a break with some nice HTML and JavaScript before we get into challenges that may require you to be very good at computers.
The download has a single HTML page:
oxdf@hacky$ file mememaker3000.html
mememaker3000.html: HTML document, ASCII text, with very long lines (63426)
Run It
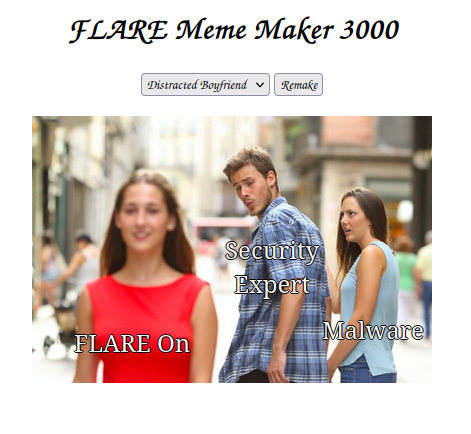
Opening the page in Firefox shows a popular meme image along with some text:

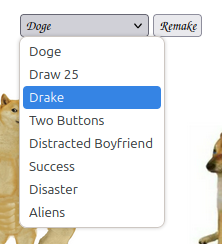
The dropdown menu has other meme images to choose from:
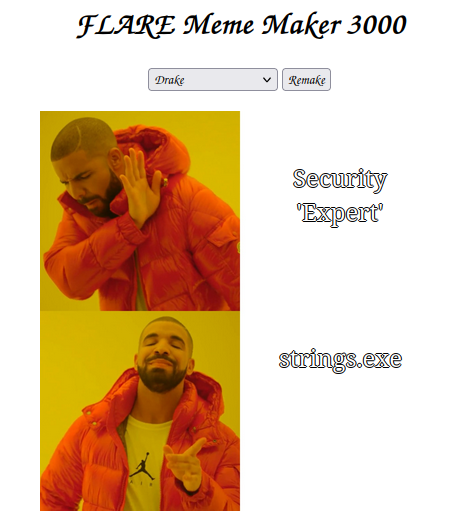
Selecting one picks that image with new text at random, and the “Remake” button randomizes the text as well:
Video Solution
I made a video showing how awesome webcrack is for this kind of JavaScript deobfuscation, using this challenge as an example:
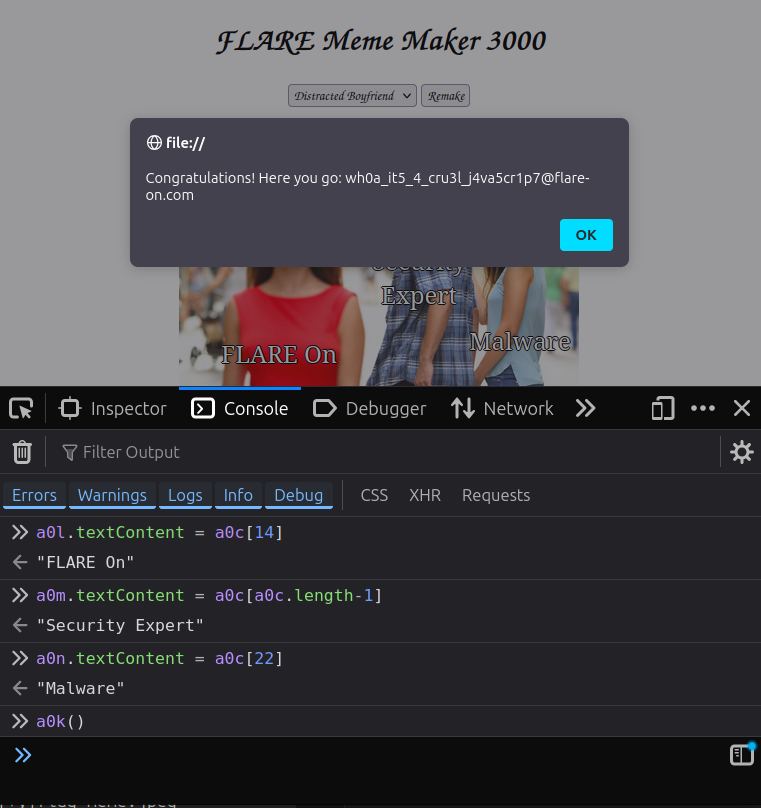
In the end, I need to have the “boyfriend” meme with these three phases and have the trigger function a0k run:
The easiest way to get that set is just to use the functions from the JavaScript in the debugger console:
a0l.textContent = a0c[14]
a0m.textContent = a0c[a0c.length-1]
a0n.textContent = a0c[22]
a0k()
Once I run that, it sleeps for three seconds and then generate the flag: